Updated March 13, 2023

Introduction to NSG Azure
The following article provides an outline for NSG Azure. In Azure, a network security group is designed to activate the access control list or rule that enables or disables the traffic in the network to the instances of the virtual machine. These network security groups can be linked with subnets of the instances of a virtual machine or any subnets available within the network. A network security group is called NSG, which is an important component in Azure’s security. It can filter the traffic from both incoming and outgoing directions from the Azure resources, which are associated with the virtual network of Azure.
What is Azure NSG?
- In simple, NSG is a finite package of access control rules which is allotted to the network security group of Azure which is associated with the virtual network of Azure.
- It reviews the outbound and inbound traffic and implies the rules to decide if it should enable disable access to a concerned network packet.
- At a maximum level, the Azure group of NSG rules the network into outbound and inbound. The configuration and management of the rules are the same for the people who work on the standard firewall.
- With the help of Azure portal, Azure CLI, Azure PowerShell, the user can manage the NSG of Azure and specify the ports, destination, and source IP, and protocol.
Azure NSG Control Access and Communication
- The NSG of Azure has control access and can manage the communication between the discrete work load hosted on one or multiple virtual networks of Azure.
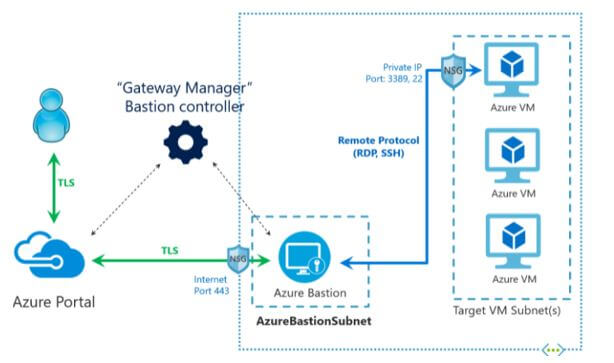
- The association between on-premise environment and Azure through a VPN gateway, application gateway, azure firewall, appliances of the virtual network, and Azure bastion services.
- It also manages the association in and out from the internet.
Azure NSG Rule Setting and Properties
A traditional subscription of Azure can have network security groups till 5000, and the user can define a maximum of 1000 rules in it.
The rules configuration and its properties are given below:
- Name: It gives the rules name, and this configuration is a free text field that should be unique within the network security group.
- Priority: The priority needs to be defined from 100 to 4096. The NSG in Azure has its rules according to the priority arranged from the minimum numbers, and they are the ones processed before the maximum ones. It is mandatory to note that the NSG in Azure will stop working in a network packet when it catches the matching rule. Therefore, it should have another rule with similar attributes arranged from the minimum value in the priority list where the NSG will not work on it.
Source or destination defines the destination or source of the traffic in the network. It can be predefined to any values from traffic anywhere and can lock it to single IP, which needs to be given in the notation of CIDR. The protocol defines the rule of the user network protocol. It can define it to look for any protocol or give any one of ESP, AH, ICMP, UDP, or TCP. Direction provides the navigation of the network traffic. It can configure it to neither outbound nor inbound Port range explains the rule of the port where the user can specify a value of the single like 90, 80, etc. or also define a range of ports like 200-300, 678-750 Action configures the action of the rule which it wants to be executed. The user can set it to either enable or disable.
Azure NSG Rule Priorities
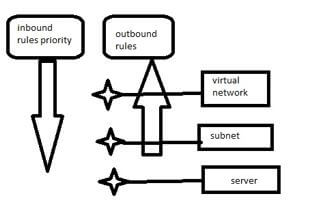
The network security group of Azure executes the rules according to the priority from the minimum number priorities, which should be worked before the maximum numbers. The user can also enable the nested network security group for resources. There should be a virtual machine hosted on a web server that has a subnet connection. The subnet develops as a section of the wide virtual network. The admin of Azure configured a triple network security group that is linked to one virtual network, virtual machine network card, and subnet.
As there is an active network group in azure, the rules configuration for the virtual machine needs the proper configuration on all the three active network security groups. For example, if the user wants to enable port 80 from the internet, which is the default HTTP port, he should develop an inbound rule on all three active network security groups. At first, the inbound traffic transverses the virtual network, then passes to the subnet and reaches the virtual machine’s network card. So every network security group requires an allow rule. It is mandatory as the NSG possess an inbuilt Denyallinbound rule.
When it comes to outbound traffic, the network security groups follow the rules in reverse. Here there is Denyalloutbound rule is enabled. So when configuring the rules to the network, the proper ruleset should be given to avoid Internet-bound traffic flowing away from the network.
Azure NSG Flow Log Use Cases
The flow case of Azure can be structured as follows:
- It is applied in network monitoring to find suspicious or unknown network traffic.
- It also monitors the traffic level and bandwidth consumption. It manages the IP filtering and port to the base of the application behavior.
- It distributes the log information for reporting and performs a live monitoring dashboard. In addition, it is used to find the top talkers and leverage the Geo-IP.
- As a part of compliance, it works to use the data flow to forecast the capacity and find the unoptimized traffic rules. It ensures the traffic rules which follow the compliance rules, obligations, and network isolations.
Conclusion
The network security flow log provides insight into the user’s need to monitor the environment for compliance, performance, and security purpose. By computing the information on the current state of the virtual network, it offers all the info like what services have a connection and the connections which have incoming part and ensure where the ports are enabled on the internet.
Recommended Articles
This is a guide to NSG Azure. Here we discuss the introduction, azure NSG control access & communication, setting & properties, rule priorities. You may also have a look at the following articles to learn more –