Introduction to Access Token
Access tokens are critical components of modern cybersecurity, acting as credentials to authenticate and authorize users or programs within digital networks. These tokens, which serve as proof of identification, are critical to enabling secure access to sensitive data and services. Access tokens are gatekeepers in modern authentication and authorization, confirming users’ identities and providing particular permissions. They prevent unauthorized access, improve user experience through seamless logins, and enable streamlined control over protected resources. Access tokens are critical components of digital security measures in today’s interconnected and data-driven internet environment.
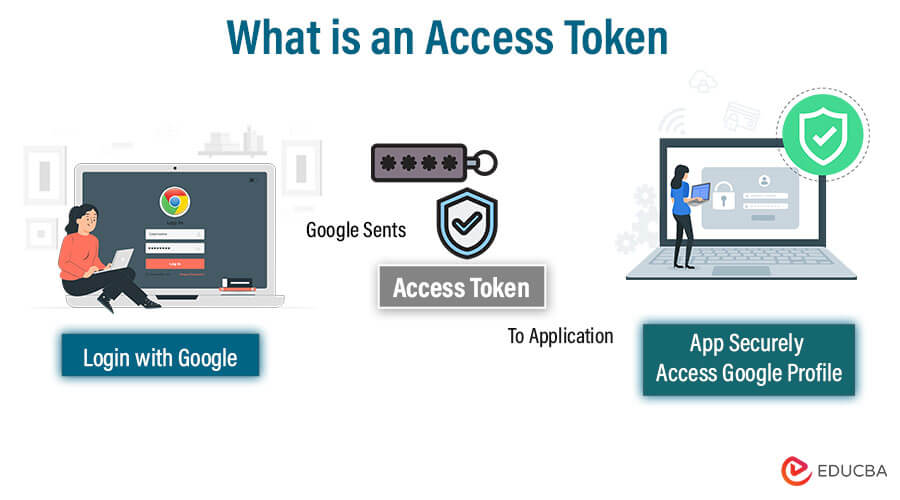
Table of Contents
- Introduction to Access Tokens
- Understanding Authentication
- Authorization and Access Control
- Structure of Access Tokens
- Generation and Issuance
- Token Types
- Bearer Tokens
- Lifetime and Expiry
- Scopes and Permissions
- Access Token Usage
- Security and Best Practices
- Access Token in Real-world Applications
Understanding Authentication
Authentication is a crucial aspect of access tokens. It ensures that the user or application requesting access to protected resources is legitimate. Access tokens play a significant role in authentication by providing a secure and uniform way of verifying a user’s or application’s credentials. When a user or application requests access to a resource, they present an access token as evidence of their identity to an authentication server or system. The server then verifies the token’s authenticity, ensuring it was not tampered with and issued by a trusted authority. Once the token is validated, it confirms the requester’s identity, and access is granted based on the permissions associated with the token.
Authentication with access tokens provides a few benefits:
- Enhanced Security: Access tokens reduce the risk of unauthorized access and exposure of sensitive user credentials, such as passwords, during the authentication process.
- Efficiency: Tokens are usually short-lived and self-contained. They allow for efficient and secure authentication without repeated username and password inputs.
- Single Sign-On (SSO): Access tokens facilitate single sign-on systems, allowing users to access multiple applications and services with single credentials.
- Interoperability: The industry widely adopts access tokens, which are compatible with various platforms and services, making them a versatile solution for authentication in diverse digital environments.
Authorization and Access Control
Authorization and access control are vital aspects of digital system security, especially when it comes to securing sensitive resources. These concepts ensure that only the right users or applications can access specific resources.
Differentiating between Authentication and Authorization
| Section | Authentication | Authorization |
| Definition | Verifies the user’s or application’s identity. | Determines what authenticated users/applications can do. |
| Purpose | Ensures the user is who they claim to be. | Grants specific permissions based on the user’s role. |
| Validation | Involves validating credentials (e.g., username, password). | Involves verifying permissions and roles associated with the user. |
| Focus | Identity verification. | Permission assignment and access restrictions. |
| Occurs | First step in the authentication process. | Follows authentication, determining actions allowed. |
Access tokens are a key element of the authorization process, acting as a link between authentication and granting permissions.
Let’s explore how access tokens play a vital role in authorization:
- Identity Verification: Access tokens, obtained through the authentication process, contain information about the authorized user or application. This information, commonly known as claims or attributes, aids the authorization system in recognizing who is making a request.
- Permission Mapping: Access tokens carry data that specifies what the authorized entity is permitted to do. These permissions and access rights are usually encoded as claims within the token.
- Token-Based Decisions: When an authorized entity presents an access token to access a resource, the authorization system assesses the token’s claims to make decisions. It verifies whether the entity has the necessary permissions to execute the requested action or access the resource.
- Access Control Lists (ACLs): Access tokens help maintain access control lists, which define who can access specific resources and perform certain actions. The tokens are a reference point to enforce these lists, ensuring only authorized users or applications can interact with particular assets.
Structure of Access Tokens
Let’s break down the components of an access token and explore the types of data stored in them in detail:
Components of Access Token
1. Header: The header typically consists of two parts: the type of token, usually “JWT” (JSON Web Token), and the signing technique used, such as HMAC SHA256 or RSA. The header is base64Url encoded to produce the first part of the JWT.
2. Payload (Claims): The payload contains claims, typically representing statements about an entity (usually the user) and additional data.
Standard claims: Here are some standard claims that are typically included in a token:
- Issued At (iat): This timestamp shows when the token was issued.
- Expiration Time (exp): This timestamp indicates when the token expires and should no longer be accepted for processing.
- Issuer (iss): The entity that issued the token, such as an authorization server.
- Subject (sub): This is the identifier for the user or application the token is intended for.
- Audience (aud): This refers to the recipients or audience for the token, such as the resource server that should accept the token.
Custom Claims: Additional information about the user, such as responsibilities or application-specific data. These claims provide context for authorization decisions.
3. Signature: The signature is created by combining an encoded header, an encoded payload, a secret key (for HMAC techniques), and a signing algorithm. The signature confirms that the sender of the JWT is who they claim to be and that the message has not been modified along the way.
Types of Data Stored in Access Tokens
- Claims: Claims provide information about the authenticated entity, such as user roles, email addresses, or other user-specific details. Example: {“sub”: “user123”, “name”: “John Doe”, “role”: “admin”}
- Scope: Scopes define the specific permissions or actions the token holder can perform. Example: scope=read write
- Audience (aud) Claim: Indicates the intended recipients of the token. It specifies the resource server(s) that should accept the token. Example: { “aud”: “api.example.com” }
- Issuer (iss) Claim: Identifies the entity that issued the access token. It could be an authorization server or an identity provider. Example: { “iss”: “auth.example.com” }
- Token Type (typ) Claim: Specifies the type of token. For access tokens, it is set to “JWT.” Example: {“typ”: “JWT”}
- Expiration Time (exp) Claim: It represents the timestamp when the token will expire, after which it should not be accepted. Example: {“exp”: 1677640071 }
Generation and Issuance
A user or application must obtain an access token to access a protected resource. The process of access token generation involves authentication of the user or application, verification of their identity by an authentication provider, and token request validation and issuance by an authorization server.
Here’s a breakdown of the process:
- Authentication: To authenticate themselves, a user or application must provide valid credentials like a username and password or use an external authentication method like OAuth 2.0.
- Authentication Provider: Once the user/application is authenticated, the authentication provider verifies their identity and generates a token request sent to an authorization server. The authentication provider can be an identity management system, Google, Facebook, or an organization’s internal system.
- Authorization Server: The authorization server validates the token request received from the authentication provider, and if the authentication is successful, it generates an access token.
- Access Token: The authorization server’s access token typically consists of a header, a payload with claims, and a signature. The authenticated user or application receives the token and uses it to access the protected resource.
Role of Authentication Providers
- Identity Verification: Authentication providers are in charge of confirming the identity of users or applications. They ensure that the entity requesting access to a resource is legitimate.
- Credential Validation: They validate the provided credentials (e.g., username and password) to ensure they match the stored user information.
- Multi-Factor Authentication (MFA): Many authentication services provide MFA, which increases security by demanding multiple forms of authentication.
Role of Authorization Servers
- Access Control: Authorization servers control access and determine which activities or resources the authenticated entity can access.
- Token Issuance: They generate access tokens that encapsulate the permissions and claims associated with the authenticated entity.
- Token Management: Authorization servers are also in charge of handling token lifecycles, which include token issuance, validation, and revocation.
Token Types
Let’s differentiate between some common types of access tokens and explore their details:
1. JWT (JSON Web Token)
Explanation: JWT is a compact, self-contained format for securely sending information between parties as a JSON object. It consists of a header, payload, and signature, providing an organized mechanism for conveying identification and permissions.
Use Cases:
- JWTs are extensively used in web applications and APIs for user authentication and authorization.
- They enable single sign-on (SSO) and secure information transmission between systems.
Strengths:
- Self-Contained: JWTs comprise data and a digital signature, making them simple to verify and secure.
- Versatility: They can hold a variety of claims and are compatible with various platforms and programming languages.
- Reduces Database Queries: JWTs can be easily self-verified. They minimize the need for frequent database searches to validate tokens.
2. OAuth Tokens
Explanation: OAuth tokens are an integral part of the extensively utilized OAuth 2.0 protocol, which facilitates delegated authorization, and they are one of the main differentiators from other protocols like SAML. OAuth tokens are an integral part of the extensively utilized OAuth 2.0 protocol, which facilitates delegated authorization. They come in different formats, such as Bearer Tokens and MAC Tokens, and their primary function is to grant applications limited access to resources.
Use Cases:
- OAuth tokens primarily find use in scenarios where third-party applications require access to user data, such as social media logins and API access.
- They allow for precise access control to user data or services, ensuring that users have complete control over what third-party apps can access.
Strengths:
- Delegated Authorization: OAuth tokens enable users to provide particular permissions to third-party applications without revealing their credentials.
- Revocable: Users can revoke access to their data anytime, boosting security and privacy.
- Widely Adopted: OAuth 2.0 is widely adopted as a standard protocol by major digital businesses and platforms, making it adaptable and well-supported.
3. Bearer Tokens
Explanation: Bearer Tokens are an OAuth token type. They are usually just random strings without information about the token.
Use Cases:
- Bearer tokens are frequently used in API authentication, embedding them in HTTP headers to gain access to restricted services.
- They make it simple for apps to access resources on behalf of users without revealing their credentials.
Strengths:
- Bearer tokens are simple to implement and function well in cases where security depends on the transport layer (e.g., HTTPS).
- Efficiency: They do not require extensive processing to decode and verify, making them suited for high-throughput scenarios.
4. SAML Tokens (Security Assertion Markup Language)
Explanation: SAML tokens are XML-based tokens that allow parties to exchange authentication and authorization data.
Use Cases:
- SSO systems frequently use SAML tokens for cross-domain authentication.
- Users can log in once and access various services or applications without re-entering credentials.
Strengths:
- Cross-Domain SSO: SAML tokens are well-suited for establishing trust between domains, allowing for smooth single sign-on.
- Fine-Grained Permissions: They can store precise information about user attributes and permissions, allowing for more flexible access control.
Bearer Tokens
Users or applications can authenticate and authorize access to particular resources or execute specific activities using bearer tokens, a form of access token.
Bearer tokens get their name from the fact that they often serve as proof of authentication and do not require any further proof of identity, such as a digital signature or client certificate. The possession of the token is sufficient to gain access to the associated resources, making them relatively simple to use.
Bearer tokens are well-known for their simplicity. Because of their ease of use and implementation, they are a popular choice for securing APIs and online services. They can be instantly generated and presented in HTTP requests without complicated encoding or parsing.
Security Concerns
Bearer tokens, while simple, come with security challenges:
- Token Leakage: If a bearer token is intercepted or stolen, anyone who has it can use it until the token expires. This is a serious security concern.
- No Inherent Context: Bearer tokens lack inherent context information about the user, client, or rights. This can make fine-grained access control and auditing difficult to implement.
- Data Sensitivity: Since bearer tokens are often sent in HTTP headers, server logs can potentially log them, exposing sensitive information.
Lifetime and Expiry
Tokens such as access tokens, used in authentication and authorization systems, have a defined lifetime and expiry period. Understanding the importance of token expiration is crucial for maintaining security and access control.
Importance of Token Expiration
- Security: Token expiration is a fundamental security measure. Limiting a token’s lifetime reduces the window of opportunity for attackers to exploit stolen or leaked tokens. Even if a token is compromised, it becomes useless once it expires.
- Access Control: Expiring tokens ensure that the system periodically re-evaluates a user’s access, particularly in cases where a user’s permissions change or when the system needs to periodically revalidate a user’s session, as tokens often carry information about the user’s identity and permissions.
- Resource Management: Tokens, especially in scenarios like API authentication, can create overhead on resource servers. Expiring tokens help manage server resources by ensuring unused tokens do not linger indefinitely.
- User Experience: Token expiration can be used as a part of a single sign-on (SSO) system to prompt users to re-authenticate, which is essential for security and provides a smoother user experience.
Token Refresh and Reissuance
To extend a token’s validity or issue a new one, you employ several mechanisms. These include Token Refresh, Reissuance, and Revocation.
- Token Refresh: Many systems use refresh tokens in conjunction with access tokens. Access tokens have a relatively short lifespan, but refresh tokens have a longer duration. When an access token expires, users can use the refresh token to obtain a new one without re-entering credentials. Scenarios like API access often employ this process in OAuth 2.0.
- Reissuance: In some cases, systems reissue tokens after their expiration. This happens when a user explicitly re-authenticates or when a system automatically renews a token. The updated expiration information typically generates the new token.
- Revocation: A token can be revoked if it is compromised or no longer needed. Revocation involves invalidating the token before its expiration. Typically, you accomplish this by making an API call to the authorization server or identity provider. Resource servers should not accept revoked tokens.
Scopes and Permissions
In the context of authentication and authorization protocols like OAuth 2.0, “scopes” define the specific actions or resources that an access token allows the client (user or application) to access.
Scopes serve as a means to limit the extent of access granted by the access token. The resource server defines them, and the client requests them during authentication.
How Access Tokens Grant Specific Permissions:
1. Scope Request: When a client requests an access token, it includes the desired scopes in the authorization request. These scopes indicate the specific actions or resources the client seeks access to.
2. Authorization and Token Issuance: The authorization server evaluates the requested scopes, making sure they fall within the client’s allowed permissions. If approved, the authorization server issues an access token with the specified scopes embedded in it.
For example: when a user logs into a social media app, the app might request scopes like “read_profile” and “post_updates.” The access token issued to the app will have these scopes embedded.
3. Access Token Usage: When the client accesses a protected resource (like an API endpoint), it presents the access token, including the scopes, to the resource server.
4. Access Control: The resource server checks the scopes in the access token to determine if the client has the necessary permissions for the requested action. If the scopes match the required level of access, the resource server grants access to the specific resource or allows the requested action.
Example: If the API endpoint requires the “read_profile” scope, the resource server validates the access token to ensure it includes this scope. The client can read the user’s profile information if the token has the required scope.
Access Token Usage
Access Token Usage in API Requests
Access tokens are crucial in authenticating and authorizing clients, such as users or applications, when interacting with protected resources, including web services or APIs. HTTP requests usually include these tokens to gain access to the resources. Here’s how users utilize access tokens in API requests:
- Authentication: The client, whether a user or an application, first authenticates to the authorization server. After successful authentication, the authorization server issues an access token.
- Token Inclusion: When accessing a protected resource, the client includes the access token in the HTTP headers of its requests. The most common way to include the token is in the “Authorization” header, using the “Bearer” authentication scheme.
- Resource Server Validation: The resource server, which hosts the protected resource, receives the client’s request and the access token in the headers.
- Access Token Validation: The resource server validates the access token by checking its authenticity, expiration, and the permissions it grants.
- Access Control: After successful validation, the resource server allows or denies access to the requested resource or performs the specified action.
Sending Access Tokens in HTTP Headers
1. Authorization Header (Bearer Token): The “Authorization” header of an HTTP request commonly includes access tokens. These tokens are prefixed with the word “Bearer” to indicate the type of token being used.
Example:
GET /api/resource HTTP/1.1
Host: example.com
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9…
2. API Key Header: In some cases, instead of bearer tokens, users employ API keys. They include these keys in a dedicated header for authentication.
Example:
GET /api/resource HTTP/1.1
Host: example.com
X-API-Key: your-api-key
3. Cookie Header: Web applications can store access tokens as cookies and send them in the “Cookie” header. This is common in single sign-on (SSO) systems.
Example:
GET /api/resource HTTP/1.1
Host: example.com
Cookie: access_token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9…
4. Custom Headers: Users can also use custom headers to transmit access tokens depending on the system or API design.
Example:
GET /api/resource HTTP/1.1
Host: example.com
X-Access-Token: your-access-token
Security and Best Practices
Security and Best Practices for Access Tokens:
- Use HTTPS: Always use HTTPS to transmit access tokens, encrypt data, and prevent eavesdropping or man-in-the-middle attacks.
- Token Expiration: Implement short token lifetimes and utilize token expiration to limit the window of opportunity for attackers.
- Token Revocation: Provide mechanisms for revoking access tokens when they are no longer needed or compromised.
- Token Storage: Store tokens securely on client devices and avoid exposing sensitive information in logs or other public records.
- Token Scoping: Use scopes to limit the access granted by tokens. Grant the least privilege necessary for the client to perform its tasks.
- Refresh Tokens: Implement refresh tokens for long-lived sessions. Refresh tokens can obtain new access tokens without requiring user credentials again.
- Token Validation: Validate access tokens on the server side for authenticity, integrity, expiration, and proper scopes before processing any requests.
- OAuth 2.0 Implicit Flow: Avoid using the OAuth 2.0 Implicit Flow due to security risks. Instead, I prefer the Authorization Code Flow with PKCE (Proof Key for Code Exchange) for better security.
- Client Authentication: Ensure proper client authentication, especially for confidential clients. Use client secrets or private/public key pairs for secure authentication.
- Standard Libraries: Use standard libraries and well-vetted security solutions to handle authentication and authorization processes whenever possible.
Access Token in Real-world Applications
Access tokens are an essential component in various real-world applications. They provide secure access to resources and enhance user experience. Below are some practical use cases from different industries:
1. Social Media Platforms (e.g., Facebook, Twitter):
Use Case: Access tokens enable third-party applications to access user data and post updates on behalf of users.
Example: Social media platforms use OAuth tokens to securely integrate with other services, allowing users to sign in to those services using their social media accounts.
2. Online Marketplaces (e.g., Amazon, eBay):
Use Case: Access tokens enable API calls to manage product listings, process orders, and retrieve customer data.
Example: Online sellers use access tokens to update product details and track sales, ensuring secure transactions and data integrity.
3. Financial Services (e.g., Banking, Payment Gateways):
Use Case: Access tokens authenticate users and authorize fund transfers, account balance checks, and payment processing.
Example: Mobile banking apps use access tokens to let users perform financial transactions, ensuring secure financial operations.
4. Healthcare Systems (e.g., Electronic Health Records):
Use Case: Access tokens provide secure access to patient records, allowing authorized healthcare professionals to view and update patient information.
Example: Authorized personnel can securely access medical records by utilizing access tokens to integrate various healthcare systems in hospitals.
5. Internet of Things (IoT) Devices:
Use Case: Access tokens authenticate devices and allow them to interact with cloud services, enabling real-time data exchange and control.
Example: Smart home devices use access tokens to securely communicate with cloud servers, ensuring secure control and monitoring of home appliances.
6. Travel and Hospitality (e.g., Booking Platforms):
Use Case: Access tokens facilitate secure interactions between booking platforms, hotel systems, and payment gateways for reservations and payment processing.
Example: Travel booking apps use access tokens to authenticate users and authorize booking changes, ensuring a smooth and secure travel experience
7. Educational Platforms (e.g., Learning Management Systems):
Use Case: Access tokens authenticate students, teachers, and administrators, controlling access to course materials, assessments, and administrative features.
Example: Online learning platforms use access tokens to verify user identities, ensuring only enrolled students and authorized faculty members can access course content.
Conclusion
Access tokens are a crucial component of modern authentication and authorization systems. They offer a secure and organized approach to managing access to resources and services, ensuring security and user convenience. A comprehensive understanding of their use, best practices, and practical applications is essential for developing robust and dependable digital systems. In conclusion, access tokens play a fundamental role in digital security, and it is imperative to comprehend their significance for building secure and reliable systems.
Recommended Articles
We hope that this EDUCBA information on “What is an Access Token” was beneficial to you. You can view EDUCBA’s recommended articles for more information.

