Updated May 24, 2023

Introduction to PostgreSQL Encryption
PostgreSQL provides encryption at different levels and gives flexibility in protecting records and data from different attacks such as database server theft, illegal administrator and insecure network, etc. Encryption is required to secure sensitive data, such as banking and financial databases. Encryption means we encode teat or data from one form to another with a decryption key. The decryption key is private and large, so only you can understand. When we encrypt data, that means we convert a plain text to ciphertext, this encryption you can only understand with the help of decryption keys. PostgreSQL has the option to provide password storage encryption to secure databases; it also provides encryption for specific columns from tables.
Syntax:
create extension statement with pgcrypto;Explanation:
- We use the create extension statement with the pgcrypto command in the above syntax.
How is Encryption Carried Out in PostgreSQL?
Different organizations deal with different types of data, such as financial transactions or we can consider medical records; this is very secure information we need to store in the database. So security is the main thing for ensuring the security of data.
PostgreSQL has a different encryption option as follows:
1. Encryption of Data at Rest
Data at rest means we store unuseful data on disk. When we host a database in a cloud environment, we give all access permission to the user, so at that time, we required encryption to protect data on disk from theft.
2. Full Disk Encryption
The basic concept in Full Disk Encryption means protecting all files and temporary storage containing data. Sometimes it isn’t easy to protect a particular file or temporary storage because selecting a file or data is not easy, so PostgreSQL provides a Full Disk Encryption method. The main advantage of this method is that no special attention is required.
3. File-Based Encryption
File-based encryption encrypts files and directories using a stackable cryptographic file system. PostgreSQL encrypted files and directories by using pg_crypto. In this approach, we use the public key cryptography method. The main disadvantage of this approach is that it leaves some files encrypted, and those file attackers easily recover.
4. Instance Level Encryption
In this approach, the buffer concept is used, in which all files are stored in the disk as data at rest encrypted. Each writes operation from the shard buffer, and the data in the disk is automatically encrypted. In this approach, we use two different commands to encrypt the data: the initdb command to initialize the database and pgcrypto. keysetup _parameter command is used to fetch the encrypted key from the server.
5. Client-Side Encryption
Sometimes, the database administrator cannot trust a client then; the database administrator uses the client-side encryption method to encrypt data from a client. After applying the client-side encryption method, the unencrypted data is not shown on the server.
6. Encrypting Data Across A Network
In this approach, the SSL connection encrypts all data before sending it to the network. The database administrator specifies the host and requires an SSL connection, so it uses different configuration files for that purpose.
Example of PostgreSQL Encryption
Given below is the example of PostgreSQL Encryption:
Code:
create extension pgcrypto;Explanation:
- In the above example, we use the create extension statement with pgcrypto command.
- The pgcrypto command is used to keep the encryption method.
- We illustrate the outline of the excess outcome of the above declaration by using the following snapshot.
Output:
After that, we encrypted the password using hashing and the blowfish technique; the hashing uses 4 or 8 rounds.
Code:
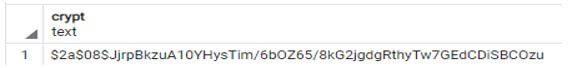
select crypt('admin', gen_salt('bf', 8));Explanation:
- In the above statement, we use a select statement with a crypt parameter to encrypt the admin password using hashing and blowfish technique.
- Here we use 8 rounds to encrypt the password.
- We illustrate the outline of the excess outcome of the above declaration by using the following snapshot.
Output:
We required a table for the further process, so we created a table using the following statement.
Code:
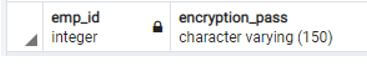
create table demo_sample(emp_id int, encryption_pass varchar (150));Explanation:
- With the help of the above statement, we created a demo_sample with different attributes, such as emp_id and encryption_pass, with the data type.
- We illustrate the outline of the excess outcome of the above declaration by using the following snapshot.
Output:
The above snapshot shows we successfully created a demo_sample table, and the below snapshot shows the actual created table as follows.
Output:
After that, we insert a record into demo_sample using the following statement.
Code:
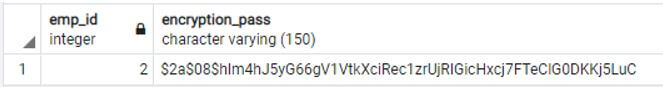
insert into demo_sample (emp_id,encryption_pass) values (1,'$2a$08$kBHePoCfMR7WGDocDKY04.9ZOgKwhkea8dDJzE1phufJRKJ7qoqAe');
insert into demo_sample (emp_id,encryption_pass) values (2,'$2a$08$hIm4hJ5yG66gV1VtkXciRec1zrUjRIGicHxcj7FTeClG0DKKj5LuC');Explanation:
- With the help of the above statement, we inserted a record into the demo_sample table with different values such as emp_id and encrypted password as shown above statement.
- We illustrate the outline of the excess outcome of the above declaration by using the following snapshot.
Output:
If we need to check if the password is correct or wrong, we can use the following statement as follows.
Code:
select * from demo_sample where emp_id = 2 and encryption_pass = crypt('admin', encryption_pass);Explanation:
- In the above statement, we use the select and where clause to check whether the password is correct or wrong; here, we check emp_id =2 and the encrypted password as shown above statement.
- We illustrate the outline of the excess outcome of the above declaration by using the following snapshot.
Output:
When we use the hacker command at that time, it does not return any single row from the encrypted password.
Let’s see how we can use hacker commands as follows.
Code:
select * from demo_sample where emp_id = 2 and encryption_pass = crypt('hacker', encryption_pass);Explanation:
- In the above statement, we change the word hacker instead the admin password, as shown in the above statement. After executing the above statement, it does not return any value of rows.
- We illustrate the outline of the excess outcome of the above declaration by using the following snapshot.
Output:
Conclusion
From the above article, we have seen the basic syntax of creating extensions in PostgreSQL and different commands related to encryption. We have also discovered how to enforce them in PostgreSQL with different examples of every technique. From this article, we have seen how we can handle encryption in PostgreSQL.
Recommended Articles
We hope that this EDUCBA information on “PostgreSQL Encryption” was beneficial to you. You can view EDUCBA’s recommended articles for more information.