Updated November 30, 2023
What is Device Management in an Operating System
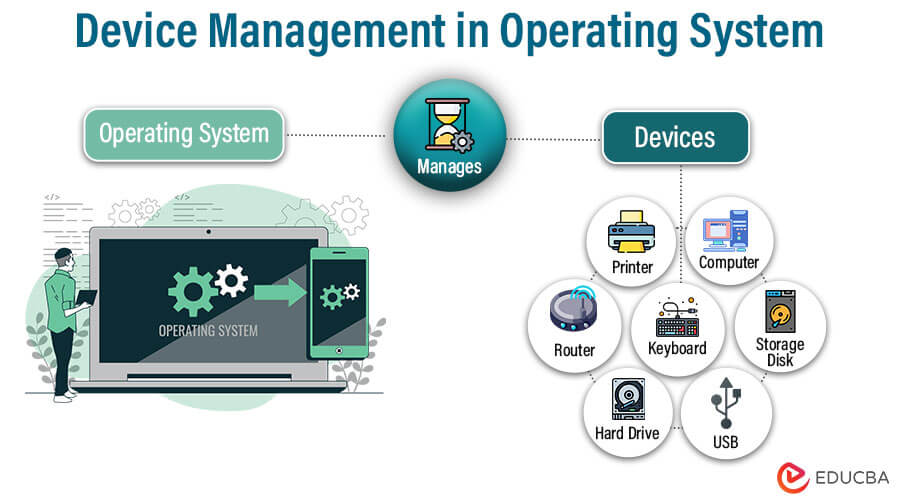
Device management in operating systems is a critical component that governs the interaction between hardware and software. It ensures efficient utilization of hardware resources, facilitates communication between devices, and handles errors. This behind-the-scenes function is crucial for the stable and effective operation of computers and other devices.
Table of Contents
- What is Device management in operating systems
- Device Types and Classification
- Classification of Operating System Peripheral Devices
- Functions of the Device Management in the OS
- Features of Device Management in Operating System
- Device Allocationg
- I/O Request Handling
- Device Initialization and Configuration
- Device Policies and Access Control
- Process Assignment and Management
Device Types and Classification
Fundamental Types of I/O Devices
In the realm of computing, Input/Output (I/O) devices serve as the essential conduits that connect our digital world to the physical one. They come in various forms, each tailored to specific functions and purposes. Here, we explore three fundamental categories: boot devices, character devices, and network devices.
- Boot Devices: Boot devices are the digital gateways to your computer’s soul. They house the initial firmware or bootloader that kicks off the operating system’s startup process. These devices include hard drives, SSDs, USB drives, and network boot options. When you power up your machine, it searches for the bootloader in these devices, initiating the boot sequence that brings your computer to life.
- Character Devices: Character devices are the unsung heroes of I/O. They handle data character-by-character, making them ideal for real-time interactions. This category encompasses devices like keyboard and mouse, which send individual keystrokes and mouse movements to the computer. Character devices enable you to interact with your computer, shaping the user experience with every key press and mouse click.
- Network Devices: In our interconnected world, network devices reign supreme. They facilitate computer data exchange, enabling communication and collaboration across vast distances. Network devices encompass network interface cards (NICs), routers, modems, and switches. They are the linchpins of the internet and local networks, ensuring seamless data transfer and connectivity.
These fundamental I/O device types are the building blocks of modern computing, and understanding their roles is essential for both users and system administrators. As technology advances, the boundaries between these categories continue to blur, giving rise to new, hybrid devices that further enrich our digital experiences.
Classification of Operating System Peripheral Devices
In the intricate world of operating systems, the management and classification of peripheral devices is a crucial task. These devices serve as the vital links between the digital realm and the physical hardware, and they come in diverse forms, each necessitating unique handling. In this context, we delve into three distinct categories: Dedicated Devices, Shared Devices, and Virtual Devices.
- Dedicated Devices: Dedicated devices are the specialists of the peripheral world. These are hardware components exclusively reserved for a specific task or application. Examples include- graphics processing units (GPUs) that focus on rendering graphics and sound cards that handle audio processing. Dedicated devices are optimized for their intended roles, delivering high performance and efficiency.
- Shared Devices: Shared devices, as the name suggests, are versatile team players. These devices can be accessed and utilized by multiple applications or processes concurrently. Printers, for instance, can be shared among various software applications, allowing several programs to print documents simultaneously. Shared devices are the multitaskers of the peripheral landscape.
- Virtual Devices: Virtual devices introduce a layer of abstraction and flexibility into the mix. These are not physical components but software emulations of hardware devices. Virtual devices are instrumental in virtualization technology, allowing multiple virtual machines to interact with emulated hardware as if it were real. This dynamic category enables efficient resource allocation, isolation, and management in virtualized environments.
Understanding the classification and management of these devices is pivotal for system administrators and developers as it directly impacts system performance, scalability, and resource allocation.
Functions of the Device Management in OS
Device management in an operating system is the silent conductor that orchestrates the intricate interplay between hardware and software. Its functions are critical in ensuring seamless operation and resource utilization. Here are the key roles it plays:
- Device Detection: Device management starts with the identification of hardware components. It scans the system to detect connected devices, verifying their presence and characteristics.
- Driver Communication: Once devices are identified, device management interacts with device drivers. Drivers act as translators, enabling the OS to communicate with specific hardware. Device management ensures the right driver is loaded for each device.
- Resource Allocation: Operating systems often manage multiple applications concurrently. Device management allocates resources like CPU time, memory, and I/O bandwidth, ensuring each device receives its fair share.
- Device Configuration: Devices often require specific settings or configurations to operate optimally. Device management handles these configurations, including resolution settings for monitors, network settings for network adapters, and more.
- Error Handling: When issues arise, device management plays a crucial role in error detection and recovery. It interprets error codes, initiates error recovery mechanisms, and, in some cases, can even hot-swap faulty devices.
- Security Management: Security is paramount. Device management ensures that only authorized applications can access specific devices, guarding against unauthorized access or potential security breaches.
- Power Management: Modern devices often require power management, allowing them to enter low-power states when not in use. Device management regulates these power states to conserve energy and extend the device’s lifespan.
- Plug-and-Play Support: Device management enables the seamless addition and removal of devices, ensuring new devices are recognized and operational without requiring system reboots.
Device management in the operating system is a complex symphony of hardware and software to deliver a user-friendly, stable, and secure computing experience. Its effective functioning is fundamental to the performance and reliability of modern computer systems.
Features of Device Management in Operating System (OS)
Device management ensures that your computer’s hardware and software work harmoniously. Here are the key features that make device management indispensable:
- Device Drivers: They are the intermediaries between your operating system and the myriad hardware components within your computer. These small but mighty pieces of software serve two fundamental roles:
Role of Device Drivers:
- Translation and Communication: Device drivers act as interpreters. They translate generic commands from the operating system into language that specific hardware components understand. They facilitate seamless communication between software applications and hardware devices.
- Optimization: Device drivers are tailored to extract the best performance from hardware. They unlock the full potential of your devices, ensuring they work efficiently and effectively.
Types of Device Drivers:
There are several types of device drivers, including:
- Kernel Drivers: These reside within the core of the operating system and provide direct communication with hardware. Nestled within the kernel, the central component of the OS, these drivers provide direct communication with hardware components. They enable the operating system to harness the full potential of your devices, ensuring smooth, low-level interactions. Kernel drivers operate at the system’s core, making them integral to your computer’s performance and stability. They are the guardians of your hardware, ensuring that every command and data transfer happens with precision and efficiency, making them the unsung heroes of your digital experience.
- Virtual Device Drivers: Used in virtualization environments to create and manage emulated hardware. These drivers don’t control physical components but create software emulations of hardware devices. They are crucial in virtualization technology, facilitating the operation of multiple virtual machines (VMs) on a single physical host. Virtual device drivers allow VMs to interact with emulated hardware as if it were real, abstracting the underlying physical components and enhancing the flexibility and isolation of virtualized environments. They are pivotal in optimizing resource allocation and ensuring efficient operation within the ever-evolving virtualization landscape.
- Filter Drivers: These intercept data as it passes between the operating system and the device, often for purposes like encryption or compression. These drivers serve diverse purposes, from data encryption and compression to firewall filtering and antivirus scans. Filter drivers enable real-time data analysis and transformation, safeguarding data integrity and security. They play a pivotal role in shaping the quality, privacy, and safety of data flows, ensuring that information passes through a series of critical checkpoints before reaching its destination. In this way, filter drivers act as the guardians protecting your data from harm.
- Plug and Play Drivers: These enable the system to configure and manage newly connected devices automatically. These drivers automatically detect new hardware connections, configure settings, and ensure the hardware is ready for use without requiring a system reboot. PnP drivers transform the once cumbersome task of installing and configuring hardware into a hassle-free, user-friendly experience. They play a pivotal role in the modern era of effortless hardware connectivity, where you can plug in a new device, and it’s instantly recognized and put to work, simplifying your tech experience.
Device drivers transform the abstract world of software into tangible and functional hardware, ensuring our devices operate smoothly.
Device Allocation
Device allocation is the art of distributing and managing resources in a computer system, a critical task for efficient operation. It comes in various flavors, with static and dynamic allocation methods and the choice between contiguous and non-contiguous allocation:
Static Allocation:
- Static allocation is like assigning dedicated parking spaces. Resources are fixed and pre-allocated, making them always available for specific devices. This method is simple and predictable but can be inefficient if devices don’t consistently utilize their allocated resources.
Dynamic Allocation: Dynamic allocation is akin to flexible office space. Resources are assigned as needed, optimizing utilization. It’s more versatile but may require extra management and can lead to resource contention in heavily loaded systems.
Contiguous and Non-contiguous Allocation: Contiguous allocation groups resources together, providing a single, uninterrupted chunk. Non-contiguous allocation scatters resources across the system. Contiguous is efficient but limiting, while non-contiguous offers flexibility at the cost of fragmentation.
Effective device allocation ensures a harmonious and productive environment in computer systems, balancing predictability with adaptability and structure with flexibility.
I/O Request Handling
I/O request handling keeps your computer’s data flowing seamlessly. It involves managing input and output requests, queuing, and scheduling algorithms, as well as buffering and caching techniques:
- Input and Output Requests: These requests are the data exchanges between your software and hardware. Handling them efficiently is crucial for system performance. These digital couriers are the messages between your software and hardware. Input requests deliver commands to hardware (e.g., keystrokes), while output requests bring results back to software (e.g., displaying text). They are the data bridge connecting your digital world with the physical one.
- Queuing and Scheduling Algorithms: Queuing algorithms prioritize incoming I/O requests, while scheduling algorithms determine the order in which they’re executed, optimizing data flow. They are essential for multitasking and resource allocation, ensuring your computer juggles numerous requests efficiently, just like a well-organized traffic system keeps vehicles moving seamlessly. These algorithms play a vital role in maintaining order and optimizing system performance, ensuring that critical tasks get the green light while preventing gridlock in the digital highway.
- Buffering and Caching: Buffering and caching techniques temporarily store data in high-speed memory to reduce data transfer bottlenecks and enhance overall system responsiveness. Buffering temporarily stores data in high-speed memory, bridging the gap between slow and fast components and preventing data bottlenecks. Caching, on the other hand, stores frequently accessed data for quick retrieval, reducing the need to fetch it from slower sources. Together, they create a dynamic duo that accelerates data transfer, reducing wait times and providing a smoother user experience. These techniques are like having quick-access notes handy, saving you from having to retrieve information from your bookshelf repeatedly.
I/O request handling orchestrates the symphony of data movement in your computer, ensuring everything plays harmoniously.
Device Initialization and Configuration
Device initialization is like the curtain rising on a tech performance. It prepares hardware for action during system startup. Configuration, the fine-tuning, ensures devices work smoothly with the operating system. Modern plug-and-play systems make this a seamless, user-friendly process, simplifying the tech symphony.
- Bootstrapping Devices: They initiate the essential processes, load necessary drivers, and set the stage for all other hardware and software components to come alive. Bootstrapping devices are the foundation upon which the entire system is built, like the ship’s captain guiding it through uncharted territory.
- Configuration Processes: During these processes, system settings are fine-tuned to optimize device interactions with the operating system. It’s like a conductor adjusting the instruments to create a harmonious performance. These processes encompass various tasks, such as setting display resolutions, configuring network connections, and tailoring device behavior.
- Plug and Play Systems: These systems make the once-complicated task of installing and configuring hardware a breeze. They automatically detect and identify newly connected devices, configure their settings, and ensure they are ready for immediate use, all without requiring a system reboot. PnP systems have revolutionized the tech experience, making it easy for users to expand and enhance their hardware without needing technical expertise. These systems are the ultimate facilitators of effortless hardware integration, turning the once daunting task of device configuration into a user-friendly and seamless process, bringing true plug-and-play convenience to technology.
Device Policies and Access Control
Device policies and access control are the conductors, ensuring every instrument plays its part harmoniously. These fundamental components steer the course of resource allocation, access control, and device sharing.
- Resource Allocation Policies: Think of resource allocation policies as the architects of a balanced orchestra. They manage the distribution of system resources to devices, preventing a single overzealous instrument from drowning out the others. These policies establish rules that guide allocating CPU time, memory, and bandwidth, promoting fair and efficient resource utilization.
- Access Control Mechanisms: Like vigilant gatekeepers, they determine who has the privilege to interact with specific devices. These mechanisms protect against unauthorized access, preserving system integrity and data security. They establish user or application permissions, ensuring that only those with the proper credentials can access devices, thereby preventing unauthorized tampering or data breaches.
- Device Sharing: Device sharing is the choreographer that enables multiple musicians to share the stage simultaneously. This strategy allows several users or processes to access and utilize devices concurrently, like an ensemble of musicians collaborating in perfect sync. Device sharing optimizes resource utilization and promotes a collaborative environment, facilitating a dynamic and efficient digital experience.
Collectively, these pillars – resource allocation policies, access control mechanisms, and device sharing – form the backbone of a well-structured, secure, and efficient digital ecosystem. They empower the overall integrity of the performance.
Process Assignment and Management
Process assignment and management allocate tasks to available resources, determining which processes run on which chores. Furthermore, these managers supervise ongoing processes, optimizing their performance and resource utilization, just as a maestro guides a performance to its peak. Effective process assignment and management are crucial for efficient multitasking and the seamless functioning of modern operating systems, ensuring that all elements work in perfect unison, creating a harmonious digital experience for users.
Here’s a glimpse into some of these Types:
- Cooperative Scheduling: Like an ensemble of musicians listening to one another, cooperative scheduling relies on processes voluntarily yielding control to allow others to execute. It promotes fairness and responsiveness but requires the cooperation of all running processes.
- Preemptive Scheduling: This type, similar to a conductor who can stop and start musicians at will, empowers the operating system to interrupt running processes when a higher-priority task emerges. It ensures that critical tasks get prompt attention but may lead to complexity and overhead.
- Round Robin Scheduling: Imagine a rotating chair for each musician; Round Robin scheduling assigns each process a fixed time slice, allowing them to execute in turns. This ensures equitable resource allocation but may lead to inefficient use of CPU time.
- Priority-Based Scheduling: Prioritizing processes is akin to giving lead roles to star performers. In this approach, each process is assigned a priority level, and the scheduler allocates resources based on these priorities. It offers fine-grained control over task execution but can result in resource starvation for low-priority tasks.
- Multilevel Queue Scheduling: This is like having multiple stages in a concert, where processes are categorized into different queues based on their attributes or priorities. The scheduler assigns processes to these queues and then schedules tasks within each queue. It’s a versatile approach that balances fairness and performance.
- Multilevel Feedback Queue Scheduling: Imagine a conductor allowing musicians to switch instruments during a performance. In this approach, processes move between different queues based on their behavior. It combines the benefits of priority-based and multilevel queue scheduling, adapting to changing workload requirements.
These various types of process assignment and management techniques reflect the multifaceted nature of operating systems. The choice of scheduling method depends on the system’s specific requirements and objectives, striving for a harmonious, efficient, and balanced digital performance.
Conclusion
Device management ensures the harmonious interplay of hardware and software. Its role extends far beyond the curtain call; it’s the invisible force ensuring that devices perform their parts in perfect unison, enriching our digital experience. From resource allocation to the meticulous configuration of each device, it meticulously fine-tunes the performance, ensuring that every interaction is seamless and secure. Device management is the key to transforming our diverse gadgets into a well-coordinated, efficient, and reliable ensemble. In the ever-evolving world of technology, this behind-the-scenes maestro continues to adapt, ensuring that our devices sing in perfect unison, contributing to the ever-evolving digital opus that is our modern lives.
Recommended Articles
This is a guide to What is Device management? Here we discuss why we use Device management in OS to be useful. along with the examples. You can also go through our other related articles to learn more –