Introduction to Public Key Encryption
Public key encryption is also called asymmetric key encryption. As the name itself says, an asymmetric key, two different keys are used for public-key encryption. One key is used for the encryption process, and another key is used for the decryption process. Once the key is decided for encryption and decryption, no other key will be used. One key is called a public key from these two keys, and another one is called a private key.
Let’s assume that you want to communicate with friends over the internet, to start the communication securely; you need to obtain both public and private key. The private key is a secret key; you should keep it as a secret. If the private key is disposed to another party, there is a chance of attack through the third party.
If X wants to communicate with Y securely, both X and Y should have a public key and private key.
- X should keep her private key secret.
- X should inform her public key to Y.
- Y should keep her private key secret.
- Y should inform her public key to X.
How does Public Key Encryption Work?
Working of Public Key Encryption is explained below:
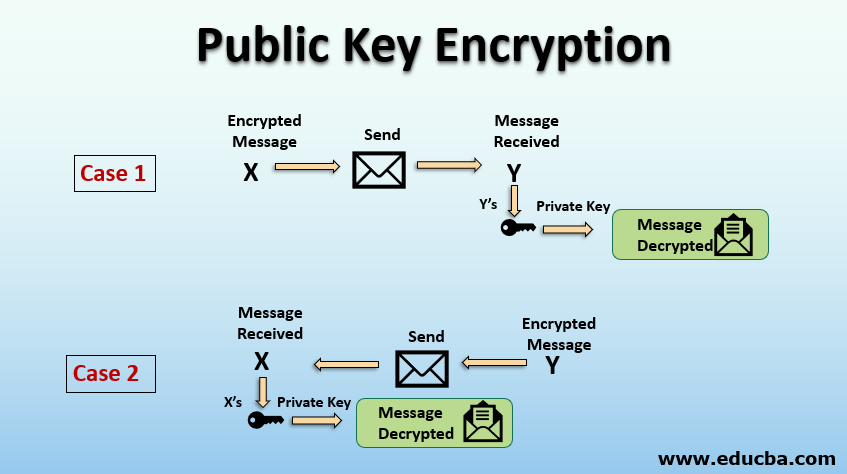
Case 1
When X wants to communicate with Y, X uses Y’s public key to encrypt the message; this is possible because Y shares her public key to X.
- X sends the encrypted message to Y.
- Y receives the message from X.
- Y decrypts the message using her, i.e. Y’s private key.
Case 2
When Y wants to communicate with X, Y uses X’s public key to encrypt the message. This is possible because X shares her public key with Y.
- Y sends the encrypted message to X.
- X receives the message from Y
- X decrypts the message using her, i.e. X’s private key.
Components
Following are the components of the public key encryption:
- Plain Text: The text in a readable format and can be understood by anyone is called plain text. The plain text is used as an input for the encryption process.
- Ciphertext: The text converted to readable format in a non-readable format using the encryption algorithm is called a ciphertext. The ciphertext is an output of the encryption process. It is in a non-readable format and not understand by anyone.
- Public Key: The key which is known to everyone is known as the public key. A public key is usually used for the encryption process at the sender’s side.
- Private Key: The key which is not known to everyone, which is kept as a secret, is known as a private key. The private key is used for the decryption process at the receiver side.
- Encryption Algorithm: The algorithm which is used to convert plain text to cipher text is known as an encryption algorithm.
- Decryption Algorithm: The algorithm which is used to convert cipher text to plain text is known as a decryption algorithm.
Public Key Encryption Algorithms
The following are the Algorithms of public-key encryption.
RSA Algorithm
RSA is the most popular public-key encryption algorithm. RSA algorithm is based on mathematical computation were identifying and multiplying a large prime number is easy but difficult to factor their factor. The private and public keys used in the RSA are large prime numbers.
Steps for RSA Algorithms:
- Select two large prime numbers X and Y.
- Calculate the product N = X*Y.
- Choose the public key E such that it is not a factor of (X – 1) and (Y – 1).
- Chose the private key D such that the following equation becomes true.
- (D * E) mod (X – 1) * (Y – 1) = 1
- For encryption, calculate CT as CT = PT^E mod N.
- Send the CT to the receiver.
- For decryption, calculate PT as PT = CT^D mod N.
ElGamal Cryptography Algorithm
ElGamal is another popular public-key encryption algorithm.
ElGamal Key Generation:
- Select large prime number P as public key and Q as the private key.
- Select the second encryption key as E1.
- Select the third encryption key as E2 such that E2 = E^Q mod P ElGamal Key encryption.
- Select random number R.
- Calculate ciphertext as CT = E1 ^R mod P.
- Calculate second Cipher text CT2 = (PT * E2^R) mod P ElGamal key decryption
- Calculate plain text as PT = (CT2 *(CT^Q)^-1) mod P.
Recommended Articles
This is a guide to Public Key Encryption. Here we discuss public-key encryption, its components, and how does it work, along with examples. You may also look at the following articles to learn more –

