Updated November 30, 2023
Introduction to Functions of Operating System
In the digital realm of today’s fast-paced and interconnected world, the Operating System (OS) stands as a vital communication bridge between users and the underlying hardware of a computer. With its multifaceted role, the Operating System is pivotal in facilitating smooth program execution, optimizing resource allocation, and ensuring overall system efficiency. As we explore the Functions of the Operating System, we delve into a realm of capabilities that encompass resource allocation, memory management, process scheduling, device management, file handling, user interfaces, and robust system security measures. In this ever-evolving landscape of technology, the Operating System serves as the backbone that enables seamless computing experiences and empowers users to harness the full potential of their machines. Let us uncover the intricacies and significance of these essential functions orchestrating the harmony between humans and machines.
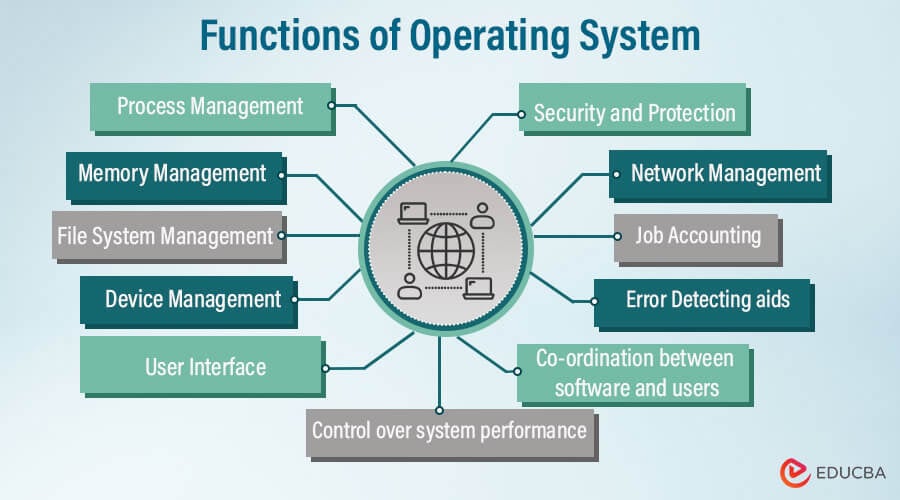
Table of Content
- Introduction to Functions of Operating System
- What is an Operating System?
- Types of Operating Systems
- Functions of the Operating System
- Operating System Services
- Characteristics of Operating System
What is an Operating System?
A computer’s operating system (OS) is crucial software that oversees hardware and software resources while offering necessary services to computer programs. It is an intermediary between a computer system’s hardware and software components, facilitating communication and coordination. The primary objective of an operating system is to create a convenient and efficient computing environment for users while ensuring the most effective use of available resources.
- OS manages the following resources – input devices, output devices, storage devices, and network devices. Input devices include a keyboard and mouse. Output devices are monitors, printers, and scanners; network devices are the modem, and so on. Also, storage devices include internal and external storage drives.
- The main components of OS are the kernel, user interface, and application programming interface. The kernel provides basic control to the devices. The user interface helps in user interaction with the system. The code is written by application developers using the application programming interface.
Types of Operating Systems
- Batch Operating System: In a batch operating system, the system can automatically process a series or batch of jobs submitted by users without requiring user input. This operating system is commonly used when the same operations are repeated, such as in large-scale data processing or scientific computations.
- Time-Sharing Operating System: A time-sharing operating system, also called a multi-user operating system, enables several users to engage with the computer simultaneously. The operating system shares the CPU’s time among various users, each receiving a small time slot to carry out their tasks. This operating system offers a responsive, interactive environment, allowing users to execute multiple programs simultaneously. Examples include Linux and UNIX.
- Real-Time Operating System(ROTS): Operating systems that operate in real-time are specifically created to manage tasks with strict time constraints. They promptly complete essential tasks and prioritize them accordingly. Applications that require quick responses use these types of tasks, such as industrial control systems, robotics, and aerospace systems. We can categorize different types of real-time operating systems, hard real-time (strict deadlines) or soft real-time (flexible deadlines), depending on the timing determinism required.
- Distributed Operating System: Distributed operating systems allow users to access distributed resources across multiple locations easily. These systems also facilitate using distributed file systems, computing, and data processing. Examples are Windows Distributed File System (DFS) and Google’s distributed operating system for data centers.
- Embedded Operating System: Embedded systems, specialized computer systems built into various machines and devices, are designed to run embedded operating systems. These operating systems are lightweight, use few resources, and are designed for particular hardware platforms and application needs. Some examples are Android for smartphones and real-time operating systems for embedded systems like FreeRTOS.
Functions of the Operating System
The operating system performs the following functions:
1. Process Management
Process management is a key feature of an operating system that handles the creation, planning, execution, and termination of processes or tasks within a computer system. The main components of process management are listed below.
- Process Creation: Creating new processes is the operating system’s responsibility. It allows the resources required for the process to run, including memory and data structures. This may involve loading the program code and initializing variables.
- Process Scheduling: The OS manages the execution of processes fairly and efficiently. The CPU executes processes in a particular order using scheduling algorithms. The scheduler chooses which process to execute next based on priority, time slice, and resource availability.
- Process Execution: After scheduling a process, the operating system hands over control of the CPU to the said process, enabling it to execute its instructions. The CPU follows a sequential process of executing instructions. The computer program retrieves directions from its memory and performs computations or actions accordingly. Throughout its execution, it may communicate with other processes, request further resources, or interact with input/output devices.
- Process Termination: A process may terminate when it has finished running or when an error or exception occurs. The operating system reclaims the resources allotted to the terminated process. Ensuring we keep all relevant data structures up-to-date, free up memory, and properly close any open files. Once a system terminates the process, it is removed from the system, freeing up its resources for other processes to use.
- Process Synchronization and Communication: To share data or coordinate activities, processes may have to synchronize their execution or communicate. The operating system has synchronization mechanisms, such as semaphores, locks, and monitors, to ensure that processes can safely access shared resources and prevent conflicts. Inter-process communication mechanisms like shared memory, message passing, and pipes enable processes to exchange data and coordinate activities.
- Process States and Control: The operating system maintains track of details about every process, such as its current state, priority, and resource utilization. A process can be in various states, such as running, waiting, or ready. The operating system controls the changes between these modes depending on circumstances like I/O completion, timer interrupts, or resource availability. It manages process execution, switching between them and dynamically allocating resources according to their requirements.
2. Memory Management
Memory management plays a vital role in any operating system. It encompasses the allocation, tracking, and deallocation of computer memory resources. Its main objective is to effectively use currently available memory to facilitate the execution of processes and applications.
- Allocation: The operating system allocates memory to processes or applications when they load into memory. Allocating sufficient memory to each process is necessary to guarantee it can complete its duties and handle memory fragmentation problems.
- Deallocation: After a process finishes or gets terminated, the operating system will release the memory used by the process. This will allow the memory to be used for other purposes in the future.
- Address Mapping: The operating system handles address mapping, which translates the logical addresses utilized by processes into physical addresses in the memory.
- Paging and Swapping: Memory management techniques such as paging and swapping enable processes to utilize more memory than is physically available. Paging divides the memory into fixed-size pages while swapping moves inactive processes or parts of them to secondary storage, freeing up physical memory.
- Memory Protection: To ensure data integrity and security, the operating system has memory protection mechanisms that prevent one process from accessing or altering the memory of another process.
- Virtual Memory: By using virtual memory, the operating system can give each process the appearance of having its own dedicated memory space. The system utilizes physical memory and secondary storage, transferring data between the two when necessary.
3. File System Management
Managing the file system is an essential task performed by an operating system. It involves arranging, storing, and retrieving files on various storage devices. I can provide you with a detailed explanation of File System Management:
- File Organization: The file system controls how files are arranged logically and systematically on storage systems. It maintains a directory structure that makes it simple for users to navigate and locate files. This organization can incorporate directories and subdirectories for the hierarchical organization of files.
- File Creation and Deletion: Users can easily create and delete files using the file system. When creating a new file, users can specify its name, location, and initial contents. Similarly, users can delete no longer required files, freeing up storage space.
- File Access and Permissions: The file system manages file access and enforces permissions to uphold data security and protect privacy. Users or user groups are assigned permissions, such as read, write, and execute, to regulate their ability to view, modify, or execute files. This ensures the protection of sensitive data and restricts unauthorized access.
- File Operations: The file system offers several ways to perform different file operations. These operations involve reading data from a file, writing data to a file, adding data to an existing file, changing the read/write pointer position, and resizing or truncating a file. These operations allow users and applications to manipulate the content of files efficiently.
- File Metadata Management: The file system stores and manages Metadata related to each file. File name, size, creation and modification dates, file owner, and permissions are just a few examples of the information included in the metadata.
- File System Integrity and Recovery: The file system implements mechanisms to guarantee the integrity and recoverability of files and file system data. It uses techniques like journaling or transaction logs to keep track of changes and recover from system problems or failures. This assists in avoiding data corruption and preserving the file system’s consistency.
4. Device Management
Device Management is an essential task for an operating system. It involves regulating and coordinating the communication between the computer system and its input/output (I/O) devices. Here is an explanation of Device Management:
- Device Drivers: Device drivers, which are software components that permit communication between the operating system and particular hardware devices, are made available by the operating system. It manages the low-level functions of a device, such as data transmission and receiving, resource management, and converting device-specific directives into a format that the operating system can understand.
- Device Allocation: The management of device allocation to different users or processes is handled by the operating system. It manages device access and prevents conflicts between requests for the same device. Assigning device access involves determining whether access is exclusive or shared, depending on priorities, permissions, and scheduling policies.
- Device Configuration: The operating system configures the device by identifying and detecting hardware attached to the computer system. Every device is classified based on its type, capabilities, and characteristics and configured for optimal performance. This includes creating communication channels, initializing device drivers, and setting device parameters.
- Device Input and Output: The operating system uses devices to manage input and output processes. It controls the data flow between the computer system, input devices (such as keyboards and mice), and output devices (like monitors and printers). The operating system transfers data accurately, buffered as necessary, and synchronized with the operation of processes or applications.
- Device Synchronization: The operating system offers synchronization techniques to manage how devices and processes interact. It manages the order and timing of device operations to avoid data inconsistencies or conflicts. Synchronization may involve locking, signaling, or interrupt handling to ensure proper device access and data integrity.
5. User Interface
The method through which users interact with a computer system or software application refers to as the user interface (UI). Users can enter commands, access system operations, and receive output or feedback from the system using the interface, which can be visual or tactile.
- Graphical User Interface (GUI): GUIs display system functions through icons, menus, buttons, and windows, allowing users to interact with the system by clicking or tapping. The design of these tools prioritizes user-friendliness and intuitive navigation to ensure effortless completion of tasks.
- Command-Line Interface (CLI): CLI is a text-based system where users input commands through a keyboard. Advanced users and system administrators prefer CLI interfaces for direct control and scripting abilities. It’s highly efficient for executing complex commands and performing repetitive tasks.
- Menu-Driven Interface: Menu-driven interfaces present users with a list of options. They are often used in more straightforward applications or for a streamlined user experience.
- Natural Language Interface: With a natural language interface, users can communicate with a system using regular, human language. They can input commands or questions in a natural sentence, and the system will interpret and respond appropriately. These interfaces commonly use artificial intelligence and natural language processing techniques to understand and process user input.
- Touch-Based Interface: Developers create touch-based interfaces explicitly for devices with touchscreens, such as smartphones and tablets. These interfaces enable users to interact with the system through direct touch on the screen and gestures such as tapping, swiping, or pinching. Touch-based interfaces offer intuitive and tactile interactions, which help users navigate, select options, and perform actions using their fingers.
6. Security and Protection
Ensuring the safety and protection of a computer system, its resources, and the data it processes are essential functions of an operating system.
- Access Control: To protect the system resources, the operating system uses access control mechanisms that only allow authorized users or processes to access them. It enforces authentication methods, manages user accounts, and sets permissions to restrict access to sensitive data, networks, devices, and files.
- Data Encryption: The operating system has built-in features that safeguard sensitive information from being accessed or intercepted by unauthorized individuals using data encryption techniques. Encryption algorithms and cryptographic protocols utilized during transmission and storage ensure data security from unauthorized access or tampering.
- Malware Detection and Prevention: The operating system includes security measures to detect and prevent malware infections. These measures include antivirus software, firewalls, and intrusion detection systems designed to detect and mitigate security threats such as viruses, worms, trojans, and unauthorized network access attempts.
- Firewalls and Intrusion Detection Systems: The network has firewalls and intrusion detection systems that oversee and manage all incoming and outgoing traffic. They filter out any malicious or unauthorized activities. Firewalls stop unauthorized network connections, while intrusion detection systems identify and respond to suspicious behavior or security breaches.
7. Network Management
Network management refers to administering, monitoring, and optimizing computer networks to ensure efficient and secure operation. It involves processes, tools, and methodologies to maintain the network’s performance, reliability, and security. Network management tasks can vary depending on the size and complexity of the network, ranging from small local area networks (LANs) to large-scale wide area networks (WANs) and data centers.
Key aspects of network management include:
- Network Monitoring: Managing a network requires ongoing monitoring of devices like routers, switches, firewalls, servers, and network links. Monitoring tools collect data on network performance, traffic patterns, and device health, allowing administrators to identify and address issues proactively.
- Network Configuration Management: Configuration management includes maintaining and updating network device configurations. Network administrators ensure proper configuration of devices, adherence to best practices, and implementation of necessary changes when required.
- Network Troubleshooting: When network issues occur, network management involves troubleshooting to identify and resolve the root causes of problems. Troubleshooting may include analyzing logs, conducting packet captures, and using network diagnostic tools.
- Network Performance Optimization: Network managers work to optimize the network’s performance, ensuring efficient data flow and minimizing delays or bottlenecks. This may involve load balancing, traffic shaping, and QoS (Quality of Service) configuration.
8. Control over system performance
Controlling system performance is critical to managing computer systems and ensuring their efficient operation. It involves various techniques and tools to monitor, optimize, and maintain the performance of hardware, software, and networks to meet user expectations and requirements. Controlling system performance helps avoid bottlenecks, reduce response times, and maximize resource utilization.
9. Job Accounting
In computing, job accounting, also known as workload accounting or resource accounting, involves tracking and recording resource usage and performance metrics of individual jobs or tasks. It gathers information on resource usage by different processes, applications, or users, aiding in billing, performance analysis, capacity planning, and optimization. Job accounting is commonly used in multi-user systems, high-performance computing clusters, cloud computing environments, and shared hosting services.
10. Error Detecting aids
Mechanisms and techniques used in computing and communication systems identify and detect errors or anomalies that may occur during data transmission, processing, or storage. These are known as error-detecting aids. These aids are crucial for maintaining data integrity, ensuring information accuracy, and improving systems’ reliability.
11. Co-ordination between software and users
Operating systems are crucial in coordinating and managing various software tools like interpreters, compilers, assemblers, and other applications for different users in a computer system. They handle resource allocation, process management, communication, and security, enabling a seamless and efficient user experience while executing different software tools.
Operating System Services
- Program Execution: The OS manages the execution of programs and ensures that they run correctly on the hardware.
- Input-Output Operations: It facilitates input and output operations, enabling data exchange between the computer and its peripherals.
- Error Handling: It handles errors and exceptions that occur during program execution.
- Resource Allocation: The OS allocates system resources, such as CPU time, memory, and peripherals, to different programs and processes.
- Communication Between Processes: It facilitates communication and data sharing between different processes running on the system.
- Resource Administration: It efficiently manages system resources, including CPU scheduling and memory management.
Characteristics of Operating System
- Resource Management: Computer operating systems are responsible for managing various computer resources, including the Central Processing Unit (CPU), memory (RAM), storage devices, and Input/Output (I/O) devices. They allocate and schedule these resources to different processes and applications to prevent conflicts and ensure smooth execution.
- Multitasking: Modern operating systems support multitasking, allowing multiple processes or applications to run concurrently. The OS manages the switching between tasks to give the illusion of parallel execution, even on single-core processors.
- Virtual Memory: Operating systems use virtual memory techniques to manage memory resources efficiently. Virtual memory allows processes to access more than is physically available by using disk space as an extension of RAM.
- Task Management: The OS manages tasks and processes, including creation, termination, and suspension/resumption. It ensures fair time-sharing among multiple processes and prioritizes critical tasks.
- Input and Output Management: Operating systems control input and output activities, allowing applications to interact with peripherals such as keyboards, mice, monitors, printers, and network devices.
FAQs
Q1. What is the role of the kernel in an operating system?
Answer: The kernel forms the central part of an operating system, providing crucial functions such as managing processes, memory, and devices and allocating system resources. It also serves as a mediator between the hardware and software elements of the system by directly communicating with the hardware.
Q2. Can I have multiple operating systems on one computer?
Ans: It’s possible to install multiple operating systems on one computer. This is called dual-booting or multi-booting. During the boot process, each operating system will have its own partition or disk space that can be selected.
Q3. How does memory management impact system performance?
Ans: Effective memory management is crucial for optimizing system performance. Insufficient memory can lead to slowdowns and system crashes, while efficient memory allocation improves responsiveness.
Q4. Are operating systems only used in computers?
Ans: No, Operating systems are used in various computing devices such as computers, smartphones, tablets, servers, embedded systems, etc. The operating system’s specific type and features may differ depending on the device and intended purpose.
Conclusion
The functions of an operating system are diverse and essential for the efficient operation of a computer system. From process management to user interface, each function contributes to the overall performance and usability of the system. Understanding these functions is crucial for both end-users and system administrators to make the most out of their computer systems.
Recommended Articles
We hope this EDUCBA information on “Functions of Operating System” benefited you. You can view EDUCBA’s recommended articles for more information.
