Updated March 29, 2023
Introduction to Ansible Iptables
Ansible iptables is a module that is used to create, verify, and maintain the IP table packet filter rules in the kernel of Linux target machines. This module manipulates the existing rules from system memory which you would have been doing by iptables and ip6tables commands. This does not save any rule or load any rule. For example, in Linux, iptables represent firewall rules, and a firewall rule represents the criteria for a target and a packet. This module handles the individual rules; if you need advanced level changing of rules, then you should better use templating in Ansible.
In this article, we will learn about Ansible Iptables and see some practical implementations of it.
Explaining the Ansible Iptables
Ansible Iptables module is the same as you use Linux commands iptables and ip6tables because internally, it invokes those commands while executing any task on remote target machines. Like any other Ansible module, we have a set of parameters, their acceptance, and default values in this Ansible module. You must use a combination of these to create a required rule. Also, you shall be wary of the default values as you might not be mentioning all parameters in a play or task, but due to the default behavior of a parameter, it will anyway be realized and applied. So, do remember these when using the Ansible Iptables module.
- action: –available options are appended and insert. The default is to decide whether to insert on top or append at the bottom.
- chain: –This is to tell which iptables chain will be modified.
- comment: – Comment to add with the rule.
- destination: –This is to specify the destination in a rule; this can be an IP, hostname, network range, etc.
- destination_port: –This is to specify the destination or destination port range. Acceptable values are port numbers as well as the service name.
- uid_owner: – This is to tell which user to use when doing a match in the owner rule.
- to_source: – This is to specify the source to be used.
- to_ports: – This is to specify the destination port range or a destination port.
- to_destination: –This specified the destination address to use.
- table: –Acceptable values are filter, nat, mangle, raw, and security. This is to specify the packet matching table on which command will work on. The default filters.
- state: –Acceptable values are absent and present. The default is present. This is to specify whether to add or remove a rule.
- src_range: –This is to specify the source IP range to match.
- source: –This is to specify a source that can be an IP, hostname, network range, etc.
- source_port: –This is to specify the source or source port range. Acceptable values are port numbers as well as the service name.
- rule_num: –To specify the number at which to Insert the rule. This works with action=insert.
- reject_with:-To specify the error when rejecting a package.
- protocol: –This is to specify the packet or protocol to check. This can be tcp, udp, icmp, esp, ah, udplite, sctpor
- policy: –Acceptable values are ACCEPT, DROP, QUEUE, and RETURN. This is to set the policy for the given target.
- out_interface: –This is to specify the interface via which a packet will be sent.
- match: –
- log_prefix: –This is to specify a log text for the rule.
- ip_version: – whether IPv4 or IPv6
- in_interface: –This is to specify the interface via which a packet will be received.
- gateway: –This is to specify the IP address where to send cloned packets. This only works when the JUMP parameter is set to TEE.
- Jump: – This is to specify what shall be done when the packet matches a rule.
- flush: –This is to specify the table and rule chains to be flushed. If nothing is specified, then all tables will be flushed.
How Does Ansible Iptables Works?
Ansible iptables modules have syntax like below and are written in YAML format (like any other Ansible module). We usually need escalated privileges for manipulating rules, so you might need to use Ansible to run this module’s task if you are not rooted, the user. For non-modifying operations, you can use non-root users to run this module. The syntax with ansible become will look like below: –
---
- hosts: <hostlist>
tasks:
- iptables:
chain: <chain to modify>
source: <source address>
jump: <rule target>
become: yes
In the next section, we will see some practical examples and their real-time usage. Also, by seeing the output of playbooks, we will try to understand how it works.
Examples of Ansible Iptables
Now by using examples, we will try to learn about the Ansible iptables module, which you might have to use in day-to-day operations.
First, let me introduce you to our lab environment. We have an Ansible controller node named ansible-controller. Also, as target remote machines, we have one Linux-based node named as host-one. We will run the Ansible command and playbooks on the Ansible control node ansible-controller and try to do changes on the target remote machine.
In this example, we have a playbook like below, where we are blocking an IP and specifying all packages to be dropped from it.
---
- hosts: host-one
tasks:
- name: Check the current iptable
shell: iptables --list
register: var_output
- name: This will display the current IP TABLEs
debug:
var: var_output.stdout_lines
- name: Here we are creating a rule to DROP packages from a sample IP
iptables:
jump: DROP
chain: INPUT
source: 192.168.0.250
- name: Check the current iptable
shell: iptables --list
register: var_output_1
- name: This will display the current IP TABLEs
debug:
var: var_output_1.stdout_lines
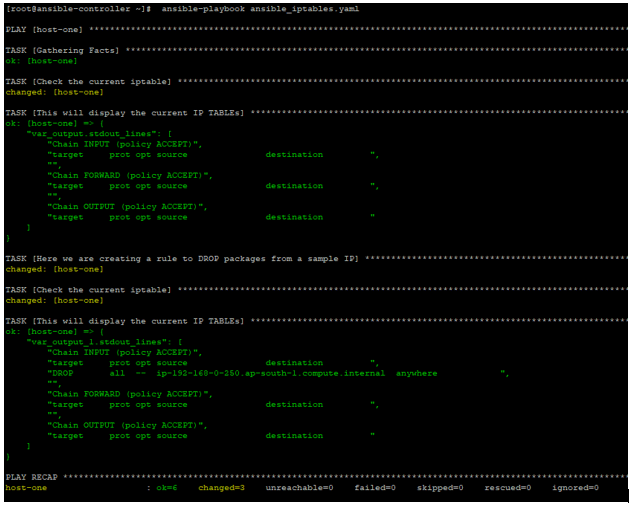
Now running it like below: –
ansible-playbook ansible_iptables.yaml
Now in the below output, you can see the iptables before and after. After the rule setup, we have all packages dropped from this IP.
Conclusion
As we saw in this article, Ansible Iptables is an important module that enables you to work on iptables remotely via Ansible. But you must only use it when you have good knowledge of Linux firewall and Ansible iptables; otherwise, you will end up in a mess of firewall rules and tables. So learn it first and then use it.
Recommended Articles
This is a guide to Ansible Iptables. Here we discuss How Does Ansible Iptables Works and Examples along with codes and outputs. You may also have a look at the following articles to learn more –