Updated March 16, 2023
Introduction to Azure Functions Authentication
The azure functions authentication is similar to preparing the web-based applications or cloud-hosted service; serverless functions will require careful development, deployment, and operation for function apps to secure the hosting infrastructure, which is provided by the azure app service function and host are the authorization scopes for each key that has named reference on the default key at the function and host level also the function keys will precedence over the host keys.
Serverless functions must be carefully developed, deployed, and operated for function apps to secure the hosting infrastructure that is provided by the Azure App Service. Function and host are the authorization scopes for each key that has a named reference on the default key at the function and host level. Additionally, function keys will take precedence over host keys in the azure functions authentication. To Find and choose the Azure Functions with the help of Command to open in the portal and to open the function app in the Azure portal, select the subscription and the name of the function app. Choose Authentication/Authorization from the Platform features tab in the function app that was opened in the portal. App service authentication should be enabled. App for Microsoft Authenticator, Microsoft Windows Hello for Business Security key for FIDO2, and Hardware token for OATH are some of the different azure authentication methods.
Key Takeaways
- Authentication/Authorization from the Platform features tab in the function app that was opened in the portal.
- App service authentication should be enabled.
- Authentication/authorization, and function keys can help prevent some unauthorized access, but the only way to properly secure the function keys
- The function is only the precise functions for which they are defined and are covered by these keys. These only give access to that function when used as an API key.
- The host is used for all functions in the function app and can be accessed using keys with a host scope. These can be used as API keys to gain access to any feature of the function app.
How to Setup Authentication for Azure Functions?
1. Select the app after searching for and choosing App Services in the Azure site after logging in to the URL of the Azure app. It will be used to set up the registration for the Azure Active Directory app.
2. Choose Azure Active Directory from the portal menu, then click the App registrations tab and New registration. Here I already registered and logged into the portal.
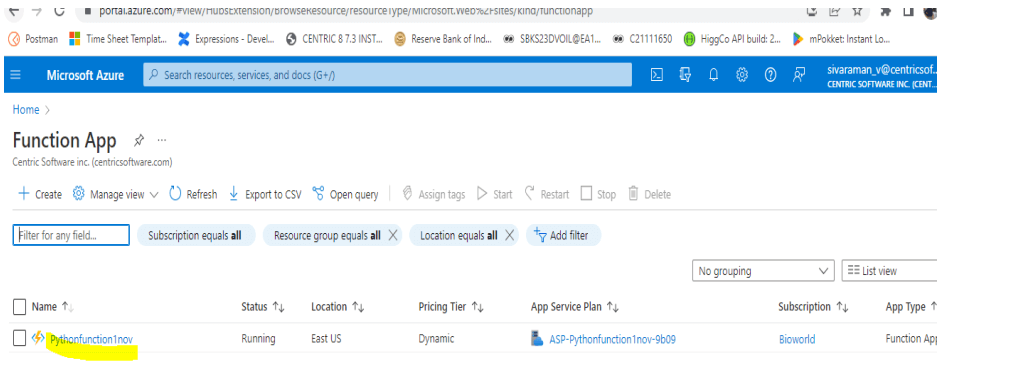
3. Then I navigate to Function App; here, I have already created one function APP.
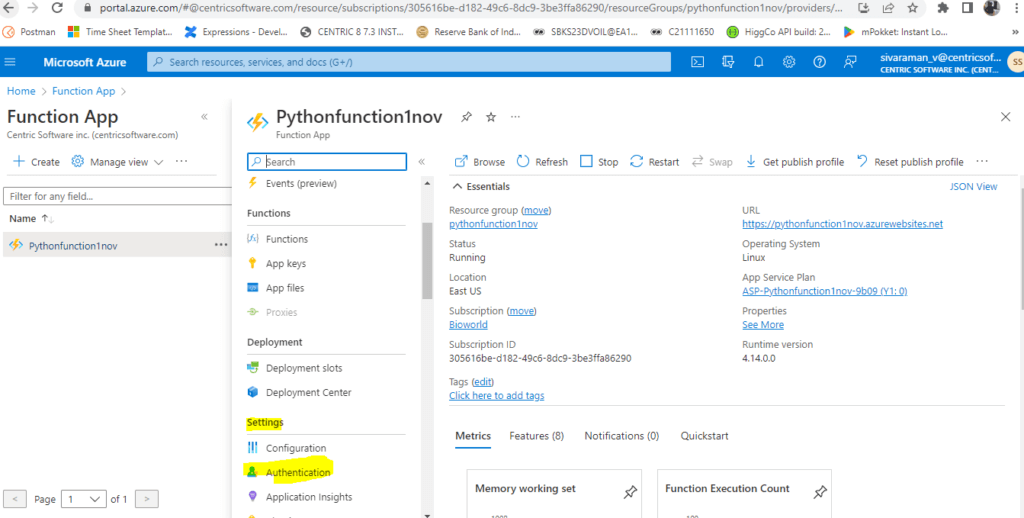
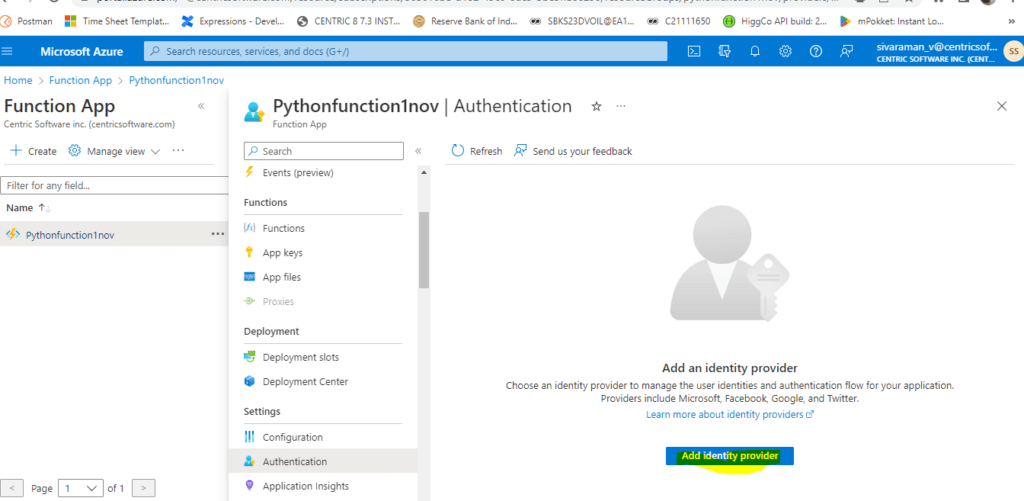
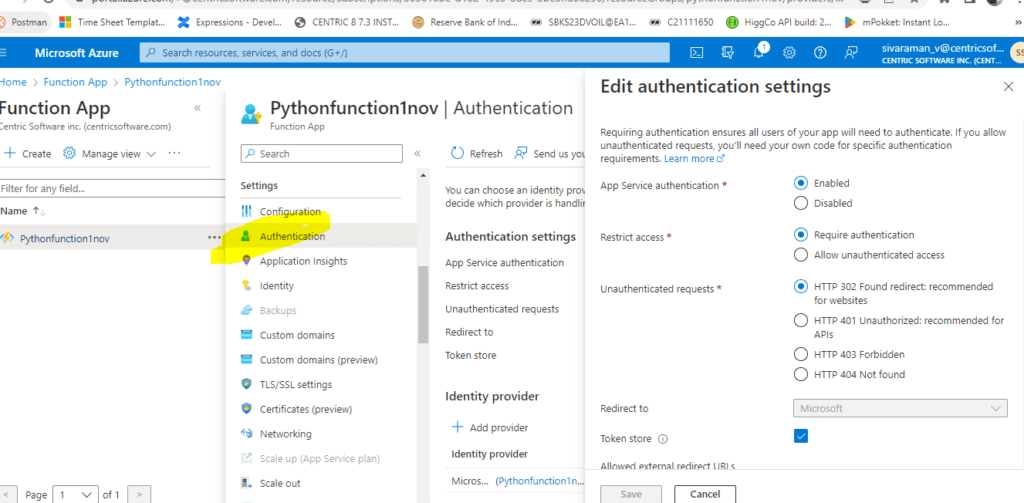
4. Inside the function APP left side tab, we can see the Settings -> Authentication tab.
5. We can add the Identity provider of our application.
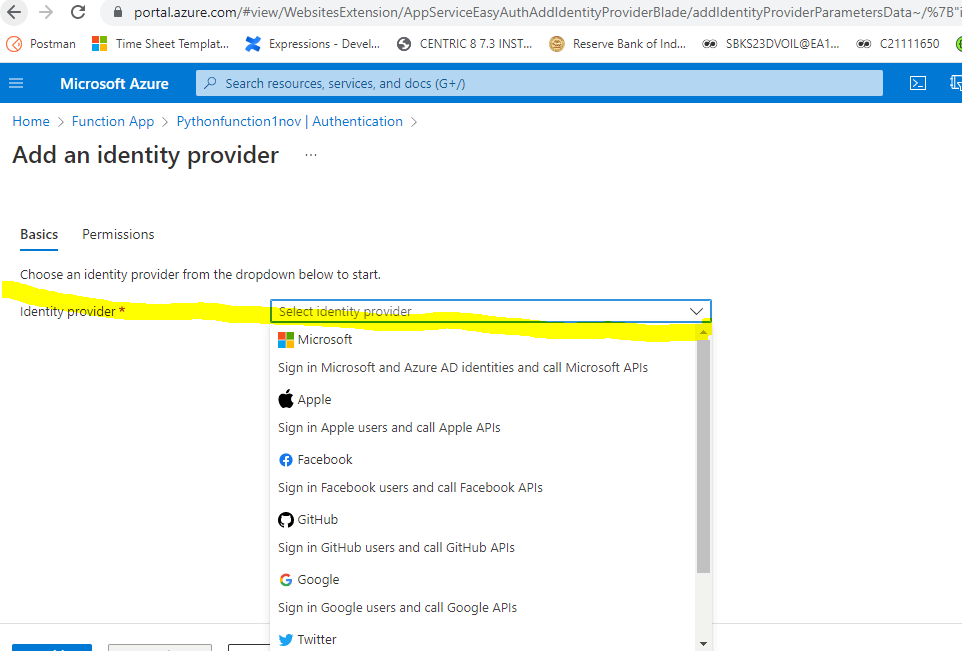
6. Choose the Identity provider, which is listed in the dropdown box.
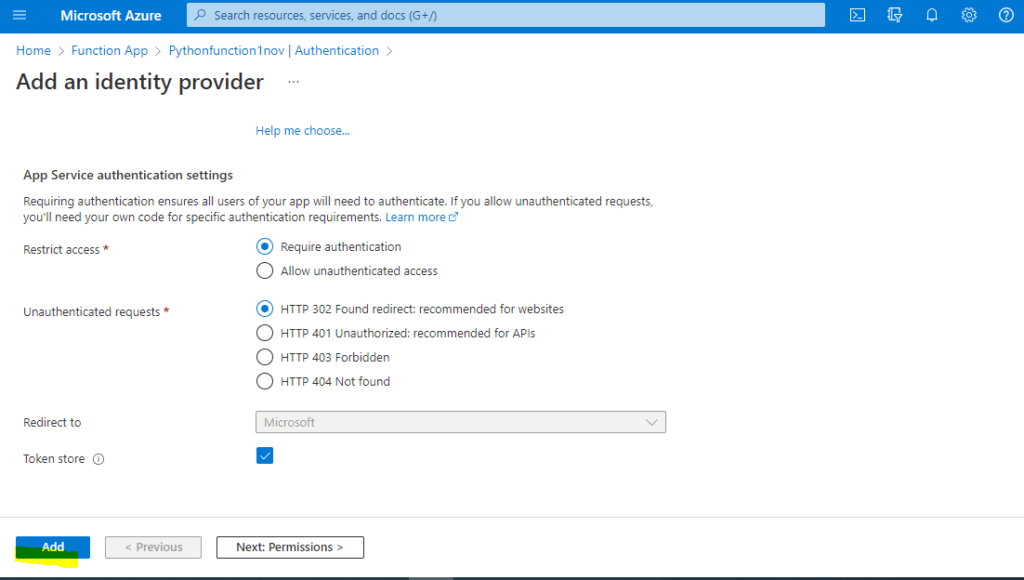
7. I am choosing Microsoft, and then I will not change anything. Click Add to generate the Token.
8. If needed, we can add the Next tab on Permissions levels; here, I am not given any permissions, so I have added the User Identity.
How to Add Authentication for Azure Functions?
Google, Facebook, Twitter, Microsoft Account, and Azure Active Directory are all supported for authentication using App Service Authentication. Some of the steps we followed to enable the authentication in azure functions. There are many alternatives available for approving queries, including App Service Authentication and employing API management. The App Service platform enables authentication customers using Azure Active Directory (AAD) and a number of external identity providers. This method enables to leverage of user data from the function code and establishes unique permission criteria for the functions.
Function keys can help mitigate unauthorized access to some extent, but implementing positive client authentication is the only way to truly secure your function endpoints. Then, based on identity, we can decide on the authorization.
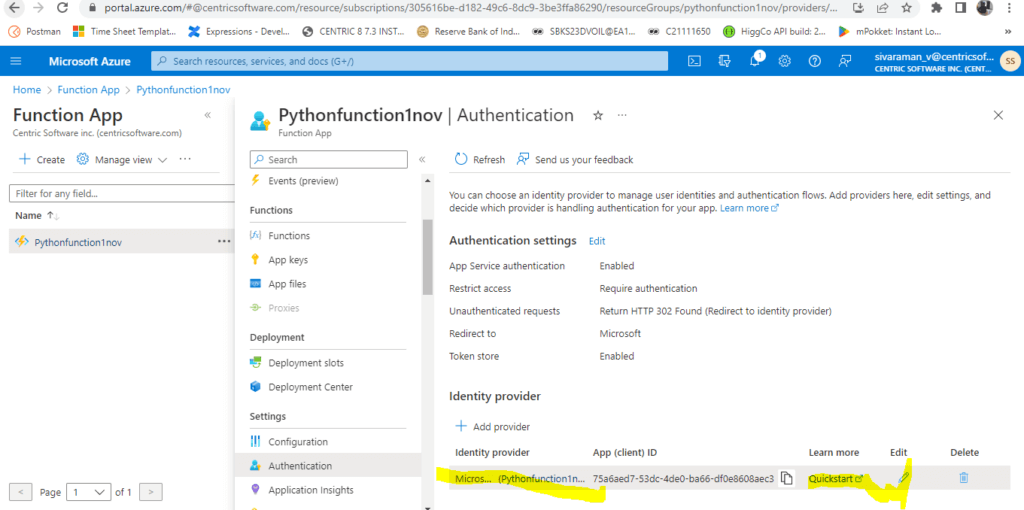
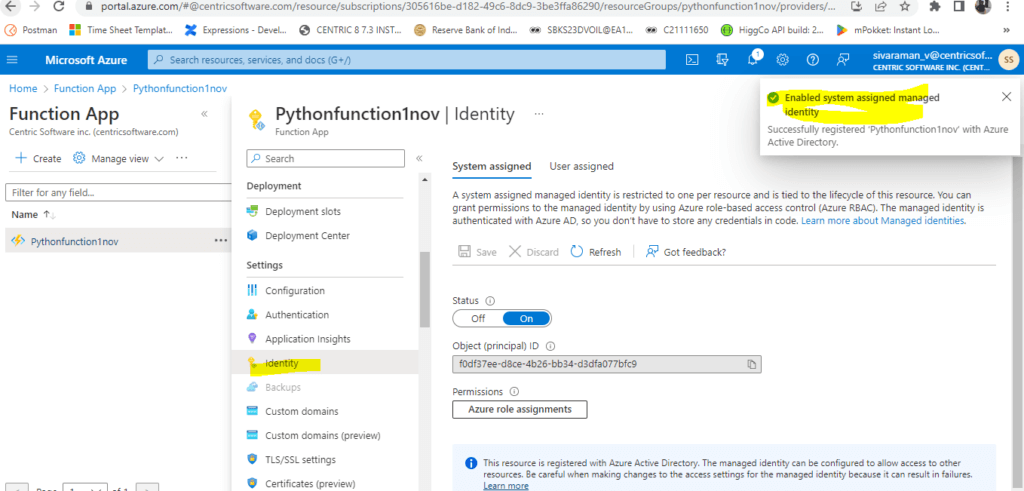
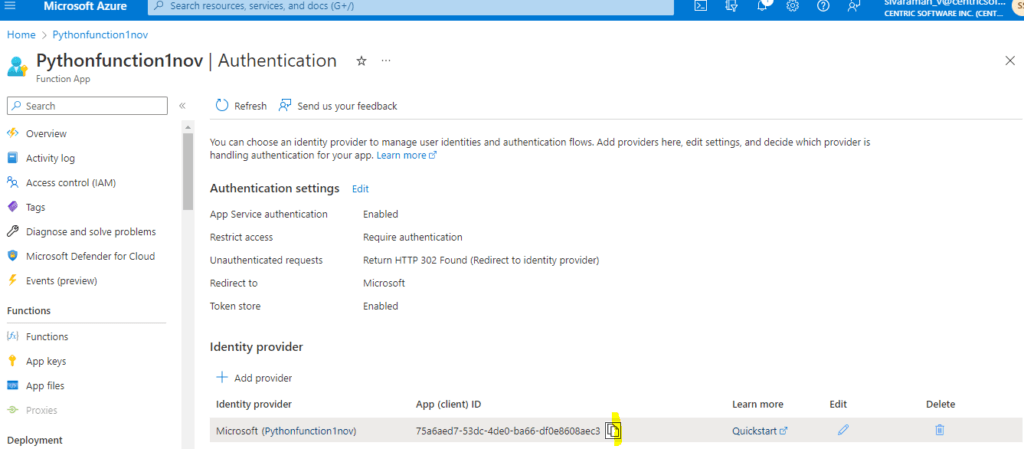
We also copied the Object ID below f0df37ee-d8ce-4b26-bb34-d3dfa077bfc9. Also, we can be able to edit the Authentication settings.
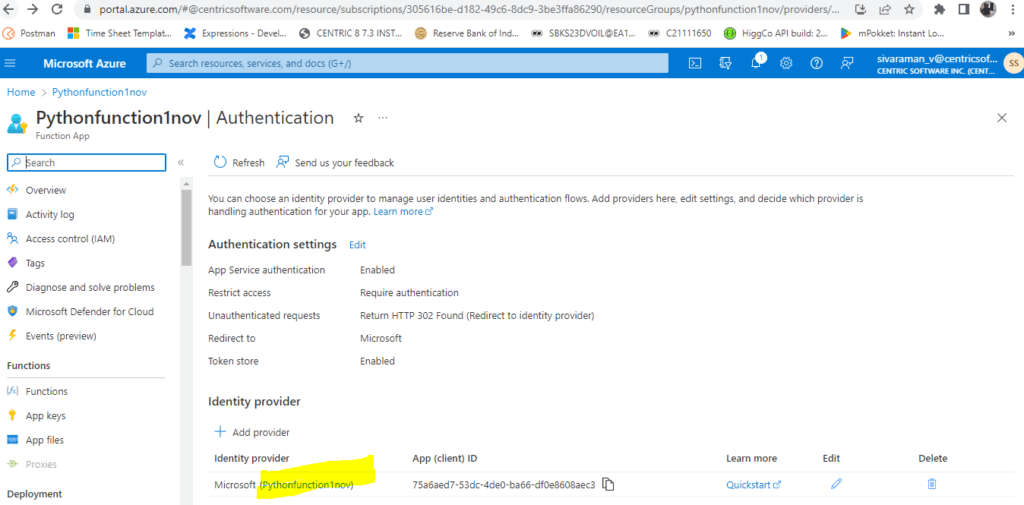
Then inside the Identity provider in Authentication.
Select Authentication.
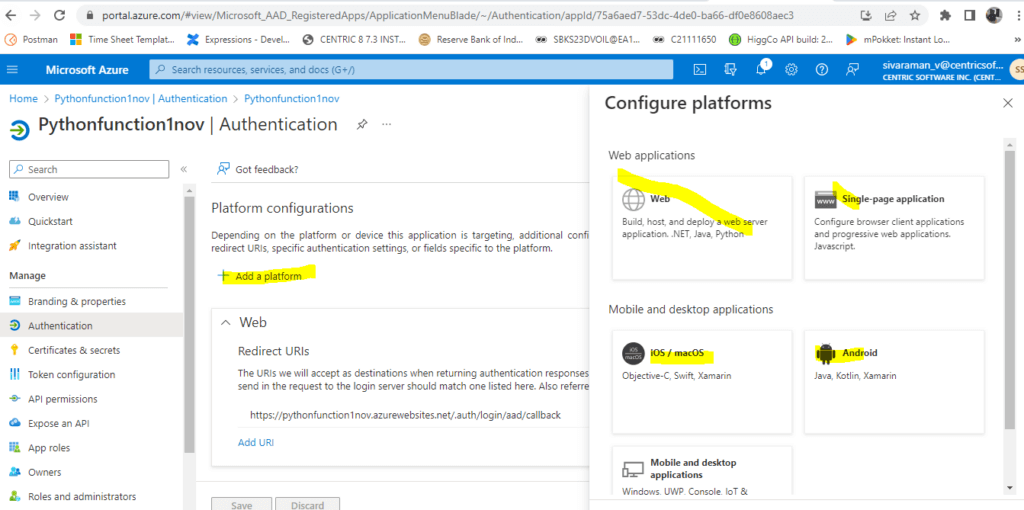
We can also configure the Platform configurations like below.
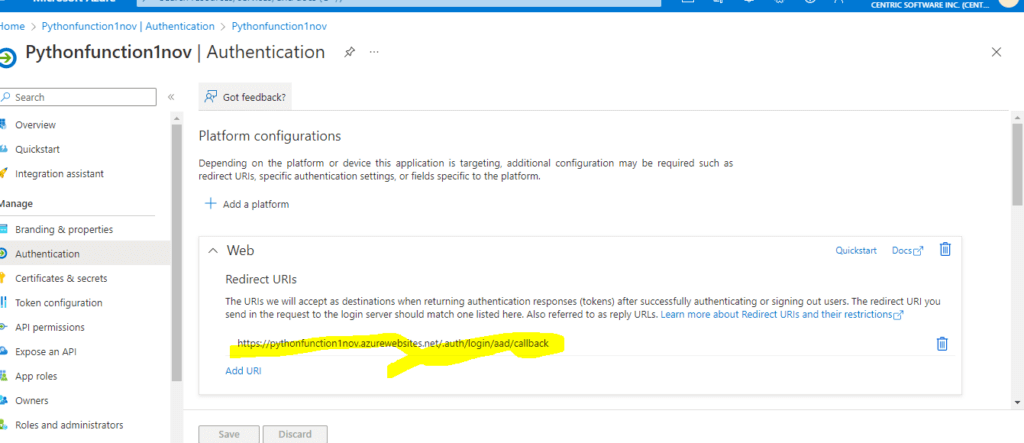
Based on the needs, we can add the platform. Here already configured the URIs in Web.
Here I am just copying that URL like below https://pythonfunction1nov.azurewebsites.net/.auth/login/aad/callback
Then paste it on the browser.
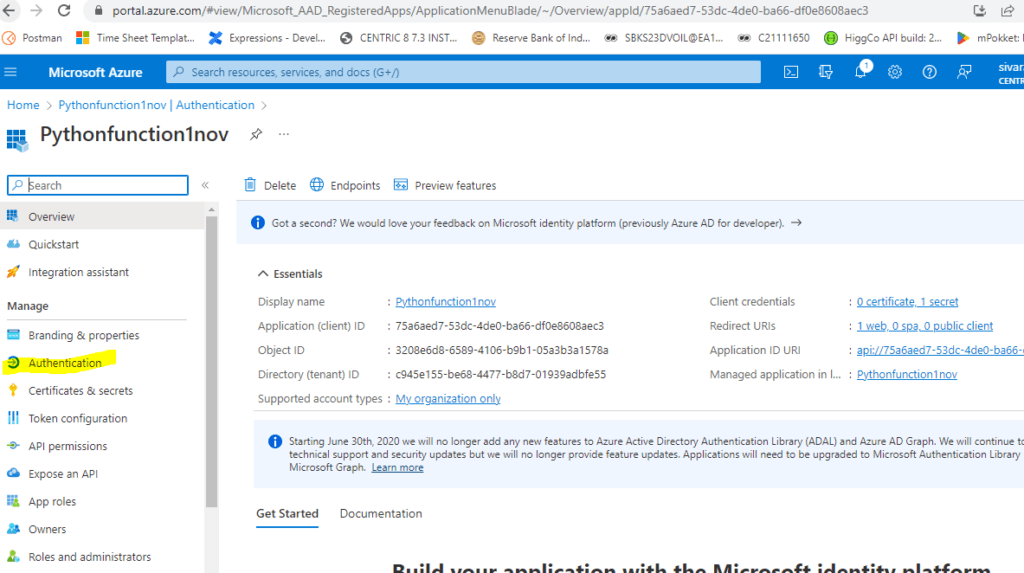
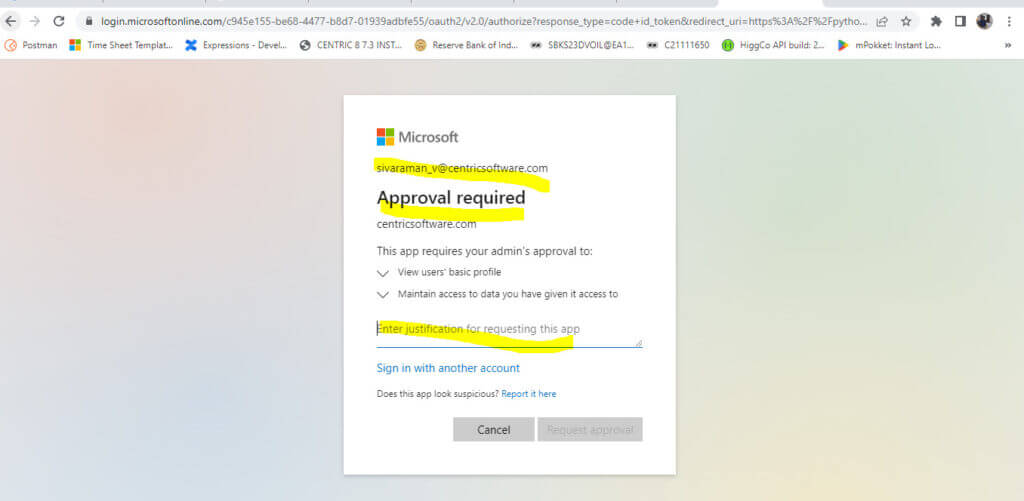
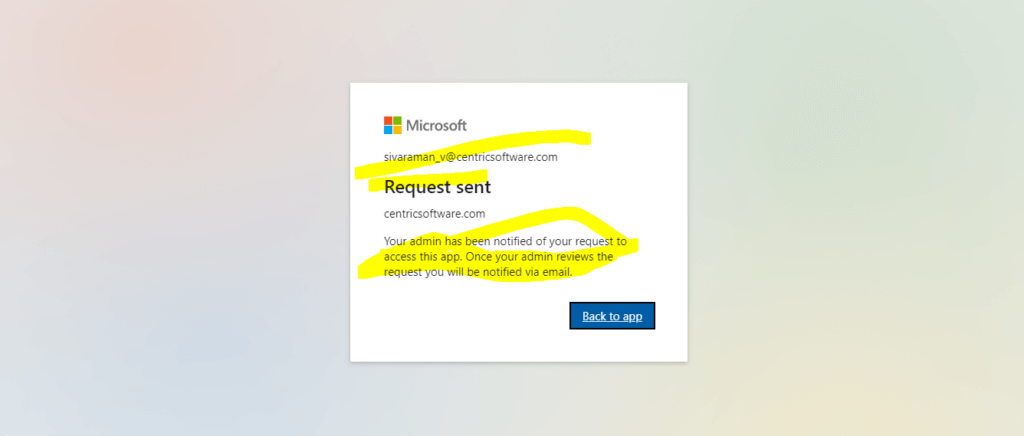
We need to choose justification for this app. Here I just copied this App client ID and paste it.
The request is sent to Admin for getting Approval.
Once Admin is approved, we will be able to access the Function APP.
Web App Using Managed Service
In the event the app is moved between subscriptions/tenants, managed identities for App Service and Azure Functions won’t behave as planned. The feature needs to be disabled and enabled again in order for the app to acquire a new identity. Access rules for downstream resources must also be modified to use the new identity. The app may simply access other Azure AD-protected resources like Azure Key Vault with the help of a managed identity from Azure Active Directory (Azure AD). We don’t need to provide or rotate any secrets because the Azure platform manages the identity.
Two different identities can be granted to the application:
Basically, the application is associated with a system-assigned identity, which is removed when the app is deleted. A system-given identity can only be assigned to one program.
An independent Azure resource that can be given to the app is a user-assigned identity. Multiple identities supplied by users are possible for an app.
We created identity by using the below steps:
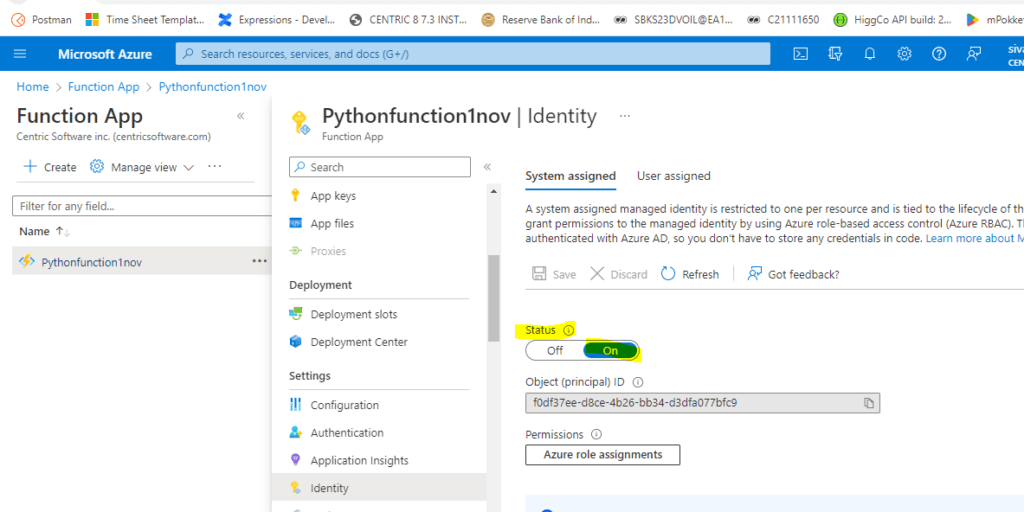
Find the Settings group by scrolling down in the left navigation of your app’s page.
Choose Identity.
Change Status to On under the System Assigned tab. Press Save.
First, we must construct the identity before adding its resource identifier to the app’s configuration in order to create an app with a user-assigned identity.
Follow these guidelines to create a user-assigned managed identity resource.
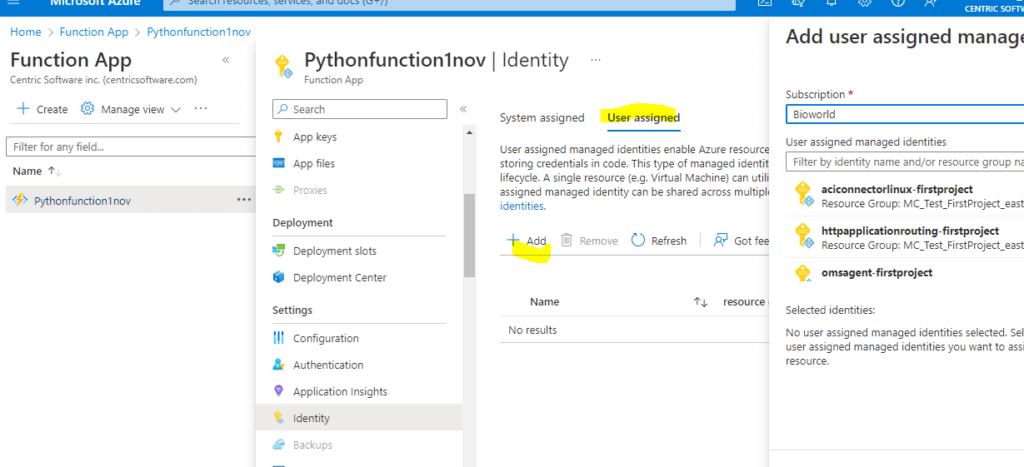
To Find the Settings group, scroll down in the left menu on the app’s website.
Choose Identity.
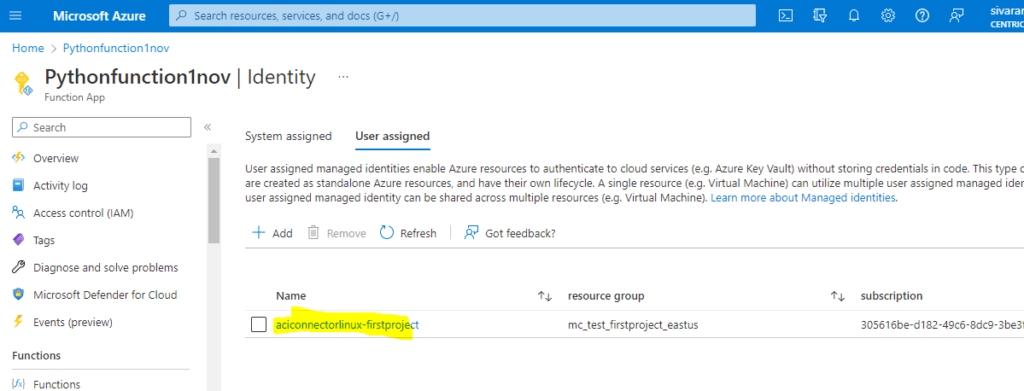
Click Add under the User Assigned tab.
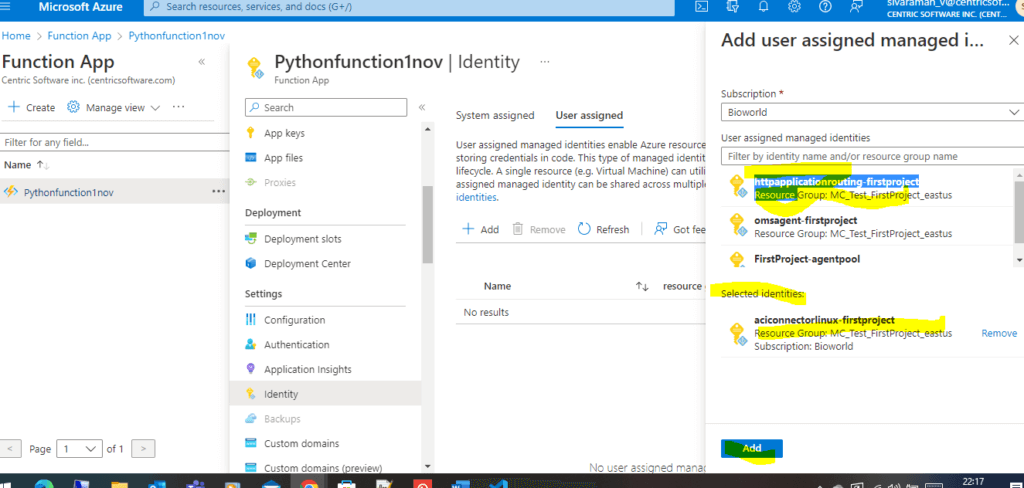
Look for and choose the identification you generated before. Select Add.
I can select any of the identities below and click Add.
Its added.
Conclusion
In conclusion, users are authenticated against an Azure AD tenant by using the Azure Functions Authentication Service. The integrated authentication method of Azure AD is set up to be used by the Azure Functions Authentication Service. Despite the fact that function keys can help prevent some unauthorized access, the only way to properly secure the function.
Recommended Articles
This is a guide to Azure Functions Authentication. Here we discuss the introduction, how to setup authentication for azure functions and web apps using managed service. You can also look at the following articles to learn more –