Updated January 4, 2023
Introduction to PHP sha1()
PHP sha1() function is a very important function as part of PHP as it is a backed server-side scripting language that needs more emphasis on the security terms. PHP sha1() deals with the security and hashing function which calculates and computes a value of SHA-1 of the hash of the string. Internally PHP sha1() makes use of a subtype of the US Secure Hash Algorithm 1. Sha1() function produces a hash string with a value of 160 characters and then when this hash string is given as an input to the function it produces an output which is a highly secured message digest.
Syntax
sha1(string, raw)Explanation: sha1() function makes use of two types of arguments like string and raw which is used for generating the string and calculating the length of the string with some value. raw is another argument or parameter which is optional in the sense if specified with the sha1() function then it passes the parameter with an optional value such as true or false and then it passes the remaining value to specify and describe the hex or binary value output format. If the optional value appears to be Raw 20 then it is a 20-character binary format otherwise it Is Default 40-character hex number with some specific value.
How does sha1() function work in PHP?
As PHP is a server-oriented scripting language it is used to keep the backend related data and manipulations preserved and secured. sha1() function has solved the problem of securing the data related to password and user management. sha1() function and its sub algorithms like US-Secure Hash algorithm 1 are used for the generation of a message digest and digital signature.
The SHA-1() function makes use of the US-Secure hash algorithm1 which is used in a way where the string is given as an input and then a message digest is given as an output. Input is fed to the signature algorithm which checks and verifies for the signature of the message. If a signature message is used as an input rather than the actual message, then it has a high chance of improving the efficiency of the overall algorithm.
This process will optimize and compress the message input and message output functionality compared to the normal hash string message as an input to the signature algorithm. Further if this algorithm is used by the verifier then a digital signature can be used by the creator of the digital signature.
sha_file() function is another subcomponent of the sha1() function which uses the hash of the file function.
This file function of the file name is used to calculate the hash of a file and one raw output will be given to it which will be used to return the message or the string with a value of whether true or false. Md5() algorithm within the function and crc32() with the function will also be used to generate the polynomial of the string. And will help in generating a more secured string with some refined digital signature.
Examples to Implement PHP sha1() Function
Below are mentioned the examples:
Example #1
his program represents the calculation of the SHA-1 hash of the string after passing one string value to get the hash of the string.
Code:
<?php
$str = "welcome to educba";
echo sha1($str);
?>Output:
Example #2
This program represents the calculation of the SHA-1 hash of the string after passing one string value to get the hash of the string and then it prints the value of the sha1 string as shown in the output. The input of the string is given as “Welcome to Educba” and the output shows the string value.
Code:
<?php
$str = "Welcome to Educba";
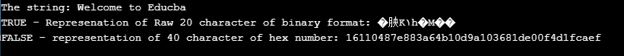
echo "The string: ".$str."\n";
echo "TRUE - Represenation of Raw 20 character of binary format: ".sha1($str, TRUE)."\n";
echo "FALSE - representation of 40 character of hex number: ".sha1($str)."\n";
?>Output:
Example #3
This program represents the calculation of the SHA-1 hash of the string after passing one string value to get the hash of the string and then it prints the value of the sha1 string as shown in the output. The input of the string is given as “Welcome to Educba” and the output shows the string value. Followed by a test of the input string being fed as an output.
Code:
<?php
$str = "educba";
echo sha1($str);
if (sha1($str) == "49108e13b1505cd6147054cfd07fb52f4c9d2641")
{
echo "\n!educba";
exit;
}
?>Output:
Example #4
This program is also a part of the sha1() function associated function of CRC 32 algorithm which takes a string “Hello World ” as input and then echoes the value without and with the string of % u value as shown in the output.
Code:
<?php
$str = crc32("Hello educba!");
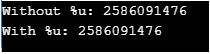
echo 'Without %u: '.$str."\n";
echo 'With %u: ';
printf("%u",$str);
?>Output:
Example #5
This program makes use of the password_hash function as part of the sha1() function and helps in generating the password_hash with an output value as shown and makes use of hashing function by putting the cost parameter as 12 to get the optimized message digest as the final output to optimize and increase the overall efficiency of the program.
Code:
<?php
$options = [
'cost' => 12,
];
echo password_hash("educba_is_a_laerning_portal", PASSWORD_BCRYPT, $options);
?>Output:
Example #6
This program makes use of the hash () function to generate the message digest of the given function which will be further used to convert into a digital signature for optimization.
Code:
<?php
function lion($data = "", $width=182, $rounds = 4) {
return substr(
implode(
array_map(
function ($h) {
return str_pad(bin2hex(strrev($h)), 16, "0");
},
str_split(hash("tiger192,$rounds", $data, true), 8)
)
),
0, 48-(192-$width)/4
);
}
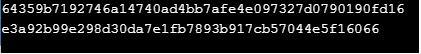
echo hash('tiger192,3', 'a-string'), PHP_EOL;
echo lion('a-string'), PHP_EOL;
?>Output:
Example #7
This program illustrated the md5 algorithm to be fed as an input string which is also counted as one of the complementary parts of the sha1() algorithm.
Code:
<?php
$str = 'apple';
if (md5($str) === '1f3870be274f6c49b3e31a0c6728957f') {
echo " i want to have a green or red apple?";
}
?>Output:
Conclusion
sha1() function is a part of PHP string references which includes a lot of security and cryptographic algorithms which is very necessary for the backend services and the servers for continuing the overall security breaches related issues and password and user management related data as secured.
Recommended Articles
This is a guide to PHP sha1(). Here we discuss an introduction, Syntax, and working of sha1() in PHP along with different examples and code implementation. You can also go through our other related articles to learn more –