Updated September 7, 2023
Introduction to iSCSI
Internet Small Computer System Interface is a transport layer protocol built on TCP Protocol. It ensures data transfer between the iSCSI initiator and the storage target over the TCP/IP network at the block level. It also supports high-level encryption of the transferred data packets and decryption on the arrival of data packets at the target side.
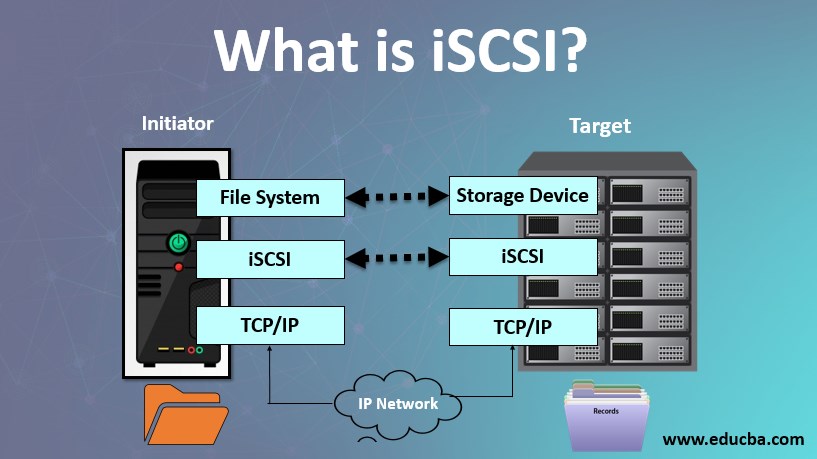
What is iSCSI?
Internet Small Computer System Interface is a Block Transport Layer protocol that works on Block Level protocol Interface. Block protocol can also directly access the storage and control the data flow inwards or outwards through a protocol SCSI. Strong encryption protects the information from the Source and Target at both the iSCSI Initiator (source) level and the iSCSI Target (destination) level, where it decrypts the information. This can be considered only when there is data transfer between LAN (Local Area Network) or WAN (Wide Area Network) as the data accessing is very fast.
How does iSCSI work?
Connect computing devices to network storage for media and data access using blocks. The iSCSI protocol uses initiators to send a set of SCSI commands to server storage targets. These storage targets may include SAN, NAS, etc. This protocol allows storing data to remote network storage and abstracts the data for applications that require storage.
It works by transporting the data at the block level between the initiator and target over the server on a device. The protocol collects the set of commands and gathers the data as packets to be transferred over the TCP/IP. A single-point connection transmits the data packets to the server. The iSCSI Protocol deconstructs the data packets using a collection of SCSI commands after they reach their destination, enabling the operating system to identify whether it is a nearby SCSI device.
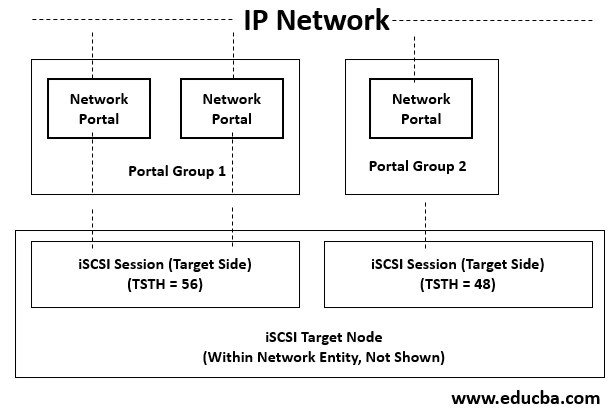
Architecture
In simple words, we can say that iSCSI is a client-server architecture. The Clients of an iSCSI interface are known as “initiators,” and the server that shares the storage area is known as the “targets.”
The TCP/IP Protocol facilitates data sharing.
iSCSI Components
There are two most important components for iSCSI through which the data transfer happens over the network. They have been discussed briefly below:
Initiator
These initiators group the commands into the network packets and instruct them to transfer at the iSCSI target. Generally, a software-based initiator is used at the OS to perform this data packet transport. Hardware devices like HBA (Host-based Adopters) with high-level encryption functionality exist. Another alternative to this hardware device is the iSOE card with an engine to operate from the host level, which frees the CPU cycles on the host server.
Target
iSCSI target is the storage device, a local drive to the host system. The operating system disassembles the data packets by executing a set of commands after they reach their destination. The target level decrypts the data packets when the initiator encrypts them.
Limitations and Features of iSCSI
Below are the limitations and features:
Limitations
- The iSCSI storage network’s main limitation is its Fiber Channel performance. With the emerging technologies, the gap between the performances has been improved.
- Now both iSCSI and FC storage performance is almost similar to each other.
Features
- IP Routing: One of the important advantages of ISCSI is that it uses TCP/IP Protocol. TCP/IP allows long-distance IP routing without external gateway hardware. It also provides high flexibility and a huge storage network environment.
- Security: The Internet Security Protocol ensures the security of IP traffic in a network by authenticating and encrypting each data packet it receives.
- Storage array: iSCSI targets a large storage array. Free array software or commercial products are available. It usually provides unique iSCSI targets for the number of clients or users.
- Standard Ethernet: It uses Standard Ethernet, and because of this, it does not require expensive components to be built for this protocol.
Importance
A few important features are listed below:
- iSCSI is a storage networking protocol that transports input-output data over a TCP/IP network.
- It is similar to FC Protocol, which transfers large data with low overhead and less latency.
- Users who wish to leverage the benefits of a SAN often find iSCSI to be more advantageous than FC.
- The block-level file sharing is more efficient and faster than any other file transfer protocol.
- It can handle natively greater distances to share files. Commonly, the storage network can be far from the users or clients. It can take this in a much better way than FC.
- It supports CHAP (Challenge/Handshake Authentication Protocol), which ensures a user or server has credentials to log in to a particular server on a SAN.
Benefits
- Cost-Effective: It provides a cheap connectivity network to transfer the files at the block level compared to FC.
- Reusability: To set up iSCSI implementation, you can reuse an existing server.
- Efficient: It is used for block storage, and it is very fast.
- Reliable: Users don’t need much knowledge of the iSCSI storage system as it is easy to understand and configure.
- Leverage: it is an internet-based protocol. It leverages the interoperability benefits of TCP/IP and Ethernet.
Conclusion
Best practices dictate that you should keep the networks supporting iSCSI from external sources or access. The main security risk in iSCSI SANs is that hackers can hack the stored data over the system or the server. With ACLs (Access Control Lists), storage admins can take precautions to lock the user privileges information.
Recommended Articles
This is a guide to What is iSCSI? Here we discuss an introduction, how it works, its importance, and the architecture, components, features, limitations & benefits. You can also go through our other related articles to learn more –