Updated April 18, 2023

Introduction to Linux iptables
In the Linux operating system, iptables is a utility or tool to manage the firewall rules in the environment. Similarly, we have one more tool to manage the firewall rules on the Linux, i.e., firewalld. The iptables are used to manage setup and examine the IP packets in the Linux kernel. It will help to restrict unwanted packets in the environment. It will hold the number of built-in chains known as the system chain and user-defined chain.
Rusty Russell originally wrote the iptables in early consultation with Michael Neuling. The man page of the iptables was originally written by Herve Eychenne (email ID: rv@wallfire.org).
Syntax of the Linux Iptables
iptables [-t table] {-A|-C|-D} chain rule-specification- iptables: We can use the “iptables” keyword in the syntax or command. It will take different arguments like table name, options, system or user chain, set of specific rules, etc. As per the provided arguments, it will manage the setup and examine the IP table.
- OPTIONS: We can provide the different flags as the option that is compatible with the “iptables” command.
- Chain: As per the condition or requirement, we can use the system chain or the user-defined chain.
How Linux Iptables Works?
Linux is a multi-user support operating system. It will support multiple servers or applications. While running these servers or applications, it is very important to manage the packet securities. The iptables have the capability to manage it. It will create a set of rules in the environment, and as per the rules, the flowing packets will allow or restrict.
Below are the lists of options that are compatible with the iptables command.
| Sr No | Option | Description |
| 1 | -A, –append chain rule-specification | It will help to append one or more rules to the end of the selected or current chain. |
| 2 | -C, –check chain rule-specification | It will help to check the rule whether it is matching the specification or not in the selected chain. |
| 3 | -D, –delete chain rule-specification
-D, –delete chain rulenum |
Both the option will help to delete the one or more rules from the selected or current chain. |
| 4 | -I, –insert chain [rulenum] rule-specification | It will help Insert one or more rules in the current or the selected chain (per the given rule number). |
| 5 | -R, –replace chain rulenum rule-specification | It will help to replace the rule in the selected chain. |
| 6 | -L, –list [chain] | It will help to list out all the rules in the selected chain. If no chain is selected, then it will list all the chains. |
| 7 | -S, –list-rules [chain] | It will help to print all rules in the selected chain. If the no chain is selected, then it will print all the chains as the iptables save. |
| 8 | -w, –wait [seconds] | This option helps to Wait for the xtables lock. It will help to prevent multiple instances of the job or the application. By default in nature, the program will exit automatically if the lock cannot be obtained. It will hold the program until the exclusive lock can be obtained. |
| 9 | -W, –wait-interval microseconds | It will help to wait for the interval to wait per each iteration. When running a sensitive application, and may observe the latency in the application or the job level. It will wait for the xtables lock for extended durations (which may not be acceptable). This option will only work with the “-w.” |
| 10 | -n, –numeric | It will help to give the output in terms of Numeric format. The IP addresses and the port numbers will be printed in the numeric format. But in the default nature, the program will try to print the output in terms of the network names, hostnames, or the applicable services. |
| 11 | -x, –exact | It will help to expand the numbers. It will also help to display the correct value of the byte counters and packet. This option will help to revert for the -L command. |
| 12 | –line-numbers | It will help to get the information on the rule’s position in the chain. When the listing rules, add line numbers to the beginning of each rule |
| 13 | –modprobe=command | While adding or inserting the rules into the chain. It will help to use the command to load any necessary modules such as targets, match extensions, etc. |
Examples of implementing Linux Iptables
Below are the examples of Linux Iptables:
Example #1 – Check IP Tables Rule
In the Linux environment, we can check the list of iptables rules available in the environment.
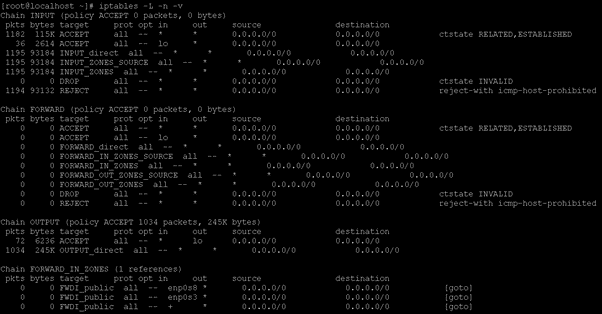
Command :
iptables -L -n -vExplanation :
As per the above command, we are listing the number of rules available in the working environment.
Output:
Example #2 – Block the IP Address
In the iptables, we have the functionality to block the specific IP address in the environment.
Command :
iptables -A INPUT -s 10.10.189.57 -j DROPExplanation :
As per the above command, we are blocking the 10.10.189.57 IP address.
Output :
Example #3 – Unblock the IP Address
While working with the Linux iptables, we can also unblock the IP address.
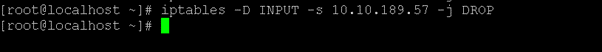
Command :
iptables -D INPUT -s 10.10.189.57 -j DROPExplanation :
As per the above command, we are unblocking the 10.10.189.57 IP address.
Output :
Example #4 – Block Outgoing Port
In Linux, we can disable the outgoing port traffic.
Command :
iptables -A OUTPUT -p tcp --dport 80 -j DROPExplanation :
We are blocking the outgoing traffic of the environment and blocking port no 80.
Output :
Example #5 – Block Incoming Port
In the iptables, we have the functionality to block the incoming port traffic.
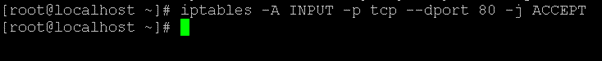
Command :
iptables -A INPUT -p tcp --dport 80 -j ACCEPTExplanation :
We are blocking the incoming traffic of the environment and blocking port no 80.
Output :
Conclusion
We have seen the uncut concept of “Linux Iptables” with the proper example, explanation, and command with different outputs. As per the requirement, we can create or drop the iptables or firewall rules. We can block or unblock the IP address or port as well.
Recommended Articles
We hope that this EDUCBA information on “Linux iptables” was beneficial to you. You can view EDUCBA’s recommended articles for more information.