Updated April 1, 2023

Definition of DBMS Locks
DBMS Locks are referred to as the locking protocols that are implemented in DBMS for the control and regulation of concurrency control, which is a practice to accomplish instantaneous procedures but without disagreeing with each other. In the transaction process, several transactions may appeal for a lock on a data record item concurrently. Therefore, for this, we need a tool for handling the locking requests through the DBMS transactions. This type of mechanism is known to be a Lock manager.
This DBMS Lock depends on the technique of message transitory where the transactions and lock manager interchange messages to control the locking as well as unlocking of the data record items. In this tool, the required data structure used for locking the DBMS transaction process is known to be the Lock table where hashing index is implemented.
Syntax:
DBMS Locks tool has the following syntax structure for operating in DBMS table data and accessing the table rows and columns as well:
DBMS Locks offers three levels for the lock procedure which are mentioned as:
1. Row Level Locking: The row-level locking is implemented if the clause WHERE calculates to only a single table row.
2. Page Level Locking: In this type of page-level locking, the locking protocol is executed of the clause WHERE assesses to a group of data.
3. Table Level Locking: This type of table locking is applied if the WHERE clause is absent and the query will access the whole table. But when the update is performed by another user the update cannot done for the whole table. Following is the syntax code for the same:
LOCK TABLE <name_of_table> [<name_of_table>]….IN {ROW EXCLUSIVE / ROW SHARE / SHARE UPDATE / EXCLUSIVE / SHARE ROW EXCLUSION / SHARE } [NOWAIT]How locks work in DBMS?
In DBMS, the locks are tools used for confirming data integrity. In Oracle, the engine locks j table data automatically while running the SQL query commands such as Insert/ Select/ Delete/ Update. This K kind of locking defines implicit locking. In general, the DBMS looks are of two types as follows:
- Binary Locks
- Shared & Exclusive Locks
Let us discuss in detail explained below:
Binary Locks: This Binary locks applied on a data item is responsible to deliver two states either locked or unlocked. Here, a distinct lock may be related to every database item suppose X, if the 1 is the value of the lock on X, then the X item will not be accessed when requested by any database operation. Similarly, when the value is 0 on X then, the data item can be accessed on request.
Shared Lock: The shared locks in DBMS are positioned on resources at whatever time a read operation such as the SELECT command is executed. Numerous shared locks can be set on a resource concurrently.
Exclusive Lock: The exclusive locks in DBMS are positioned on resources at whatever time a write operation such as UPDATE/INSERT/DELETE are executed. But we can place only a single exclusive lock on one resource at one time. It means that the initial user who will obtain an exclusive lock will be able to continue to hold the individual proprietorship of the resource, and here, no other operator can obtain the exclusive lock on that resource.
Generally, a lock can be defined as a data variable that is related to a data item and the lock indicates that operations can be executed on the data item. Therefore, these DBMS Locks aid to coordinate access to the database record items through concurrent transactions. These entire lock requests are generated to the concurrency control manager and further the transaction will proceed just once when the lock appeal is accepted.
Examples
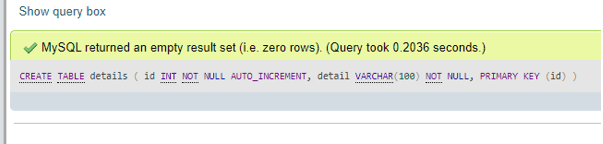
Let us discuss an example to explain the DBMS Locks illustrated as follows considering the transaction process that occurred taking the database tables. Before proceeding forwards, we will create a details table to practice with the locking of table statements as,
CREATE TABLE details (
id INT NOT NULL AUTO_INCREMENT,
detail VARCHAR(100) NOT NULL,
PRIMARY KEY (id)
);Output:
In MySQL, the table can be locked with the below query command that provides the table lock explicitly:
LOCK TABLES name_of_table [WRITE | READ];The syntax code above identifies the table name that one wants to lock either with type READ or WRITE. Similarly, for unlocking those tables we can release the table as follows:
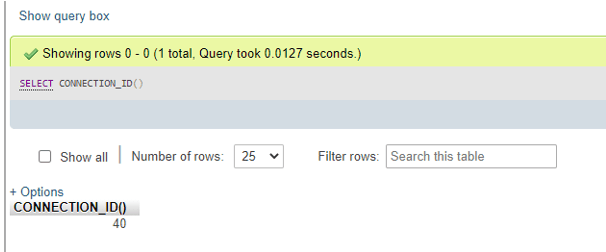
UNLOCK TABLES;Let us discuss the READ operation type to show how lock-in DBMS works. For this initiative, we will check the connection id present by the SQL query as,
SELECT CONNECTION_ID();Output:
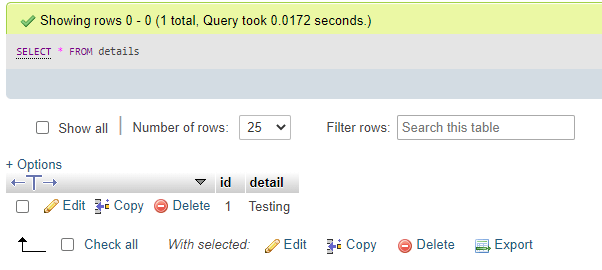
We will then also enter a new record into the table details using the command:
INSERT INTO details(detail) VALUES (‘Testing’);View the data in the table,
SELECT * FROM details;Output:
After this, we will lock the table as,
LOCK TABLE details READ;Again, try to enter a new record into the table:
INSERT INTO details(detail) VALUES (‘Hello’);The server will display an error because we can only perform read operations after locking the table with READ lock,
Error Code: 1099. Table ‘details’ was locked with a READ lock and can’t be updated.
Again, if we connect with a different connection using the connection id function running again and inserting a new record then it will show the waiting status since the table was locked in the first session and not released yet. We can view the detailed info as,
SHOW PROCESSLIST;For this, we will unblock the table from the first session and check the insertion of the next session. Now, it will show proper execution.
For this, the DBMS lock helps to establish concurrency and serializability too.
Advantages and disadvantages
Find some of the listed advantages of the DBMS Locks typed below:
- DBMS Locks delivers Data integrity for the information stored or accessed from the server.
- The transactions being performed in any altered manner to confirm serializability and also to escape deadlock.
- This Lock based protocol is most suitable for read-only type transactions.
- Here, in this DBMS Locks, all read requests are acknowledged always.
- This DBMS Locks can be applied to get an improved level of concurrency with a precise low rate of conflict.
In the same way, we can also list out few disadvantages of DBMS Locks mentioned as follows:
- The protocol DBMS Locks occasionally develops overhead when a transaction setup on a deadline producing rolling back yet again.
Here, the prevention of Deadlock can never be ignored.
We may find a coincidental of transaction starvation because of disagreeing short transactions.
Conclusion
In DBMS, we have various techniques based on protocols followed for the concurrency control that delivers several benefits for controlling the overhead amount which they enforce. DBMS Locks helps to maintain serializability to resolve the conflicts caused among the synchronized transactions. These lock-based protocols provide a mechanism where the transaction cannot write or read the data record unless it attains an applicable lock.
Recommended Articles
We hope that this EDUCBA information on “DBMS Locks” was beneficial to you. You can view EDUCBA’s recommended articles for more information.