Updated March 24, 2023
Introduction to Fog Computing Architecture
Fog architecture involves using services of end devices (switches, routers, multiplexers, etc) for computational, storage and processing purposes. Fog computing architecture consists of physical as well as logical elements of the network, software, and hardware to form a complete network of a large number of interconnecting devices. Fog node distribution (physical as well as geographical, along with the topology and protocols used form key architectural features of a fog architecture. Fog architecture involves the distribution of functions at different layers, the types and the number of protocols used, and the constraints imposed at various layers.
Hierarchical Fog Computing Architecture
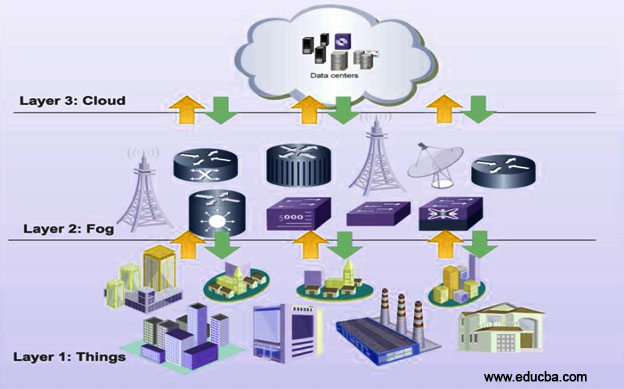
The hierarchical fog architecture comprises of following three layers:
1. Terminal Layer
- The terminal layer is the basic layer in fog architecture, this layer includes devices like mobile phones, sensors, smart vehicles, readers, smartcards, etc.
- The devices which can sense and capture data are present in this layer. Devices are distributed across a number of locations separated far apart from each other.
- The layer mostly deals with data sensing and capturing. Devices from different platforms and different architectures are mainly found in this layer.
- The devices have the property of working in a heterogeneous environment, with other devices from separate technologies and separate modes of communication.
2. Fog Layer
- Fog layer includes devices like routers, gateways, access points, base stations, specific fog servers, etc., called as Fog nodes.
- Fog nodes are located at the edge of a network. An edge can be a hop distance from the end device. The Fog nodes are situated in-between end devices and cloud data centers.
- Fog nodes can be static, e.g., located in a bus terminal or coffee shop, or they can be moving, e.g., fitted inside in a moving vehicle.
- Fog nodes ensure services to the end devices. Fog nodes can compute, transfer and store the data temporarily.
- Fog nodes and cloud data center connections are enabled by the IP core networks, providing interaction and cooperation with the cloud for enhancing processing and storage capabilities.
3. Cloud Layer
- This layer consists of devices that can provide large storage and machines (servers) with high performance.
- This layer performs computation analysis and stores data permanently, for back-up and permanent access to the users.
- This layer has high storage and powerful computing capabilities.
- Enormous data centers with high computing abilities form a cloud layer. The data centers provide all the basic characteristics of cloud computing to the users. The data centers are both scalable and provide compute resources on-demand basis.
- The cloud layer lies at the extreme end of the overall fog architecture. It acts as a back-up as well as provides permanent storage for data in a fog architecture. Usually, data that isn’t required at the user proximity is stored in a cloud layer.
Layered Fog Computing Architecture
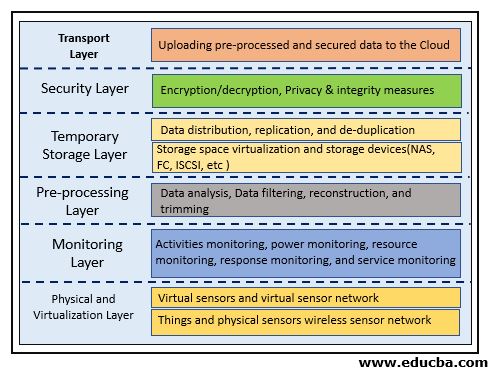
The layered fog architecture consists of six layers:
1. Physical and Virtualization Layer
- This layer comprises nodes (Physical and virtual). The nodes perform the primary task of capturing data and are located at different locations. Nodes usually involve sensing technology to capture their surroundings.
- Sensors used at this node collect data from the surroundings and collect data which is then sent to upper layers via gateways for further processing.
- A node can be a stand-alone device like a mobile phone or it can be a part of a large device like a temperature sensor fitted inside a vehicle.
2. Monitoring Layer
- In this layer, we perform node monitoring related to various tasks.
- Nodes can be monitored for the amount of time they work, the temperature and other physical properties they are possessing, the maximum battery life of the device, etc.
- The performance of applications as well as their present state is also monitored.
- The fog nodes are checked for their energy consumption, the amount of battery power they consume while performing their tasks.
3. Pre-processing Layer
- This layer performs various data operations mainly related to analysis.
- Data is cleaned and checked for any unwanted data present. Data impurity is removed and only useful data is collected.
- Data analysis at this layer can involve mining meaningful and relevant information from a vast amount of data collected by the end devices.
- Data analysis is one of the essential features that should be taken into consideration before data is used for a specific purpose.
4. Temporary Storage
- This layer is associated with non-permanent distribution and replication of data.
- Storage virtualization like VSAN is used in this layer.
- Data is removed from the temporary layer once data is moved to the cloud, from this layer.
5. Security Layer
- This layer is involved with the privacy of data, the integrity of data, encryption, and decryption of data.
- Privacy in the case of fog computing data can include use-based privacy, data-based privacy, and location-based privacy.
- The security layer ensures secure and preservation of privacy for the data which is outsourced to the fog nodes.
6. Transport Layer
- The primary function of this layer is to upload partly-processed and fine-grained secure data to the cloud layer for permanent storage. For efficiency purposes, the portion of data is collected and uploaded.
- The data is passed through smart-gateways before uploading onto the cloud. The communication protocols used are chosen to be lightweight, and efficient, because of the limited resources of fog computing.
Conclusion
Fog architecture is a model which comprises of a number of different layers. The model serves as an ideal for the construction of a fog network. The architecture provides an overview of different functionalities that are performed by respective layers. The protocols used at different layers, the particular devices that are used at different layers and their functionalities, specifications are identified by going through the fog architecture.
Recommended Articles
This has been a guide to Fog Computing Architecture. Here we discuss the introduction, hierarchical and layered fog computing architecture. You may also have a look at the following articles to learn more –