Updated April 4, 2023

Difference Between Nmap vs Nessus
Nmap (Network Mapper) is defined as a network scanning tool that is used by network administrators to map their networks and discovers hosts and services by sending packets and analyzing the responses, also it is a free and open-source tool to check for inabilities or weaknesses of the network, Whereas, Nessus is defined as the remote security scanner tool which can be used to scan the computer and set up an alert if the system detects the state of being exposed to the possibility of being attacked or may hackers try to gain access to any computer which we have connected in a network.
Head to Head Comparison Between Nmap vs Nessus (Infographics)
Below are the top differences between Nmap vs Nessus.
Key Differences
Nmap and Nessus both are network scanning tools so there are quite differences in what they try to accomplish.
1. Security
Nessus is a vulnerability scanner, vulnerability means to scan the system weaknesses in computers and networks to identify security and improve the effectiveness of the system. Whereas, the network mapping is the first purpose of the Nmap which mapping discovers the hosts and services on the system. Mostly the network administrators and security professionals use Nmap to map their networks.
The Nmap determines the up and down status of the host also determines the unexpected presence of hosts, services in the network, firewall, operating system, and version on the host. The Nessus have security check plugins to determine the performance of the system network.
2. Vulnerability scanner
Scanning can keep our system secure. Finding vulnerability before hackers do anything is very important to keep our company data safe concerning network security. Vulnerability means identifying the weakness or inability of the system in the network. Vulnerability scanning detects inability and by using the Nessus tool we can detect the weaknesses of a system which will help to protect our system and improve the effectiveness of the system. Nessus provides a lot of functionality in one tool, the hackers can run the very same tool and it is advantageous to know what the result is that they scan the system. Nessus is one of the vulnerability scanners used to find malicious attacks.
Whereas, Nmap is not a full vulnerability scanner it is a reporting tool that is used to analyze the service response that is coming in packets and the reporting tool may help to identify vulnerabilities in the network. Nmap uses a scripting engine to identify the vulnerability information.
3. Installation on Windows
Before a Windows version was released the Nmap was a Unix-only tool and after release, it is the second most popular platform for Nmap. It is popular because Windows users do not have a compiler and also maintain a guide for users who wants to run Nmap on Windows. Nmap supports the Ethernet interface for raw packets scan. The scanning speed is slower than Unix because there are deficiencies in windows networking API. Windows has three choices for installing Nmap, which are available on the downloading page at https://nmap.org/download.html that are Windows self-installer, command-line zip binaries and, optional is a compiler.
Whereas, for Nessus we can obtain the windows installer and need to download it as per the operating system, once downloaded double-click on the installer and then finish installation, the welcome wizard for Nessus users gets opens.
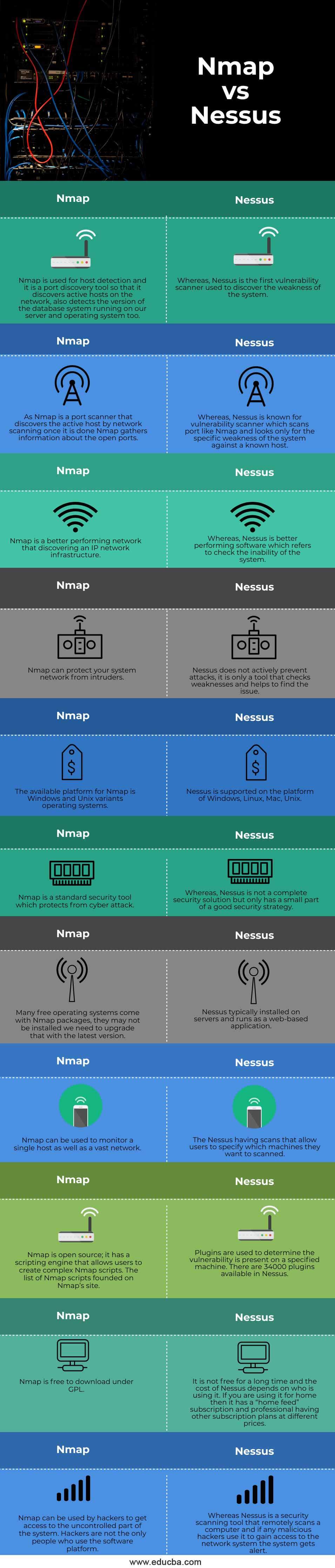
Comparison Table of Nmap vs Nessus
| S.NO | Nmap | Nessus |
| 1 | Nmap is used for host detection and it is a port discovery tool so that it discovers active hosts on the network, also detects the version of the database system running on our server and operating system too. | Whereas, Nessus is the first vulnerability scanner used to discover the weakness of the system. |
| 2 | As Nmap is a port scanner that discovers the active host by network scanning once it is done Nmap gathers information about the open ports. | Whereas, Nessus is known for a vulnerability scanner which scans ports like Nmap and looks only for the specific weakness of the system against a known host. |
| 3 | Nmap is a better performing network that discovering an IP network infrastructure. | Whereas, Nessus is better performing software which refers to check the inability of the system. |
| 4 | Nmap can protect your system network from intruders. | Nessus does not actively prevent attacks, it is only a tool that checks weaknesses and helps to find the issue. |
| 5 | The available platform for Nmap is Windows and Unix variants operating systems. | Nessus is supported on the platform of Windows, Linux, Mac, Unix. |
| 6 | Nmap is a standard security tool that protects from cyber attacks. | Whereas, Nessus is not a complete security solution but only has a small part of a good security strategy. |
| 7 | Many free operating systems come with Nmap packages, they may not be installed we need to upgrade that with the latest version. | Nessus is typically installed on servers and runs as a web-based application. |
| 8 | Nmap can be used to monitor a single host as well as a vast network. | The Nessus having scans that allow users to specify which machines they want to scanned. |
| 9 | Nmap is open-source; it has a scripting engine that allows users to create complex Nmap scripts. The list of Nmap scripts founded on Nmap’s site. | Plugins are used to determine the vulnerability is present on a specified machine. There are 34000 plugins available in Nessus. |
| 10 | Nmap is free to download under GPL. | It is not free for a long time and the cost of Nessus depends on who is using it. If you are using it for home then it has a “home feed” subscription and professional having other subscription plans at different prices. |
| 11 | Nmap can be used by hackers to get access to the uncontrolled part of the system. Hackers are not the only people who use the software platform. | Whereas Nessus is a security scanning tool that remotely scans a computer and if any malicious hackers use it to gain access to the network system the system gets alert. |
Conclusion
The above article concludes that both are used for examining network security, and their role in network security scanning is the best fit in our network security. We also conclude that Nmap and Nessus use their commands to check network and server inability before these tools administrators manually checked their networks.
Recommended Articles
This is a guide to Nmap vs Nessus. Here we discuss the Nmap vs Nessus key differences with infographics and comparison table. You may also have a look at the following articles to learn more –