Introduction
Cloud computing security architecture is the comprehensive framework of policies, procedures, controls, and technologies to protect cloud-based systems, data, and infrastructure. It encompasses various security measures implemented to safeguard cloud resources against unauthorized access, data breaches, cyber threats, and compliance violations. It is a holistic approach to securing cloud environments, encompassing various technical, operational, and compliance measures to protect against evolving cyber threats.
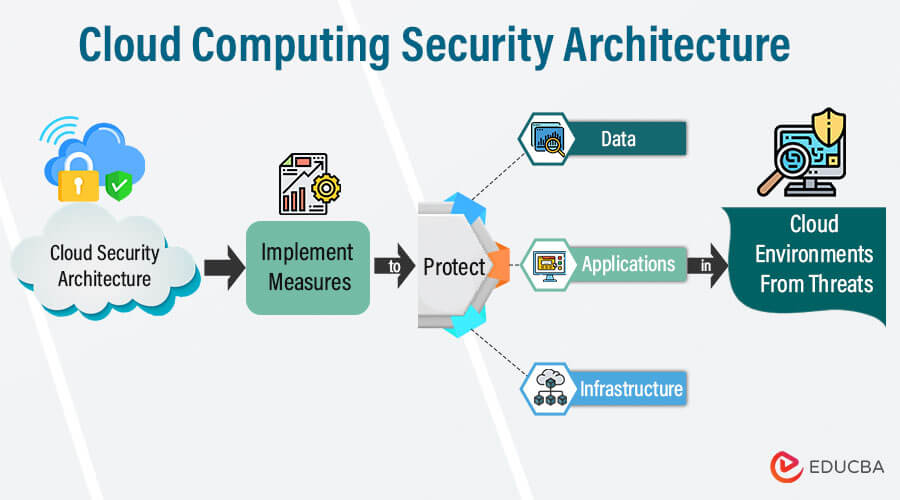
Table of Contents
Key Components of Cloud Security Architecture
Identity and Access Management (IAM)
IAM serves as the gatekeeper, controlling Who can use cloud resources and what can be done by them. It grants users only the access level necessary for their tasks.
- Authentication: verifies the identity of users and entities accessing the cloud environment through passwords, multi-factor authentication (MFA), biometrics, or security tokens.
- Authorization: Granting appropriate permissions and privileges to authenticated users based on their roles, responsibilities, and least privilege principles.
- User Provisioning and De-provisioning: Automated processes for provisioning user accounts, assigning roles, and revoking access when users leave the organization or change roles.
Data Security
Cloud data security protects sensitive data from unauthorized access, disclosure, alteration, or destruction. Data is an organization’s lifeblood, and securing it in the cloud is paramount. Key components include:
- Encryption: This process involves encrypting data at rest (stored data) and in transit (data in motion) using robust encryption algorithms and secure protocols like SSL/TLS.
- Data Loss Prevention (DLP): Implementing policies and procedures to prevent sensitive data from being transmitted or leaked without authorization through monitoring, classification, and encryption.
- Data Masking and Anonymization: Concealing sensitive information in non-production environments to prevent unauthorized access during development, testing, or analytics.
- Data Residency and Compliance: Ensuring compliance with data privacy regulations and industry standards by maintaining data residency, data sovereignty, and data protection requirements.
- Data Classification: Classify data according to sensitivity and use the proper security controls accordingly.
Network Security
Network security protects cloud infrastructure, applications, and data from unauthorized access, attacks, and vulnerabilities. Securing the pathways within your cloud environment is crucial. Network security involves:
- Firewalls: Filtering and inspecting network traffic to enforce security policies and prevent unauthorized access to cloud resources.
- Intrusion Detection and Prevention Systems (IDS/IPS): Monitoring and analyzing network traffic for indications of malicious behavior or security threats and taking automated actions to block or mitigate attacks.
- Virtual Private Networks (VPNs): Creating secure, encrypted connections between remote users, devices, or networks and cloud environments to ensure secure communication and data transmission.
Infrastructure Security
Infrastructure security involves securing cloud environments’ underlying components and resources, including servers, storage, networks, and virtualization platforms. Whether it’s a public cloud, private cloud, or hybrid model, it includes:
- Vulnerability Management: involves identifying, assessing, and remediating security vulnerabilities in cloud infrastructure components through regular scanning, patching, and configuration management.
- Asset Management: involves inventorying and tracking cloud assets, configurations, and dependencies to ensure visibility and control over the entire infrastructure.
- Security Hardening: involves implementing best practices, standards, and benchmarks to harden cloud infrastructure components and minimize security risks.
- Incident Response and Forensics: Establishing procedures and tools for identifying, looking into, and handling security incidents in cloud environments, including incident triage, containment, and recovery.
- Physical Security: Ensuring the physical security of data centers where cloud infrastructure resides.
- Resource Access Control: Restricting access to cloud infrastructure components like storage and compute resources.
Application Security
Application security protects cloud-native and third-party applications from vulnerabilities, exploits, and security threats. Application security involves:
- Secure Development Lifecycle (SDL): Integrating security into the complete process of developing software, from designing and coding to testing and implementing, through practices such as secure coding, code reviews, and security testing.
- Web Application Firewalls (WAF): Deploying WAFs to protect web applications against widespread assaults like cross-site scripting (XSS), SQL injection, and application layer DDoS attacks.
- API Security: This involves securing APIs (Application Programming Interfaces) used to integrate cloud services and applications by implementing authentication, authorization, encryption, and rate-limiting controls.
- Container Security: Securing containerized applications and microservices running in cloud environments through container image scanning, runtime protection, and Kubernetes security policies.
- Secure Coding Practices: Following secure coding principles during application development to minimize vulnerabilities.
- Vulnerability Scanning: Regularly scanning applications for known vulnerabilities and patching them promptly.
Security Design Principles
Security design principles are foundational guidelines and best practices organizations follow to design and implement secure cloud environments. These principles adequately protect against various threats, including unauthorized access, data breaches, malware attacks, and other security risks, to ensure that cloud-based systems and data are protected.
Zero Trust
This principle assumes that no user or device, inside or outside the network, is inherently trustworthy. Every access request must be thoroughly authenticated and authorized before granting access.
- Identity Verification: Verifying the identity of users, devices, and applications before granting access through multi-factor authentication (MFA), device posture checks, and identity-based policies.
- Least Privilege Access: Restricting access permissions to the minimum level necessary for users to perform their tasks.
- Continuous Monitoring: Monitoring user and entity behavior, network traffic, and access patterns in real-time to detect anomalous or suspicious activity.
Defense in Depth
Defense in Depth is a layered approach to security that involves deploying multiple layers of security controls. It creates a layered defense that makes it more difficult for attackers to infiltrate your system. If someone breaches one layer, others can still impede further progress.
- Perimeter Security: involves securing the network perimeter with firewalls and intrusion detection systems-intrusion prevention systems (IDS)/(IPS) to filter and inspect incoming and outgoing traffic.
- Endpoint Protection: This involves deploying endpoint security solutions such as antivirus software, host-based firewalls, and endpoint detection and response (EDR) tools to protect individual devices from malware and unauthorized access.
- Data Encryption: Sensitive data encryption both in transit and at rest using robust encryption algorithms and secure protocols to prevent unauthorized access and data breaches.
Least Privilege
It is a security principle that restricts users and entities to the minimum access permissions required to perform their tasks or functions. Organizations can reduce the possible harm brought about by compromised credentials or insider threats by only granting the minimum of privileges.
- Role-Based Access Control (RBAC): Assigning access permissions based on users’ roles, responsibilities, and job functions to ensure they can access only the resources and data necessary for their work.
- Just-In-Time (JIT) Access: Temporarily granting elevated access privileges to users for a specific period or task and revoking those privileges once the task is completed.
- Privilege Escalation Controls: Implement controls and approval workflows to govern the granting of additional access privileges beyond the user’s default permissions.
Visibility and Monitoring
Visibility and Monitoring refer to continuously monitoring and analyzing security-related events, activities, and behaviors within an IT environment to detect and respond promptly to security incidents.
- Security Information and Event Management (SIEM) Gathering, connecting, and evaluating security event data from various sources to identify patterns, anomalies, and potential security threats.
- Network Traffic Analysis: Monitoring and inspecting network traffic in real time to detect suspicious behavior, malicious activities, and unauthorized access attempts.
- User Activity Monitoring involves tracking and auditing user actions, access requests, and privilege changes to detect insider threats, account compromises, and unauthorized activities.
- Incident Response and Forensics: Establishing procedures and tools for carrying out forensic investigations, responding to security incidents, and recovering from security breaches.
Designing a Secure Cloud Infrastructure
Designing a secure cloud infrastructure involves implementing comprehensive security measures to protect cloud resources, data, and applications from unauthorized access, data breaches, and cyber threats. This is an outline of the key steps involved:
1. Planning and Assessment:
- Identify Assets: Determine the data types, applications, and resources hosted in the cloud, including sensitive and critical assets.
- Assess Risks: Make a detailed risk assessment to find possible security threats, vulnerabilities, and compliance requirements relevant to your cloud environment.
- Set Objectives: Define security goals and objectives, such as ensuring data confidentiality, integrity, and availability, complying with regulatory requirements, and mitigating specific threats.
2. Design and Implementation:
- Select a Cloud Provider: Choose a reputable cloud provider with with a proven track record in security and offerings that align with your security requirements.
- Implement Identity and Access Management (IAM): Establish strong IAM policies with multi-factor authentication and least privilege access control.
- Secure Your Data: Encrypt data at rest and in transit, implement data loss prevention (DLP) controls, and classify data based on sensitivity.
- Fortify Your Network: Configure firewalls, deploy intrusion detection/prevention systems (IDS/IPS), and segment your network.
- Harden Infrastructure Security: Ensure physical security of data centers, follow secure VM configurations, and manage resource access control.
3. Automation and Orchestration:
- Leverage Infrastructure as Code (IaC): Use IaC tools to automate infrastructure provisioning and configuration, ensuring consistency and reducing human error.
- Security Automation: Utilize cloud-native security tools for automated vulnerability scanning, security configuration management, and incident response.
4. Continuous Monitoring and Improvement:
- Log Monitoring: Continuously monitor logs for suspicious activity and potential security incidents.
- Security Awareness Training: Educate your employees on cloud security best practices to foster a security culture within your organization.
- Regular Penetration Testing: Conduct periodic penetration testing to identify and address security vulnerabilities in your cloud environment.
- Incident Response Planning: Create a thorough incident response plan to respond to security breaches and minimize damage effectively.
5. Establish Incident Response and Compliance Processes:
- Develop Incident Response Plan: Create an incident response plan outlining procedures for detecting, responding to, and recovering from security incidents in the cloud.
- Conduct Regular Audits: Perform security audits, assessments, and penetration testing of your cloud infrastructure to identify vulnerabilities and ensure compliance with security standards.
- Monitor and Report Compliance: Implement tools and processes for monitoring and reporting compliance with regulatory requirements, industry standards, and internal security policies.
Cloud Security Frameworks and Standards
Cloud security frameworks and standards are guidelines, best practices, and protocols that help organizations secure their data, applications, and infrastructure in cloud environments.
NIST Cybersecurity Framework
The National Institute of Standards and Technology is referred to as NIST. The NIST Cybersecurity Framework (CSF) provides a voluntary framework built upon accepted norms, regulations, and practices for managing and enhancing an organization’s cybersecurity risk management processes.
Key Features: The CSF consists of five core functions—identify, Protect, Detect, Respond, and Recover—that guide organizations in assessing and enhancing their cybersecurity posture.
ISO/IEC 27001
ISO/IEC 27001 is an international standard for information security management systems (ISMS). It provides a systematic, risk-based approach to managing and protecting sensitive information from security threats.
Key Features: ISO/IEC 27001 outlines specifications for creating, implementing, preserving, and continuously enhancing an ISMS. It includes risk assessment, treatment, security controls, and compliance with legal and regulatory requirements.
Cloud Controls Matrix (CCM)
The Cloud Controls Matrix (CCM) is a framework developed by the Cloud Security Alliance (CSA) that provides a set of controls and security principles for cloud computing environments.
Key Features: The CCM offers a standardized and comprehensive catalog of cloud security controls mapped to leading industry standards, regulations, and frameworks. It aids businesses in evaluating cloud service providers’ security posture and establish security requirements for cloud deployments.
Compliance
Compliance refers to adherence to laws, regulations, industry standards, and organizational security, privacy, and data protection policies in cloud computing environments.
Key Features: Common compliance frameworks and regulations applicable to cloud computing are the General Data Protection Regulation, the Health Insurance Portability and Accountability Act, the Payment Card Industry Data Security Standard, Service Organization Control 2, and the Federal Risk and Authorization Management Program.
Case Study on Netflix and Microsoft Azure
Netflix (NIST Cybersecurity Framework)
Netflix, a leading provider of streaming media and entertainment services operating in the cloud.
Implementation: Netflix has adopted the NIST Cybersecurity Framework to enhance its cybersecurity risk management processes. The company leverages the framework’s Identify, Protect, Detect, Respond, and Recover functions to assess, prioritize, and mitigate cybersecurity risks across its cloud-based infrastructure. By implementing security controls and practices aligned with the framework, Netflix strengthens its resilience against cyber threats. It ensures its streaming platform and customer data’s confidentiality, integrity, and availability.
Microsoft Azure (ISO/IEC 27001)
Microsoft Corporation offers cloud computing services and platforms through Microsoft Azure.
Implementation: Microsoft Azure has achieved ISO/IEC 27001 certification for its information security management system (ISMS), demonstrating its commitment to implementing robust security controls and practices by international standards. By adhering to ISO/IEC 27001 requirements, Azure ensures the security, confidentiality, and availability of customer data and services hosted on its cloud platform.
Emerging Trends and Best Practices
Emerging Trends:
- Security and Artificial Intelligence (AI): Threat detection will progressively rely more on AI and ML. Security systems with AI capabilities can analyze enormous volumes of data to identify real-time anomalies and potential security incidents.
- Shift Left Security: Integrating security considerations throughout the software development lifecycle (DevSecOps) will become even more critical. This proactive approach helps identify and address vulnerabilities early in the development process, reducing the risk of security breaches.
- Cloud-Native Security Tools: As organizations embrace cloud-native architectures, security tools specifically designed for the cloud environment will gain prominence. These tools will offer features like automated security configuration management, workload protection, and container security.
Best Practices to Stay Ahead:
- Invest in Security Awareness Training: Educate your staff on best practices for cloud security to create a culture of security within your organization. Phishing attacks and social engineering remain prevalent threats, and a well-informed workforce is a strong defense.
- Stay Updated on Regulations: The regulatory landscape surrounding cloud security is constantly changing. Keep up with any relevant regulations and ensure your cloud environment remains compliant.
- Focus on Data Security: Implement strong data security practices like encryption, data loss prevention (DLP), and data classification to safeguard sensitive information.
Conclusion
These days, cloud computing is an essential part of any modern IT infrastructure, enabling organizations to achieve scalability, agility, and cost efficiency. However, the widespread adoption of cloud services also brings significant security challenges, as organizations must protect sensitive data, applications, and infrastructure from evolving cyber threats. Cloud Computing Security Architecture is a critical framework for organizations to safeguard their data, applications, and infrastructure in cloud environments. As businesses increasingly leverage the benefits of cloud computing, they must address significant security challenges to ensure their assets’ confidentiality, integrity, and availability.
Frequently Asked Questions (FAQs)
Q1. What are the different cloud service models?
Answer:
- IaaS (Infrastructure as a Service): Provides essential infrastructure components (e.g., virtual machines, storage, networking).
- PaaS (Platform as a Service): Provides a development platform for building and deploying applications.
- SaaS (Software as a Service): Offers ready-to-use software programs delivered over the internet.
Q2. What emerging technologies and trends shape the future of Cloud Computing Security Architecture?
Answer: Some emerging technologies and trends shaping the future of Cloud Computing Security Architecture include:
- Artificial Intelligence (AI) and Machine Learning (ML) for threat detection and response
- Cloud-native security solutions for containers, serverless computing, and microservices
- Edge computing and distributed security architectures
- Quantum-safe cryptography to protect against quantum computing threats
Q3. What are the common security threats in cloud computing?
Answer: Cloud environments face various security threats, including:
- Data Breaches: Unauthorized access to sensitive data.
- Insider Threats: Malicious actions by authorized users.
- Insecure APIs: Vulnerabilities in application programming interfaces.
- Data Loss: Accidental or intentional data deletion.
- Denial of Service (DoS): Overwhelming cloud resources to disrupt services.
- Shared Technology Vulnerabilities: Exploiting shared infrastructure.
- Lack of Visibility and Control: Challenges in monitoring and managing security across cloud providers.
Q4. How does Cloud Computing Security Architecture address insider threats and privileged access management?
Answer: Cloud Computing Security Architecture addresses insider threats by implementing granular access controls, least privilege principles, and robust identity and access management (IAM) practices.
Recommended Articles
We hope that this EDUCBA information on “Cloud Computing Security Architecture” was beneficial to you. You can view EDUCBA’s recommended articles for more information,

