Updated April 14, 2023
Introduction to Ansible Authorized_key
In Ansible, to execute tasks and plays on remote target machines, we need to either make the connection password less or provide password/keys in real-time while running a playbook. Ansible uses native OpenSSH as its default connection method. By default, Ansible considers that we are using SSH keys to connect to target remote machines.
To work with SSH we need either passwords or SSH key of the concerned user account. Ansible has a very useful module named authorized_key to add or remove authorized keys for concerning user accounts on remote machines. In this article, we will try to learn about many methods and options to use this module.
What is Ansible Authorized_key?
An SSH key pair is a combination of two keys which are public and private. The private key is kept locally and the public key is shared with remote hosts to which we want to connect. This combination is used for achieving asymmetric encryption, it means is something is encrypted with one key of this combination, then another key of combination is used to decrypt that. In Ansible, we are using OpenSSH to make SSH connections to remote target nodes.
We can either set up SSH connection using keys with remotes hosts by either Linux commands or Ansible itself using a module named authorized_key. This module can identify key files for user accounts from provided locations and copy to remote target machines on the specified path (when unset, default is ~/.ssh/authorized_keys)
How Does Ansible Authorized_key work?
To make this the SSH connection using keys in Ansible. We must follow steps, which can be done in multiple ways which we will discuss in this document.
- Generate a key pair containing private and public keys as id_rsa and pub respectively.
- These will be generated under ~/.ssh directory by default, if not set otherwise.
- Send public key pub to remote hosts by copying it in file ~/.ssh/authorized_keys at end of the file.
- Make ssh connection to the remote host and give yes when it asks to make entry of fingerprint of target hosts to ~/.ssh/known_hosts. If you do not do this, then every time the SSH connection is made, the system will ask to add
This can either be done by Linux command or by using the Ansible authorized_key module. In this article, we see this Ansible module and its parameters with available options. Some of those are described below.
- key: The SSH public key. It accepts a string or
- path: Path to authorized_keys file, default is ~/.ssh/authorized_keys.
- state: should the key be present or absent from file ~/.ssh/authorized_keys. The default is present.
- user: The username on remote hosts whose authorized keys file will be modified.
- validate_certs: When using https url for the source of the key file, this is used to set whether to allow validating certificate for that source site or not. Default is Yes
- exclusive: This is set to remove all other non-specified keys from the authorized key Default is no.
- comment: To specify the comment on the public key, this is useful in cases where you are using GitHUB/GITLAB for managing your
- manage_dir: This option is set to tell the module to manage the directory of authorized_key
The default is yes. Note that when using the parameter path, make sure you set no for manager_dir.
Example to Implement Ansible Authorized_key
Now by using examples, we will try to learn about the Ansible authorized_key module and some other ways to use keys to setup successful connection to remote target hosts, which you might have to use in day to day operations. We will take some examples, but before going there, we first understand our lab, we used for testing purpose.
Here we have an Ansible control server named ansible-controller and two remotes hosts named host-one and host-two. We will create playbooks and run ansible commands on the ansible-controller node and see the results on remote hosts.
Example #1
Now in this example, we will use an Ansible playbook to create a key combination for a user. Then copy the public key from Ansible controller node to remote target nodes in ~/.ssh/authorized_keys file using Ansible authorized_key
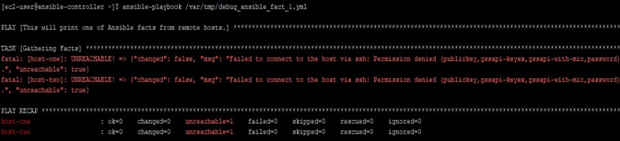
For this, we have made a setup. Here currently our playbooks are failing because we do not have a successful connection to remote target nodes. SSH keys are missing for ec2-user on controller machine and this user’s entry is also mission on remote target machines.
Code:
ansible-playbook /var/tmp/debug_ansible_fact_l.yml
Output:
Now we create SSH public and private keys on the controller node using below command.
Code:
ssh-keygen -q -b 2048 -t rsa -N "" -f ~/.ssh/id_rsa
ls -l .ssh/id_rsa*
Output:
This will create 2 files like below: –
Example #2
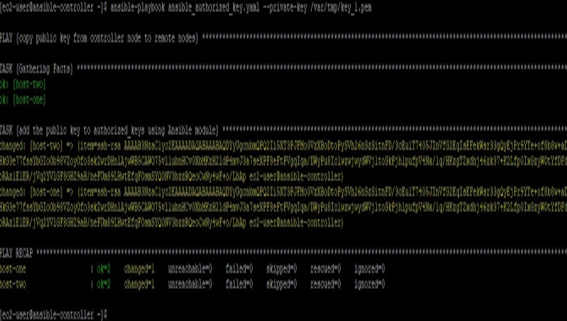
Now we create a playbook like below which will use Ansible authorized module to copy the public key file to remote hosts: –
Code:
name: copy public key from controller node to remote nodes hosts: all
tasks:
name: add the public key to authorized_keys using Ansible module authorized_key:
user: ec2-user state: present key: '{{ item }}'
with_file:
- ~/.ssh/id_rsa.pub
Example #3
Now execute this playbook, but to execute this playbook, we need to pass a private key to connect to target remote hosts on the command line with an ansible-playbook command or we can use parameters to ask for a password.
In the below example, on the command line with ansible-playbook, we are using a private key to connect to the remote target node, this key’s public key is already present in authorized keys on remote target machines.
By running this playbook, we are making entries in ~/.ssh/authorized_keys of remote target machines.
Code:
ansible-playbook ansible_authorized_key.yaml --private-key /var/tmp/key_l.pem
Output:
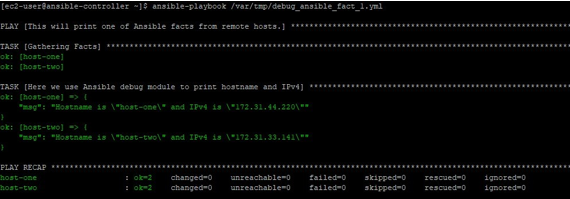
Now when we run the same Ansible playbook which we ran previously, it will run smoothly like below. Because now we have the public key of the controller node copied to remote target node’s authorized keys file, this has made SSH password less from the controller to remote nodes.
Output:
Conclusion
Managing all your infrastructure from a single control can be quite risky if your connection method is not secure, but SSH is a very secure way to make connections, and SSH keys play an important role to make connection to remote target nodes. Managing keys is simplified with modules like authorized_key. So we should need to use it wisely. So learn it first and then use it.
Recommended Articles
This is a guide to Ansible Authorized_key. Here we discuss an introduction to Ansible Authorized_key, syntax, how does it works, and examples to implement. You can also go through our other related articles to learn more –