Updated August 10, 2023

The Basic Fundamental of Networking
Most people want to become an IT technicians, but all they know about our hardware. Some start learning Linux Servers and some Windows Servers, but everyone gets stuck at one point, which they don’t consider necessary. And this is what I will be blogging about today. It’s all about clearing the fundamentals of networking. In short, I mean TCP/IP and other similar protocols.
The Most Important Networking Protocols – TCP/IP
Before I get on to the basics of home networking, let me ask you a simple question. Have you ever imagined how computers talk to each other when sending messages via LAN, WAN, or MAN? Understanding the way computers interact is essential when becoming a network administrator. Networking Protocols are necessary not only for a System Admin but also for developers who build applications related to servers using JAVA or Socket based programming like Python or bash.
Computer networking utilizes a distinct set of IP protocol suites. The most commonly used protocols are TCP and IP. TCP stands for Transmission Control Protocol, and IP stands for Internet Protocol. Every protocol has a specifically layered architecture and its functionalities. Let’s take a look at the IP Protocol first:
The IP Protocol for Basic Fundamentals of Networking
The IP or the Internet Protocol defines the principles of networking communication protocols. This IP protocol helps to relay multiple datagrams over network boundaries. The IP protocol’s primary function is to provide routing functions to establish inter-networking connectivity to enable the Internet. The IP Protocol’s primary task is to deliver packets from one host to another only depending upon the IP addresses present in the headers of the packets.
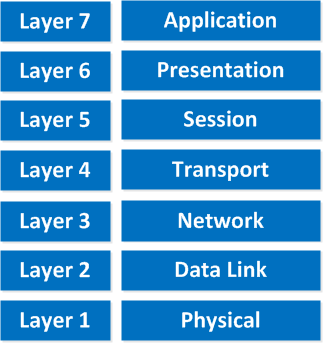
All of the layers of this IP protocol have their own set of instructions to carry out. The TCP and IP typically consist of 4 layers here, i.e., the Application layer, the Transport layer, the Data Link Layer, and the Network Layer. However, the OSI networking model (Open Systems Interconnection) typically points out 7 different layers.
So, let’s take a look at all of them as follows:
1. The Basic Fundamental of the Application Layer
The Application layer is the topmost layer of the TCP and IP protocol suite in Networking. This specific layer transfers data to computers from one end to another with the help of applications and processes that use transport layer protocols. These applications and processes carry specific instructions to execute a task and then communicate with the second layer, which is the Transport Layer. Following are a few popular application layer protocols:
- HTTP or Hypertext transfer protocol is mainly used in modern web browsers. It is the actual foundation of the World Wide Web (www). HTTP is a request and response type protocol that performs actions on behalf of the client and requests a response from the server for the same. The request may contain images, text, audio, and video in return. Although people widely use HTTP, they replaced it with HTTPS, or Hypertext Transfer Protocol Secure, because it is highly insecure. Developers developed HTTPS to authenticate a website’s certificate and to protect the privacy of transmitted data.
- FTP or File transfer protocol for transferring data over various networks. FTP uses the client and server architecture model to control and transfer computer data. The server is configured by default to connect automatically and anonymously, but it can be configured to use a plain text password for authentication. Additionally, SSL (Secure Sockets Layer), TLS (Transport Layer Security), and SSH (Secure Shell) can be used to encrypt the data being transferred. Among these options, SSH is the most commonly used, and it utilizes Public Key authentication, which is highly secure. SSL is also entirely safe but can be decrypted with applications like SSL strip via a Man in Middle attack. The most popular SSH tool for Windows is Putty, an SSH and Telnet Client, along with being open source (http://www.putty.org/).
- SMTP, or Simple Mail Transfer Protocol, transmits emails. SMTP is a text-based protocol that works on the TCP and IP connection. An SMTP connection consists of three things: MAIL to determine a returning address, RCTP to connect to the recipient, and DATA, which is the message’s body. This DATA also consists of a message header for it to work correctly.
- SNMP, or Simple network management protocol, is an IP-based protocol. SNMP collects information about the IP addresses from various machines consistently. There have been multiple versions of SNMP protocols, such as the SNMPv1, SNMPv2, and SNMPv3. Routers, Switches, modems, and servers support the SNMP protocol.
2. The Basic Fundamental of the Networking Presentation Layer
This layer converts or does the job of translating data such as character encoding like Unicode or UTF8, encryption/decryption, and data compression between a networking device and a software application. A few examples would be JSON, XML, HTML, CSS, and many more. This Layer is more useful when doing secure transactions such as banking and transferring money to an account because the data needs to be encrypted and decrypted. This layer is also responsible for converting formats like UTF8 to ASCII. Although other application layers can do the encryption and decryption or the session layer, each has disadvantages, which is why this layer takes care of that. Nowadays, most applications treat the application and presentation layers equally when coding and transmitting data over the network.
3. The Basic Fundamental of the Networking Session Layer
In Networking, the session layer is responsible for opening, closing, and managing an end-user application session. This session can include multiple requests and responses occurring inside the software. If disconnection occurs or if there are any packet losses, the OSI session layer Ip protocol tries to recover the connectivity. If it fails to do so, then it tries to close totally and opens a new connection. This can either be a full or a half-duplex operation. This layer also handles the combining of packets and sorting in proper order. When you download something from BitTorrent, you can see packets downloaded but do not follow a synchronized order. The session layer combines packets from different streams, enabling them to synchronize correctly.
4. The Basic Fundamental of the Networking Transport Layer
The transport layer is the one that communicates with the application layer to transfer data to the appropriate hosts. The TCP and the UDP protocols are the two most important protocols used almost everywhere at transport layers. However, the TCP (Transmission Control Protocol) connections are more reliable when compared to the UDP (User Datagram Protocol) connections. Each of these has its own set of advantages and disadvantages and is used according to specific requirements.
The Transmission Control Protocol distributes the data received from the application layer into precisely sized chunks of data and then transfers these packets part by part into the network. It first acknowledges the packets it receives, requests acknowledgments for the packets sent, and then sets response timeouts to retransmit any packet if their acknowledgment is not received before the timeout expires. This is the main reason this is considered a reliable connection since it takes care that the opposite host receives every packet transmitted. People mainly use this protocol when downloading and uploading large files because packet loss can cause corruption in the uploaded or downloaded data.
User Datagram Protocol, on the other hand, is much simpler but unreliable than Transmission Control Protocol. In UDP, no acknowledgment is done for any data sent or received to and from the host. Thus there are high chances of packet drops and leaks.UDP is considered unreliable and not used for quality data transmission because of this main reason. YouTube or Vimeo mostly use this type of protocol when streaming videos because it can handle a few packet drops without affecting the user experience.
5. The Basic Fundamental of Networking Network Layer
The Internet Layer, also known as the Network Layer, routes data over networks using the IP protocol to distinguish between addresses.
It uses popular protocols such as ICMP and IFMP. The ping command uses the Internet Control Message Protocol (ICMP) to check whether the host is active or down. The ICMP is one of the most important protocols of the IP protocol suite. ICMP also sends error messages over the network to indicate if a host is down, unresponsive, or only available via the wake-on LAN feature, among other things.
6. The Basic Fundamental Of Networking Data Link Layer
The Network Interface Layer also called the Data Link Layer, provides drivers for various devices in the Operating System. These drivers are of the NIC or the Network Interface Card present in the system. The network cards and their properly configured device drivers are responsible for communicating and transferring data onto networks. Without a network interface card, communication is not possible. Devices share this data either wirelessly using routers and Wi-Fi or via cables such as cross-wired or RJ-45 cables. The protocols used to transfer data here are the ARP (Address Resolution Protocol) and the PPP, i.e., Point to Point Protocol.
7. The Basic Fundamental Of Networking Physical Layer
The Physical layer is the topmost layer in the OSI model of computer networking. This layer typically consists of networking hardware. Due to the variety of networking devices available in the market, this is probably the most complex networking layer in the OSI architecture. The job of this layer is to transfer raw bits over the physical hardware via the connecting nodes. This layer typically consists of hardware such as wireless hardware, i.e. the Wi-Fi, the cables, the connectors, the network interface cards, and many more.
The Basic Fundamental of Networking Ports, IP Addresses, and MAC Addresses
Basics of wireless networking Now that you know how essential internet connectivity works, let’s look at the most critical part of how the packets find their way to the proper hosts. Think of this IP address, ports, and Mac address as the person’s default physical address. For example, let’s say the person Mr. Smith has an Address as 21, New Wing Tower, High Roller Street. Here the MAC ID is the New Wing Tower, which is the name of the building or the society that never changes.
The High Roller Street is the area or the street address, which is the IP Address here. Since there are several streets to reach a destination, this is similar to an IP Address since the IP address can change depending upon the network DHCP. And finally, the port is the Room Number which in our case is 21. This whole scenario works like this. Say, for example, you are about to receive a courier at your above address, but if you give the wrong room number, the courier may reach a closed room that isn’t even there.
If a firewall has closed the other port or is already busy with another packet’s connectivity, an incoming packet given the wrong port number may not reach the intended address.
Understanding the languages of networking is not that hard. It only takes a person willing to dig deeper and ready to get their hands dirty. These are just the basics of networking. You can learn in detail by reading about packet transmission and how the connectivity takes place by reading the SYN and ACK methods, which I have not mentioned here. Consider learning a CCNA book, which will cover all networking aspects.
Recommended Articles
This is a guide to the Basic Fundamental of Networking. Here we discussed the basic concepts and the IP protocol for the basic fundamental of networking. You can also look at the following articles –