Updated March 27, 2023
Difference Between IPS and IDS
Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) both are components of the network infrastructure. IPS vs IDS both are the database containing known cyber Attack Signatures that compares network packets to cyber threats, with a matching flag. The main difference is that IDS is a system for tracking, while IPS is a system for regulation. Whereas the IPS prevents the packet from being transmitted depending on the packet content, IDS does not change the network packet in any way, much like firewalls block the traffic by IP address.
What are IPS and IDS?
IPS – This tool will take action and does not require the administrators’ decision to prevent any data packet to identified as a threat by the IPS tool. In addition, IPS systematically evaluated and applied for all packets reaching the network automatically. And also, IPS have two types which are Statistical Anomaly Detection, Signature-Based detection.
- Statistical Anomaly Detection: They randomly use samples of network traffic and compare them. They are linked by ports, bandwidth, protocols, and tools.
- Signature –Based Detection: Every type of attack uses significant patterns recognizable. The signature can be an attacker-facing signature where packets can be tracked by finding a match in your stored exploit attack file.
IDS – IDS is described as a tool to detect packet intrusion and classify which packets may or may not be threatened. It should only be noticed not to obstruct. It is a hybrid hardware/software protection platform that tackles external and internal threats and tracks in real-time network activity. IDS also have two types which are as follows.
- Host-Based Intrusion Detection System: This is a host-based sensor, which involves the use of software as agents on workstations. HIDS has tracked such agents. The agents track and log files of a specific operating system when the agents are installed.
If the activity has been changed unusually and the job starts as soon as the activity monitoring is installed. They can monitor attacks based on changes in internal system activities. - Network-Based Intrusion Detection System: It is a network-based sensor (Ethernet or WIFI) located in segment points or boundaries and tracked device and system transfer data packets
These use real-time surveillance so that attackers can no longer hide, modify or erase evidence of an attack. These are extremely useful for forensic analysis.
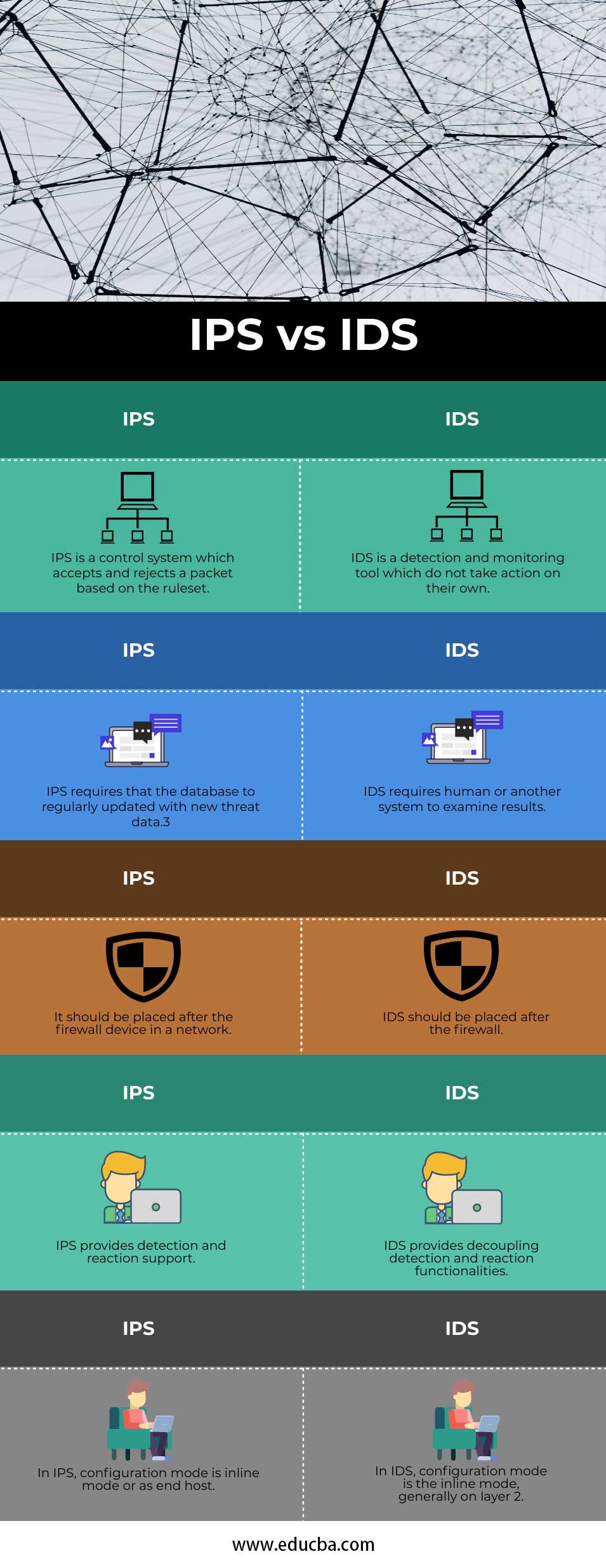
Head to Head Comparison between IPS and IDS (Infographics)
Below are the top 5 comparisons between IPS vs IDS:
Key differences between IPS and IDS
Let us discuss some key differences between IPS vs IDS in the following points:
- The IDS and IPS both read and compare network packets with the contents of known threats. IDS are tools for detection and surveillance, which take no action on their own.
- IPS is a control system accepting or refusing a registered packet. IDS requires a person or other device to review and decide the next steps that can depend on the quantity of network traffic generated on a daily basis.
- The IPS, on the other hand, aims at gathering and dropping dangerous packets before hitting their target. It is more proactive than IDS, which just needs a regular update of the database with new threat data.
- The failure of an IPS system leads to unexpected attacks. Don’t forget to use a firewall to filter, block and allow ports, addresses, operations, but some of them can also be accessed over the network. Unless technology is integrated into a single device, the manager has options to use as an inline IPS or only to identify strategically placed sensors to track the network traffic passively.
- IDS should be placed after the firewall, whereas IPS should be placed after the firewall device in a network.
- In IDS, configuration mode is the inline mode, generally on layer 2. On the other hand, In IPS, configuration mode is an inline mode or as an end host.
Comparison Table of IPS vs IDS
The table below summarizes the comparisons between IPS vs IDS:
|
IPS |
IDS |
| IPS is a control system that accepts and rejects a packet based on the ruleset. | IDS is a detection and monitoring tool which do not take action on their own. |
| IPS requires that the database to regularly updated with new threat data.3 | IDS requires human or another system to examine results. |
| It should be placed after the firewall device in a network. | IDS should be placed after the firewall. |
| IPS provides detection and reaction support. | IDS provides decoupling detection and reaction functionalities. |
| In IPS, configuration mode is an inline mode or as an end host. | In IDS, configuration mode is the inline mode, generally on layer 2. |
Conclusion
Keep in mind that internet security threats become quieter and dangerous when evaluating a security solution for your corporate infrastructure or your home. A layered security system integrating signature and computational technology with other instruments would enable you to level the field of play against actors involved in threats and their attack methods. One of these important instruments and has a vital role in protecting corporate network infrastructure and personal computers are the intrusion prevention program’s integrated functionality, whether network or host-based.
Recommended Articles
This is a guide to the top differences between IPS vs IDS. Here we discuss the key differences with infographics and comparison table. You may also have a look at the following articles to learn more –