What is a Keystroke
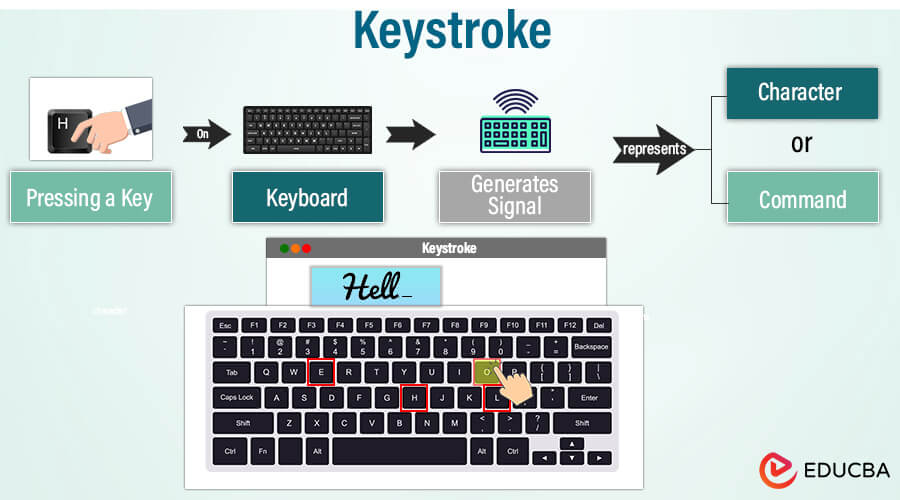
A keystroke relates to the act of pressing a key on a computer keyboard or a similar input device, such as a typewriter or a numeric keypad. Each keystroke produces an electrical code that the computer’s hardware and software translate into characters or actions on the screen. Keystrokes are fundamental to text input and interaction with computers, as they are used to enter letters, numbers, symbols, and various commands to control the computer’s functions and software applications. You can also use the term “keystroke” to monitor or record the sequence of keys a user presses, often for security or analytical purposes.
Key Takeaways
- The discrete actions of pushing keys on a keyboard are called keystrokes.
- Essential for computer interaction, translating to specific codes or characters.
- Fundamental to programming, typing, and using software.
- Permit text entry and command execution.
- Critical for communication with computers and devices.
- Serve as the foundation for user communication in computer settings.
Table of Contents
Types of Keystroke
Three main types broadly categorize keystrokes:
- Click Keystrokes: These keystrokes involve pressing a key on the keyboard, such as letters, numbers, and special characters.
- Modifier Keystrokes: These keyboard combinations include manipulating the behavior of other keys when pressed in conjunction with them by using keys such as Shift, Ctrl, Alt, or the Windows key.
- Function Keystrokes: These keystrokes involve using the function keys (F1 through F12) to trigger specific functions or commands within software applications.
Anatomy of a Keystroke
The anatomy of a keystroke” examines the elements and procedures involved when you press a key on a keyboard. It involves learning about electronic operations through circuitry and controllers, understanding physical components such as keycaps and switches, and experimenting with different keyboard configurations. It summarizes what occurs when you push a key on your keyboard.
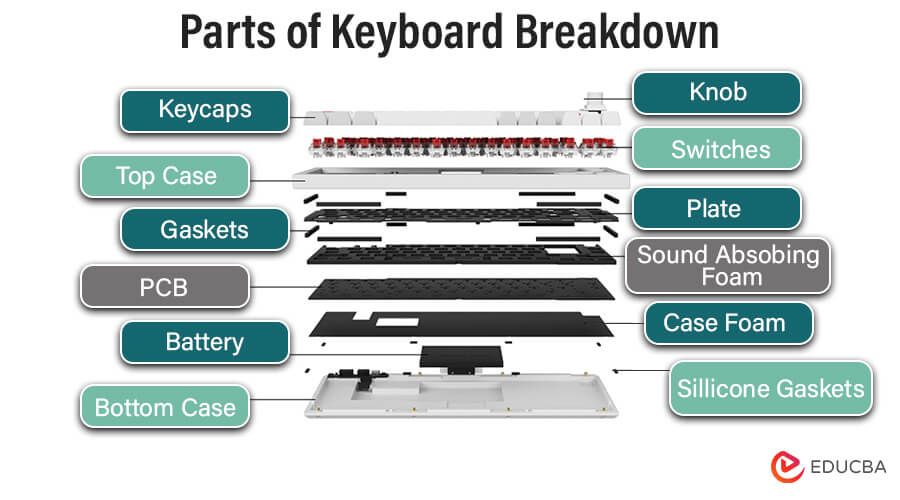
Physical components of a Keyboard
Keycaps:
The areas of keys that users push that are visible and tactile are called keycaps. Typically, they feature markings, symbols, or letters that denote the letter or function allocated to them.
Key Switches:
Key switches, located under the keycaps, register keystrokes. Silent and affordable membrane switches provide tactile feedback, but mechanical switches, However, mechanical switches see more common usage.
Top Case:
The top case is the upper part of the keyboard housing that holds the keycaps and switches. It provides protection and structural support to the internal components.
Gaskets:
Flexible seals, often made of silicone, serve as gaskets. In the context of keyboards, gaskets serve to reduce vibrations. Dampen keystroke noise and create a more comfortable typing experience. They absorb shocks and minimize sound between different components.
Plate:
The plate is a rigid component that holds the switches in place. It is typically made of metal or plastic and provides stability to the switches. The plate can also influence the overall feel of key presses.
Circuit Board(PCB)
The electronic components that allow the keys and the computer to communicate are housed on the circuit board, often known as the PCB (Printed Circuit Board). Every key on the board has a corresponding circuit.
Sound Absorbing Foam:
Sound-absorbing foam is often placed inside the keyboard’s case to reduce noise generated by key presses. It helps dampen vibrations and minimize the sound produced by the internal components.
Silicone Gaskets:
As mentioned previously, manufacturers use silicone gaskets in various parts of the keyboard to absorb shocks, reduce vibrations, and give key presses a softer feel. Commonly, they are placed between the keycaps, switches, and other components to enhance the typing experience.
Case Foam:
Case foam refers to additional foam padding placed inside the keyboard’s case. It contributes to sound dampening and helps create a more solid and refined feel when typing.
Bottom Case:
The bottom case is the lower part of the keyboard housing. It provides structural support, protects internal components, and, along with the top case, encloses all the keyboard elements.
Connectors and Cables
Keyboards usually use connections and cables to establish a physical connection with the computer or other device. USB, PS/2, and wireless interfaces like Bluetooth are standard connectors.
Backplate
The backplate is a rigid surface that supports the key switches and provides stability to the keyboard. It helps maintain the proper spacing and alignment of the keys.
Case and Frame
The case or frame is the outer shell of the keyboard that houses all the internal components. It provides structural support, protects the internal parts, and often includes features like tilt legs for ergonomic adjustments.
How keys are registered electronically
Contact Closure:
In a key switch, pressing a key results in a physical contact closure. By completing an electrical circuit, this closure alerts the keyboard controller to the press of a particular key.
Direct Wiring or Matrix:
Keyboards arrange and link the keys to the controller using direct wiring or a matrix. Although matrix layouts reduce the need for wiring, they may have drawbacks, such as ghosting, which happens when accidental keys are registered.
Keyboard Controller:
The keyboard controller receives electrical impulses from pushed keys, processes them, and outputs digital data that the computer can understand. It sends this information to the computer’s operating system.
Overview of keyboard layouts
Type keyboard layouts can vary greatly depending on the specific design and the language or input method they’re intended for.
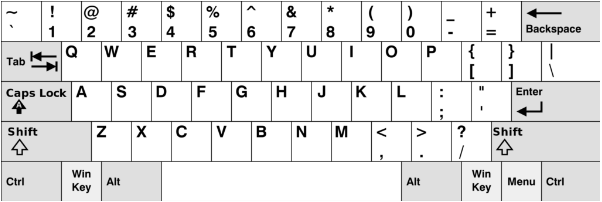
QWERTY Layout:
The QWERTY keyboard layout holds the status of being the most commonly used layout on computer keyboards. The first six letters in the top row provide the basis for its name. Its purpose was to prevent typewriter jams by spacing out frequently used letters.
AZERTY Layout:
The AZERTY keyboard layout, primarily used in French-speaking areas, is comparable to QWERTY but differs in some letters and symbols’ arrangement.
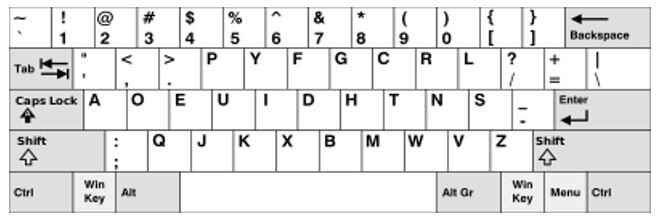
DVORAK Keyboard Simplified:
The DVORAK layout’s home row contains the most frequently utilized keys, which improves typing efficiency. It seeks to speed up and decrease finger movement.
Colemak Configuration:
Another arrangement called Colemak aims to strike a compromise between efficiency and familiarity. It seeks to enhance typing comfort and provide a smoother switch from QWERTY.
Keystrokes in Digital Communication
Keystrokes in digital communication involve pressing keys on a keyboard to input characters or commands into a computer. Each key generates an electrical signal corresponding to a specific function, crucial for typing, sending emails, or entering passwords. Keylogging can raise security concerns, and it’s crucial to ensure input efficiency for a better user experience. Different keyboards, including physical and virtual ones, facilitate this fundamental aspect of digital communication.
Text Input:
There are many keystrokes involved in typing text. Users compose and send messages using keyboards on various digital communication platforms, including social media, emails, and messaging apps.
Editing:
Users need keystrokes to alter and fine-tune text in digital communication tools after initially entering it. Users may quickly edit, improve, and correct their communications by using keystroke shortcuts for operations like copying, pasting, and deleting text.
Accessibility:
Keystrokes are an essential accessibility element for people with trouble interacting with a mouse. These people can use keyboard input to access digital communication platforms, guaranteeing usability and inclusion.
Shortcuts:
Combinations of keys are helpful quick cuts that speed up routine tasks in digital communication interfaces. For example, utilizing keyboard shortcuts like Ctrl+C to copy or Ctrl+Enter to send a message improves productivity by streamlining the user experience.
Security:
For digital communication to be secure, keystrokes are essential. Users depend on keystrokes to safely enter passwords and other sensitive data, protecting access to their accounts and preserving the privacy of their communications.
Keystrokes and Shortcut Commands
Keystrokes and shortcut commands are integral components of digital interaction, providing users with efficient ways to navigate the software, perform tasks, and streamline their workflow.
Shortcut Commands
Shortcut commands denote distinct keystroke combinations or sequences that initiate predetermined activities within software programs. These shortcuts aim to increase user productivity by speeding up tasks. For example, you often use the keyboard shortcut “Ctrl+C” to copy selected text and “Ctrl+V” to paste it somewhere else. Many software programs, including word processors, graphic design tools, web browsers, and operating systems, provide shortcut commands.
Examples of Shortcut Commands:
- Copy: Ctrl+C (Windows/Linux) or Command+C (Mac)
- Paste: Ctrl+V (Windows/Linux) or Command+V (Mac)
- Cut: Ctrl+X (Windows/Linux) or Command+X (Mac)
- Undo: Ctrl+Z (Windows/Linux) or Command+Z (Mac)
- Save: Ctrl+S (Windows/Linux) or Command+S (Mac)
- Select All: Ctrl+A (Windows/Linux) or Command+A (Mac)
Customization:
Many software programs let users design or make their shortcut instructions according to their preferences and working methods. This flexibility allows Users to customize their digital experience to meet their demands better.
Keystroke Logging and Security
Explanation of keystroke logging
Keystroke logging, also known as Keylogging, is a technique for keeping track of user keystrokes on a computer or mobile device. Designers create keyloggers to capture all keystrokes, capturing credit card numbers, passwords, and confidential information. They can be either hardware- or software-based. Genuine keyloggers serve system monitoring and troubleshooting purposes, but malicious keyloggers can seriously jeopardize user security and privacy.
Working on Keystroke Logging
Software-Based Keyloggers: These keyloggers are typically malware or malicious programs that infect a user’s system. They can record keystrokes, capture screenshots, and even monitor the clipboard for copied information.
- Installation:
- Disguised as legitimate software or bundled with malware/phishing emails/attachments.
- User interaction triggers installation (e.g., clicking a link or opening an attachment).
- Operation:
- It operates silently in the background, logging keystrokes and monitoring system events.
- May log keystrokes to a file, transmit them to a remote server, or both.
- Can capture additional information like window titles, timestamps, and clipboard contents
Hardware-Based Keyloggers: Physical devices can be attached to a computer or placed between the keyboard and the computer. These devices intercept and record keystrokes as they pass through.
Risks and Dangers Associated with Unauthorized Keystroke Logging:
- Identity Theft: Using stolen login credentials can result in financial information and identity theft.
- Privacy Invasion: Keystroke tracking can compromise emails, private conversations, and other sensitive data, compromising privacy.
- Financial Loss: Information entered during online transactions, such as credit card numbers and banking details, may be intercepted and result in financial loss.
- Theft of Credentials: Email addresses and usernames for various services, such as social media and email, can be compromised.
- Exposure to Sensitive Data: Keystroke loggers can record sensitive data, like trade secrets or intellectual property, which puts companies in danger.
How to protect against Keystroke Logging Attacks
To prevent malicious software or devices from gathering personal information, it is necessary to adopt security measures to avoid keystroke recording attacks. These are a few tactics:
Use Antivirus and Anti-Malware Software:
Use trustworthy anti-virus and anti-malware programs that can identify and eliminate keyloggers. To guarantee that the program contains the most recent threat definitions, update it frequently.
Firewall Protection:
Enable and configure firewalls on your computer or network to keep an eye on and manage incoming and outgoing traffic. It reduces the likelihood of illegal access and the transfer of captured keystrokes.
Secure Your System:
Update your operating system and apps with the most recent security updates. And update your system frequently to fix security holes that keyloggers might exploit.
Be Cautious with Downloads:
Software from unreliable sources should not be downloaded or installed. Malicious keyloggers can pass for trustworthy apps. Download software only from reliable sources, and always double-check the source.
Use Virtual Keyboards:
When entering sensitive information, use virtual keyboards to input data by clicking on on-screen keys with a mouse. It can bypass physical keyloggers that capture keystrokes from a hardware keyboard.
Secure Your Wi-Fi Network:
Encrypt your Wi-Fi network using WPA3 or WPA2 protocols to prevent unauthorized access. It helps protect against remote keylogging attacks that may occur over unsecured networks.
Implement Two-Factor Authentication (2FA):
Enable two-factor authentication whenever possible. Even if a keylogger captures your password, a second authentication factor (e.g., a code sent to your mobile device) adds an extra layer of security.
Regularly Check for Suspicious Activity:
Monitor your system for unusual behavior, such as unexpected network traffic or changes in system performance. Unexplained anomalies may indicate a potential keylogging threat.
Use Keystroke Encryption Software:
Employ specialized keystroke encryption software that encrypts the data as it travels from the keyboard to the application. It makes it more challenging for keyloggers to capture meaningful information.
Educate and Raise Awareness:
Teach people to spot phishing efforts and to exercise caution when opening unknown attachments or clicking on dubious links. Social engineering often achieves the distribution of keyloggers.
Evolving Trends
Keystrokes, as a fundamental aspect of human-computer interaction, continue to evolve, influenced by technological advancements and changing user needs. Several trends are shaping the utilization and security of keystrokes in various digital environments.
1. Gesture-Based Input:
Description: With touch-enabled devices in particular, gesture-based input techniques are becoming more and more common. Gestures such as swiping and tapping allow users to enter text and commands.
Impact: Improved touchscreen device usability, offering a substitute for conventional typing.
2. Voice Recognition and Ordering:
Description: Voice recognition technology is integrated so users can speak commands and input text.
Impact: Better efficiency, hands-free use, and increased accessibility, especially for mobile and smart home applications.
3. Auto-Correction and Predictive Typing:
Description: As users type, context-aware recommendations are provided by more advanced predictive typing algorithms and auto-correction capabilities.
Impact: Improved typing efficiency overall and a decrease in the requirement for manual corrections due to faster and more accurate text input.
4. Interactive Keyboards:
Description: More and more keyboards are adjusting to the context and behavior of their users. The keyboard arrangement, size, or display may vary depending on the program or language used.
Impact: Users can work more comfortably and efficiently by customizing the keyboard interface to certain jobs or preferences.
5. Dynamics of Biometric Keystrokes:
Keystroke dynamics—an analysis of each person’s distinct typing pattern—are increasingly being investigated for biometric authentication.
Impact: Increased security by using biometric verification adds an extra degree of authentication on top of conventional techniques.
Conclusion
Keystrokes are the fundamental building blocks of digital communication because they allow users to enter data onto electronic devices via keyboards. The physical parts of a keyboard, such as the key matrix, switches, and keycaps, make this procedure possible. To protect sensitive data from keystroke logging attacks, companies must implement firewalls, antivirus programs, encryption, and other security measures as part of a comprehensive security strategy. Individuals and businesses can confidently navigate the digital landscape by being alert, using secure practices, and utilizing technological safeguards. This lessens the dangers connected to possible dangers to the reliability of keystroke-based input systems.
FAQs
Q1. What are key rollover and anti-ghosting in keyboards?
Answer: The term “key rollover” refers to the ability of a keyboard to register multiple keystrokes simultaneously. When several keys are touched simultaneously, anti-ghosting technology stops false key presses, guaranteeing correct input.
Q2. How do I troubleshoot keyboard issues related to keystrokes not registering?
Answer: To find and fix the problem, you can check for physical damage, reconnect the keyboard, update drivers, or test the keyboard on a different computer using troubleshooting techniques.
Q3. Are there alternative input methods besides keystrokes?
Answer: Certainly, gestures, voice recognition, and touchscreens are examples of other input modalities. However, typing continues to be the most common and meaningful way to enter data on desktop and laptop computers.
Q4. Can I change the keyboard layout to suit my preferences?
Answer: Yes, a lot of operating systems let users customize keyboard layouts to fit their own tastes or different language requirements. AZERTY, Dvorak, and QWERTY are common keyboard layouts.
Q5. What is key mapping, and how can it enhance my keyboard usage?
Answer: Key mapping is a personalized and effective approach for users to operate applications, carry out orders, and automate repetitive chores by assigning particular functions or actions to individual keys.
Recommended Articles
We hope that this EDUCBA information on “Keystroke” was beneficial to you. You can view EDUCBA’s recommended articles for more information.