Updated March 17, 2023
Introduction to Advanced Persistent Threats (APT)
Advanced Persistent Threats are targeted attacks that are long-term operations carried out by its creators (hackers) by delivering the attack payload through sophisticated methods (i.e., bypassing traditional endpoint protection solutions), which then secretly carries out its intended actions (like information stealing) without being detected. Usually, the target of such attacks is very carefully chosen, and careful reconnaissance is carried out first. The target of such attacks is usually large enterprises, government organizations, often inter-government, which create rivals and launch such attacks on each other and mine highly sensitive information.
Some of examples of advanced persistent threats are:
- Titan rain (2003)
- GhostNet (2009)-Stuxnet(2010), which almost took down Iran’s nuclear program
- Hydra
- Deep Panda (2015)
Characteristics and Progression of Advanced Persistent Threats
The APT differs from traditional threats in many different ways:
- They use sophisticated and complex methods to penetrate the network.
- They remain undetected for a much longer duration of time. At the same time, a traditional threat might just get detected at the network or at the endpoint protection level, or even if they get lucky and pass by endpoint solutions, a regular vulnerability check and continuous monitoring will catch the threat. In contrast, the advanced persistent threats just pass by all layers of security and finally make their way to hosts, and they stay there for a longer time and carry out their operation.
- The APTs are targeted attacks, while traditional attacks may/may not be targeted.
- They also aim to infiltrate the entire network.
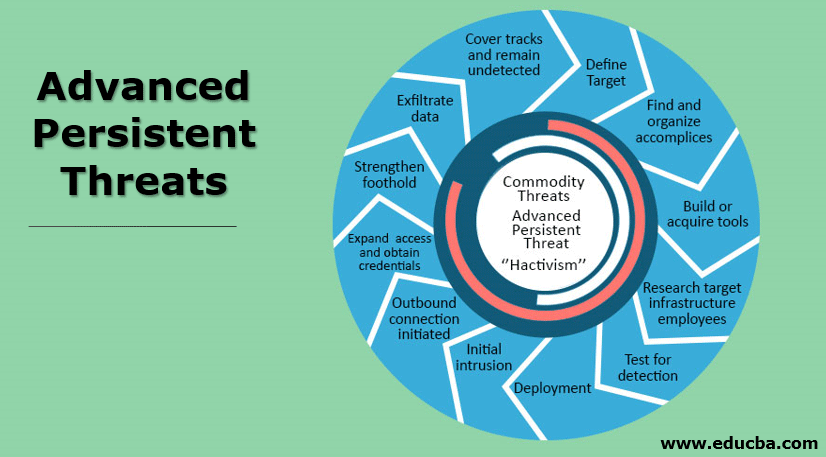
Progression of Advanced Persistent Threats
Following are the progression of advanced persistent threats:
- Selecting and Defining Target – A target should be defined, i.e. which organization should be the victim of an attacker. For this, the attacker first gathers as much information as possible via footprinting and reconnaissance.
- Find and Organize Accomplices – The APT involves advanced as sophisticated techniques that are used for attacking, and most of the time, the attacker behind ATP is not alone. The second would be to find the “partner in crime” that possesses that skill level to develop sophisticated techniques for carrying out APT attacks.
- Build And/or Acquire Tolls – To carry out the APT attacks, the right tools need to be selected. The tools can be built as well to create an APT.
- Reconnaissance and Information Gathering – Before carrying out an APT attack, the attacker tries to gather as much information they can to create a blueprint of the existing IT system. An example of information gathering could be the topology of the network, DNS and DHCP servers, DMZ (zones), Internal IP ranges, web servers, etc. It is worthwhile to note that defining a target might take a while, given the size of an organization. The larger an organization is, the more time it will take to prepare a blueprint.
- Test for Detection – In this phase, we look for vulnerabilities and weak spots and try to deploy a smaller version of reconnaissance software.
- Point of Entry and Deployment – Here comes the day when the full suite is deployed through an entry point chosen among many other weak spots after careful inspection.
- Initial Intrusion – Now, the attacker is finally inside the targeted network. From here, he needs to decide where to go and find the first target.
- Outbound Connection Initiated – Once the APT goes to target, sets itself, it then tries to create a tunnel through which data exfiltration will take place.
- Expansion of Access and Credentials Hunt – In this phase, the APT tries to spread itself in the network and tries to gain as much access as possible without being detected.
- Strengthen Foothold – Here, we try to look for and exploit other vulnerabilities. By doing this, a hacker increases the chance of getting access to other elevated access locations. Hackers also increase the chance of establishing more zombies. A zombie is a computer on the internet that a hacker has compromised.
- Exfiltration of Data – This is the process of sending the data to the hacker’s base. Hacker generally tries to use the company’s resources to encrypt the data and then send it to their base. Often to distract, the hackers exploit noise tactics to distract the security team so that the sensitive information can be moved out without being detected.
- Cover the Traces and Remain Undetected – The hackers make sure to clear all the traces during the attack process and once they exit. They try to remain as stealthy as possible.
Detecting and Preventing Apt Attacks
Let us see the detecting and preventing apt attacks:
Preventive Measures:
- Awareness and Required Security Training: The organizations are well aware that most of the security breaches that are happening these days, it happens because users have done something which should not have been done, maybe they have been lured, or they have not followed proper security measures while doing anything at offices such as downloading software from bad sites, visiting sites which have malicious intent, became a victim of phishing and many more! So, an organization should keep running security awareness sessions and make their employees on how to do work in a secure environment about the risks and impact of security breaches.
- Access Controls (NAC and IAM): The NAC or the network access controls have a variety of access policies that can be implemented to block the attacks. If a device fails any of the security checks, it will be blocked by NAC. Identity and access management (IAM) can help to keep the hackers away who tries to steal our password tries to crack a password.
- Penetration Testing: This is one great way to test your network against penetration. So, here the organization people itself become hackers who are often called as ethical hackers. They have to think like a hacker to penetrate inside the organizational network, and they do! It exposes the existing controls and vulnerabilities that are in place. Based on exposure, the organization puts the required security controls.
- Administrative Controls: The administrative and security controls should be intact. This involves regular patching of systems and software, having intrusion detection systems in place accompanied by firewalls. The organization’s public-facing IPS (such as proxy, web servers) should be placed in DMZ (Demilitarized zone) to separate from the internal network. By doing this, even if a hacker gains control of a server in DMZ, he will not be able to access internal servers because they lie on the other side and are a part of a separate network.
Detective Measures:
- Network Monitoring: Command and Control (C&C) center are the wings for Advanced Persistent Threats to carry in and out payloads and confidential data, respectively. The infected host relies on the command and control center to execute the next series of actions, and they generally communicate periodically. If we try to detect the programs, domain name queries that are happening in a periodic cycle, it would be worth investigating those cases.
- User Behavior Analytics: This involves employing the use of Artificial Intelligence and solutions that will keep an eye on the user’s activity. The expectation is – the solution should be able to detect any anomaly in activities that a host is doing.
- Use of Deception Technology: This serves as a double benefit for the organization. At first, the attackers are lured to fake servers and other resources, thereby protecting the original assets of an organization. Now, the organization also uses those fake servers to learn the methods which attackers use while they attack the organization; they learn their cyber kill chain.
Repair and Response
We must also learn the response and repair procedure if any Advanced Persistent Threats (APT) attacks happen. At first, APT might get caught in its initial phase if we are using the right tools and technologies, and in its initial phase, the impact will be much less because the main motive of APT is to stay longer and remain undetected. Once detected, we should try to get as much information from the security logs, forensics, and other tools. The infected system must be reimaged, and one should make sure that no threat is removed from all the infected systems and networks.
Then the organization should thoroughly run a check on all the systems to check if it has reached more places. The security control should then be modified to prevent such attacks or any similar ones that may happen in the future.
Now, if the Advanced Persistent Threats (APT) has spent days and it has been detected at a much later stage, the systems should immediately be taken offline, separated from all sorts of networks, any file serves which are affected must be checked as well. Then a complete reimaging should be done of affected hosts; a deep analysis should be done to reveal the cyber kill chain that was followed. The CIRT (Cyber Incident Response Team) and Cyber Forensics should be engaged to tackle all data breaches.
Conclusion
In this article, we have seen how an APT attack works and how we can prevent, detect and respond to such threats. One should get a basic idea about a typical cyber kill chain that is involved in APT attacks.
Recommended Articles
This is a guide to Advanced Persistent Threats (APT). Here we discuss the introduction, characteristics, progression of advanced persistent threats, detecting and preventing APT attacks respectively. You can also go through our other suggested articles to learn more –


