Updated March 30, 2023
Difference Between Telnet vs SSH
The following article provides an outline for Telnet vs SSH. In the past, both Telnet and Secure Shell (i.e. SSH) were widely used to connect to remote servers. Telnet is the original protocol that was used in 1969 when the internet was first launched and is still in use today. However, it is irrelevant when used on public networks because it was designed to be used in private networks and has no security features. SSH was developed as a replacement for Telnet because of this. In addition, remote terminal service (RTS) allows users at one site to interact with a time-sharing system at another site as if their keyboard and display were directly connected to the remote machine. As a conventional protocol, Telnet differs from SSH, which is an enhanced version of the Telnet protocol with enhanced features.
What is Telnet?
Telnet is a network protocol that enables a user to communicate with a remote device via the Internet. Network administrators use it to remotely access and manage devices. Administrators can connect to a remote device by dialing its IP address or hostname. The telnet client software must be installed on your computer before you can use telnet. In addition, a Telnet server must be installed and running on the remote device. Default TCP port for Telnet is 23 (TCP). As a result, all data, including usernames and passwords, are sent in cleartext. This poses a potential security risk for users. As a result, telnet is rarely used today and is being replaced by a much more secure protocol called SSH (Secure Shell) for this reason. Telnet access on Cisco devices is described.
What is SSH?
You can remotely access and manage a device using the SSH network protocol. Since SSH uses encryption, all data transmitted over a network can’t be intercepted, whereas Telnet does not. Public-key encryption is used by SSH for such purposes. Users accessing remote devices must have an SSH client installed, just like Telnet. Installed and running an SSH server on a remote device. Port 22 is SSH’s default TCP port and is used by default.
Head to Head Comparison Between Telnet vs SSH (Infographics)
Below are the top 9 differences between Telnet vs SSH:
Key Difference Between Telnet vs SSH
Let us discuss some of the major key differences between Telnet vs SSH:
- Telnet is a conventional protocol, although it is still used in various applications. SSH is the replacement for Telnet and has some enhanced features as well as Telnet.
- For security reasons, Telnet transmits data in plain text. SSH, on the other hand, encrypts transmitted data, so a security breach is highly unlikely. Man-in-the-middle and insertion/replay attacks can’t stop SSH, but eavesdropping is possible.
- In contrast, SSH is more secure and provides security measures, whereas Telnet doesn’t provide any security mechanisms.
- Use of the Telnet protocol requires a private network. SSH, on the other hand, works on a public network. Telnet communicates over TCP/IP via port 23. SSH, on the other hand, communicates via port 22.
Telnet vs SSH Comparison Table
Let’s discuss the top comparison between Telnet vs SSH:
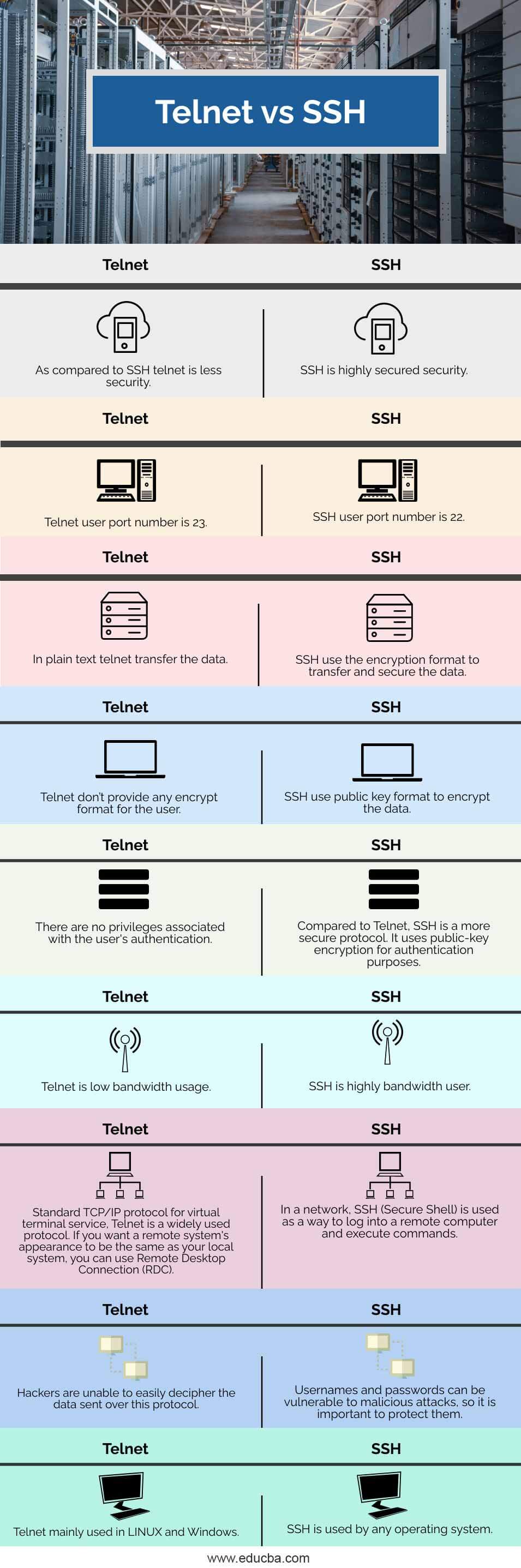
| Sr. No | Telnet | SSH |
| 1 | As compared to SSH, telnet is less security. | SSH is highly secured security. |
| 2 | Telnet user port number is 23. | SSH user port number is 22. |
| 3 | In plain text, telnet transfer the data. | SSH use the encryption format to transfer and secure the data. |
| 4 | Telnet doesn’t provide any encrypt format for the user. | SSH use a public key format to encrypt the data. |
| 5 | There are no privileges associated with the user’s authentication. | Compared to Telnet, SSH is a more secure protocol. It uses public-key encryption for authentication purposes. |
| 6 | Telnet is low bandwidth usage. | SSH is a highly bandwidth user. |
| 7 | Standard TCP/IP protocol for virtual terminal service, Telnet is a widely used protocol. If you want a remote system’s appearance to be the same as your local system, you can use Remote Desktop Connection (RDC). | In a network, SSH (Secure Shell) is used as a way to log into a remote computer and execute commands. |
| 8 | Hackers are unable to easily decipher the data sent over this protocol. | Usernames and passwords can be vulnerable to malicious attacks, so it is important to protect them. |
| 9 | Telnet is mainly used in LINUX and Windows. | SSH is used by any operating system. |
Conclusion
In terms of security, SSH is a better alternative to Telnet. Telnet does not provide much security, but it is still widely used today despite this. Even though both Telnet and SSH can be used to send data to remote servers, it is highly recommended that you use SSH instead.
Recommended Articles
This is a guide to Telnet vs SSH. Here we discuss Telnet vs SSH key differences with infographics and comparison table, respectively. You may also have a look at the following articles to learn more –