Introduction to Lock Based Protocols in DBMS
The DBMS houses data that can interact with one another and can be manipulated at any given instant. In a few scenarios, there is a possibility of more than one user trying to access a certain data item at the same time creating a concurrency. Thus, a need arises to deal with the said concurrency to handle the simultaneous execution of tractions among the multiple databases in the picture. One such method is termed as Lock Based Protocols. In this topic, we are going to learn about Lock Based Protocols in DBMS.
Lock Based Protocols eliminate the shortcomings caused by the concurrency access in DBMS by providing the required isolation to the tractions involved within the DBMS.
This article tends to provide an insight on Lock Based Protocols in DBMS.
What is Lock Based Protocols in DBMS?
Hundreds of transactions happen each moment. Consider booking a movie ticket in your favorite cinemas, chances are two users will try to book the same seat unknowing to one another. A scenario like this, when dealt on a large scale, might affect the database consistency leading to the corruption of data. In order to avoid conflicts w.r.t the user access to read and write into the database, and to maintain consistency throughout the DBMS, each traction must be enforced in isolation. This task is achieved by implementing Lock Based Protocols in DBMS.
Lock based Protocols in simpler terms helps overcome the issues related to accessing the DBMS concurrently by locking the current transaction for only one user. The assumption or more like a requirement that is necessary for implementing Lock Based Protocol is that all the data items involved are accessed in a mutually exclusive manner i.e. when one traction is active by a user, no other traction is allowed access to update or modify that traction at the same time. As the name suggests, the Lock based protocols when in action, are required to acquire a lock to access the data items and release the lock when the said traction is completed.
Types of Locks in DBMS
The locking and unlocking of data items in Lock based Protocols in DBMS are implemented in 2 modes:
- Shared Lock (lock-S)
- Exclusive Lock (lock-X)
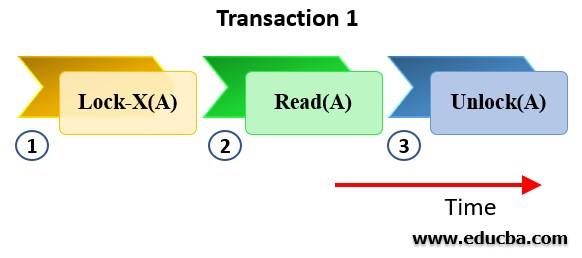
1. Shared Lock
Often represented as lock-S(), Shared Locks are basically the locks that grant Read-Only access to the data items associated with it. This means when a shared lock is implemented on a database, it can be READ by multiple users, however, none of the users reading the data items will be able to update it. In other words, there is no write access associated with Shared Lock. Since multiple users can read the data items simultaneously, more than one shared lock can be placed on them at a given time but for the shared lock to be placed, the data item must not have any other locks associated with it.
Example of shared Lock:
Consider a transaction(T1) which requires only to read the data item value A. The following steps take place when lock protocol is applied to this traction
- T2 will acquire an exclusive lock on the data item A
- Read the current value of data item A
- Once the transaction is completed, the data item will be unlocked
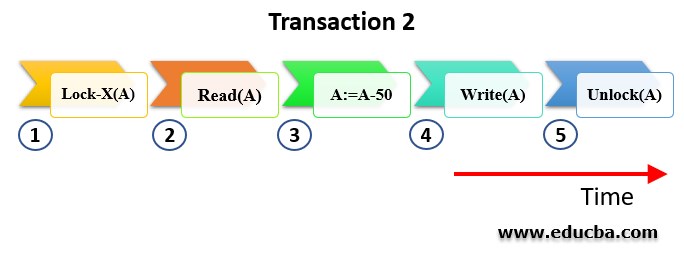
2. Exclusive Lock
While Shared Lock allows Read-Only access, Exclusive Locks allow both Read and Write access on a data item present in the database. Often represented as lock-X(), Exclusive locks provide the privilege of reading and modifying the data as seen fit by a user. For the sake of security and consistency of the database, this process will be exclusive to the user using them and is not permitted to other users trying to access the same data item. Once the exclusive lock is placed, no other locks including the Shared lock can be placed on the same row or column until its unlocked.
Example of Exclusive Lock:
Consider a transaction(T2) which requires to update the data item value A. The following steps take place when lock protocol is applied to this traction
- T2 will acquire an exclusive lock on the data item A
- Read the current value of data item A
- Modify the data item as required. In the example illustrated, a value of 50 is subtracted from the data item A
- Write the updated value of the data item
- Once the transaction is completed, the data item will be unlocked.
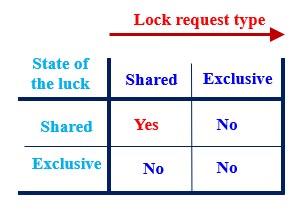
Lock Compatibility Matrix
A keynote while applying the Lock based protocols in DBMS is that: any number of tractions can hold a Shared Lock while only one traction has a claim over Exclusive Lock since because shared lock is only reading the data and not performing any other actions whereas the exclusive lock is performing both read and write operations. This can be illustrated using a compatibility matrix like the one shown below:
The figure illustrates that when two transactions are involved, and both attempt to only read a given data item, it is permitted and no conflict arises, but when one transaction attempts to write the data item and another one tries to read or write at the same time, conflict occurs resulting in a denied interaction.
Conversion between the locks is possible by the two methods listed below:
Upgrading: conversion from a read lock to write lock
Downgrading: conversion from a write lock to read lock
Problems associated with Simple locking:
- Data inconsistency between multiple transactions
- Deadlock, a situation where the transactions try to access lock on already locked data items
- No guarantee of serializability (i.e. execution of a concurrent transaction equivalent to that of a transaction executed serially)
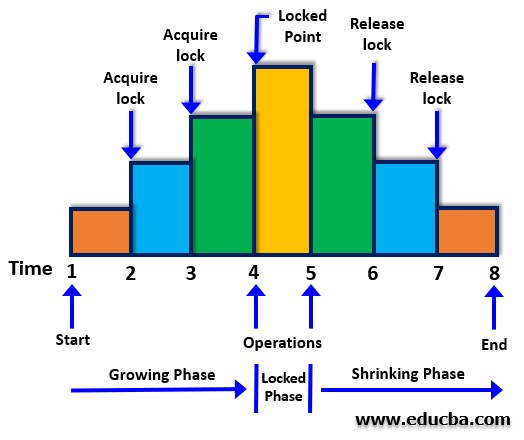
Two Phase Locking (2PL)
The trivial requirement for a 2PL to exist is that the locking and unlocking of a transaction take place in either of the 2 phases i.e. Growing or Shrinking phase
Growing Phase: It is the phase where new locks can be acquired on the data items.
Shrinking phase: It is the phase where the existing locks on the data items are released.
The above phases in a DBMS are determined by something called a ‘Lock Point’. Lock point is the point where a transaction has achieved its final lock. It is also the point where the growing phase ends and the shrinking phase begins.
Types of 2 Phase Locking (PL)
Here are the types of 2 phase locking mention below
1. Conservative 2PL
Conservative or Static 2PL when implied acquires all the locks before a transaction begins and releases the locks once the transaction is committed. This kind of 2 PL helps in overcoming problems related to cascading rollback and deadlocks.
2. Strict 2PL
In this type of 2PL, the exclusive (write) lock is released only after a transaction is committed, whereas a shared (read) lock can be released at regular intervals. Though Strict 2PL helps overcome the cascading rollback issues, it may also cause a bottleneck in some cases.
3. Strong strict or Rigorous 2PL
In this type of 2PL, both shared and exclusive locks are released only when the transaction is ended, i.e. when the transaction is committed or aborted. This kind of 2PL is used in practice today, promotes serializability and is simpler to implement due to the strictness involved w.r.t the implementation of the phase endings.
Conclusion
Concurrency control is essential in DBMS for handling the simultaneous execution of transactions among various databases. Lock Based Protocols being an essential member in the concurrency control technique enforces isolation among the transactions, preserve and maintain the reliability of the database, and resolve the conflicts of read-write and write-read operations. In addition to Lock based Protocols concurrency control can also be achieved via methodologies such as Timestamp Protocol, Mutilversion concurrency Protocol, and Validation Concurrency Protocols.
Recommended Articles
This is a guide to Lock Based Protocols in DBMS. Here we discuss what is Lock Based Protocols in DBMS and its types along with the examples and 2 Phase Locking. You may also look at the following articles to learn more –