Updated February 15, 2023
Introduction to Kali Linux Penetration Testing
We know that Kali Linux is used to perform penetration testing and it provides different tools and utilities to the users to perform the penetration testing. Basically, Kali Linux provides security to IT companies to maintain their system security. Normally penetration testing is used to determine the technical risk of software and hardware devices. We can perform penetration on different web-based applications and websites.
Key Takeaways
- With the help of penetration, we can determine the strength of our machine.
- It helps us to improve the regulation and compliance of our organization.
- It helps to protect our data from hackers.
- Penetration simulation provides the cyber chain mapping to see the hacker’s directions which are used for hacking.
What is Kali Linux Penetration Testing?
Kali Linux is an open source appropriation in view of Debian zeroed in on giving penetration testing and security reviewing devices. Effectively created by Hostile Security, it’s one of the most well-known security conveyances used by infosec organizations and moral programmers.
To work on the security and nature of items, use Kali Linux for infiltration testing. Penetration testing has turned into a necessary piece of a thorough security program. Moral programmers lead pen tests to mirror the methodologies and activities of the aggressor. This muddled assignment is imaginative, and it needs you to totally grasp your errand.
An exceptionally urgent move toward the infiltration testing process is imparting the consequences of the penetration test and proposals to further develop the security level of the objective IT climate and the business at large. The report from the infiltration test is utilized to come to informed conclusions about the business by partners. It is in this way critical that the report sums up every one of the exercises conveyed, discoveries, and suggestions in a way that is reasonable by partners.
How can we Use Kali Linux Penetration Testing?
Let’s see how can we use penetration in Kali Linux as there are many tools in the market here we will see OWASP ZAP as follows:
First, we need to open the ZAP tool from an application which is shown in the below screenshot.
After clicking on the icon, we get a new window, where we can see the dashboard of the ZAP application as shown in the below screenshot.
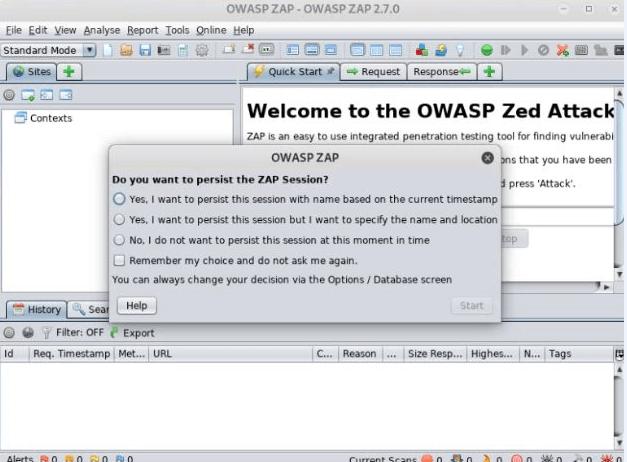
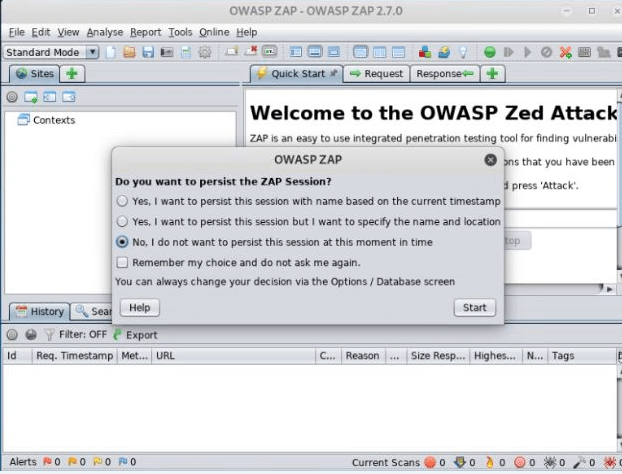
Here we can see the different options on the POP-UP message, so select the third number option and click on the start button as shown below screenshot.
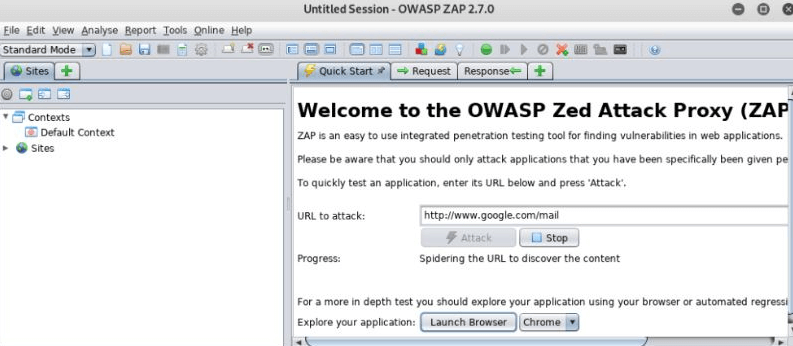
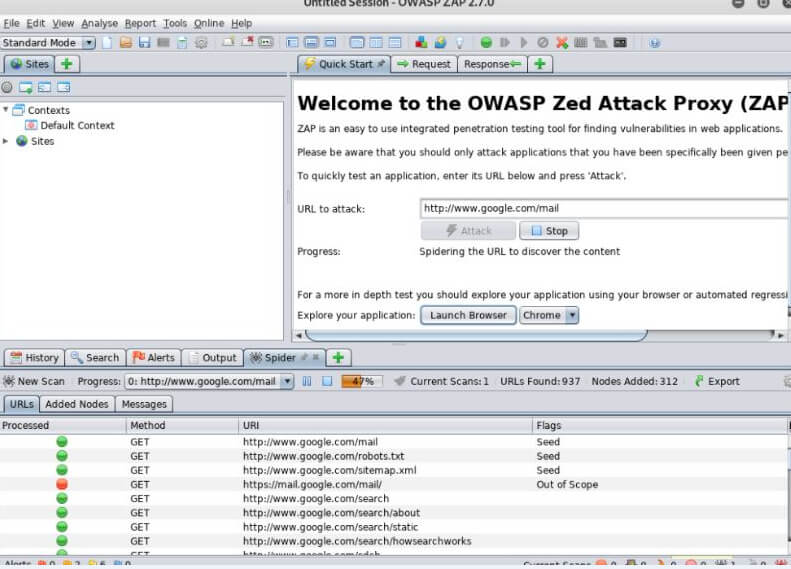
After clicking on start, we get a new window with some other information as shown in the below screenshot.
Here we can see the text box where we need to enter the URL which we want and then click on the Attack button, after that we can see different URLs and methods that ZAP processes for a scan as shown in the below screenshot.
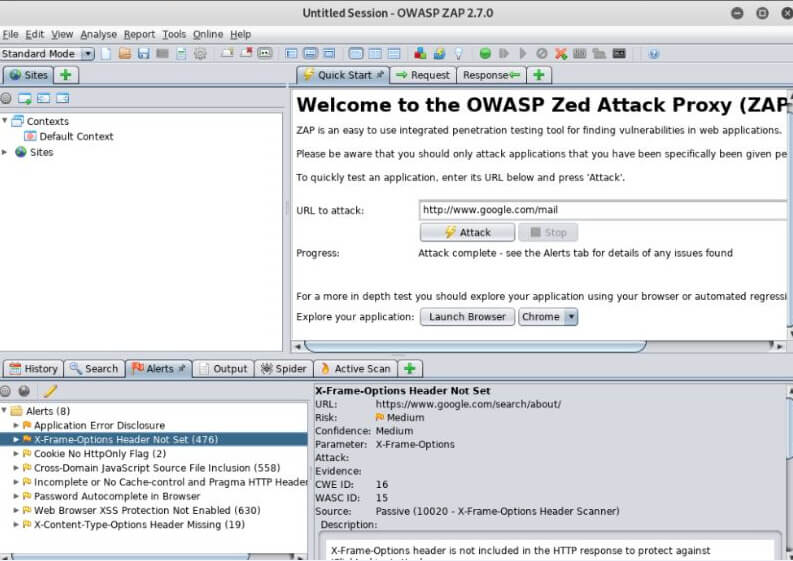
Here we also have the option to see the Alerts, for that we need to click on the Alert button which is shown below. So, we can see the Alert message with the respective URL.
Kali Linux Penetration Testing Database Tools
Kali Linux provides different tools to perform penetration testing as follows:
1. Sqlmap
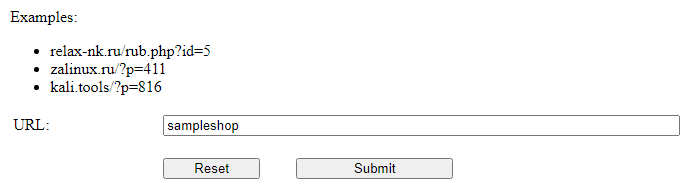
Sqlmap is an open-source penetration testing application that robotizes the method involved with recognizing and taking advantage of SQL injection blemishes and taking over information base servers. It accompanies a strong recognition motor, numerous specialty highlights for a definitive infiltration analyzer, and an expansive scope of switches enduring from data set fingerprinting, over information bringing from the data set, to getting to the hidden record framework and executing orders on the working framework through out-of-band associations. Here we use an online tool, so first, we need to enter the base URL as shown in the below screenshot.
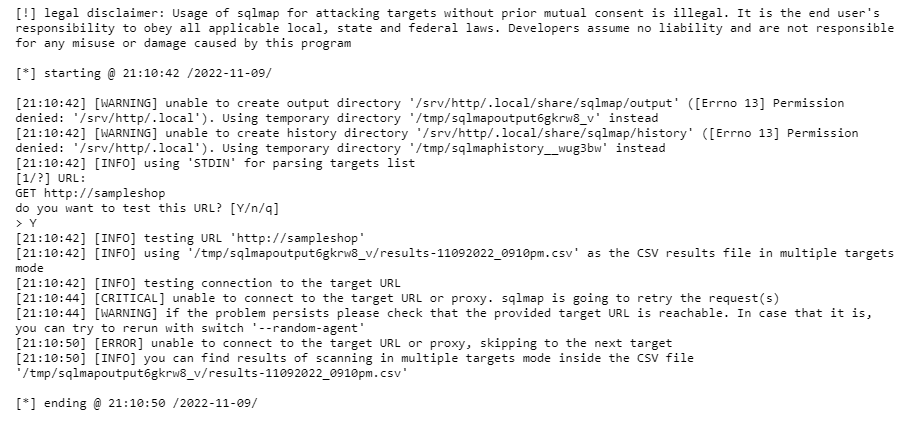
After that, we need to click on the submit button to see the result which is shown in the below screenshot.
2. Sqlninja
This is another tool used to perform SQL injection on the SQL server. With the help of sqlninja we can perform SQL injection vulnerabilities on the different web applications that use the Microsoft SQL server as the back end as shown below.
3. WPScan
This is another tool used to perform vulnerability, with the help of this tool we can find the security issues.
4. Joomscan
This is the most widely used tool of CMS because of its flexibility. For CMS users it works as a Joomla scanner, and it helps developers to determine possible security issues.
5. SSL Scanning Tools
This is another category of database tool, and it contains different tools as follows.
6. TLSSLed
This is a shell script-based tool used to determine the security of web server implementations and it is based on SSLscan.
We also have the w3af tool.
Kali Linux Penetration Testing Applications
Given below are the applications mentioned:
- DNSMap: It is used to determine the security of infrastructure as well as it also helps to determine the security of netblocks, subdomains, domain names, etc.
- Nmap: By using this application we can implement the firewall, in other words, we can say that it analyzes all raw data we have, and based on that data it creates the firewall.
- Arp-scan: Arp scan is a device that outputs networks with Ethernet ARP bundles, Layer-2, and Mac. Input can be gotten by sending ARP packets to characterize has on your host organization. ARP scan can be shipped off various hosts utilizing yield data transmission and configurable packet rate.
- SSLsplit: This is an additional tool used for penetration and forensics testing, with the help of this tool we can perform the man-in-middle on the network connection. It has the ability to stop the reoriented network connection.
- CrackMapExec: This is a tool used to perform testing on the active directory with help of different types of technology.
- SQLmap: SQLmap is another open-source tool that assists you with robotizing the discernment alongside it the usage of SQL infusion mistakes and edict of information base servers.
- Apart from this tool we also have different tools.
FAQs
Given below are the FAQs mentioned:
Q1. How many types of penetration testing are there?
Answer: Basically, there are three different types of penetration such as back-box, white-box, and gray-box assessment.
Q2. What are the different stages of penetration testing?
Answer: There are five different stages. Planning is the first stage and Scanning in this stage determines how the destination responds to different Intrusion, Gaining Access, Maintaining Access, and Analysis.
Q3. Can we do penetration testing on the database?
Answer: Yes, we can do penetration testing on databases and we have different tools such as sqlmap, sqlninja, WPScan, Joomscan, and SSL Scanning tools.
Conclusion
From the above article, we have taken in the essential idea of Kali penetration testing and the representation of Kali Linux penetration testing. From this article, we saw how and when we use Kali Linux penetration testing.
Recommended Articles
This is a guide to Kali Linux Penetration Testing. Here we discuss the introduction, use, database tools, and applications. You may also have a look at the following articles to learn more –