Updated December 8, 2023
Difference Between Maskable and Non-Maskable Interrupts
Interrupts are crucial in computer systems, enabling them to respond to external events promptly. Maskable interrupts and non-maskable interrupts are two distinct types with unique characteristics. The system can temporarily turn off or “mask” maskable interrupts, enabling controlled interruption handling. In contrast, non-maskable interrupts are essential events that the system cannot ignore or delay, ensuring prompt responses to critical situations. Understanding the differences between these interrupt types is fundamental for designing reliable and responsive computer systems, influencing everything from hardware architecture to software development.
Table of content
- Difference Between Maskable and Non-Maskable Interrupts
- What is Maskable?
- What are Non-Maskable Interruptions?
- Key Difference: Maskable and non Maskable interrupts
- Choosing between Maskable and Non-Maskable interrupts
What is Maskable?
Maskable” refers to the capability of temporarily disabling or ignoring a specific type of interrupt in a computer system. In the context of interrupts, a maskable interrupt can be masked or blocked by the system, meaning that its processing can be postponed or temporarily halted. This ability to mask interrupts allows the system to prioritize certain tasks or prevent specific interrupt sources from disturbing critical operations. Maskable interrupts are often used to manage the flow of interrupt requests in a controlled manner, enabling the system to handle them based on its current state and priorities.
RST 7.5, RST 6.5, RST 5.5: These are examples of maskable interrupts in the 8085 microprocessor. They are software interrupts and can be turned on or off based on the system’s needs. These interrupts allow the software to initiate specific routines when required.
Role in System Operation
The role of maskable interrupts in system operation is crucial for managing the flow of a computer system and handling various events. Here are critical aspects of their role:
- Event Handling: Maskable interrupts provide a mechanism for the system to respond to external events. These events can include signals from peripherals, hardware devices, or software conditions that require immediate attention.
- Priority Management: Maskable interrupts often have different levels of priority. The system can be configured to give higher priority to critical events, ensuring that they are addressed before less critical ones. This enables for more efficient use of system resources.
- Program Control: By turning specific maskable interrupts on or off, programmers can control when interruptions occur. This control is essential for managing the timing of interrupt service routines (ISRs) and ensuring that critical sections of code are not interrupted at inappropriate times.
- Customization and Flexibility: The ability to mask interrupts provides customization options for system designers and programmers. They can tailor the interrupt handling to suit the application’s requirements, optimizing system performance and responsiveness.
- Resource Allocation: Maskable interrupts play a role in resource allocation and sharing. For example, in a multitasking environment, the system may allocate processing time to different tasks based on the occurrence of specific interrupts, allowing for a more responsive and dynamic system.
- Error Handling: Some maskable interrupts may be associated with error conditions. By masking or unmasking these interrupts, the system can adapt its response to errors, either pausing normal operations to address the issue or continuing with a predefined error-handling routine.
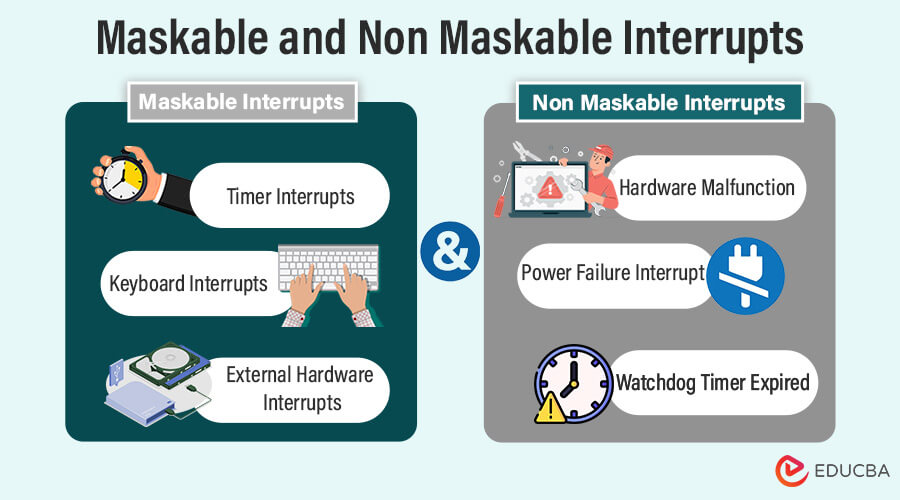
Examples of Maskable Interrupts
Maskable interrupts in a computer system are typically associated with events that can be temporarily disabled or masked, allowing the system to control when these interrupts are serviced. Here are some common examples of maskable interrupts:
1. External Hardware Interrupts:
- IRQ (Interrupt Request): When used in microprocessor-based systems, external devices can send an interrupt request to the CPU to gain attention.
- DMA (Direct Memory Access) Requests: Devices such as disk controllers or network interfaces may request data transfer access to the system’s memory.
2. Software Interrupts:
- INT (Software Interrupt): Some processors allow software to generate interrupts to initiate specific services or routines.
- TRAP Instruction: Triggered by specific instructions in the program, causing an interrupt to handle exceptional conditions.
3. Timer Interrupts:
- Clock Interrupts: An internal system clock or timer generates these interrupts, and users can employ them for tasks such as timekeeping, scheduling, or triggering periodic events.
4. Peripheral Interrupts:
- Serial or Parallel Port Interrupts: Devices connected to communication ports can generate interrupts when data is ready to send or receive.
- Keyboard Interrupts: The system must immediately attend to a signal generated upon pressing a key on the keyboard.
5. Maskable Software Exceptions:
- Floating-Point Exceptions: Systems with floating-point units can treat exceptions such as overflow or divide-by-zero as maskable interrupts.
- Memory Protection Violations: Programs generate interruptions when accessing restricted memory areas.
6. System Calls:
- SWI (Software Interrupt) in ARM architecture: ARM-based systems use system calls to allow user programs to request services from the operating system.
Handling Maskable Interrupts
Handling maskable interrupts involves several steps to ensure the system responds appropriately to external events while maintaining control over the interrupt process. Here’s a brief overview of handling maskable interrupts:
- Interrupt Detection: The system continuously monitors for external events that may trigger maskable interrupts, such as hardware signals, timer overflows, or software instructions.
- Interrupt Request (IRQ): When an interrupting event occurs, the CPU receives an interrupt request (IRQ) to alert it that attention is needed for the interrupt.
- Context Switching: The CPU performs a context switch, saving the current state of the program (registers, program counter, etc.) to memory. This allows the system to resume normal execution after handling the interrupt.
- Interrupt Controller: The interrupt controller prioritizes and manages multiple interrupt requests. It may temporarily mask or enable specific interrupts based on their priority levels.
- Interrupt Vector Table (IVT): The system relies on an interrupt vector table, a data structure that maps each interrupt type to a specific memory address containing the corresponding interrupt service routine (ISR).
- Context Restoration: If the interrupt caused a context switch, the system restores the saved state, allowing the interrupted program to resume execution seamlessly.
- Interrupt Service Routine (ISR): The CPU jumps to the memory location specified by the interrupt vector table, executing the ISR associated with the triggered interrupt. The ISR performs the necessary tasks to address the interrupting event.
- Interrupt Acknowledgment: After handling the interrupt, the system acknowledges the interrupt controller, indicating that the interrupt has been serviced. This step may involve clearing flags or registers to prepare for the next interruption.
- Return from Interrupt (RTI): Some architectures use a specific instruction, such as “Return from Interrupt” (RTI), to complete the interrupt handling process and return control to the interrupted program.
- Enabling/Disabling Interrupts: Programmers can control the maskable interrupts by turning them on or off as needed, using instructions or flags provided by the system.
What are Non-Maskable Interruptions?
Non-maskable interrupts (NMIs) are crucial in computer systems as they cannot be postponed or ignored. Unlike maskable interrupts, NMIs override the system’s normal processing flow, ensuring an immediate response to critical situations such as hardware failures or other emergencies. System disabling of these interrupts is impossible, guaranteeing the prompt execution of their associated handlers. NMIs play a vital role in maintaining system integrity and responding to urgent conditions, making them a crucial component in a computer system’s overall reliability and resilience.
TRAP Interrupt: TRAP is a non-maskable interrupt in the 8085 microprocessor. Programmers typically use it to handle exceptional conditions, such as hardware-generated signals that require immediate attention.
Significance in System Reliability
Non-maskable interrupts (NMIs) enhance system reliability by ensuring immediate attention to critical events. Here’s why NMIs are crucial for system reliability:
- Emergency Handling: Critical system events, such as hardware failures or other urgent conditions, trigger NMIs. To ensure that these emergencies are promptly addressed without being delayed or overlooked, it is necessary to make NMIs more unmaskable.
- Fault Isolation: NMIs help in quickly identifying and isolating faults. When a critical event occurs, the system immediately invokes the NMI handler, enabling it to gather diagnostic information and take appropriate actions to prevent further damage or data loss.
- Preventing System Hangs: When a system might otherwise hang or become unresponsive, NMIs act as a fail-safe mechanism. They force the system to divert attention to the critical event, preventing prolonged freezes or crashes.
- Ensuring Data Integrity: NMIs are essential in environments where data integrity is paramount. By responding swiftly to critical events, NMIs contribute to maintaining the reliability and consistency of stored data.
- System Recovery: NMIs can be used to initiate recovery procedures after a critical event. This ensures the system can return to a stable and operational state as quickly as possible, minimizing downtime and improving overall system reliability.
Examples of Non-Maskable Interrupts
Typically, non-maskable interrupts (NMIs) are associated with critical and urgent events in a computer system. Here are some common examples:
1. Hardware Faults:
- Memory Parity Errors: When a memory module detects a parity error, it may generate an NMI to signal a potential hardware issue affecting data integrity.
- Machine Check Exceptions (MCE): Detecting unrecoverable hardware errors, such as CPU malfunctions or bus errors, can trigger NMIs.
2. Power Failures:
- Power Supply Issues: A sudden loss or fluctuation in power can lead to NMIs to ensure the system responds appropriately to the power-related event.
3. Watchdog Timer Expiration:
- Embedded Systems: In embedded systems, a watchdog timer might generate an NMI if it times out, indicating a potential system lock-up or failure.
4. System Health Monitoring:
- Temperature Sensors: Temperature sensors may generate NMIs if they detect critical overheating, helping prevent component damage.
- Fan Failures: Failure to cool fans may trigger NMIs to prevent the system from overheating.
5. Security Violations:
- Security Violations: In secure computing environments, NMIs can be used to respond to security breaches, triggering immediate actions to safeguard the system.
6. Machine-Specific Events:
- Initiated by External Hardware: External hardware generates NMIs, signaling events that demand immediate attention.
7. Real-Time Clock Alarms:
- Real-Time Systems: Alarms set in real-time clocks may result in NMIs, ensuring time-sensitive tasks are executed promptly.
8. Initiating System Recovery:
- Critical Software Failures: When essential software components fail, initiating recovery procedures through NMIs can prevent system instability.
Handling Non-Maskable Interrupts
Handling Non-Maskable Interrupts (NMIs) involves procedures to address critical events that demand immediate attention in a computer system. Here’s an overview of how NMIs are typically handled:
- Interrupt Vector Table (IVT): NMIs have a dedicated entry in the interrupt vector table, a data structure that maps interrupt numbers to their corresponding interrupt service routines (ISRs). The system uses this table to locate and execute the NMI handler quickly.
- Priority Mechanism: NMIs often have a higher priority than maskable interrupts. This ensures that when an NMI occurs, it takes precedence over other interrupt requests, allowing the system to respond promptly to critical situations.
- Exception Handling: Many treat NMIs as exceptions, causing them to trigger an exceptional condition in the system. The system then employs exception-handling mechanisms to transfer control to the NMI handler, which initiates the specific actions needed to address the critical event.
- Specialized NMI Handlers: Systems typically have specialized NMI handlers designed to deal with specific types of critical events, such as hardware failures or environmental emergencies. These handlers are responsible for diagnosing the issue, logging relevant information, and initiating appropriate corrective measures.
- Minimal Latency: One of the critical aspects of NMI handling is minimizing latency. Systems aim to reduce the time between the occurrence of the NMI and the execution of the associated handler to address the critical situation and swiftly prevent further complications.
- Non-Interruptibility: Unlike maskable interrupts, the system cannot turn off or mask NMIs, ensuring that it always acknowledges and handles them promptly, regardless of their state.
- Logging and Diagnostics: NMI handlers often include logging mechanisms to record information about the critical event. This data is valuable for post-event analysis, troubleshooting, and improving overall system reliability.
Key Difference: Maskable and Non-Maskable Interrupts
| Feature | Maskable Interrupts | Non-Maskable Interrupts (NMIs) |
| Disabling Capability | It can be disabled or masked temporarily. | It cannot be disabled or masked by the system. |
| Priority Level | Typically, they have lower priority. | Typically, they have higher priority. |
| Source of Interrupts | External events or internal signals. | Critical system events or hardware failures. |
| Handling Flexibility | Allows for controlled interruption handling. | Forces an immediate and unconditional response. |
| Interrupt Vector Table | Has dedicated entries in the IVT. | It also has dedicated entries, often at a higher priority. |
| Usage Examples | Keyboard input, software-generated interrupts. | Hardware failures, environmental emergencies. |
| Impact on System State | It can be postponed, allowing the system to continue its current tasks. | Demands an immediate response, potentially altering the system state. |
| Prevention of Masking | It may be intentionally masked to prioritize specific tasks. | It cannot be intentionally masked; it always takes precedence. |
| Typical Handling Time | May have slightly longer handling times due to flexibility. | Requires minimal latency for swift response. |
| Examples | External hardware interrupts, software-generated interrupts. | Hardware failures (e.g., power loss, system overheating). |
Choosing between Maskable and Non-Maskable interrupts
The choice between maskable interrupts and non-maskable interrupts in a system depends on the specific requirements and characteristics of the application. Here are considerations for when to choose between maskable and non-maskable interrupts:
Choose Maskable Interrupts When:
- Flexibility is Needed: A system can utilize maskable interrupts if it needs flexibility in controlling interrupt handling and prioritizing specific tasks over others. You can turn these interrupts on or off based on the system’s current state and needs.
- Less Critical Events: System designers often use maskable interrupts to handle events that are not critical to the immediate operation of the system. Examples include keyboard input, communication from peripheral devices, or other non-urgent events.
- Handling Time Variability is Acceptable: Maskable interrupts may have slightly longer handling times than non-maskable interrupts due to their flexibility. If the system can tolerate some variability in interrupt handling times, maskable interrupts may be appropriate.
- Software-Generated Events: When the software generates the interrupts and is not inherently critical to the system’s stability, maskable interrupts can provide a suitable mechanism.
Choose Non-Maskable Interrupts When:
- Critical and Urgent Events: Non-maskable interrupts are essential for handling vital and urgent events requiring immediate response. This includes hardware failures, power loss, or other situations requiring close attention to prevent further damage.
- System Stability is Paramount: If maintaining the stability and reliability of the system is the highest priority, non-maskable interrupts are crucial. They ensure the system cannot ignore or delay critical events, contributing to robustness.
- Predictable Handling Time is Required: Typically, minimizing latency is necessary when handling non-maskable interrupts. Using non-maskable interrupts is preferable if the system requires predictable and rapid responses to critical events.
- Prevention of Masking is Necessary: In situations where it is imperative that certain critical events cannot be intentionally masked or disabled by the system, non-maskable interrupts are essential.
Conclusion
Understanding the nuanced roles of maskable and non-maskable interrupts is fundamental in designing resilient and responsive computer systems. Maskable interrupts offer flexibility in interrupt handling, suitable for non-critical events, while non-maskable interrupts ensure immediate attention to vital, time-sensitive situations. Striking a balance between the two types contributes to system stability, reliability, and effective management of routine and emergency scenarios. A reasonable selection based on the system’s requirements is critical to optimizing interrupt handling, ultimately enhancing computing systems’ overall performance and dependability.
Recommended Articles
We hope this EDUCBA information on “Maskable and Non-Maskable Interrupts” benefits you. You can view EDUCBA’s recommended articles for more information,