Updated March 23, 2023
Introduction to Authentication Header
The Authentication Header is also called as AH. It provides support for data integrity and authentication of IP data packets. Here data integrity ensures that the data that lies inside the IP packets are not altered during the transmission of packets, and Authentication services enable the user or computer system to authenticate the user to the application at other end and based on the result, it decides whether to allow or reject. An authentication header prevents the IP spoofing attack. In order to use AH, two parties must share the secret key for communication.
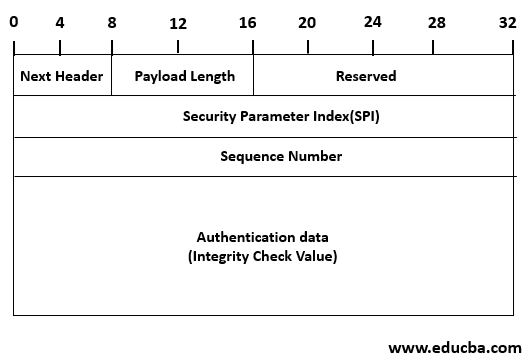
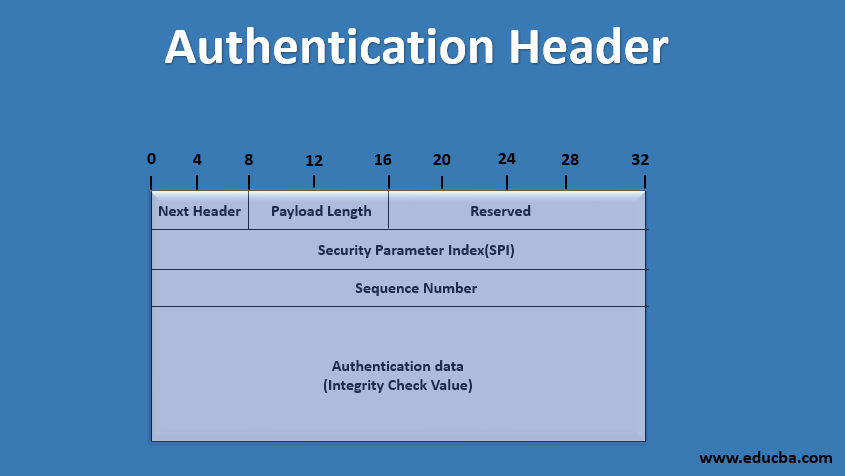
Format of Authentication Header
The authentication header format is as follows. There are a total of 6 fields in the Authentication Header. Below is the list of them:
- Next Header
- Payload Length
- Reserved
- Security Parameter Index (SPI)
- Sequence Number
- Authentication Data
let us discuss the above fields in detail:
- Next Header: This field is 8 bit used to identify the header types that immediately follow the authentication header. For example, if the ESP header follows the AH, this field contains 50 as a value; otherwise, if another AH follows this AH, it contains 51 as a value.
- Payload Length: This field is 8 bit. It contains the length of the Authentication header in 32-bit words minus.
- Reserved: This field is 16 bit, which is reserved for future use.
- Security Parameter Index (SPI): This field is 32 bit. It is used in combination with the source address and destination address and the IPsec protocol (Internet Protocol Security), uniquely identifying the security association (SA) for the traffic to which the datagram belongs.
- Sequence Number: This field is 32 bit which is used for the replay attacks.
- Authentication Data: This variable-length field contains the authentication data, called an Integrity Check Value of (ICV) for the datagram. This value is used for integrity, and authentication purpose is in MAC form. For example, For the IPV4 datagram, this field is an integral multiple of 32; for the IPV6 datagram, this field is an integral multiple of 64. Integrity Check Value is calculated by generating MAC using the HMAC digest algorithm.
Modes of Operations in Authentication Header
There are two modes in the Authentication header:
- Authentication Header Transport Mode: In transport mode, it lies between the original IP header and the IP packet’s original TCP header.
- Authentication Header Tunnel Mode: In tunnel modes, first, the original IP packet is authenticated entirely, and the authentication header is inserted between the original IP header and the new outer IP header. Here the inner IP header contains the ultimate source IP address and destination IP address, whereas the outer IP header contains different IP addresses (IP addresses of the firewalls or other security gateways)
How does the Header Deal with Replay Attack?
Int his section, we are going to discuss how the authentication header deals with the replay attack:
- In a replay attack, the attacker obtains a copy of an authenticated packet and then sends it to the intended destination. As the same packet received twice, the destination user could face some problems. To overcome this problem, the Authentication header uses a sequence number field.
- At the initial stage, the value of this field is set to 0. Whenever the sender sends a packet to the same receiver over the same SA, it increments the field’s value by 1. Then the sender must not allow this value yo circle back from 2^32 – 1 to 0. If the number of packets over the same increases this number, then communicating with the receiver sender must establish a new SA with the receiver.
- At the receiver side, the receiver maintains a sliding window size to W. The default value of this W is 64. This window’s right edge represents the highest sequence number N received so far for a valid packet.
When the receiver gets a packet from the sender, it performs some action. The appropriate action depends on the sequence number of the packet. - « If the sequence number of the received packet falls within the window and if the packet is new, then its MAC is checked. If the MAC is successfully validated, the corresponding slot of the window is marked. The window itself does not move to the right-hand side.
- « If the received packet is to right of the window, i.e. The sequence number of the packet is greater than N., And if the packet is new, then the MAC is checked. If the packet is authenticated successfully, the window is advanced to the right so that the right edge of the window will match the sequence number of this packet, i.e. The sequence number now becomes a new N.
- « If the received packet is to the left of the window, i.e. The sequence number of the window is less than (N -W), and if the MAC check fails, the packet will be rejected, and an audible event is triggered.
This is how to authenticate the header prevents the replay attack.
Recommended Articles
This is a guide to the Authentication Header. Here we discuss what is the authentication header, its 6 formats, modes and how the authentication header deals with the replay attack? You can also go through our other related articles to learn more –