Updated April 17, 2023

Definition of Kali Linux Metasploit
Kali Linux Metasploit is defined as an open source framework that enables users to perform penetration testing, which includes finding, exploiting and validating vulnerabilities) along with enabling users to build and develop platform that in turn provides exploits for variety of applications, operating system and platforms. This is one of the most widely used tool for penetration testing and is a feature which comes built-in in Kali Linux distributions. This framework provides infrastructure, content and tools for performing penetration tests and also allows users to extensively audit securities together with addition of new modules on regular basis so as to keep the framework up to date and ready for any compromising situations!
How Kali Linux Metasploit works?
Now that we know the brief description of Metasploit, it becomes important for us to know the working methodology of Metasploit owing to the vast utilities it provides to the users. Metasploit is built on number of components and these components are known as modules. Modules are nothing but small chunks of standalone code or a software application that allows users with the requirement of the functionality of what Metasploit intends to provide. There are total 6 modules, namely payloads, exploits, nops, encoders, posts, and auxiliary. Now, in order to understand the working of Metasploit, we would need to understand each of these elements and later in this section, we will try to combine all and provide the bigger picture of how Metasploit works. The main component of Metasploit is payloads and exploits.
Payloads
Payload is an element in Metasploit or in other words simple scripts that enables hackers to interact with the hacked system. With the interaction, the hacker or user is able to transfer data to the victim system. This is done using 3 types of payloads that are available.
- Singles: These are small scripts that are used for creation of communication and thus allowing to move to next stage.
- Staged: This is a bigger piece with respect to singles and allows attacker to upload a bigger file into the victim system.
- Stages: These are components that are downloaded by stager modules and these provide advanced features with no restriction to size.
Post execution of a payload, there is a listener created at the correct port, and then establishes a connection for targeting the SMB service. Thus, providing the facility to Metasploit for port creation can be used by exploits for its functionality.
Exploits
Exploits are a sequence of commands that gets executed to target a vulnerability specifically which might be present in the system or application. This vulnerability can reach a stage where the attacker might even get access to the system. Some exploits which are very common are buffer overflow, web application, code injection, etc. Now when an exploit script is run, an attack plan is built on the basis of various characteristics of target system like operating system, service, vulnerability information, and so on. One thing to be kept in mind is that a normal authenticated control mechanism is not abused. Once the exploit is set up and run, the data from incoming connection of the exploited system enables Metasploit to deliver the required functionality.
Nops
As we mentioned that payloads and exploits are 2 important components and hence while working with exploit payloads we would need to make sure that some randomness is added to the final output using NOPS. Metasploit comes handy to users as it contains a number of NOP generators. NOP generator always uses the random one first.
Encoders
As we mentioned that payloads and exploits are 2 important component and hence, while working with exploit payloads we would need to encode our payloads so that any bad characters are removed, and this is where encoders will play the major role. One needs to keep in mind that encoders are used when one need not need to touch the registers and be under max size in addition to requirement of removal of bad characters.
Posts
This component enables Metasploit to run wide variety of post-exploitation modules that are available with Metasploit which can be run on compromised targets for evidence gathering, enabling pivot deeper into a target network and much more.
Auxiliary
Anything which is not an exploit is termed as an auxiliary module. While it is required by an exploit to have a payload, auxiliary on the other hand are fascinating features that allows Metasploit to extend the variety of exploitation.
With the understanding of various component above, we are now able to picturize the bigger picture of Metasploit working.
Advantages and disadvantages
It is now important for us to know about the advantages and disadvantages so that one can score on utility of Metasploit
Advantages
- Metasploit is open source, and hence free!
- There is a huge community that will enable you to use the features in much better way.
- This framework is mostly up to date as it gets updated frequently.
- User-specific exploit can be easily deployed
Disadvantages
- Learning Metasploit can be a challenging task.
- There is very limited GUI based utility, as it is mostly CLI driven.
- If not handled safely, it can crash the system.
- In case your system has antivirus, it might be difficult to install Metasploit.
Examples
Let us discuss examples of Kali Linux Metasploit.
Example #1
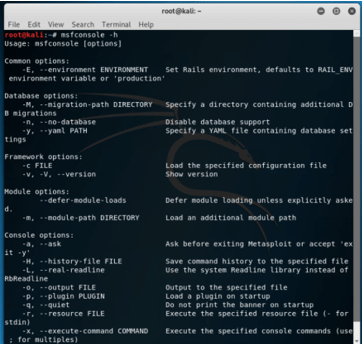
Access the help documentation of console of Metasploit
Syntax:
msfconsole -hOutput:
Example #2
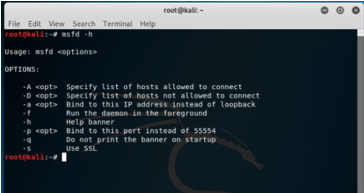
Access the help documentation of utility for providing instance of msfconsole where remote clients can connect to
Syntax:
msfd -hOutput:
Example #3
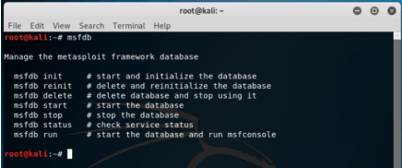
Command to manage framework database
Syntax:
msfdbOutput:
Example #4
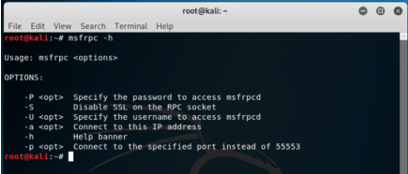
Command to connect to RPC instance’s documentation
Syntax
msfrpc -hOutput:
Usage of Kali Linux Metasploit
For using Metasploit we would first need to install Metasploitable. For this first, we need to set up a virtual environment. Once the environment is set, we need to make sure that Metasploit is not on our actual network and the setting configuration needs to be accordingly configured and also make sure that Kali Linux machine is on host-only adapter. Once configured, we can start Metasploitable and utilize it as per our requirement of framework utilization.
Conclusion
In this article, we have got a flavor of how Metasploit works in Kali Linux, and with advantages and disadvantages mentioned so that it is clearer for our readers to weigh each of these pointers when it comes to using of Metasploit in day to day work. Also, kudos to the team of Rapid7 for the constant update to the modules so as to keep the framework up to date!
Recommended Articles
We hope that this EDUCBA information on “Kali Linux Metasploit” was beneficial to you. You can view EDUCBA’s recommended articles for more information.