Updated March 8, 2023
Introduction to Azure storage encryption
Storage encryption is requested by many companies as it doesn’t require any coding process and it is a simple feature that is readily available. But it applies to queues, files, tables, and blob storage. In Azure dashboard, CLI, PowerShell, REST API, and the .NET client library, the per-storage account has the option to enable or disable the security encryption. In Microsoft, both premium and standard storage of the resource manager accounts are encrypted.
How to perform storage encryption in azure?
The encryption of azure storage is made using the server-side encrypt technique when the data is present in the cloud. The advanced encryption technology is followed at both ends of data transit and is similar to windows BitLocker encryption. Storage encryption in Azure can be done by two methods. One is using the key-based authentication method and the other is infrastructure encryption with doubly encrypt data. Service-level encryption (SSE) in Azure is done either by customer-managed keys or Microsoft-managed keys.
Microsoft-managed keys are achieved by the Azure key vault. The following are the steps involved in creating storage encryption in Microsoft Azure using a key vault.
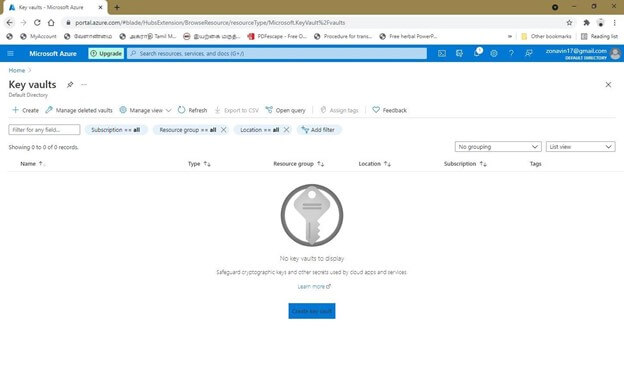
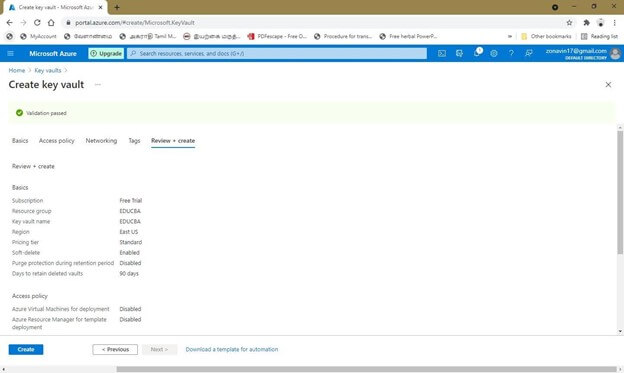
- Providing a new or existing Azure key vault. Tap on the NEW option and choose security and identity as shown, then choose the Key vault.
- Enter the name, location, resource group, and subscription in the given field. Then create the key vault.
- By security administrator, create a new key.
- After choosing the key vault, we have to configure keys. So, choose More from the portal and choose the key vault in the security and Identity screen.
- In the search bar, type key vault and it shows the list of services in the service menu.
- In the key vault list, choose the + button to manage the already encrypted keys by giving the name of the key vault.
- Choose Generate from the key list and enter the name of the key, then choose to create an option.
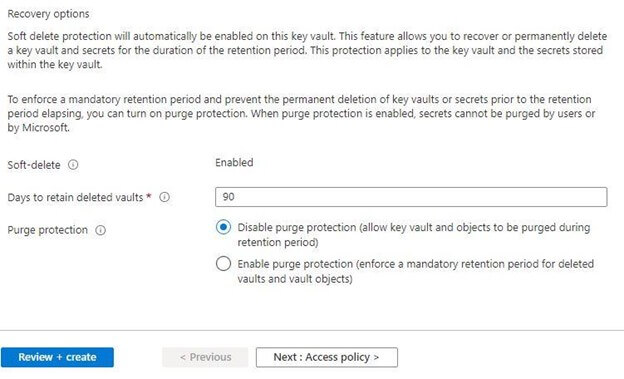
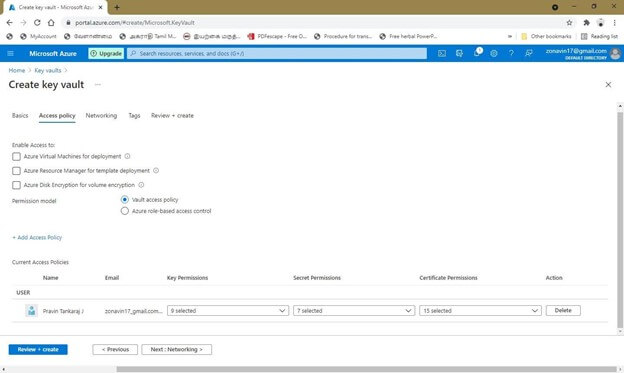
- The access permission in the key vault should be unwrapped, wrap, sign, verify, list, create and get. So prior to the SQL server accessing, the keys should be ensured correctly, and configure the access policies in the appropriate policies.
- Choose access policies on the navigation list after returning to the overview of the key vault page.
- Select the account from the list as you have mentioned earlier.
- Choose the key permission option, there check on unwrap, wrap, get, sign, create, list, and verify. Choose OK and save the settings to proceed further.
- A master and column encryption key is then generated using the DBA.
- Ensure the internet connection is stable with SQL server by establishing SQL Server Management studio. If both Azure key vault and SQL server are not connected, we have to update with SSMS 17.2 version.
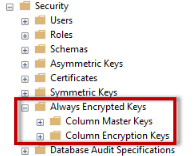
- In the database, expand the option and enables the always encrypted option. Then expand the encrypted keys column from expanding the security.
Database -> always encrypted -> Security -> always encrypted key -> column master keys -> column encryption keys.
- Finally, in column master keys, choose the new wizard and select folder of always encrypted keys, and again choose a new master key column in the same wizard.
- Create a name for the key, and in the key store change the option to the key vault. Then, the credentials can be provided by selecting the sign-in option.
- After verifying the identity, the authentication is successful, and choose for the required subscription, features, and key vault. Then the OK button should be used to close the dialog box.
- We can also create a new key in the azure key vault from the new column master key by choosing to generate a key option. By simply expanding the folder of column master keys, the SQL navigation system SSMS will display the recently created key.
Database -> always encrypted -> Security -> always encrypted key -> column master keys
- If you choose the folder of column encryption keys and choose a new column in the column encryption key, and meanwhile, if you choose the folder of always encrypted keys and select a new option. Then both the option will display the same wizard.
Disk encryption in Azure enables the user to mention the data disk on IaaS and OS which needs to be encrypted. DM-crypt encryption is followed in Linux and IS bit locker is applied in Windows OS encryption.
In Linux, the data partition in the shell cannot be encrypted. It applies to the on-premise data present at the particular portion uploaded in azure in Linux OS. Using tables, specific access can be given to the partitions.
In client-side encryption, the application encrypts the data and transited it by wire to feed into the storage account.
When the data reaches the host, again application decrypts it. To imply this, Azure key vault is enabled, where an active directory in Azure permits access to the keys to work on encryption. So, it manages to declaim the vaults and extract the keys and applies to client-side encryption. In blobs, where encryption to be made follows the combination of SSE and HTTPS to meet the perquisites of security policies. It is the optimum method of decryption and encryption to execute without any codes.
At the time of data transit, the HTTP protocol is used to provide safe communication over the open cyberspace.
In SaaS, the query parameter is implied to use that HTTP can be operated only with URL. In file share, on Windows encrypt, the SMB 3.0 is executed to the data flowing on the public internet. In Linux and Apple, the security support SMB 3.0 is executed to embed the file share servers on the machines which encrypt the data at transit.
Conclusion
Azure key vault protects the cryptographic codes used in Azure services and applications. The encryption and configuration keys can be saved in the Azure key vault. It cannot directly control the data objects in Active Directory but has access to the Azure key vault in AD which means that the user can drop the storage keys in the Azure key vault and then provide access to concerned groups, applications, or users.
Recommended Articles
This is a guide to Azure storage encryption. Here we discuss How to perform storage encryption in azure in detail. You may also have a look at the following articles to learn more –