Updated June 29, 2023
Introduction to Firewall
The firewall is a very vast concept. Every day, new improvements are coming with better design, firmware, software upgrades, features, etc. Different architecture is available in the firewall, like screened host firewall architecture, packet filtering routers firewall architecture, dual-homed firewall architecture, and screened subnet firewall architecture. As per the industrial requirement, and network design, we must choose suitable firewall architecture.
The basic concept of a firewall is to protect the internal or organizational environment from any external security attack. Similarly, three major aspects will define the firewall’s configuration, like the network’s objective regarding the organization’s point of view, the development ability, and how we need to implement it. While considering it in terms of the hardware level, then we need to consider the budget also.
Firewall Architecture in Detail
There are different types of architecture available in the firewall.
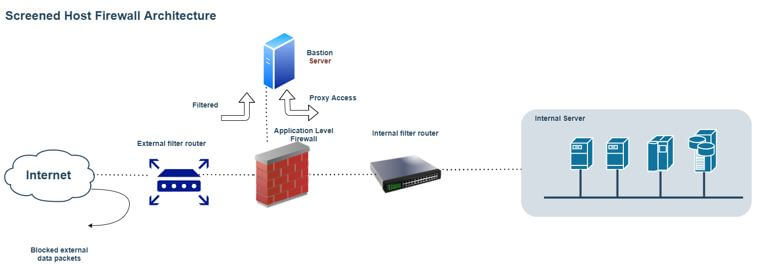
1 Screened host firewall architecture
We have improved the packet filtering routers firewall architecture in the screened host firewall architecture. In this architecture, we use the packet filtering routers firewall technique with the dedicated or the separate firewall. It is known as the application proxy server. In the packet filtering router’s firewall architecture, we have a very big overhead to filter the network traffic (once the access control list increases). Due to this, we are facing lots of issues. Here, we have tried to overcome it and added a dedicated firewall. This technique will allow the router to access the firewall. Due to this architecture, the routers will pre-screen the network traffic or the packets to minimize the network overhead. It will also help to distribute the load as well.
The separate application proxy server will work on layer 7 (on the TCP protocol). It will filter the packets on the application level. It can filter out the packets like HTTP, HTTPS, FTP, SFTP, etc. In other words, the separate application proxy server is also known as the bastion host. It will be a high chance of an external attack, and it will be less secure also. The action host or the separate application proxy server holds the cached copies of the web documents. But in this architecture, the external attacker must compromise the two different systems. Before making any attack, it will access the internal data also.
- Work Flow: As per the above architecture, a separate host is available, i.e., the bastion host. It acts like a proxy server to balance the load on the firewall. The firewall holds all the set of rules and access control. The Bastion server will help to filter out the network traffic. If it is a valid packet, it will allow it via proxy access to the internal filter router, moving further in the internal network.
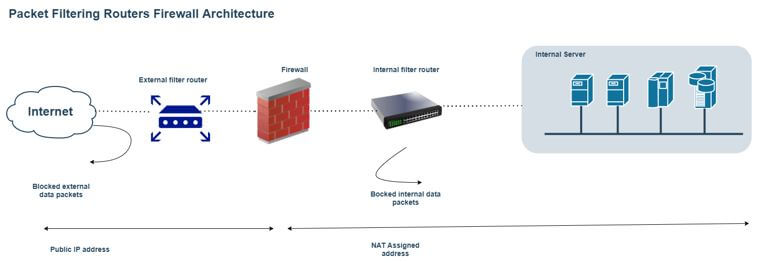
2. Packet filtering routers’ firewall architecture
Many organizations want internet connectivity. If we enable internet connectivity, the organization without a firewall will be exposed to the external world. We need to install and configure the firewall to avoid an external security attack. In the packet filtering routers, we have the router concept. Here, the router interface acts as the internet provider to the organization. The router acts as an intermediate between the organization and the internet provider. On the same level, we are enabling the network packet filtering process.
If any unwanted packets may come, so it will filter them out on the same level. Hence the packages will drop or be rejected. It will not come in the organization-level network. It is a very simple way to implement it. It will also help to lower the risk of external security threats. But it has a few concerns also. If we go with the packet filtering routers, there will be less auditing of the network traffic. Similarly, we are also having the drawback of the strong authentication mechanism. Day by day, the access control list will grow. Hence, it will be a very big overhead to filter the incoming network packets. Due to this, it will decrease the network performance also. In a few cases, we will face a lag.
- Work Flow: It is the basic technique to implement the firewall. Here, the ISP will provide an internet connection to the organization. Then, it is attached to the external filter router. First, we need to add the list of ACLs and configurations on the firewall. Then, with the help of the same configuration, the network traffic will filter and pass to the internal filter router. Further, the internal filter router will separate the network traffic into the internal organization-level network.
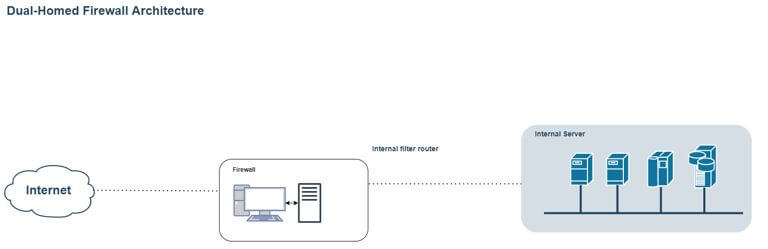
3. Dual-homed firewall architecture
The architectural complexity is increasing because we need high performance and less network lag. We use the single network interphase card in the previous firewall architecture. But when using such firewall architecture, the bastion host will contain the two different network interphase cards. In this architecture, one network interphase card will connect with the external network, and the other will connect with the internal network. Here, all the network traffic will physically travel from the firewall between internal and external network interphase cards.
- Work Flow: In this architecture, there is no separate proxy server. In this firewall architecture, there are two different NIC’s available. In one NIC, the external ISP connection will connect. In the second NIC, the internal network will connect. Once the traffic comes, the firewall will filter the traffic and pass it to the internal network. If the traffic is not valid, the firewall will drop the packet and not flow it further.
Conclusion
We have seen the uncut concept of the “firewall architecture” with the proper explanation. Several firewall architectures are available; we must choose them per our requirements and budget. The firewall will track the traffic on the application level also.
Recommended Articles
We hope that this EDUCBA information on “Firewall Architecture” was beneficial to you. You can view EDUCBA’s recommended articles for more information.