Introduction to Ansible Vault
Ansible Vault, a cornerstone of Ansible, offers a comprehensive approach to safeguarding sensitive data within automation workflows. It effectively protects confidential information, including passwords, API tokens, and configuration details, by leveraging robust encryption and password-based authentication. This powerful tool mitigates the risks associated with unauthorized access and potential security breaches, ensuring the confidentiality and integrity of sensitive data. Ansible Vault seamlessly integrates with Ansible playbooks and variable files, enabling secure management and utilization of secrets throughout the automation process. By incorporating Ansible Vault into DevOps practices, organizations can significantly enhance their security posture, safeguarding their critical infrastructure and sensitive information from potential threats, and thereby improving their overall operational efficiency.
What is Ansible Vault?
To keep the sensitive data, save and protected, we basically have two options listed below: –
- Use a third-party Key Managements Service and store the sensitive information on the cloud. The kind of tools is like Amazon’s AWS Key Management Service and Microsoft Azure Key Vault.
- Use the Ansible Vault to protect any structured data file.
In this article, we will discuss the Ansible Vault. Which operates via a command-line tool called “ansible-vault”. This command is used to encrypt, decrypt, rekey, view, edit and create files.
Ansible-vault is the command-line tool, which is used on the Ansible server to do below tasks
- Encrypt an existing important file.
- Decrypt an encrypted file.
- View an encrypted file without breaking the encryption.
- Edit an encrypted file and maintain its encryption and secret key/ password.
- Create a new encrypted file.
- Rekey or reset the password of an already encrypted file.
How Does Ansible Vault Work?
Few points which are needed to add to your knowledge, by which you can understand how Ansible Vault works: –
- Ansible Vault does not implement its own cryptographic functions but uses an external Python toolkit. So, you must have python in your system. Which is also a pre-requisite for working Ansible Environment.
- Files are protected with symmetric encryption using AES256 with a password as the secret key. This encryption may be 128-bit AES in older versions of Ansible.
- Using ansible-vault with option edit will always rewrite the file and can create issues when you have some version control system on the same files. Better to use option view when you want to only read the file.
- You should have the same passwords for files encrypted under a role. This is a better practice and more practical otherwise it will be difficult and manage more passwords and such files. Otherwise use labels by vault-id when having multiple files encrypted but this is dependent on your ansible version.
- You can use a vault password file as well when you have encrypted files while running a playbook or any other ansible operations. You should use ask-vault-pass and vault-password-fileparameters to provide passwords and password file respectively.
Examples of Ansible Vault
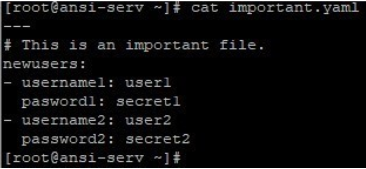
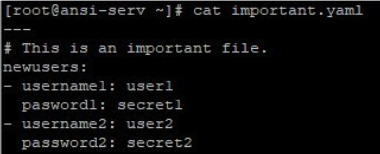
Below are few samples on how these operations work, here we are working on a sample file named “important.yaml”, /etc/ansible/hosts, playbook1.yaml and secret_important.yaml (just as an example). Below are the contents of this file.
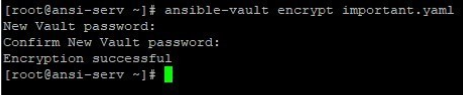
1. Encrypt the important file. Using ansible-vault like below will ask you for a password and reconfirm it. You must remember this password otherwise you will not be able to recover this file.
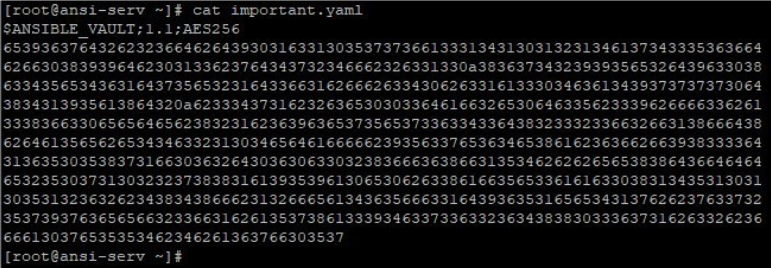
Now if you try to read this file. You will find, the file is encrypted but contents will still be in ASCII text.
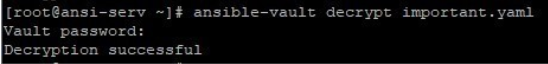
2. Decrypt the file. Using ansible-vault like below will ask you for the password you gave while encrypted it.
The same file will now be in plain text now.
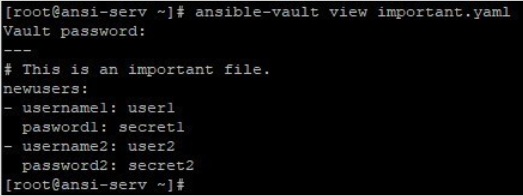
3. View the encrypted file. Using ansible-vault like below will ask you for the password and you can read the file.
4. Edit an already encrypted file without breaking its encryption and keeping the same password. By using ansible-vault like below will ask you for its password and then open the file by default editor.
The default editor, which opens will be vim but can be changed by setting and exporting the $EDITOR
environment variable.
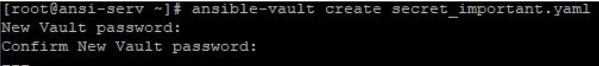
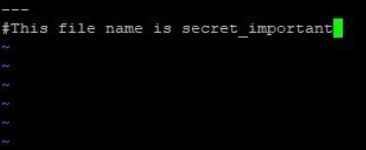
5. Create a new encrypted file. In this example you will see, using ansible-vault like below to create a new encrypted file secret_important.yaml.
This will open the secret_important.yamlfile like below, by default editor.
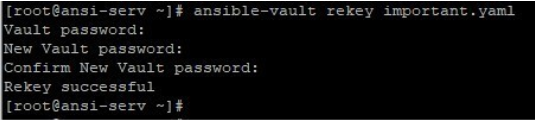
6. Rekey an already encrypted file, using ansible-vault like below to rekey or reset the password or secret key of a file.
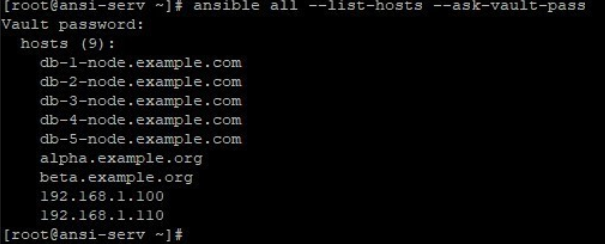
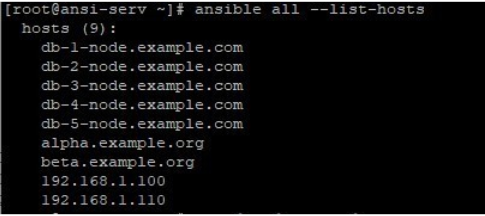
7. Using ask-vault-pass, while running some Ansible operation, like listing all hosts in the mentioned inventory file
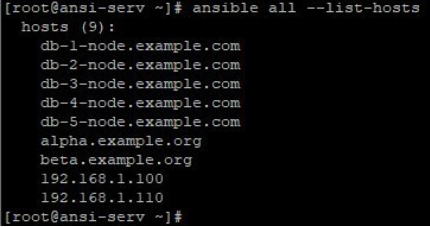
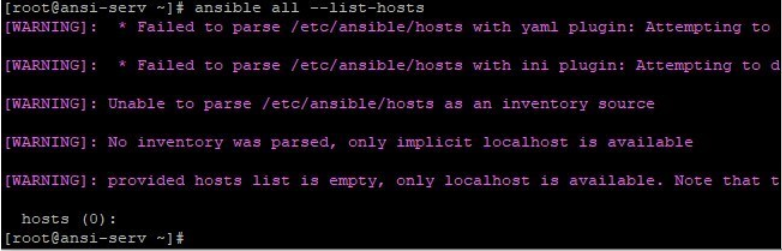
Here in this example, we have our default inventory file /etc/ansible/hosts. If this file is not encrypted, we can simply list all hosts in it like below:
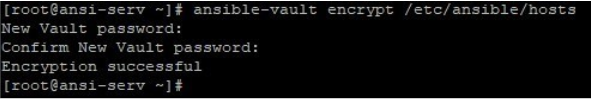
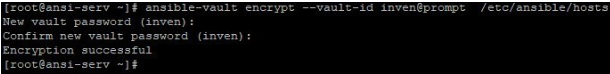
If you encrypt /etc/ansible/hosts, like below and try to run above command it will give you an error like below where it failed to parse the file.
Then you should provide vault password when prompted after using ask-vault-passin above command like below:
8. Using a vault file to pass the values of vault passwords in commands like ansible or ansible-playbook command. Few things to note while using a vault file: –
- The password should be in plain text in this file.
- The password should be a string stored as a single line in this file.
- This file contains the password, which is highly sensitive information, so this file should be protected by file permissions and other system security measures.
- The parameter vault-password-file should be used while using the vault file.
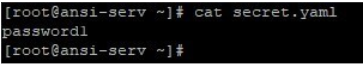
In this example, we have a vault file secret.yaml, which will be used while running the same command in the previous example. Below are the contents of secret.yaml.
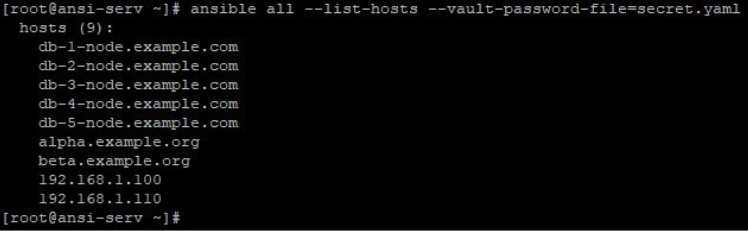
Now running the same command but with the parameter, vault-password-filewill executes successfully as it takes password from secret.yaml.
The default location of the password file can also be specified by using
$ANSIBLE_VAULT_PASSWORD_FILE
environment variable.
Now if this environment variable is set, then ansible command will neither ask you for vault password nor you have to give parameters like ask-vault-pass and vault-password-file.
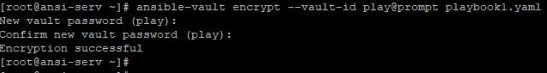
9. Ansible version 2.4 onwards, we have a very useful feature added which is vault-id. Suppose a case where you have multiple files that are encrypted and have different vault passwords. In this case, working with such files will really be a pain. Here comes the usefulness of vault-id. In this case, when you encrypt a file, you should assign a label and source name for the password for it.
In this example:
We have a playbook named playbook1.yaml and inventory /etc/ansible/hosts. Which are labeled and password is set like below. Here labels are inven and play. The source is kept to prompt, means take input from prompt, this can be vault file location as well.
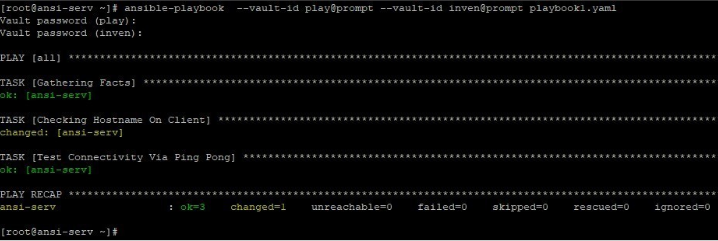
Now, as the password for inventory and playbook file is different, we can’t simply run it by giving flag ask-vault- pass to run playbook as we must give password multiple times while it will ask for a single password. So, we will run it as below and give vault-id in label@source format and password multiple times when asked.
Conclusion
In today’s world where we have technology growing rapidly in terms of quantity as well as quality, maintaining the security of your infrastructure environment without hampering the smoothness of operational tasks, is a challenging task. One must have many tools in his skillset to achieve this.
In the world of Configuration Management Automation, where Ansible is covering most of the market. Ansible Vault plays a very important role where you can store your Usernames, Passwords, Secret Keys, Access Keys, IP addresses, Hostnames, Port Numbers, Communication Methods, API Token, Important Web Locations, and any sensitive information.
Using Ansible Vault in an effective manner can lead to secure and protected operational tasks execution. Where you have a layer of security on Ansible level which can complement the other security tools you might have in your infrastructure.
Recommended Articles
This is a guide to Ansible Vault. Here we discuss how does Ansible Vault Work along with the examples in details. You may also have a look at the following articles to learn more –