Updated April 1, 2023
Definition of DBMS Checkpoint
In database management systems when we execute multiple transactions at the same time log files are created and it utilizes system memory space for storage. The size of the log file may increase continuously and at one point it is difficult to handle. With the help of a checkpoint mechanism, we can remove all log files from the system and store them as secondary storage disks permanently. We can declare a checkpoint before which the DBMS is inconsistent state and all transactions are committed. Sometimes transaction execution may fail and it requires log files for re-execution, but searching log files is a time-consuming process, so we can overcome this problem by using checkpoints.
Syntax:
checkpoint [ check_point_interval ];Explanation:
In the above syntax, we use checkpoint with checkpoint interval time. When checkpoint interval time is specified then the SQL server database engine tries to complete the task within the specified checkpoint interval time. The check_point_interval time must be an integer value and it is always greater than zero. A checkpoint is an advanced option for SQL server engines to execute transactions.
How Checkpoint works in DBMS?
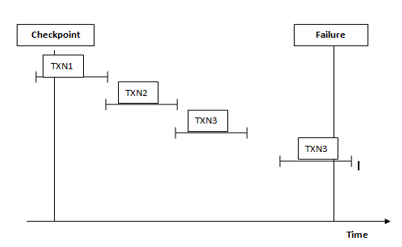
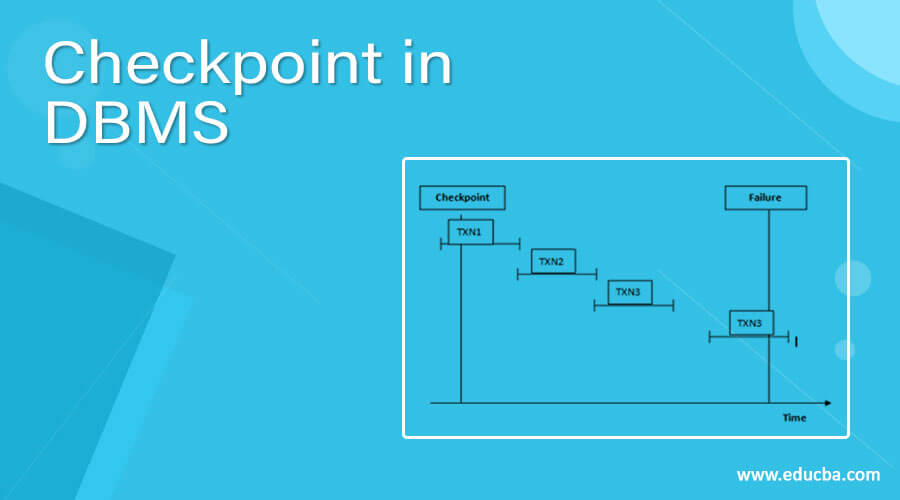
Let’s understand how a checkpoint works in DBMS with the help of the following diagram.
- Checkpoint is used in the recovery system to recover failure transactions. The above diagram shows four transactions such as TXN1, TXN2, TXN3, and TXN4. In which that recovery system reads all files from start to end means it reads TXN1 to TXN4.
- The recovery system maintains two different lists for undo and redo.
- The transaction goes into the redo list if the recovery system sees all logs file with <TXN N, Commit>. In redo list, all log files as well as all the transactions are removed and differently save their logs files.
- For example: in all log file transactions TXN2 and TXN3 will have <TXN N, Start> and <TXN N, Commit>. The TXN1 commits in the log file that is the main reason transaction TXN1 is committed after the checkpoint is crossed. So TXN1, TXN2, and TXN3 go into the redo list.
- In the next step recovery system sees all log files but there is no commit or abort log are found in the undo list so all transactions are undone and all log files are removed from the list.
- If transaction TXN 4 fails will be put into the undo list because transaction TXN4 is not completed.
Different Types of Checkpoint
Database engines support different types of checkpoints as follows.
1. Automatic Checkpoint
Every time each database without a user-defined recovery time, the SQL server database engine generates automatically checkpoints. The advanced recovery server provides maximum time to recover a database during the system restart. Automatic checkpoint depends on the number of log files generated in the database. After a system crash, the recovery time depends on the amount of time required to redo a dirty page which is more than recovery server time.
2. Indirect Checkpoints
In indirect checkpoint, recovery time is maintained at SQL server database engine and it provides more accurate recovery time as compared to the automatic checkpoint that means a number of dirty pages is less as a compared threshold value in the database. In indirect checkpoint, dirty pages in the database are written smoothly in the background. From SQL server 2016 the default checkpoint type is an indirect checkpoint and the default recovery time is 60 sec for the created database. Physically we can easily transfer the data page in indirect checkpoints.
3. Internal Checkpoints
An internal checkpoint is used many times to take a backup of the database. It is also used to add databases, remove database files, and clean SQL servers. This is the main use of internal checkpoints in DBMS. When 70% of transaction log files are created on the server file then the server is shut down.
4. Manual Checkpoints
This is an optional checkpoint provided in DBMS to provide internal time manually by using checkpoint T-SQL command. If checkpoint interval is not specified then a manual checkpoint will be run for completion, the required interval time depends on dirty pages that operation writes.
Examples
Let’s see a different example of a checkpoint as follows.
Example #1: Database
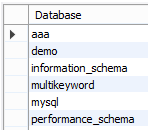
show databases;Explanation:
In the above example, we use the show database command; it shows the number of available databases on the server. Illustrate the final result of the above statement by using the following snapshot.
Example #2: Global Status
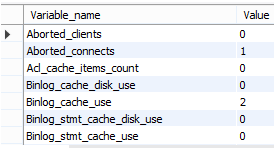
show global status;Explanation:
With the help of the above statement, we can monitor the ratio of disk write operation on the server. Illustrate the final result of the above statement by using the following snapshot.
In the above snapshot, it shows different variable names, and some of them we explain to her as follows.
- Aborted_clients: The number of connections is aborted because a client died without closing the connection properly.
- Aborted_connenct: It shows the number of failed clients that attempted to connect to the MYSQL server.
- Binlog_cache_disk_use: It is used to show number transactions are temporary and uses binary log files to store the transaction statement.
Example #3: To Check Performance of System
ALTER DATABASE sample SET TARGET_RECOVERY_TIME = 25 SECONDS WITH NO-WAIT
GoExplanation:
In the above example, we use the alter database command to increase the performance of MYSQL server. In which we set target recovery time in second as shown in the above statement with no wait state. Illustrate the final result of the above statement by using the following snapshot.
After execution of the above statement, it increases the performance of the server.
Example #4: Indirect Checkpoint
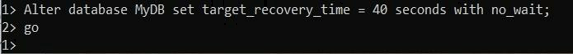
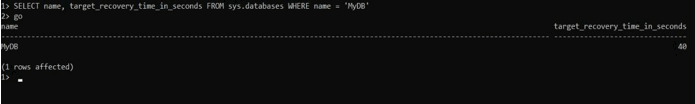
SELECT name, target_recovery_time_in_seconds from sys.database where name = 'MyDB'
goExplanation:
In the above example, we use a select statement to show the target recovery time of the database. Illustrate the final result of the above statement by using the following snapshot.
Conclusion
We hope from this article you have understood the DBMSL checkpoint. From the above article, we have learned the basic syntax checkpoint. We have also learned how we can implement them in SQL Server with different types of DBMS checkpoints with different examples of each operation. From this article, we have learned how we can handle checkpoint in DBMS.
Recommended Articles
We hope that this EDUCBA information on “Checkpoint in DBMS” was beneficial to you. You can view EDUCBA’s recommended articles for more information.