Updated March 16, 2023
Introduction to Azure Service Endpoint
The following article provides an outline for Azure Service Endpoint. Azure service endpoints promote network security by allowing vnet traffic to communicate with service resources without using the internet. It provides direct connectivity to azure services via an optimized route. It serves as the network’s backbone. Azure endpoints will allow us to secure our azure services, which are critical in virtual networks.
Key Takeaways
- The service endpoint of the virtual network provides secure and direct connectivity for azure services, which are optimized from the azure network.
- The azure service endpoint allows us to secure our service resources into the virtual network, service endpoint allows the private IP addresses in vnet.
What is Azure Service EndPoint?
Azure virtual machines interact with Azure storage accounts and Azure SQL because they are in the same virtual network. The azure virtual machine is connecting to the public endpoint. We enable the endpoint in two ways. The first step is to add the service endpoint to the virtual network and specify the subset.
We must visit the platform service when selecting an endpoint. For example, we can say that the SQL server is adding the subnet and virtual network that we configured into the virtual networks and firewalls. Azure service endpoint allows virtual network resources to connect to the public endpoint using private IP addresses.
How does Azure Service EndPoint Work?
At the time, azure service endpoints were released for azure storage accounts and Azure SQL. At the time of enabling the service account, we are enabling the same by using two ways. Enable the service endpoint by using a virtual network, and second, we need to visit to the platform service.
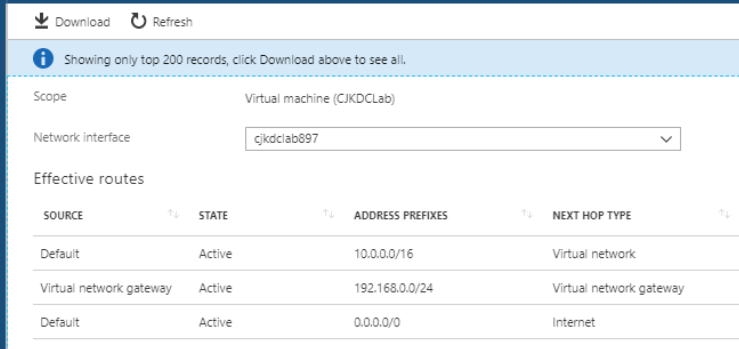
Even if we have not enabled the endpoint of the service, we can perform the step later. We include the route inherited from the specified subnet in the comparison. The new route includes the public range for the Azure SQL service, and the traffic is coming from the virtual network’s service endpoint. It will ingress into the Azure fabric, which was forwarding traffic via the public endpoint. It is important for stating the endpoints that were not removing the public endpoint from the azure storage accounts and the azure SQL; it’s the redirection in traffic.
Below figure shows the effective route as follows:
Configuration – (Azure Service Endpoint VM and Storage Accounts, Storage Explorer Setup)
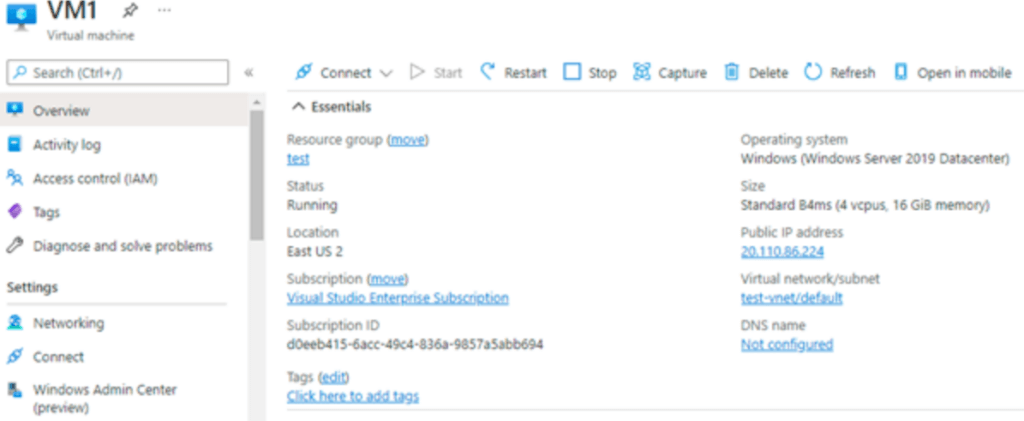
At the time of understanding the working of service endpoints, we need a few resources in place. To configure the azure service endpoints, we require the single windows VM and two storage accounts to understand the service working endpoints. In the below example, we are taking the VM size as B4ms and defining the OS as windows server 2019.
We need storage explorer to be installed in our VM to understand the access of service endpoints and storage accounts. We are defining two storage accounts we are creating below storage accounts as follows.
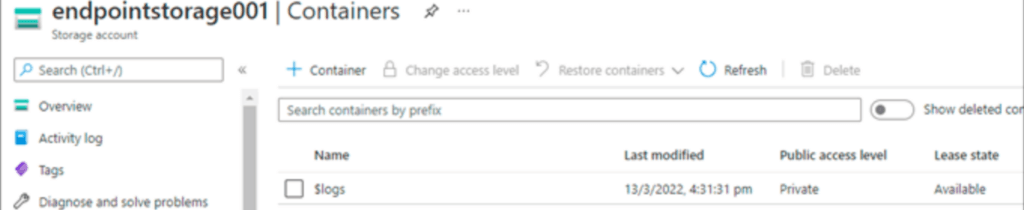
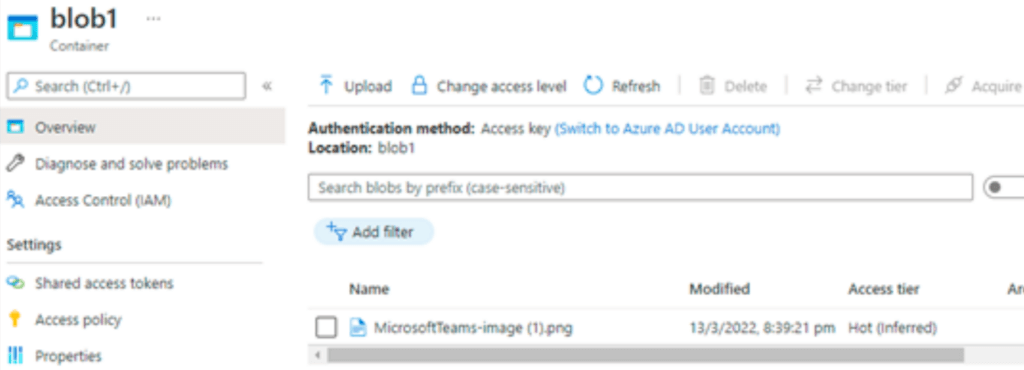
In the below example, we are creating the containers name as blob1 in both accounts and updating the sample files.
Now in the below example, we are accessing the storage accounts from the inside VM by using the storage explorer.
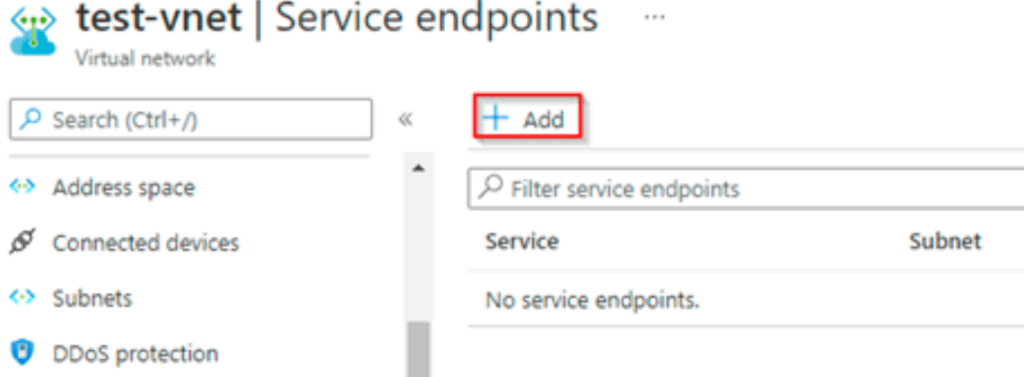
In the below example, we can see how we set up the service endpoints and their functionality as follows.
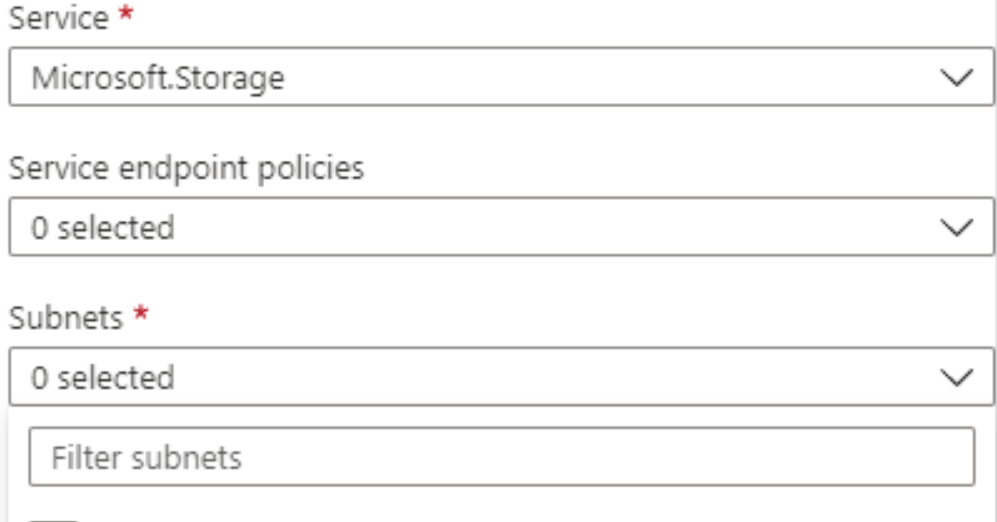
In the below example, we are selecting the subnet for which we are attaching the endpoint as follows.
Explanation of Azure Service endpoint
Azure service endpoint storage accounts will contain multiple redundancy options such as zone redundant storage, locally redundant storage, and geo-redundant storage. So the GGRS redundancy at the time of storing data in the storage account, another copy of the data is created, and the same is stored in the region pair.
Suppose we contain the service endpoints in place from the VN for connecting to the storage account into the primary region. If the primary region goes down, the connectivity to the secondary region is done by using the service endpoint. Suppose we have access to the account of backup storage in the secondary region; then we have another virtual network in place for the new endpoint; the new VM will contain secure access to the account of backup storage.
Enabling
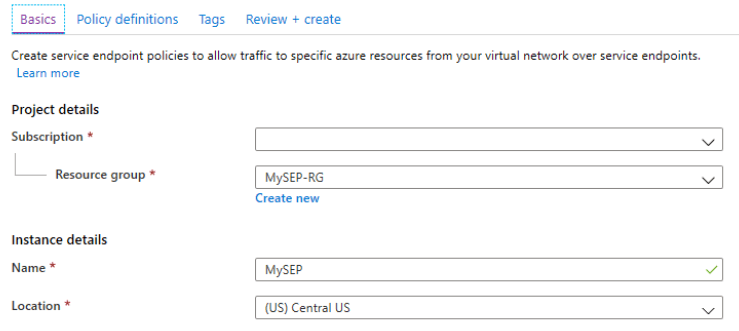
To enable the service endpoint policy, we need to follow the below steps as follows:
We are creating and enabling the policy as follows:
1. Select the create resource tab, and in the panel type, the service endpoint policy, then click on create as follows.
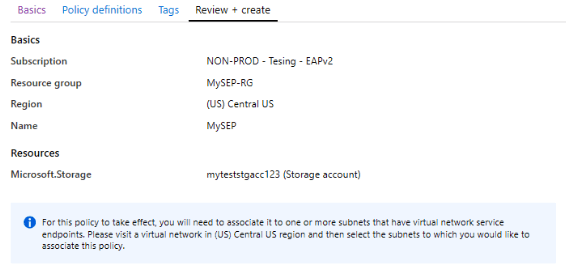
2. After the page opens, we need to enter the following information as we have entered in the below figure.
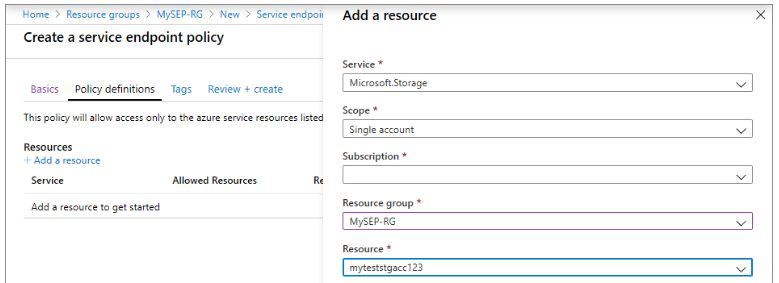
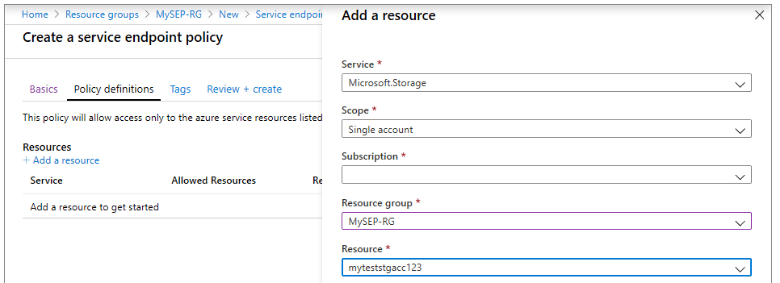
3. After defining the options, we are adding the resources and enter the below information as follows.
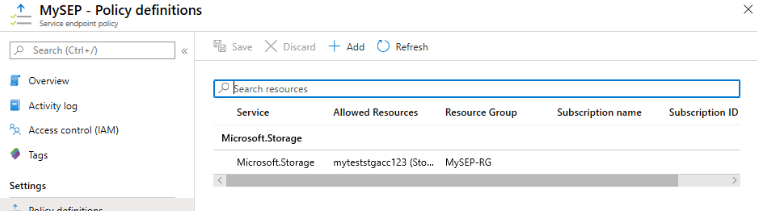
4. After adding the resources now in this step, we are enabling and creating the azure service endpoint policy as follows.
Policies
The feature name as service endpoint policies will be present in the Azure service endpoint, allowing us to restrict access from the VNET where we have deployed the endpoints from the specific storage accounts. To view the endpoint policy in the Azure portal, we need to provide the following information.
After creating the policy, we gave associated with the subnet by using subnet association as follows.
Private Endpoint Example
In the below example, we are creating the private endpoint by using Azure CLI. The below steps shows how we can create a private endpoint as follows:
1. In the first step, we are creating the resource group as follows.
Command:
az group create \
--name end-rg \
--location eastusOutput:
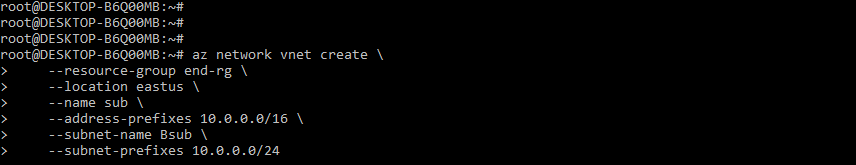
2. After creating the resource group now, in this step, we create the virtual network and the bastion host as follows.
Command:
az network vnet create \
--resource-group end-rg \
--location eastus \
--name sub \
--address-prefixes 10.0.0.0/16 \
--subnet-name Bsub \
--subnet-prefixes 10.0.0.0/24Output:
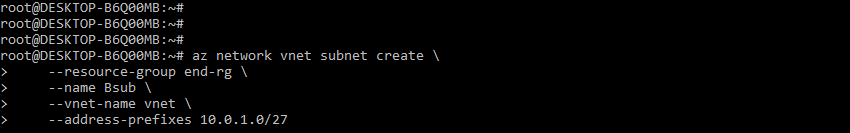
3. After creating the virtual network in this step, we create the bastion subnet as follows.
Code:
az network vnet subnet create \
--resource-group end-rg \
--name Bsub \
--vnet-name vnet \
--address-prefixes 10.0.1.0/27Output:
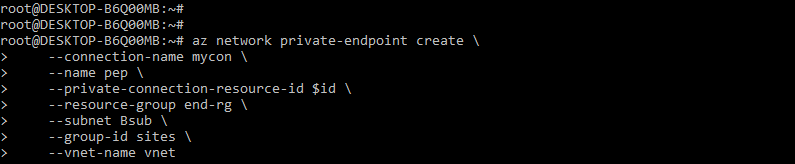
4. After creating the bastion subnet now, in this step, we are creating the private endpoint as follows.
Code:
az network private-endpoint create \
--connection-name mycon \
--name pep \
--private-connection-resource-id $id \
--resource-group end-rg \
--subnet Bsub \
--group-id sites \
--vnet-name vnetOutput:
Features
Below is the feature of the azure service endpoint. It will contain multiple features as follows:
- Improved security for the azure service endpoint – We are not using overlapping spaces, so the azure service endpoint is secured.
- Azure service endpoint routing – This contains the optimal routing, and it forces the internet traffic into it.
- Less management overhead with a simple set – We no longer need to use public IP addresses in our virtual network for securing the resources from the firewall.
- Service endpoint connectivity – Azure service endpoint contains the connectivity in service.
- Service endpoint policies – We are defining our own policy for the azure service endpoint; this feature is very important.
- Connectivity from the secondary location – We can access the service endpoint from the secondary location when our first endpoint will fail.
Conclusion
Azure virtual machine is interacting with the azure storage accounts, and azure SQL contains the same virtual network. The azure virtual machine is accessing the public endpoint. Azure service endpoint is promoting network security which was allowing the vnet traffic which was communicating with the service resources without going over the internet.
Recommended Articles
This is a guide to Azure Service Endpoint. Here we discuss the introduction, working, configuration, example, and features. You can also look at the following articles to learn more –