Updated May 17, 2023
Introduction to Data Encryption Standard (DES) Algorithm
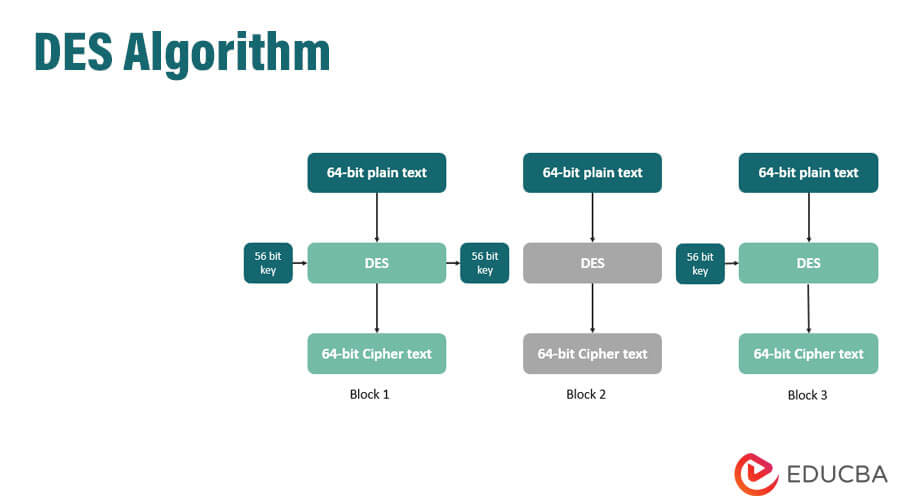
The DES algorithm, also known as the Data Encryption Standard, is a block cipher for encrypting a block of 64-bit plain text with a 56-bit key, resulting in a 64-bit ciphertext. It relies on two cryptographic techniques: substitution and transposition, which are carried out over 16 rounds. The algorithm has two variations: double DES and triple DES.
Key Features
The Data Encryption Standard (DES) is an encryption technique that uses a symmetric-key method of data integration. It was first developed over five decades ago in the early 1970s by IBM, and soon after, the US government adopted it as an official Federal Information Processing Standard in 1977. However, initially, the only use of DES was to encrypt unclassified government computer data.
Later on, recognizing the algorithm’s importance and utility, the US government decided to make it publicly available. This decision resulted in other industries adopting DES for their data encryption needs. The banking industry, finance industry, communication industry, and many more were among the major industries that adopted this encryption algorithm.
Some other important and fascinating facts about the DES algorithm are:
- Designed by IBM and first published in 1975.
- Its successors include Triple-DES and G-DES.
- The ciphertext consists of 64 bits, but only 56 bits are usable.
- It uses 16 rounds for encrypting data.
Creation of DES Logic
This section divides into two sub-categories:
- Encryption Logic
- Decryption Logic
1. Encryption Algorithm
- The Data Encryption Standard (DES) is a block cipher that applies a cryptographic key and its related algorithm to a block of data. This block of data is generally 64 bits in size. However, DES does not follow a bit-by-bit concept. Instead, it processes a complete block of 64 bits of data at once.
- Each 64-bit block of data is enciphered using the secret key, which generates a 64-bit ciphertext through different permutation and substitution methods.
- This process involves 16 rounds that can run under four different modes.
- Each block of data requires individual encryption.
2. Decryption Algorithm
- The decryption algorithm is simply the reverse of the encryption process.
- To decrypt the encrypted message, all steps are processed in reverse order.
Drawbacks of the DES Algorithm
However, the DES algorithm has some major drawbacks that led to its failure. Anyone who wants to decrypt the encrypted message using DES has to use a brute force attack. A brute force attack is a mechanism in which one applies multiple combinations randomly to decrypt the message. In brute force, different combinations are tried one by one until the right combination is found. Therefore, brute force works on the hit-and-trial method, where the intruder tries to hit again and again until they decrypt the message.
The length of the combination determines the number of possible combinations. For example, DES uses 64 bits of encryption logic, out of which 8 bits come into use for parity check. Hence, effective bits are reduced to 56 bits only. These 56 bits form a maximum combination of 2^56. Hence only 2^56 attempts are necessary to decrypt a message using brute force logic. This particular combination of hit and trial methods or brute force is quite low, which makes the algorithm vulnerable to attacks.
Explanation with Illustration
A typical example to illustrate the DES algorithm is to convert plain text, such as “It’s fun to learn,” to encrypted text. One may assume that the DES key for encrypting this plain text is “cipher”. When one applies the encryption logic, the ciphertext will generate as “90 61 0c 4b 7f 0e 91 dd f4 23 e4 aa 9c 9b 4b 0a a7 20 59 2a bb 2d 59 c0.”
One can also use the decryption technique with the same key, “cipher,” on the encrypted message to obtain the original text, which is “It’s fun to learn.”
Why is the DES Algorithm Important?
- It is easy to debate that the DES algorithm is obsolete and not in practice anymore. Even messages encrypted using this algorithm can be decrypted easily. So why is this algorithm still important?
- Well, the simple and straightforward answer to all of the above questions is its fundamental concept. The concept of encrypting the message before transmitting it formed the foundation for the entire security concept for digitally transmitted messages.
- This is the main reason why the DES algorithm holds such a special and important place in the history of cryptography.
Conclusion
The DES algorithm has proven to be a milestone in the importance of network security or the importance of securing messages that need to be transmitted over any medium. The DES algorithm laid the foundation for the encryption technique and provided the first mechanism for applying and achieving this encryption. In addition, the DES algorithm laid the foundation for other algorithms that used the basic concept and further improved it to create better encryption techniques.
Recommended Articles
Here are some further related articles for expanding understanding:

