Updated February 15, 2023
Introduction to Kali Linux Hydra
Kali Linux Hydra is parallelized login cracker that supports various protocols to attack. It is fast, and flexible and new modules can be added easily. It is a pre-installed tool used for brute forcing username passwords to various services like ssh, ftp, MS SQL, telnet, etc,. Hydra tool also makes it possible for users such as researchers, and security consultants that helps in gaining unauthorized access to any system remotely.
What is Kali Linux Hydra?
Having weak passwords is still one of the biggest problems in security, cracking algorithms and guessing passwords has become easier, with the help of the brute forcing technique. It can be used on Linux as well as Windows and supports protocols such as HTTP FORM GET, AFP, HTTP FORM POST, HTTP HEAD, HTTP GET, HTTP PROXY, etc.
The basic rule of having a strong password is to have a minimum of 8 letters, with at least one special character, a capital letter, and a numeric. And to crack such passwords, Kali Linux has a brute force tool known as Hydra. Basically, it is a pre-installed tool, if in any case, if it is not installed or the user has been working with other distributions, below is the installation process to install Hydra on Kali Linux.
How to Install Kali Linux Hydra?
In the first place, Hydra is pre-installed on Kali Linux, if still, it needs to be installed due to any other issues, there are two ways, one is with Command Line Interface and the other with Graphical version. Most probably Command Line Interface is used with real developers.
Case 1:
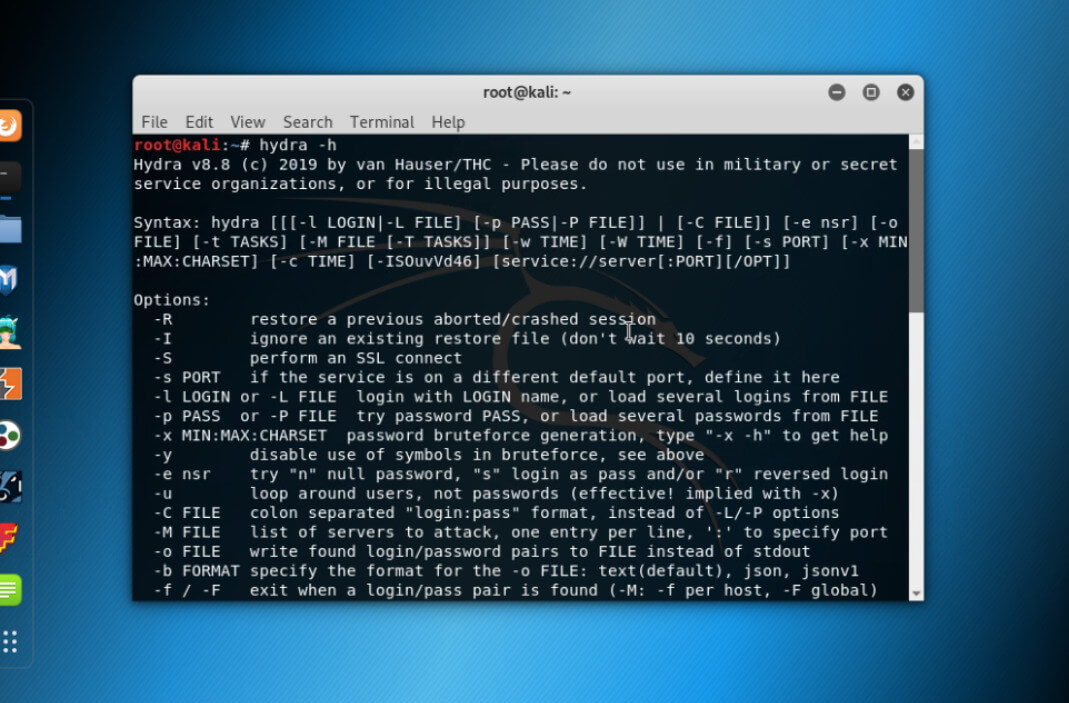
Let us assume Hydra is pre-installed on Kali Linux, and check for the Hydra helper command.
Command:
hydra -hOutput:
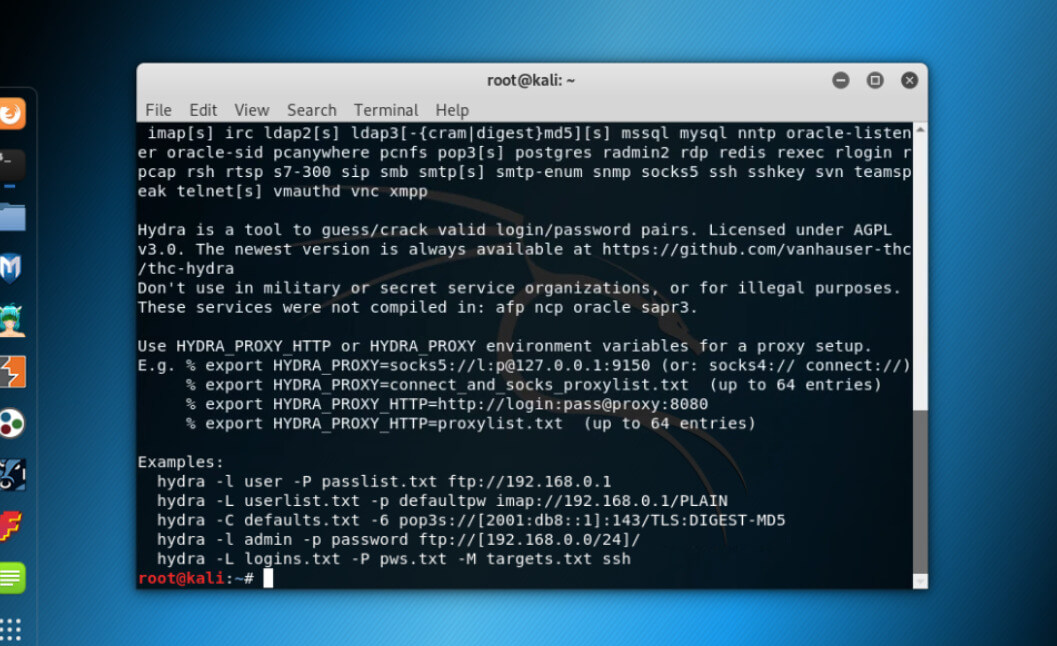
Hydra helper is shown, with possible flags. Have a look at the description of each command and as we can see, with Brute force, Hydra can crack a single username password or a list of it.
Case 2:
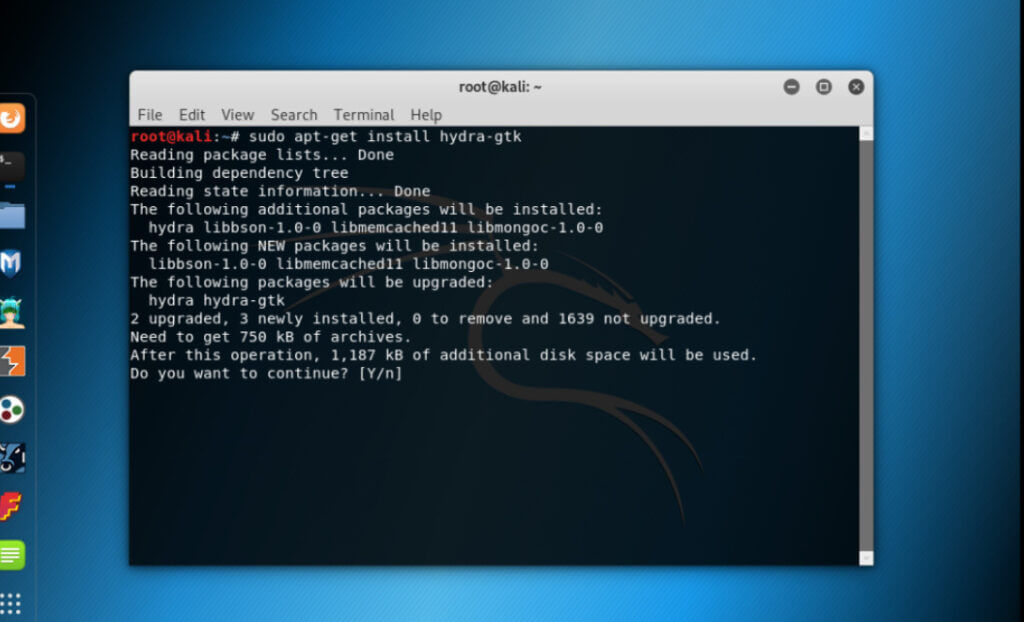
If Hydra is not pre-installed and the user wants to install it from the Source Repository, then use the below command.
Command:
sudo apt-get install hydra-gtkOutput:
This command will install Hydra directly from the Repository.
It installs the Command line version with Front End Graphical User Interface on Linux System.
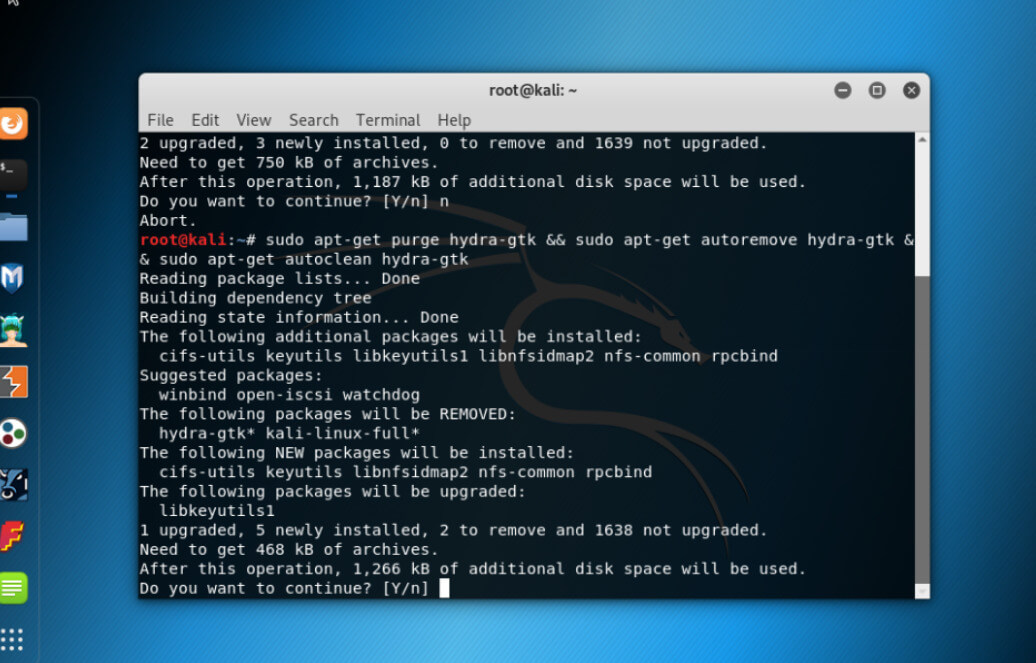
This command has a drawback in that the user will not be able to get the latest version, so if in case Hydra is already installed or pre-installed, it can be removed using the below command.
Command:
sudo apt-get purge hydra-gtk && sudo apt-get autoremove hydra-gtk && sudo apt-get autoclean hydra-gtkOutput:
Case 3:
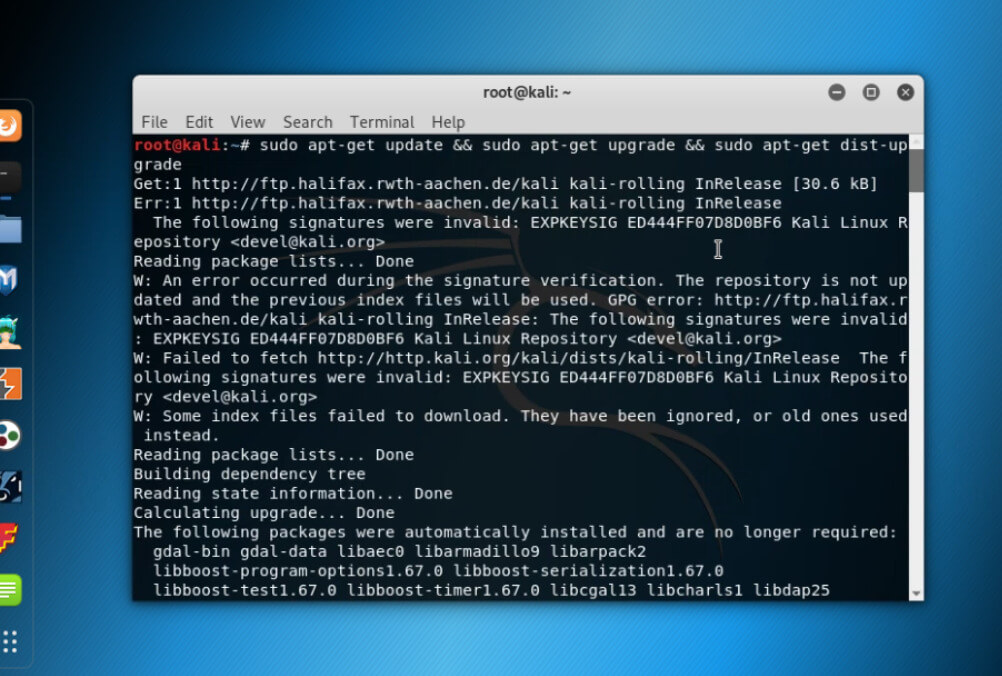
Installing from Source Repository with Latest version. Before installing the new version of Hydra, the system should be up to date. And hence by using the below command.
Command:
sudo apt-get update && sudo apt-get upgrade && sudo apt-get dist-upgradeOutput:
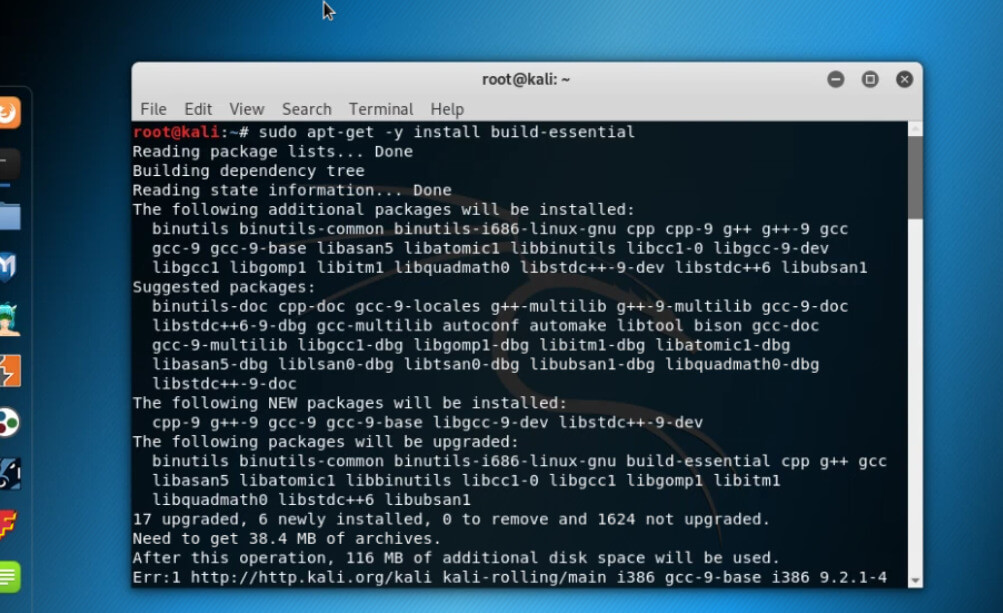
Once the system is up to date, some essential things are needed to install for hydra.
Command:
sudo apt-get -y install build-essential
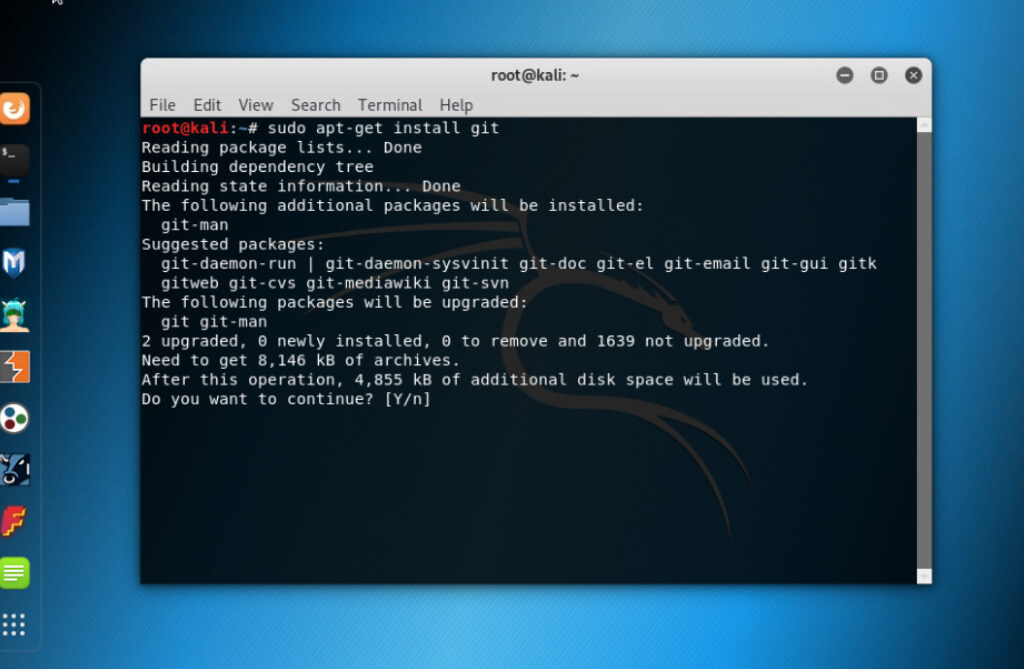
sudo apt-get install gitOutput:
If the user is using Debian or ubuntu based distribution, there need to be some supplementary libraries to be installed using the below command.
Command:
sudo apt-get install libssl-dev libssh-dev libidn11-dev libpcre3-dev \ libgtk2.0-dev libmysqlclient-dev libpq-dev libsvn-dev \ firebird-dev libncp-devKali Linux Hydra Login Pages
Passwords are used with systems since the earliest days of computing, introduced in 1961. System had a login command, which requested the user’s password, and hence after typing the word “PASSWORD”, the system turns off the printing mechanism. The strength of passwords depends on length, unpredictability, and complexity. Whereas weak passwords shorten the time to guess the password and gain control over corporate mail, business information, financial information, credit card data, etc.
The most popular credential attack is the brute force attack, which is a trial-and-error method, like guessing, attempting to decode the encrypted data used by an application program or a hacking tool. It is a fast network logon cracker that supports attack protocols. Hydra supports brute forcing services, one of which is used for brute forcing web-based logins, like user banking login forms, social media login forms, router web-based login forms, etc, HTTP-GET/POST-FORM handles these requests. Before firing up the Hydra login, there are some much-needed arguments.
- Target: URL: http://testasp.vulnweb.com/Login.asp?RetURL=%2FDefault%2Easp%3F
- Username for Login: Admin
- Password List: Location of dictionary file list that contains passwords that are possible
- Form Parameters: Use proxy or Tamper data to obtain from request parameters.
- Service Module: HTTP-POST-FORM
Kali Linux Hydra Tools and Examples
Given below are the kali linux hydra tools and examples mentioned:
Example #1
Usage of Hydra Example
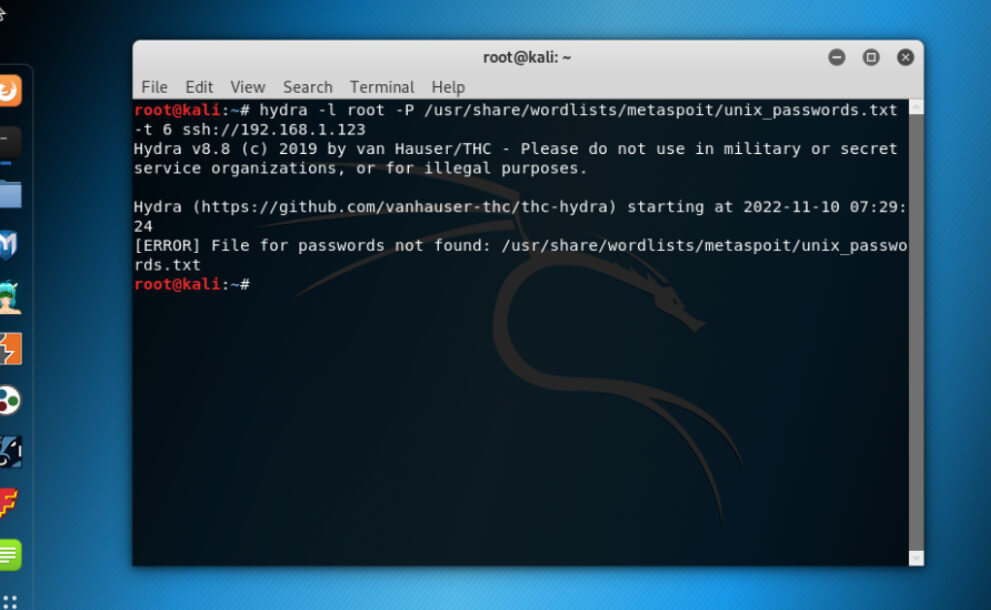
Here, we shall attempt to login as root user as “-l root” and password list as “-P /usr/share/wordlists/metaspoit/unix_passwords.txt” with threads 6 on the SSH server.
Example #2
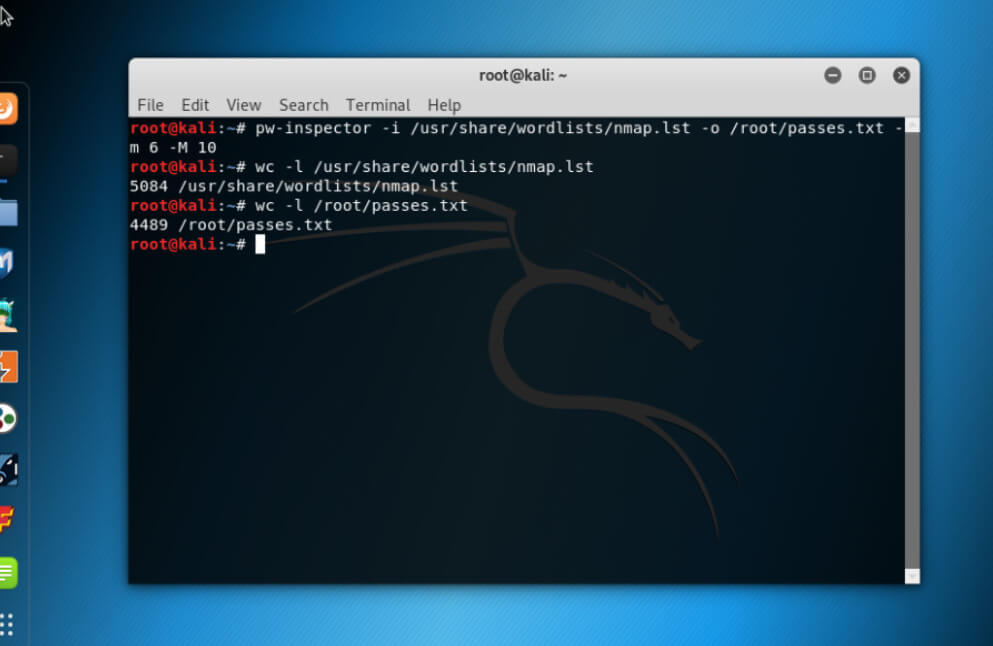
Usage of pw-inspector Example
Reading list of passwords and saving to file, here we shall select passwords with a minimum length of 6 and a maximum of 10.
Example #3
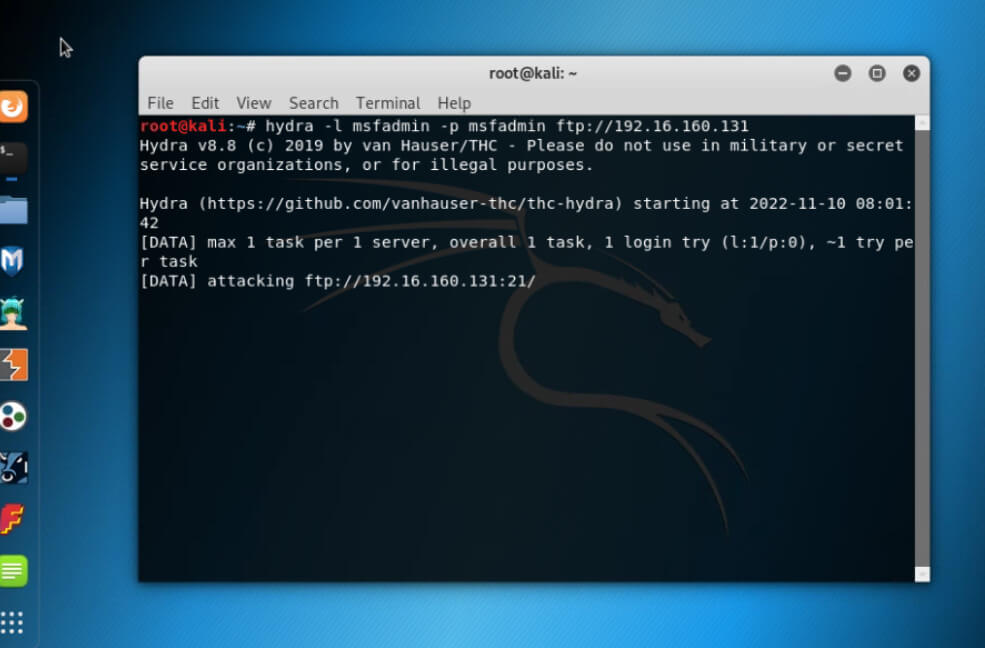
Usage of Brute Forcing FTP Username and Password.
Command:
hydra -l <username> -p <password> ftp:<target IP>Output:
Example #4
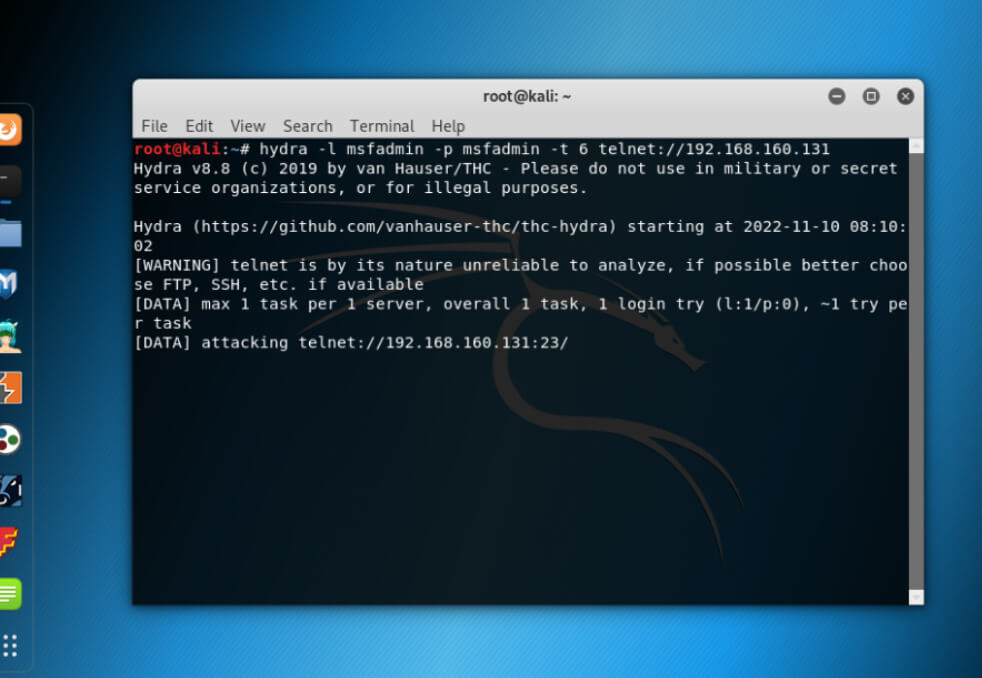
Usage of Brute Forcing Telnet Username and Password.
Code:
hydra -l <username> -p <password> telnet:<target IP>Output:
Conclusion
We have seen what Kali Linux Hydra means and how it can be installed on Kali Linux. As we have seen, there are 3 such ways to install a tool, the first being pre-installation of the Hydra tool, or by using Command Line, or by upgrading and then installing the latest version of the Hydra tool on Kali Linux. We have also gone through the Hydra login pages and its tools along with examples, above are some of the mitigation techniques that help to avoid brute force attacks.
Recommended Articles
This is a guide to Kali Linux Hydra. Here we discuss the introduction, installation, kali linux hydra login pages, and examples. You may also have a look at the following articles to learn more –