How to Secure Linux? Critical Tools and Tips to Protect
Securing your Linux Server is critical to maintaining system integrity, protecting sensitive data, and ensuring the smooth functioning of your services. A Linux VPS (Virtual Private Server) accessible over the Internet is particularly vulnerable to malicious attacks like DDoS, brute-force attempts, and malware infections. Implementing robust Linux VPS security measures helps safeguard your server from these threats.
In this article, we will look at the tools and strategies to enhance Linux VPS security and protect your server.
Why Linux VPS Security Should Be a Top Priority?
Without proactive security measures, your Linux VPS becomes an easy target for:
- Distributed Denial of Service (DDoS) Attacks: These flood your server with excessive traffic, causing it to crash or go offline.
- Brute-Force SSH Login Attempts: Attackers can break into your system by repeatedly trying multiple login attempts.
- Malware Exploits: Vulnerabilities in outdated software can allow malware to infiltrate your system.
Implementing the right security tools and techniques reduces the risks of such attacks, ensuring your VPS remains secure and reliable.
Top Tools and Techniques to Secure Your Linux Server
Securing a Linux system requires multiple layers of protection to defend against various threats. For Linux VPS users, it is essential to implement the right security measures to prevent data breaches, downtime, and malicious attacks. Below are the most effective tools and techniques to secure your Linux VPS:
#1. Firewalls (UFW, iptables)
Firewalls are crucial for controlling incoming and outgoing traffic, helping to block unauthorized access.
- UFW (Uncomplicated Firewall): A simple, easy-to-use front-end for iptables.
- iptables: A powerful tool that allows advanced traffic filtering.
Both allow you to set network traffic rules, block malicious connections, and limit exposure to potential attackers, ensuring robust Linux VPS security.
#2. Intrusion Detection Systems (IDS)
IDS tools monitor suspicious activity to prevent unauthorized access, especially from brute-force attacks.
- Fail2ban: Automatically blocks IP addresses showing malicious behavior, such as repeated failed login attempts.
- Snort: A more advanced IDS that analyzes network traffic and alerts you to potential threats.
#3. Mandatory Access Control (SELinux or AppArmor)
These systems enhance security by enforcing policies that limit the actions users and applications can perform.
- SELinux (Security-Enhanced Linux) and AppArmor reduce the risk of unauthorized access by ensuring that processes have only the necessary permissions.
#4. SSH Key Management and Disabling Root Login
SSH key authentication is safer than using passwords.
- Disable root login: Prevent attackers from accessing your system using default or weak credentials.
- SSH Key Authentication: Only authorized users with the correct SSH key can connect to your server, improving security.
#5. Two-Factor Authentication (2FA) for SSH
Add an extra layer of protection to SSH access.
- Two-Factor Authentication (2FA) requires both your SSH key and a temporary code for access, making it much harder for attackers to get in, even if they have your password.
#6. Regular Software Updates and Patching
Keeping your system up to date is vital for securing your server.
- Keep your system updated by regularly applying security patches to fix vulnerabilities before attackers can exploit them.
- Package managers like apt (Debian-based systems) or yum (CentOS) can be used to automate this process.
#7. Use Strong Passwords
Strong passwords are one of the most useful ways to prevent unauthorized access.
- A strong password should be at least 12 characters long and contain a combination of numbers, lowercase letters, uppercase letters, and special characters.
- Avoid using easily guessed passwords and use a password manager to create and store strong, secure passwords.
- Use tools like PAM (Pluggable Authentication Module) to enforce password policies.
#8. Secure Your OpenSSH Configuration
Securing OpenSSH is crucial to prevent unauthorized access.
- Disable root login to restrict access to only users with the proper SSH key.
- Use SSH key authentication instead of passwords.
- Limit SSH access to specific trusted IP addresses and change the default SSH port to make it harder for automated attacks to target your server.
#9. Restrict Sudo Usage for Enhanced Security
The sudo command grants administrative privileges, which can be risky if misused.
- Only grant sudo access to trusted users who need it.
- Limit the commands users can execute with sudo by carefully configuring the sudoers file.
- Regularly review sudo privileges and remove unnecessary permissions to reduce the risk of privilege escalation.
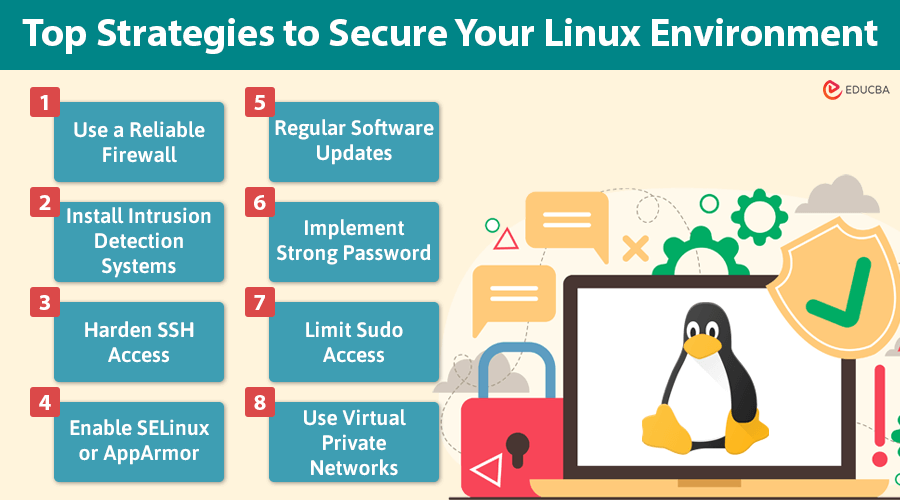
Top Strategies to Secure Your Linux Environment and Protect Data
Here are the top strategies to strengthen Linux VPS security:
- Use a Reliable Firewall (UFW, iptables): Control incoming and outgoing traffic to your server, blocking unwanted connections.
- Install Intrusion Detection Systems (IDS): Tools like Fail2ban and Snort monitor suspicious activities and prevent brute-force attacks.
- Harden SSH Access: To secure remote access, disable root login, use SSH key authentication, and implement two-factor authentication (2FA).
- Enable SELinux or AppArmor: These tools enforce mandatory access control, limiting user and application actions.
- Regular Software Updates: Apply security patches promptly to fix vulnerabilities before attackers can exploit them.
- Implement Strong Passwords: Use long, complex passwords for all accounts and enforce password policies to avoid weak credentials.
- Limit Sudo Access: Restrict sudo privileges to trusted users only, reducing the potential for privilege escalation.
- Use Virtual Private Networks (VPNs): Using a VPN adds extra encryption to the network traffic between your server and clients, making it harder for attackers to access sensitive data.
- Configure Log Monitoring and Alerts: Regularly monitor logs (e.g., system, authentication, and application logs) to detect unusual activity early. Set up log monitoring tools to trigger alerts on suspicious activity.
- Security Audits with OpenVAS: OpenVAS (Open Vulnerability Assessment Scanner) can help you identify security vulnerabilities by running comprehensive audits of your Linux system. It ensures that your security measures are up-to-date and effective.
- Use Docker Containers for Isolation: Docker containerization isolates applications, preventing them from accessing unnecessary parts of your system. This method limits the impact of a potential attack by containing it within the container.
- Backup and Disaster Recovery Plans: Make regular backups of your data and test your recovery procedures. A solid disaster recovery plan minimizes downtime and data loss in case of an attack.
- Use Security-Enhanced Kernel (grsecurity): grsecurity is a kernel patch set that improves Linux VPS security. It adds multiple security features, including access control, memory corruption protection, and auditing.
Final Thoughts
Securing your Linux VPS protects sensitive data and maintains system integrity. By taking proactive steps like configuring firewalls, enabling SELinux or AppArmor, securing SSH access, using strong passwords, and enabling two-factor authentication (2FA), you can defend against common threats such as brute-force attacks, malware, and DDoS. Keeping your system updated with security patches, limiting sudo access, and regularly reviewing user privileges enhance Linux VPS security. Investing in a secure Linux VPS protects against breaches and helps safeguard your system.
Recommended Articles
We hope this guide on Linux VPS Security has been helpful. Check out these recommended articles for more information on advanced server protection and system administration best practices.

