Updated April 10, 2023
Introduction to PHP Encryption
PHP Encryption is nothing but achieving the encryption code with the help of some algorithms which are sometimes called hashing algorithms and they usually work with by taking a string or some other input and then it will help in creating a unique fingerprint from the string/other. Encryption involves changing the particular text/others into some different code text or other just to made the data safe without any exposure to most of all the people except to some who have the access. Check out the different types of PHP Encryption methods below.
Types of PHP Encryption
There are many different kinds of encryption methods in present-day use but commonly it is by being hashing, and the second one is the secret key encryption and the third one is the Envelope Encryption method. To each and every encryption method will have some multiple algorithms or ciphering to choose from each (for each it will have their own weaknesses and their own strengths ). Here we are going to focus on the implementation of hashing and the secret key encryption.
1. Hashing
The Hashing Algorithm of the PHP Programming Language usually takes one input value and then transforms it into one message digest. In one nutshell/more the plain text -values will be transformed into fixed lengths of hash, and it can only be validated just bypassing one original value to the unique hashing algorithm. This will make the hashing perfect just for storing all the user passwords.
It’s just worth noting that the hashing is not at all bulletproof solution for our query but some will not have all the hashing algorithms which are equal. We have considered the MD5 and SHA1 algorithms which are efficient and fast, and then making all those things ideal for the file verification and checksumming. The speed of them makes most of them unsuitable for hashing the user’s password. With the power of computation of modern GPU’s, the password will be cracked just with the help of the brute force in the simple matter of minutes and just by revealing the original plaintext password/passwords and intentionally the slower hashing algorithm/algorithms which are like bcrypt or Argon2 will be used.
Hashing the password which is generated with an algorithm then it will obscure certainly the actual and original data and then it will slow down the attacker whereas the developers should try one strongest algorithm which is available. The PHP Language will have a basic syntax which is password_hash().
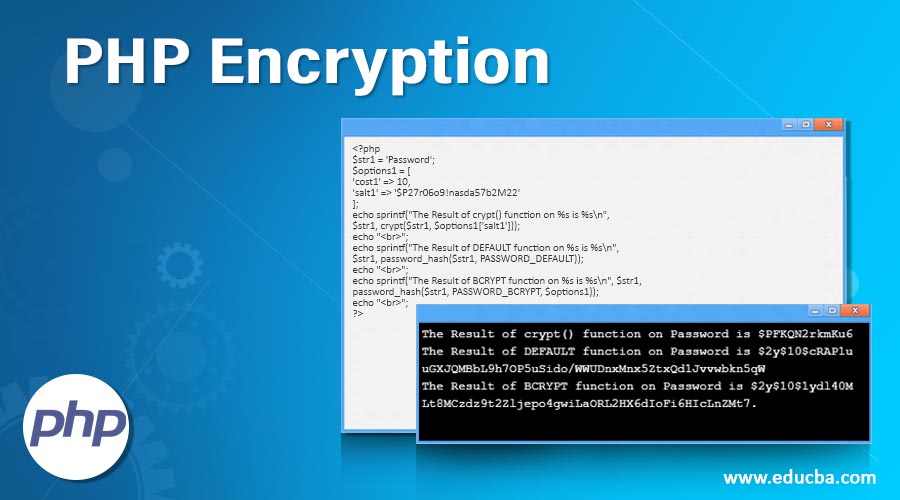
This is the example of using hashing technique ‘bcrypt’.
Code:
<?php
$str1 = 'Password';
$options1 = [
'cost1' => 10,
'salt1' => '$P27r06o9!nasda57b2M22'
];
echo sprintf("The Result of crypt() function on %s is %s\n",
$str1, crypt($str1, $options1['salt1']));
echo "<br>";
echo sprintf("The Result of DEFAULT function on %s is %s\n",
$str1, password_hash($str1, PASSWORD_DEFAULT));
echo "<br>";
echo sprintf("The Result of BCRYPT function on %s is %s\n", $str1,
password_hash($str1, PASSWORD_BCRYPT, $options1));
echo "<br>";
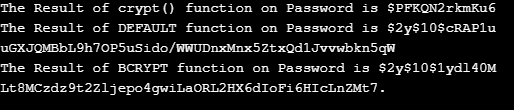
?>Output:
2. Secret Key Encryption
The Secret Key Encryption of the PHP usually uses one single key to both encryption and decryption data. It is also known as symmetric encryption. For this, if you are running an old version of the PHP Programming Language then install sodium of PHP Programming Language via PECL.
At first, you need the encryption key which is actually generated just by using the random_bytes() function code. But usually, you have to do only once and stores it just as an environment variable. This is the key which we have to keep as a secret. If the secret key is known then the encrypted will also be compromised.
$secret_key = random_bytes (SODIUM_CRYPTO_SECRETBOX_KEYBYTES);In order to encrypt the value which is going to pass to the sodium_crypto_secretbox() function with our key/secret key and $nonce. Then the nonce variable is generated using the random_bytes() function and it is just because the same/similar nonce can’t be used ever.
$nonce = random_bytes(SODIUM_CRYPTO_NONCEBYTES);
$ciphertext = sodium_crypto_secretbox(‘This is secret key!!!’, $nonce, $secret_key);This will represent the problem because we need that nonce which is going to decrypt the value later/afterward. But the NONCE/NONCES is not having any key to keep as a secret so that we can easily prepend it as out $ciphertext and then base64_encode() function is the value which is happening before saving it to the actual database.
$encoded1 = base64_encode($nonce . $ciphertext);
Var_dump($encoded1);The above syntax is just for encrypting the value. In order to decode/decrypt the encoded value then use the below syntax.
$decoded1 = base64_decode($encoded1);The length of the nonce variable or function will be extracted using the mb_substr() function just before decrypting the value.
This is the example of implementing random_bytes() function to understand the secret key encryption. Here the random string’s length will be converted with the help of binary hex in order to secure the random bytes in a string.
Code:
<?php
$length1 = random_bytes('3');
var_dump(bin2hex($length1));
?>Output:
3. Envelope Encryption
We all know that our data is vulnerable if our secret key is known/compromised. Just consider that a malicious user/attacker got access to the server point which is actually hosting our application/other. In this situation, attacker most of the times gets/discovers out the secret key which should be kept as secret. If it is discovered then our data may be in danger of exposing to the malicious user/attacker.
We can use Cloud KMS service which is actually provided by the Google Cloud Key Management Service. It provided a wide variety of so many useful features. It includes automatic key rotation and also the delayed key destruction capability.
Before sending plaintext to the CLOUD KMS, generate a unique encryption key each and every time when we actually write the data to the database. This key is called DEK (Data Encryption Key) which is actually used in encrypting the data. DEK which is sent to the Google Cloud KMS will be encrypted and then it will return the KEK (key encryption key). At last, KEK will be stored side by side in the actual database point which is next to the encrypted data and then the DEK will be destroyed.
Check out the data encryption and decryption as below:
Encryption process
- It will generate unique DEK – Data Encryption Key
- Using the SKE (Secret Key Encryption) the data will be encrypted
- Now the DEK – Data Encryption Key will be sent to the Cloud KMS for encryption purpose which actually returns the KEY – Key Encryption Key.
- Then the encrypted data will be stored and KEK side by side
- Then the destruction of the DEK will be done
Decryption Process
- Now at first, from the database encrypted and KEK (Key Encrypted Key) will be retrieved.
- Then send KEK for the Cloud KMD for decryption which actually returns the DEK – Data Encryption Key
- Now the DEK – Data Encryption Key will be used to decrypt the encrypted data.
- Now DEK – Data Encryption Key will be destroyed.
Conclusion
I hope you learned what is the definition of PHP Encryption and along with the various types of PHP Encryption methods along with the examples by mentioning their brief description. An example is shown here for envelope encryption because it is cloud-based encryption.
Recommended Articles
This is a guide to PHP Encryption. Here we discuss an introduction to PHP Encryption, top 3 types of encryption with examples in detail. You can also go through our other related articles to learn more –