Updated April 5, 2023

Introduction to Port Forwarding
Port forwarding can be defined as a method or technique of networking using which we can redirect web traffic from the world outside to our local IP or server. It translates the network address that usually redirects a communicational request from a combination of one IP address and port to another IP address and port with the help of a traverse gateway being created at the time of communication. This method allows the external connection to connect to the internal source node. It is often known as tunneling, port mapping, or punch through as well. Usually, there are two types of ports inside the firewall; namely, Open and Close. These two ports decide which sort of web traffic to take in and send out.
Why we Need Port Forwarding?
The first question that might come to our mind would probably be why? Why do we need port forwarding at all? Let us just imagine a situation where you are accessing Facebook, and all you could see are those unwanted people whom you don’t even want to meet at all. Didn’t a thought cross your mind that it would be good if I could have a technique using which I could block those unwanted people and their content? The same way it is with the internet network.
- The port forwarding protects your privacy (IP addresses when it comes to the internet). It protects the clients’ data to be exposed to some unwanted stuff.
- Port forwarding hides those unwanted servers and services available on those networks, and the user will be able to experience the limited accesses without any disturbance apart from the granted IP addresses.
- Port forwarding adds an extra layer of security to the user networks and IP.
- For all external communications, it allows one IP address to be used by the network admin. For internal communications, it allows multiple servers and multiple servers and different IPs.
We, in short, could say that port forwarding allows us to keep away the unwanted traffic through our networks and, at the same time, allows us to use multiple connecting options to hover internally. The administrator could set up a single IP address based on which all the internal traffic could be managed, and at the same time, all unwanted servers are blocked. This way, the admin can hide his work on the internal server from the world outside.
Working of Port Forwarding
- Suppose you are working with your pc. I have requested some information from google weblink with standard port 80. In this case, your computer’s IP (Ex. 01.0.0.1) is trying to access the information from google’s IP (say 01.0.0.8) through port 80 (standard port). Meanwhile, an intermediary IP (say 01.0.0.4) takes your request and forwards it to 01.0.0.8. Which forwards it to 01.0.0.4, and from there on, it comes to your system.
- In this case, even though you are trying to connect to 01.0.0.8 through port 80, that IP actually doesn’t know that you have requested the information (since there is an intermediary IP to forward the request). And this working in reverse mode as well. The information shared by 01.0.0.8 (through port 80) will be shared with you by an intermediary IP 01.0.0.4, and you never get an identity exposed of google’s IP.
- Therefore, your identity is safe and never gets exposed to the other IP and vice-a-versa. This is why port forwarding makes the internet user’s life easier to browse for the data with your identity being safe.
Steps to Perform Port Forwarding
Given below are the steps to perform port forwarding:
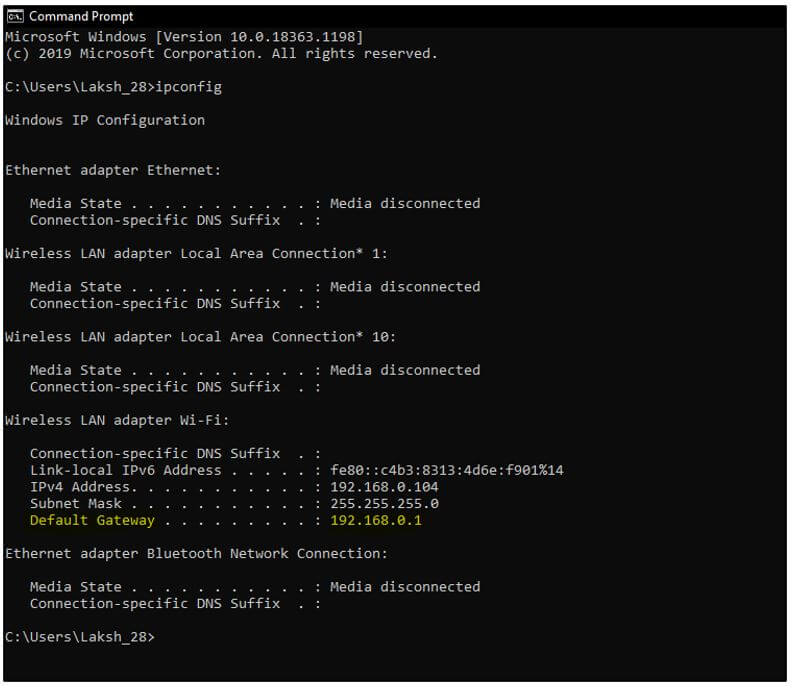
Step 1: First thing first, you need to know your default gateway, which you can get by going to the command prompt and hitting ipconfig as a command there.
Step 2: Once you know the Default Gateway, use it to log in through your router.
Step 3: On the router’s login page, put out the default administrative login credentials to get logged into the router. For most of the routers, the login id will be “admin”, and the password would be “password” itself (Most of the routers are either D-Link or TP-Link nowadays. These credentials are based on those). Some of the routers will have login credentials as “administration”, and the password will be the same as well.
Step 4: You have to navigate towards the port forwarding settings. This usually sits under the Advanced setting option, and within it, you will have the Port Forwarding option. If not, sometimes it will be there under the Virtual Server option.
Step 5: Once you navigated towards the Port Forwarding setting page, follow the below procedure:
- Enter the name of the server or a game or device for which you want to set the port forwarding rule. Ex. “Netflix”, “Minecraft”, etc.
- In the port field, set up the port you are trying to forward.
- You will also need the “TCP/UDP” protocol to set for the port forwarding. You can select both as well (In case you are not so sure which one to go with). Or can select any one of them.
- Input the IP address (internal IP address) of the device which you want to port forward. Then click the Apply button to apply the settings and finally hit the Save button to save all the changes you’ve made.
This is it; following these steps, you should be able to do port forwarding in our system.
Advantages and Disadvantages of Port Forwarding
Given below are the advantages and disadvantages of port forwarding:
Advantages:
- The core advantage of port forwarding lies in the fact that it allows you to secure public IP addresses.
- Port forwarding allows you to create multiple forwarding rules for the same user.
- Creates a private network gateway environment for the user, and he doesn’t even need a password for that.
Disadvantages:
- For each device and each resource, you need to create a separate rule. No single rule applied for all resources kind of facility available.
- If the port is open, hackers can easily identify such and hack your internal system.
- Additional site visits may be required at the time of changing the original rule or creating a new rule.
Conclusion
Port forwarding is a way using which we can preserve the identity of the user on the internet, and at the same time, we still can request or access the data from different web sources without even exposing your IP address to them. Almost every admin usually uses this method in order to prevent the threat of their IP being exposed to the outer world.
Recommended Articles
This is a guide to Port Forwarding. Here we discuss the introduction; why we need port forwarding? Working, steps, advantages and disadvantages. You may also have a look at the following articles to learn more –