Difference Between Authentication vs Authorization
In the context of security and access control, authentication and authorization are two separate but related processes. The main goal of authentication is to establish the legitimacy of people, systems, or other organizations requesting access to a resource by confirming their identity using passwords, fingerprints, or tokens. It tries to confirm that the claimed identity corresponds to the real one, preventing unauthorized access. Authorization, in contrast, entails granting or refusing particular permissions to authenticated entities by their roles, attributes, or other distinguishing qualities.
It answers the query of what capabilities or assets an authenticated user can access. Authorization establishes the range of permitted behaviors, whereas authentication establishes the legitimacy of the identity. Users must establish their identification before configuring and establishing their access permissions. Therefore, these procedures take place sequentially, with authentication before authorization.
Table of Contents
Key Takeaways
- User identification is verified by authentication utilizing techniques like passwords or biometrics.
- Authorization chooses which resources a user can access based on roles or permissions.
- In the access process, authentication comes before authorization.
- Authorization regulates resource access, while authentication verifies identity.
Explanation of Authentication and Authorization
What is Authentication?
The authentication process is to verify a user, system, or entity’s identity when they want to access a resource, system, or service. It entails verifying that the person or thing is who they say they are, frequently using credentials like tokens, passwords, PINs, or biometrics (such as fingerprints or facial recognition). Modern solutions like Passkeys are now emerging, offering a passwordless approach that leverages public-key cryptography tied to a user’s device or biometric data. Passkeys reduce reliance on traditional credentials, enhancing security and user convenience.
Example:
Imagine you have a personal email account. When you log in to your email, you must provide a username (your email address) and a password. Verifying your identity using a unique set of credentials is known as authentication. The system checks if the provided username and password match the stored credentials, and if they do, you’re granted access to your email account.
Here is an illustration of a straightforward username and password authentication procedure:
User: Henry
Password: Pa$$w0rd07
- The user enters their login information.
- The server checks the database to see if the username is present.
- The server extracts the user’s hashed password from storage if the username is present.
- After hashing the provided password, the server compares it to the previously stored hashed password.
- If the hashes match, authentication succeeded, granting the user access.
- Access is denied if the hashes do not match and authentication fails.
What is Authorization?
According to their responsibilities, qualities, or other distinguishing factors, authorized users are granted or denied access permissions throughout the authorization process. The activities or resources a user can access within a system, application, or network are determined by authorization once the user’s identity has been verified through authentication. This entails establishing permissions, identifying access levels, and implementing access control policies. To prevent authenticated users from accessing restricted or sensitive areas, authorization ensures they only have access to resources and functionalities pertinent to and appropriate for their roles or privileges.
Example:
On the other hand, authorization determines if a user has permission to utilize a particular resource or carry out a specific action.
A sample authorization procedure is provided below:
Resource: Document “DailyUpdate.docx”
User: Henry
- Henry attempts to access the “DailyUpdate.docx” document.
- The system checks Henry’s role or permissions level.
- If Henry’s role has sufficient permissions (e.g., “Manager” or “Administrator”), he is granted access.
- If Henry’s role does not have sufficient permissions (e.g., “Guest” or “Employee”), access is denied.
Infographics
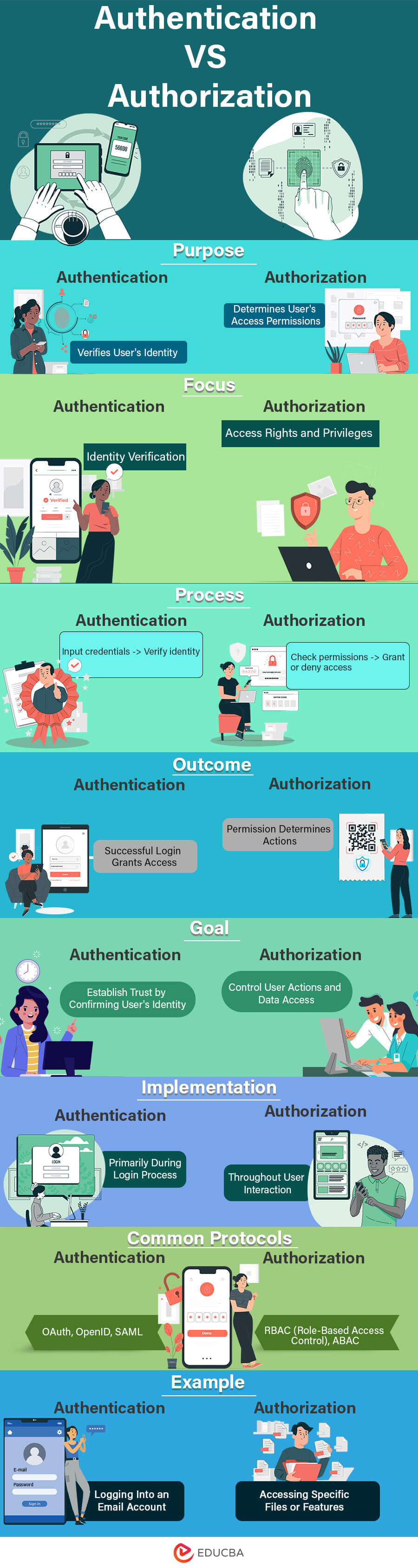
Now, with a grasp of Authentication and Authorization fundamentals, let’s explore the key distinctions visually in the infographic provided below. This graphical representation will simplify understanding of the eight major differences between Authentication and Authorization, including their technologies.
Factors and Methods
For Authentication
To verify the identity of users accessing systems or resources, authentication uses a variety of factors and techniques. These elements create a higher level of security by asking individuals to present identification proof. Here is a summary of the elements and procedures involved in authentication:
Factors:
- Knowledge Factor: This calls for using knowledgeable data, such as a password, a personal identification number (PIN), or the answers to security questions. Despite being the most used authentication, phishing attacks can exploit it.
- Possession Requirement: For this to work, the user must have a tangible item or technological equipment. It comprises tools that produce one-time codes, such as security tokens, smart cards, or mobile phones. Access could not be obtained without the possession factor, even if a password was compromised.
- Inherence Factor (Biometric): Biological or behavioral characteristics specific to the user, such as fingerprints, face recognition, iris scans, voiceprints, or even behavioral patterns like typing speed, are used as the Inherence Factor (Biometric). Biometrics offer a reliable method of authentication since they are challenging to copy.
Methods:
- Single-Factor Authentication (SFA): Users only supply one authentication element, such as a password or a fingerprint scan, with single-factor authentication (SFA). This is straightforward but might not offer enough protection from sophisticated attackers.
- Two-Factor Authentication (2FA): Users give two distinct factors from various categories when using two-factor authentication (2FA), which commonly combines a password (knowledge) with a possession factor (token) or inherence factor (biometric). This greatly improves security.
- MFA (Multi-Factor Authentication): Like 2FA, MFA asks users to input two or more factors from many categories. For instance, it might entail a password (knowledge), a fingerprint scan (inherence), and a temporary code from a smartphone app (possession).
- Adaptive Authentication: This method evaluates several contextual elements, including the user’s location, device, and behavior patterns, to ascertain the proper level of authentication needed. For instance, more authentication factors can be required if a user signs in from a strange location.
For Authorization
The choice of authorization factors and methods depends on the organization’s security requirements, the complexity of the system, and the need for precise control over resource access.
Factors:
- Identity: The identity of the user or entity requesting access to a resource affects authorization decisions. This entails being aware of the user’s identity and any roles or characteristics they may have within the system.
- Context: The setting in which the authorization request occurs has an impact. The information comprises the user’s current actions, time of day, location from which they request access, device, and other elements.
Methods:
- Role-Based Authorization (RBAC): RBAC grants access permissions based on the roles allocated to users. Users are assigned to specified roles connected to a specific permissions set. The administration is simplified because permissions are now maintained at the role level rather than separately for each user.
- ABAC (Attribute-Based Authorization): Attribute-Based Access Control (ABAC) bases choices on the user, resource, and context attributes. It makes use of rules that specify circumstances affecting these characteristics. For instance, access might be permitted if a user with the “manager” job tries to open a file with the label “confidential.”
- Rule-Based Authorization: Authorization based on pre-established rules is known as rule-based authorization. These rules may cover different circumstances and acts. For instance, a rule can specify that users can only edit data if they created the document.
- Discretionary Access Control (DAC): Resource owners can manage access using discretionary access control (DAC). Owners can give or withdraw permissions for other users, giving them additional freedom but sometimes resulting in inconsistent access control.
Security Concerns
Authentication
- Password-Based Vulnerabilities: Weak passwords, password reuse, and the possibility of brute-force assaults all present serious security threats.
- Phishing Attacks: Phishing attacks compromise authentication by tricking users into divulging their credentials through phony emails or web pages.
- Credential Theft: Malware, keyloggers, and credential harvesting tools can use infected machines to obtain authentication credentials.
- Account Lockouts: Account lockouts or service interruptions may occur due to several unsuccessful login attempts made by authorized users or attackers.
- Biometric Spoofing: Forged biometric information or images can be used to get around biometric authentication procedures.
- Credential Stuffing: Attackers utilize compromised data to gain unauthorized access by exploiting reused credentials across several services.
- Lack of Multi-Factor Adoption: Many users only use passwords, omitting the extra security that multi-factor authentication offers.
- Weaknesses of Legacy Systems: Older systems may lack contemporary security features, making them vulnerable to breaches in authentication.
Authorization
- Over-Privileged Access: Unauthorised data exposure and misuse can result from users or entities having greater access than necessary.
- Under-Privileged Access: Inadequate permissions prevent legal acts, which may impact corporate procedures and productivity.
- Role Creep: As roles grow over time, it may become difficult to monitor and audit access rights without confusion.
- Inconsistent Role Definitions: Users who shouldn’t have access to resources may do so due to inaccurate or inconsistent role definitions.
- Access Control Misconfiguration: Access control configuration errors might result in unauthorized access or data leakage.
- Insufficient Logging and Monitoring: Insufficient logging and monitoring can delay the timely discovery of unauthorized access. Weak tracking of permission events can contribute to this.
- Broken Inheritance: Inadvertently granting unauthorized access can occur when the inheritance of permissions is handled improperly.
- Externalized Authorization: Externalised Authorization provides external dependencies and potential failure spots when authorization depends on external services.
Key Difference Between Authentication VS Authorization
The section below highlights key differences between the Authentication vs Authorization topics with clarity and detail. Let us examine them closely and gain a clear understanding of both concepts.
Authentication
The process of authentication can be completed through the following:
- Passwords: User credentials like passwords and user Ids are among the most common authentication factors. If the user provides their username and password, which matches the credentials stored in the system, then the system allows access to the user, assuming they are genuine.
- One-time passwords: One-time passwords are pins provided to the user through some communication channel authorized by the user. It grants access to the user only for a transaction or session.
- Authentication Apps: In some cases, the system generates a security code that can be accessed through a third-party app used to access the system.
- Biometrics: In this case, the user has placed their finger or has to go through an eye scan to access the system.
There are also some cases where the system needs to verify the user through multiple authentication factors to allow access. Two-factor or multi-factor authentication is generally used to increase security beyond passwords.
Now, organizations are going passwordless and providing modern authentication techniques through one-time passwords, also called OTPs or single sign-on, SSO, or two-factor or multi-factor authentication or biometrics for authenticating the users and to have security beyond passwords, which can easily be hacked nowadays.
Authorization
- Authorization generally comes after the user has been verified and authenticated. Authorization allows the user full or partial access to a particular resource, funds, or database, or it can also be some critical information.
- Let’s take an example of an organization once an employee gets verified through a user ID and password or other factors like biometrics. The next step is to authorize the user what things they can access or what actions they can take in the system.
- Identity access management administrators must understand the gist of using authentication and authorization wisely and how to differentiate between them.
- The wisest thing to do is to implement authentication with the perfect authorization techniques to have the best security to protect the organization from identity thefts, hacks, or cyber-attacks. Combining these two also ensures the smooth flow of work and information in the organization, making the organization more productive.
Popular Authorization Techniques are:
- Role-based access controls (RBAC): This authorization technique implements privilege management for user-to-system or system-to-system interactions.
- JSON Web Token (JWT): One of the most common authorization techniques. It enables secure data transmission between users, clients, and parties, with authorization of the parties using a private key pair.
- SAML: Also known as Security Assertion Markup Language, is an authorization technique using the Single Sign-On format (SSO), in which the authentication information is transferred through XML documents signed digitally.
- OpenID Authorization: This authorization technique verifies the user using the authorization server’s authentication.
- OAuth: This authorization technique enables an API to authenticate and provide access to the user for the requested resource or action.
Authentication vs Authorization Comparison Table
Let’s discuss the top comparisons between Authentication and Authorization:
| Aspect | Authentication | Authorization |
| Definition | User identity verification. | Granting authenticated users access rights based on their roles or characteristics. |
| Purpose | Verifying the identity of the user. | Limiting the actions and resources a user can utilize. |
| Focus | User identity | User access rights. |
| Objective | Ensuring that only individuals with the appropriate access can use the system. | Make sure users have the proper permissions. |
| Information Used | Identification documents (passwords, tokens, biometrics). | Roles, qualities, and permissions for users. |
| Interaction | The user directly participates. | Set rights by system administrators. |
| Timing in Session | Beginning of a user session. | Throughout the user session. |
| Dependency | Authorization depends on successful authentication. | Authentication is a prerequisite for authorization. |
| Risks of Insufficient Implementation | Unauthorized access and identity theft. | Data breaches and data exposure. |
| Challenges | Identity theft and phishing attempts. | Insider threats and complex access control policies. |
Conclusion
To ensure digital safety, authentication and permission are needed. While authorization establishes access restrictions, authentication verifies users to strengthen the gateway. For the protection of information and resources, both are essential. As threats change, integrating these procedures becomes important for flexible, user-centered security frameworks. This mellow interaction strengthens systems and gives authorized people legitimate access. Integrating authentication and authorization forms the cornerstone of thorough cybersecurity in a digital environment that is evolving quickly.
FAQs
Q1. How does authentication relate to user identity verification?
Ans: The purpose of authentication is to confirm that the person using a system is who they say they are.
Q2. How can organizations balance security and usability in authentication?
Ans: Organisations should employ reliable authentication techniques while considering consumer convenience.
Q3. What is the concept of least privilege in authorization?
Ans: Referring to the least privilege and reducing the potential consequences of a security breach involves giving people the bare minimum of access.
Recommended Articles
This guide explores the key distinctions between Authentication and Authorization. It includes a comparison table, infographics, and a discussion of Authentication vs. Authorization with examples. Additionally, you can explore related articles by referring to the following links.