Difference between Phishing vs Spoofing
What is Spoofing?
Spoofing is a type of cyberattack in which an untrusted or unknown form of communication is impersonated as a legitimate one. Spoofing’s overall purpose is to get consumers to reveal personal details. Spoofing is a type of computer virus attack in which someone takes the information of a valid user and impersonates them. It’s a form of identity fraud. This technique is commonly used to compromise the security of large systems or steal critical information from users.
What is Phishing?
Phishing is a method used by cybercriminals to get personal details like login information, bank details by sending an email that appears to be from a trusted source but is meant to deceive you into clicking on a malicious link or downloading a potentially dangerous attachment. This type of social engineering tries to get you to reveal personal data.
To make a phishing attempt look more legitimate, a cybercriminal could use spoofing. To make it more legitimate, an attacker can impersonate an email domain or phone number. The more realistic the method of communication, the more likely the victim may fall victim to these tricks. Victims can reduce the risk of falling for such attacks by using a malicious link checker to verify the safety of any suspicious URLs before clicking on them.
Head to Head Comparison Between Phishing vs Spoofing (Infographics)
Below are the top differences between Phishing and Spoofing.
Key Differences between Spoofing And Phishing
Phishing and spoofing are frequently interchanged in the field of cybercrime. Company owners and system administrators, on the other hand, must understand the distinction between phishing and spoofing. Though it’s common to dismiss emails that appear to be phished or faked because they’re classified as spam, it’s still important to know the difference. Before we look at the differences between Phishing and Spoofing attacks, let’s look at the definitions of both.
Types of Phishing
- Phone Phishing – This is performed over the phone.
- Email Phishing – the attacker attacks online via email.
- Spear Phishing – This is a more advanced phishing attack in which a malicious email is targeted to a specific person.
- Clone Phishing – is a whaling attack intended at a company’s top executives.
- Angler Phishing – This is performed through the use of social media. It is done for malicious intent to steal data posted on social media, and people are tricked into disclosing personal details.’
- Smishing and Vishing – Telephones are used to communicate in this attack. Smishing includes sending text messages, whereas vishing includes communicating over the phone.
Types of Spoofing
- Email Spoofing – stealing the email’s “from address” to make the message feel legitimate.
- website spoofing –When attackers take over an existing website and change the address or create new websites.
- IP spoofing – It occurs when someone steals or hides their IP address in order to hide their true identity.
- Caller ID Spoofing – It has to do with a phone number. These numbers appear to be legitimate, and when the receiver answers the phone, he is prompted to disclose personal information.
- DNS Server Spoofing – It occurs hackers send traffic to a malware-infected IP address.
The following are the key differences between spoofing and phishing.
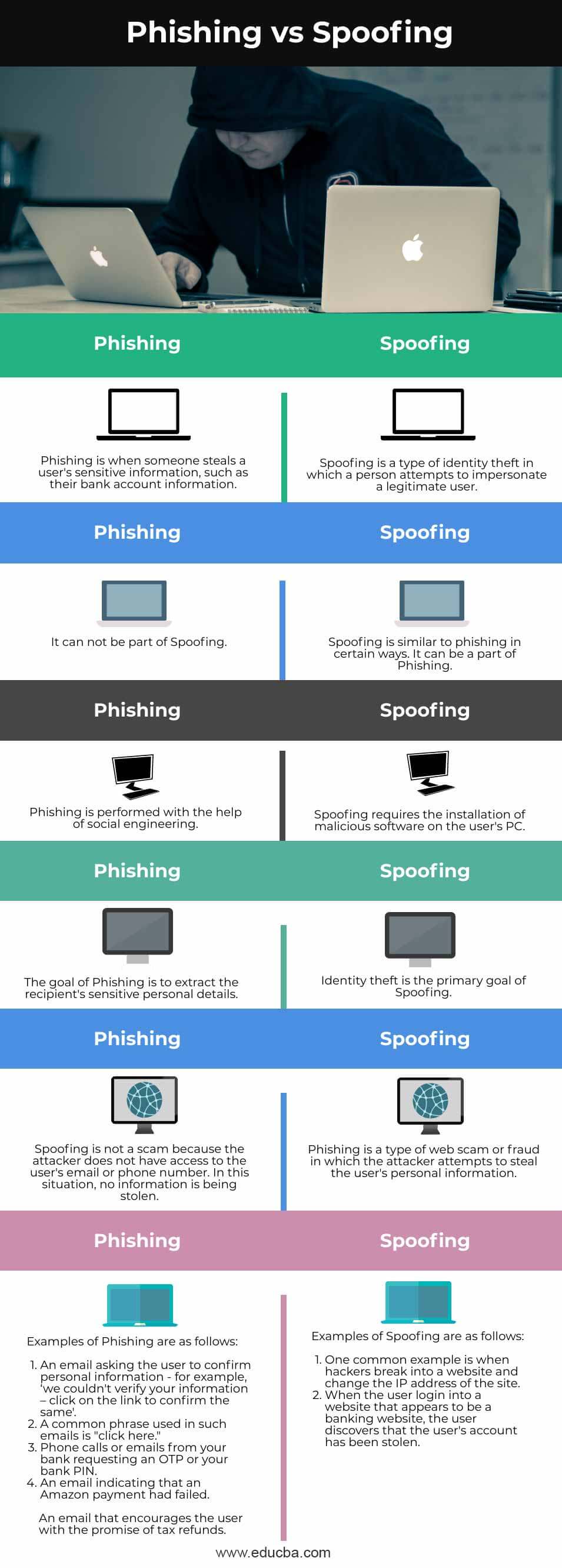
- Spoofing is a type of identity theft in which a person attempts to impersonate a legitimate user. Whereas Phishing is when someone steals a user’s sensitive information, such as their bank account information.
- Spoofing is similar to phishing in certain ways. It can be a part of Phishing. In the context of Phishing, it can not be part of Spoofing.
- Spoofing requires the installation of malicious software on the user’s PC. On the other hand, Phishing is performed with the help of social engineering.
- The goal of Phishing is to extract the recipient’s sensitive personal details. Whereas Identity theft is the primary goal of Spoofing.
- Phishing is a type of web scam or fraud in which the attacker attempts to steal the user’s personal information. On the other hand, Spoofing is not a scam because the attacker does not have access to the user’s email or phone number. In this situation, no information is being stolen.
Comparison Table of Spoofing and Phishing
| Sr. No. | Phishing | Spoofing |
| 1 | Phishing is when someone steals a user’s sensitive information, such as their bank account information. | Spoofing is a type of identity theft in which a person attempts to impersonate a legitimate user. |
| 2 | It can not be part of Spoofing. | Spoofing is similar to phishing in certain ways. It can be a part of Phishing. |
| 3 | Phishing is performed with the help of social engineering. | Spoofing requires the installation of malicious software on the user’s PC. |
| 4 | The goal of Phishing is to extract the recipient’s sensitive personal details. | Identity theft is the primary goal of Spoofing.
|
| 5 | Spoofing is not a scam because the attacker does not have access to the user’s email or phone number. In this situation, no information is being stolen. | Phishing is a type of web scam or fraud in which the attacker attempts to steal the user’s personal information. |
| 6 | Examples of Phishing are as follows:
An email that encourages the user with the promise of tax refunds. |
Examples of Spoofing are as follows:
|
Conclusion
In this article, we have seen key differences between spoofing and phishing. We hope you will find this article helpful.
Recommended Articles
This is a guide to Phishing vs Spoofing. Here we discuss the Phishing vs Spoofing key differences with infographics and comparison table. You may also have a look at the following articles to learn more –