Introduction to Cloud Computing Security
Cloud computing security refers to the security enforced on cloud computing technology. In simpler terms, cloud security provides support and security to the applications, infrastructure, and procedures and protect data from vulnerable attacks. Cloud security came into existence because of the vast infrastructure of cloud computing systems that runs online and requires proper maintenance daily. There is only one single server where all user data are stored, so in order to utilize resources, in order to restrict user data to get leaked or viewed by other users, cloud computing security handles such sensitive computing resources.
How does Cloud Computing Security Work?
Various organizations now these days have moved to cloud-based computing systems for ease of work and to save time and money. The business has been uplifted to new cloud service technologies replacing the traditional practices. Thus to provide controls and safeguard applications and cloud applications, cloud security came into existence. There are a lot of risks and concerns as far as the online flow of data is concerned, which includes data breaches, data hijacks, unauthorized access, system malfunctions, etc.
Integrating container security best practices, such as securing orchestration tools and implementing robust access controls, is vital for enhancing the protection of cloud-based systems against vulnerabilities. To handle such risk take care of the user needs, and to maintain the database, cloud computing security ensures proper security by working in various ways:
- Old traditional technologies lack the measurement of giving full protection to the server. With the advent of cloud computing security, the data first goes to the cloud instead of passing directly through the server that acts as a medium. In that way, the data is transmitted to the authorized user who has access to it before directly reaching the server. This maintains data integrity, and the cloud blocks unwanted data, if any, before reaching the server.
- The traditional approach consists of applications that filter the data that are very costly and difficult to maintain. The data filtration is done upon reaching its desired network, and in the midway, due to large chunks of data, systems get crashed and shut down completely while filtering good and bad data without proper utilization. The web security services solved it by working on a cloud model where data gets filtered in the secured cloud itself before reaching other computing systems.
- Cloud-based security platforms also work on a private model that consists of a private cloud, isolating the unauthorized data access from the clients ensuring protection from shared security platforms.
- It also works on securing data identity by deciphering the encrypted data to the desired users who need access to it.
Why is Cloud Computing Security Important?
Traditional computing systems offer a great approach to transmitting data but lack a security system that is eventually unable to control data loss and data integrity which is very important in computing systems.
This is where cloud computing security takes the advantage, and it is very important because the security model is purely defined in a cloud server that provides the best resource backup and security when data is concerned. It provides a variety of data services, including data backup, virtual desktop, and other communicating tools, has increased tremendously from the year 2015.
The cloud model is important in several ways:
- Ensures proper data integrity and safety since the data that gets transmitted online through servers are sensitive data.
- Lots of hacking cases have been observed while transmitting data that is a very common topic for any business purposes, but cloud computing technology assured us the best safety feature system for all cloud storage devices and applications.
- While cloud technology provides cloud provider services at a very effective cost, the security systems also came to provide the most efficient platform at such cost benefitting for every user.
- There have been various government regulatory authority services that ensure why cloud security and choosing the right cloud provider are equally important. Under the Data Privacy Act, the cloud providers perform efficiently, which outsources the organization’s critical data over the cloud protecting every customer’s private data utilizing every service of the cloud provider.
- The third-party providers also get in touch with the cloud systems that provide necessary security and data privacy and also encrypt data before reaching directly to the client.
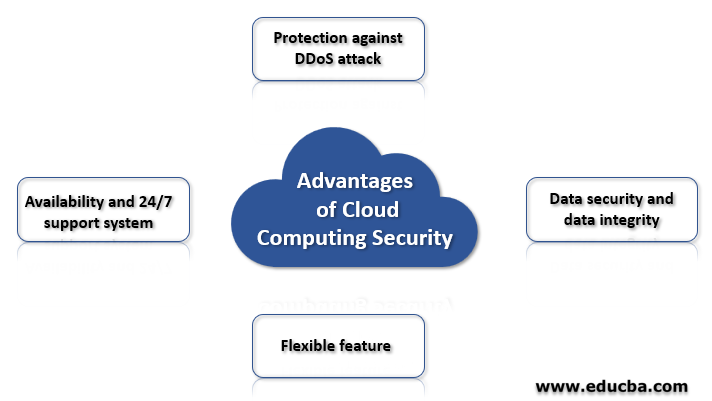
Advantages of Cloud Computing Security
Cloud computing has created a tremendous boom in the recent technologies that help the business to run online, to save time and be cost-effective. Therefore, besides having a lot of advantages of cloud computing systems, cloud computing security also plays a major role in this technology that ensures clients to use it without any risk or tension.
Below are the advantages of cloud security:
- Protection against DDoS attack: Many companies face the Distributed Denial of Service (DDoS) attack that a major threat that hampers company data before reaching the desired user. That is why cloud computing security plays a major role in data protection because it filters data in the cloud server before reaching cloud applications by erasing the threat of data hack.
- Data security and data integrity: Cloud servers are real and easy targets of falling into the trap of data breaches. Without proper care, data will be hampered, and hackers will get the hands of it. Cloud security servers ensure the best quality security protocols that help in protecting sensitive information and maintain data integrity.
- Flexible feature: Cloud computing security provides the best flexibility when data traffic is concerned. Therefore, during high traffic user gets the flexibility in a happening server crash. The user also gets scalability resulting in cost reduction when the high flow of traffic ends.
- Availability and 24/7 support system: Cloud servers are available and provide the best backup solution giving a constant 24/7 support system benefitting the users as well as clients.
Conclusion
The big organizations must seek out the best cloud computing security solutions that will give them reliability, security, and availability. The cloud servers must be bundled with the best cybersecurity features providing a comprehensive solution for cloud data.
Recommended Articles
This is a guide to Cloud Computing Security. Here we discuss the working of cloud computing security along with its importance and advantages. You may also look at the following articles to learn more-