Updated April 14, 2023
Introduction to Linux User Mode
In Linux, the Linux user mode is also known as User Mode Linux and abbreviated as UML. This methodology helps in enabling many kernel-based operating systems, which are Linux operating systems themselves within another Linux system. The kernel-based Linux operating system is also known as guests, and the Linux system on which they are run is known as the host. This enables multiple users to run their own set of Linux versions but limiting the number of hardware utilized. This also ensures that minimum hardware cost is involved without compromising on the isolations, privacy, and effect on the host’s operating system’s configuration. This also ensures that the original host environment is stable even if any of the Kernel-based operating systems are down!
Procedure and Syntax
In this section, we will take a look at the procedure one would need to follow to set up their User Mode. In the same context, we would also provide you with the syntax so that it becomes handy while you are setting it up! So here we go:
- Download the kernel from the source page of UML in accordance to the 32-bit or 64-bit operating system you might have. Post the kernel download, you would need to download another file system named FedoraCore5-x86-root_fs.bz2 (32-bit) or FedoraCore6-AMD64-root_fs.bz2 (64-bit).
- Once they are downloaded, one would need to decompress both the downloads and the syntax for that is:
host% bunzip2 <Kernel file name downloaded><File system file downloaded>Here, <Kernel file name downloaded>is the kernel file which one would download for preparing the UML. bunzip2 enables the user to unzip the files with the filenames trailing after the command. <File system file downloaded>needs to be replaced by 32-bit version (FedoraCore5-x86-root_fs.bz2) or the 64-bit version (FedoraCore6-AMD64-root_fs.bz2)
- Once the unzip process is complete, one would need to run the UML as follows. The syntax is:
host% chmod755 ./<Kernal File which got created after unzip>
host% ./<Kernal File which got created after unzip>ubda=<File system which got created after unzip> mem=128M- When the corresponding commands are run, log in to the system as root (no password would be required).
- Perform all kinds- of exploration you have planned for yourself.
- Once everything is done, remember to shut the kernel down!
How does Linux user mode work in Linux?
In this section, we would learn about the process of working of User Mode in Linux, and at first, we will look at a diagram and then discuss in detail the working. So, here we go!
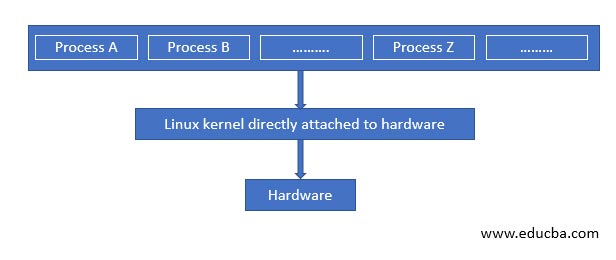
1. Normal process without UML
In the above configuration, the processes A, B, C …. and so on interact directly with the Linux Kernel, and in this way, any process directly asks the kernel, and correspondingly the Kernel links itself to the hardware. Now a problem with this kind of setup is the fact that once any process gets corrupted, it tends to impact the original Linux Kernel, and as a result of that, the entire system gets disrupted, and many times the only solution left is to flash the Kernel all over again leading to erasing of all the setup which was done for the Kernel.
And then comes to the rescue is the UML methodology which we will discuss now!
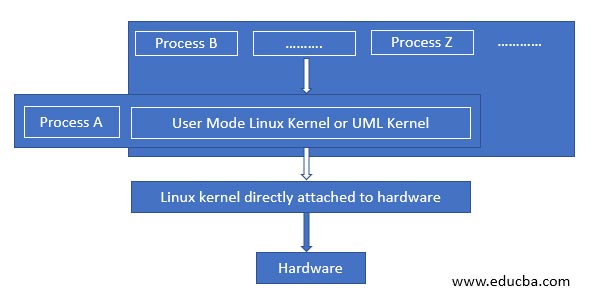
2. Process with UML
When we contrast the previous architecture to this, we see that the there is a very minute change in the level of the architecture and where it differs is that any process which need not require direct communication to the original Linux Kernel will pass through the User Mode Linux Kernel and the reason of this change is the fact that the process which tends to get corrupt will pass on the corruption to the UML Kernel only spun off for that particular User and will protect the original Kernel from getting disrupted, as a result of this any other user who is using the same Linux hardware and the original Linux Kernel will be safeguarded!
This particular architecture comes a long way in safeguarding the interests and the environment in a scenario where the hardware is shared among all the users, and the concept of hardware sharing is predominant given the effective and optimized use of resources.
Next, to understand the complete flow of Linux User Mode or UML working, it is also very important to understand the utilities of the UML after it has been set up, and that’s what we call “What’s next after configuring the UML”.
There are loads of possibilities on what one can do after a kernel is configured. So, in each of the cases, we would drop a few lines to know how UML in each of the cases works!
- Putting the configured UML on Network: Using uml_net and eth0 device, one can put the UML, which is configured over the network, so that it is accessible to the required users of that kernel.
- Build kernel from source: Here, the UML will give flexibility on how the kernel needs to be built. And in doing so, a default configuration UML is used for botting, and required changes are done in the menuconfig or xconfig.
- Configuring virtual machine from the configured UML: Here, a virtual machine is configured, and the hardware of the corresponding machine is shared among the different users who have access to the Kernel.
- Host Files accessing: Here, a filesystem is mounted in the system within the UML, and all the contents are ready for access to the required audience.
- Hack into Kernels: With using GDB, a direct method for examining memory is made capable, which essentially builds a capability for examining the memory for debugging by understanding the processors and segments and helps to figure out what exactly is going on!
Conclusion
With this article, we have taken a deep dive into the concepts which are essential for one to use the User mode function in Linux for the various utilities they are capable of. Furthermore, using it as a sandbox and playing with the environment without fear of breaking the kernel serves as the important point of research and innovation! Hence, anyone looking for the same usability should experiment on this at least once!
Recommended Articles
We hope that this EDUCBA information on “Linux User Mode” was beneficial to you. You can view EDUCBA’s recommended articles for more information.