What is Zero Trust Network Access (ZTNA)?
The way companies conduct business has gone through a significant transformation. The modern workplace with remote teams and cloud computing demands has replaced the old ways of running IT systems. Perimeter-based security systems designed to defend corporate networks no longer protect assets since they were made for a different time. Zero Trust Network Access (ZTNA) represents the latest security technology available today. ZTNA transforms network security with its core belief that all access must be verified before being trusted. This article explores ZTNA basics and explains why it works better than standard security tools while showing how businesses use it today. You will understand through this blog why businesses need to use ZTNA and Fudo Enterprise solutions to build strong security today.
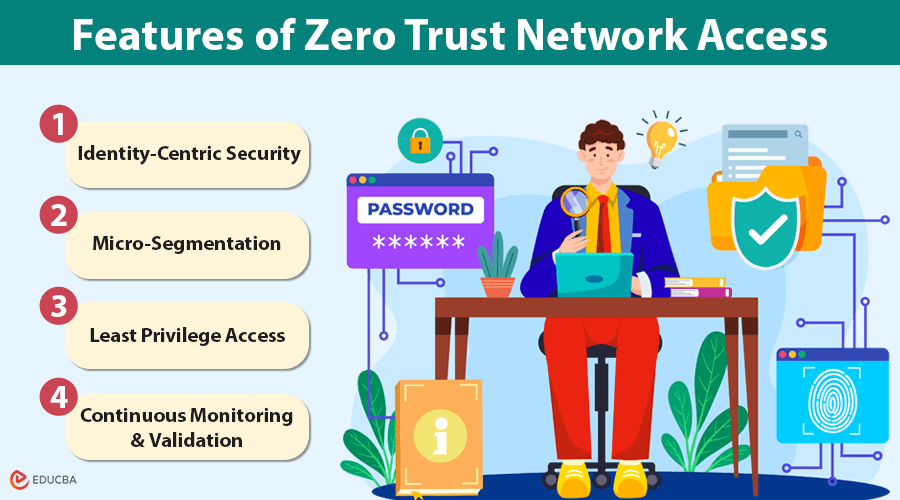
Features of Zero Trust Network Access
Zero Trust Network Access takes the modern stance of not trusting any user or device until proven secure, whether they are inside or outside the network. It uses many security methods to guard against the biggest network risks.
- Identity-Centric Security: ZTNA prioritizes authenticating users and devices over just granting access based on network locations. Each connection is identity-verified, adding an additional layer of assurance.
- Micro-Segmentation: ZTNA creates network security by splitting the network into separate areas that isolate each other. The system lets users reach only the application and data required to perform their assigned work. By segmenting access, you can effectively block most threats and minimize the impact of cyberattacks, keeping your data safer.
- Least Privilege Access: You are granted access only to what is necessary for your role, striking the perfect balance between security and minimizing the risk of unauthorized entry to sensitive systems.
- Continuous Monitoring and Validation: ZTNA continuously monitors your sessions, ensuring your access remains secure and trusted at all times. A device or user’s context—such as geographic location or unusual activity—is assessed continuously to detect risks in real-time.
ZTNA vs. Traditional VPNs
Businesses have used traditional VPNs to offer remote access for the last few decades. Although these networks have been used for many years, they depend on trust built through experience and work poorly in modern network situations. Now, let us look at VPN challenges and ZTNA advantages.
- VPN Challenges: VPNs grant users broad access to internal networks, creating vulnerabilities. If an attacker compromises one user’s credentials, they can traverse the network laterally, posing significant cybersecurity risks.
- ZTNA Advantage: With ZTNA, access is hyper-specific. It operates at the application or resource level, granting access only to pre-defined assets. This minimizes the attack surface and strengthens security by removing the concept of implicit trust.
Why is Zero Trust Network Access (ZTNA) Crucial for Modern Security?
Addressing Modern Security Challenges
- Combat Insider and Credential Threats: Insider misuse or compromised credentials are the leading causes of breaches. ZTNA limits what users can access, even with valid credentials, reducing the risk of insider attacks.
- Secure Cloud Applications: With businesses increasingly leveraging SaaS platforms and hybrid cloud environments, ZTNA enables selective and encrypted access to these applications.
- Minimize Lateral Movement: Even if attackers infiltrate the network, ZTNA’s segmentation restricts their movement, stopping them from compromising other valuable resources.
- Improved Visibility and Control: With real-time monitoring, you gain complete visibility into user activity and access history, giving you greater control over sensitive systems and data.
Supporting Business Agility and Remote Work
ZTNA supports flexible operations, a necessity in decentralized workplaces.
- Secure Remote Access: ZTNA ensures that employees, contractors, and third parties can securely access only the resources they need, no matter where they are.
- Enhanced User Experience: Its streamlined, low-friction approach combines security with user productivity, enabling seamless, secure access without cumbersome processes.
Meeting Compliance and Regulatory Requirements
Compliance requirements around data privacy and protection are becoming more stringent. ZTNA helps meet these requirements by implementing robust security postures that prevent unauthorized access, secure sensitive data, and generate audit trails that satisfy regulators and partners alike.
ZTNA in Action: How Fudo Enterprise Embodies Zero Trust Principles
Fudo Enterprise is a cutting-edge implementation of ZTNA principles, purpose-built to manage and protect privileged access. It enables enterprises to achieve optimal security while enhancing operational functionality.
Key Features of Fudo Enterprise as a ZTNA Solution
- Zero-Trust Access Control
- Just-in-Time (JIT) Access: Fudo ensures that users have access only when required and only for the specific duration necessary.
- Granular Access Management: Access is limited to predefined applications, servers, databases, or devices. Users can only access what is absolutely essential for their role.
- Multi-Factor Authentication (MFA): By integrating MFA for every user, Fudo guarantees layered protection when verifying identity.
- Agentless Architecture
- Easy-to-Deploy Infrastructure: Unlike agent-based solutions, Fudo’s agentless approach reduces implementation complexity and improves usability.
- Seamless User Experience: A frictionless, intuitive interface ensures productivity is not disrupted—all while fortifying network security.
- Session Monitoring & Recording
- Continuous Visibility: Track and record all privileged sessions, offering comprehensive logs for compliance and audit purposes.
- Real-Time Control: Admins can intervene in active sessions to stop suspicious activity or mitigate risks as they arise.
- AI-Powered Prevention
- Behavioral Analysis: Identify unusual patterns of user activity to detect threats proactively.
- Anomaly Detection: Machine learning ensures faster identification and resolution of missteps or malicious actions.
- Secure Credential Management
- Password Vault: Safeguard sensitive account credentials while reducing dependency on static passwords.
- Automated Credentials: Automate secure logins for systems without exposing users to sensitive credentials.
Benefits of ZTNA and Fudo Enterprise for Businesses
ZTNA, especially when implemented through Fudo Enterprise, can bring businesses a range of advantages, including but not limited to:
- Enhanced Security: Reduce the risk of cyberattacks, manage user behavior effectively, and safeguard sensitive data from breaches.
- Optimized Efficiency: Streamline access management to free up IT teams for strategic priorities, cutting down on manual tasks.
- Increased Productivity: Empower employees with quick, secure, and seamless access, improving daily workflows.
- Strengthened Compliance: Demonstrate a commitment to data security and transparency, ensuring confidence from regulators and customers alike.
- Cost Savings: Mitigate the financial impact of cybersecurity threats while enhancing operational cost efficiency.
Final Thoughts
Zero Trust Network Access stands as an operational need that businesses must adopt to secure their IT systems. ZTNA helps organizations defend against modern cyber dangers by reducing security weaknesses and building protection against future threats.
Fudo Enterprise is one of the most reliable and innovative platforms to implement ZTNA principles effectively. Its easy deployment, agentless architecture, and robust feature set empower businesses to protect their most sensitive systems and maintain a competitive edge. Explore a future-proof approach for your business today. Learn more about Fudo security and secure modern operations with confidence.
Recommended Articles
We hope that this article on “Zero Trust Network Access” has provided you with valuable insights into the importance of this security approach. You can view EDUCBA’s recommended articles for more information:


