Updated March 8, 2023
Introduction to Azure bastion
Microsoft Azure Bastion is a full platform managed service users can deploy on the cloud; this service lets users connect to the virtual machines using the Azure portal or browser. Azure bastion service is provided as part of a virtual network, and it provides secure and seamless RDP/SSH connectivity from the Azure portal to the Virtual Machines over TLS. Virtual machines do not need a public IP address, agent, or third-party software if we are using Azure Bastion for the connection. Azure bastion protects virtual machines from outside worlds as it hides RDP/SSH ports by providing secure access to RDP/SSH.
How does Azure bastion work?
Microsoft Azure bastion is not dependent on subscription/account or virtual machine as it is deployed as per virtual network. Virtual machines in the Virtual network use the RDP/SSH for connectivity when Azure bastion is provided in the virtual network. RDP and SSH are used as fundamental connection service to connect to the workload running in the azure. Exhibiting RDP or SSH ports over the internet is highly insecure, and this can be seen as a significant threat, and it frequently happens due to protocol vulnerabilities. To prevent a system from these threats and vulnerabilities, users can deploy the bastion hosts or jump-servers to the public side of the perimeter network. The bastion host server is mainly designed and configured to resist any attack. This server also provides RDP/SSH connectivity to the inside of the network and workloads used behind the bastion.
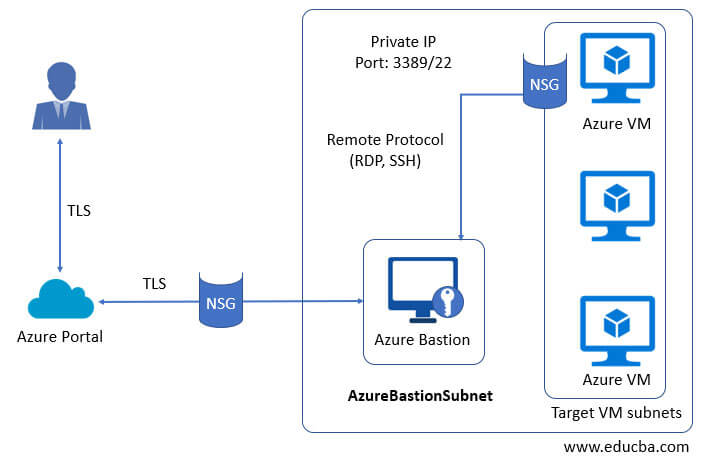
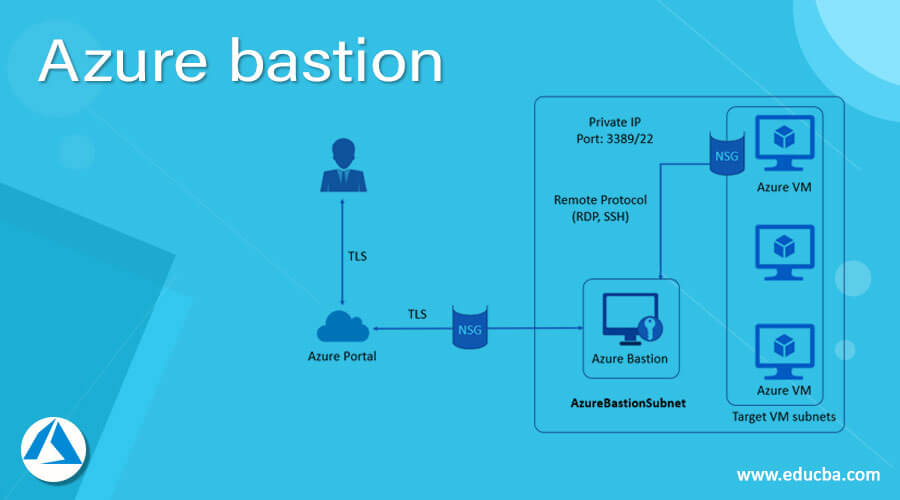
Azure bastion follows the below steps while deployment as describes in the diagram below:
- Azure bastion hosts are migrated to the virtual network in virtual machines.
- Using HTML5 browser user is connected to the Azure portal.
- Users can select which virtual machines to connect to.
- RDP/SSH session is opened in the browser with a single click in the Azure portal.
- Azure VM does not use any public IP for connection.
How to create and use Azure Bastions?
Pre-requisites:
Before learning to create the Azure Boards, users must have an Azure subscription so that they can log in with valid credentials to the Azure Portal and create Azure Bastions.
Steps using Azure Portal :
Create the bastion host:
Step #1
Login into the Azure Portal using the below URL:
https://portal.azure.com/learn.docs.microsoft.com
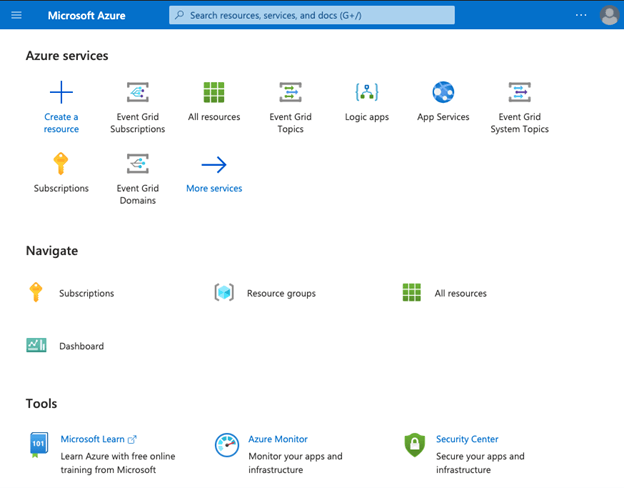
Step #2
From the Azure portal home page, select the +Create a resource.
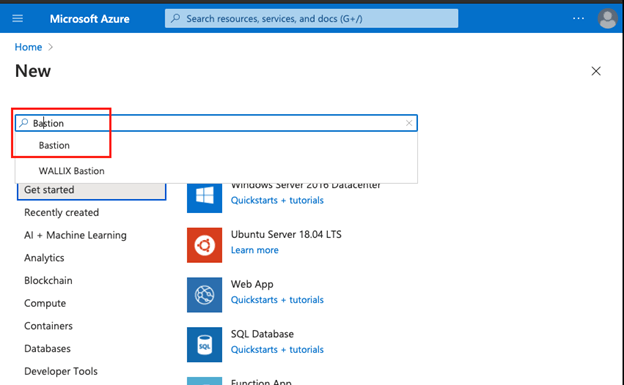
Step #3
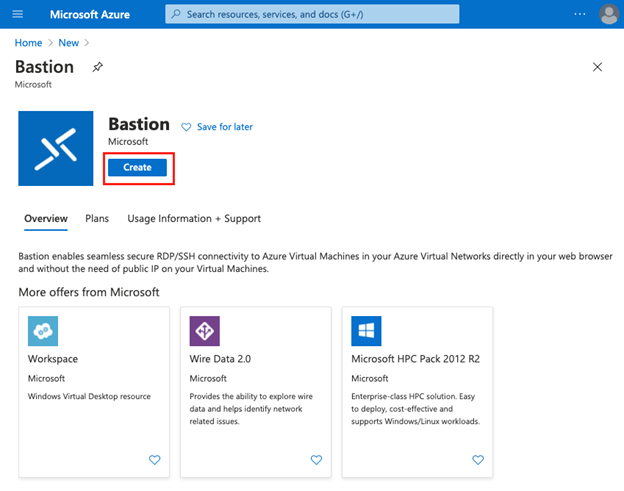
In the Search field of Azure Marketplace, search for Bastion and click on enter to open the Bastion page:
Step #4
From the Bastion page, select Create:
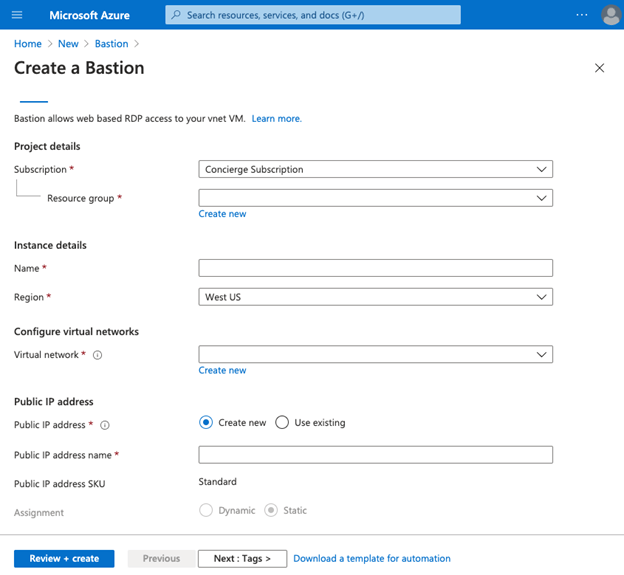
Step #5
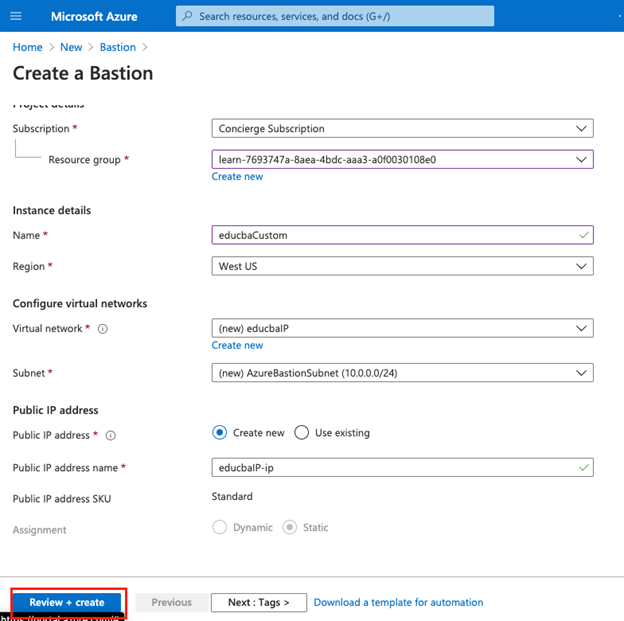
On a Create a Bastion page, enter the details as below:
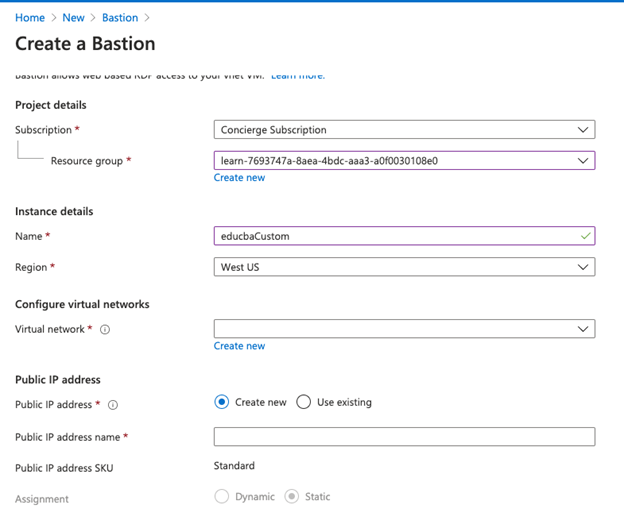
Step #6
Enter the details of the new bastion as below:
Subscription: Select your subscribed plan from the drop-down list.
Resource group: Select the resource group in which you want to create bastion.
Name: Enter the unique name for the Bastion instance.
Virtual Network: Select a virtual network created in the location.
Public IP address: Select public ip address from existing or new.
Public IP address name: enter the name of the public ip address.
Step #7
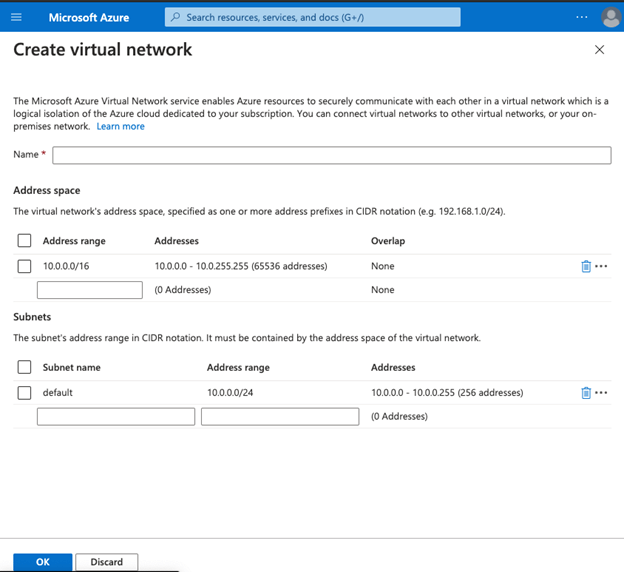
Select create new from the virtual network to create a new virtual network:
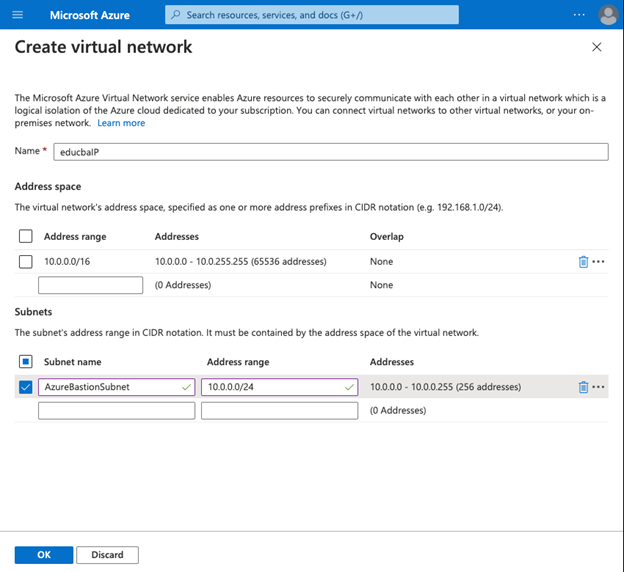
Step #8
Click on OK from the create a virtual network:
- In the subnet section, the subnet name should always start with AzureBastionSubnet.
Step #9
After specifying all the details and creating a new virtual network, select Review+Create from the page to validate details and then click on the create:
Step #10
Once the deployment is complete, the user can see the message that deployment is in progress/underway.
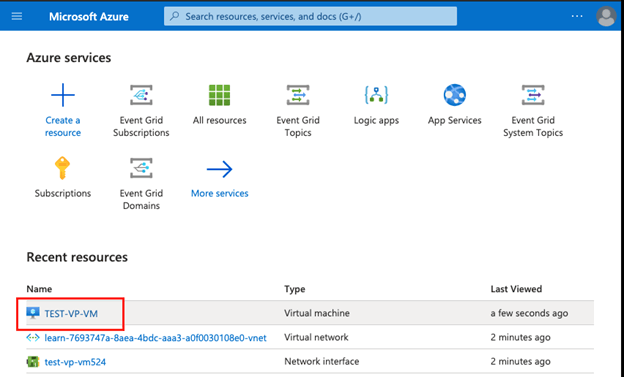
Step #11
From the home page, check the newly create VM and open the Virtual Machine:
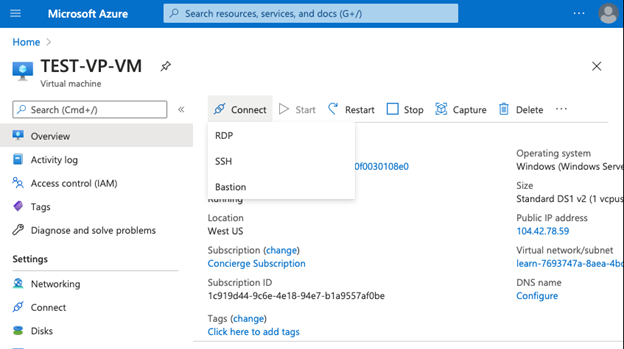
Step #12
Select Connect from the virtual machine page:
Step #13
Select Bastion from the drop-down list:
Step #14
Select Use bastion from the page user will be asked to enter the username and password used to create a virtual machine, then click on the connect :
Step #15
This will open a virtual machine directly in the Azure portal.
Uses of Azure Boards
- RDP and SSH are directly integrated into the Azure portal and using a single click; users can have a seamless experience.
- It uses HTML5 based web client, which helps to get RDP/SSH sessions over TLS on port 443, which helps to traverse in corporate firewalls securely.
- Azure Virtual Machine does not need public IP while using Bastion.
- It is a full platform managed service, and this protects against zero-day use using bastion, and it is always up to date.
- Users do not need to apply any NSGs on the Azure bastion as the Azure bastion connects to the VM over private IP.
Conclusion
In conclusion, Azure bastion helps users connect to the virtual machine over private IP and has in-built security offered due to RDP/SSH for connectivity. Due to the seamless integration of bastion with other Azure services, users can have to manage Azure bastion with a single click.
Recommended Articles
This is a guide to Azure bastion. Here we discuss How does Azure bastion work and How to Create and Use it, along with the steps. You may also have a look at the following articles to learn more –