Updated February 15, 2023
Introduction to Redis TLS
Redis TLS is supported in redis from version 6, we need to enable the TLS in redis at the time of compilation. We are using TLS type of authentication in redis. Managed redis instances provide the benefits of automated updates, high availability, and TLS. When connecting to a database server, we use TLS to send sensitive information from the server to the client across the network.
Key Takeaways
- At the time of configuring the redis TLS certificate, we need to configure the private key and the certificate of x.509. At the time of configuring the server, it is required to specify the CA certificate.
- The TLS-port configuration directive is used to enable the TLS connection in the specified port.
What is Redis TLS?
The Redis command line interface and redis cli do not support TLS connections. The cryptographic protocol is preventing secure communications from entering the network. As a result, we can conclude that redis-cli is not a secure method of connecting to a remotely hosted redis server. The tunnel will be used to establish a one-way connection for managed instances of redis and will use the TLS protocol.
We are using the tunnel, which is nothing but an open-source proxy used to create secure tunnels and allows us to communicate with other machines via TLS. We use TLS to communicate with our clients and our database. TLS is also used to communicate between our database and the redis replica cluster.
Redis TLS Certificate
Authenticated and encrypted communications are required in any application. It is a cryptographic protocol that combines all technologies’ encryption power. We require a TLS certificate. Before we can configure TLS in Redis, we need to obtain a certificate from a trusted certificate authority, also known as a CA. If our organizations already have a private key, certificate, and root certificate, we can skip the certificate configuration.
In order to request a certificate from our certificate authority using step, we must first bootstrap our certificate authority using CLI bootstrap and the step command. The following example shows how to bootstrap the certificate authority certificate using the step command. Sub is simply the server name for the actual DNS name of the redis server. When we run the following command, the server.crt and server.key files are generated in the default location from which we are running this command.
Command:
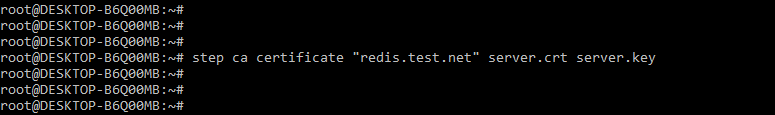
# step ca certificate "redis.test.net" server.crt server.keyOutput:
We can see in the above figure that we have stored the certificate on the server.crt file and the private key into the server.key file. We can request the root certificate of the certificate authority, which was used to ensure that each application trusts the certificates presented by the other applications. Our TLS certificate was basically saved in the ca.crt file.
Command:
# step ca root ca.crtOutput:
It is nothing but the cryptographic protocol of transfer layer security which ensures the secure delivery of data between applications and databases of redis. In it we are also generating the environment variables, to make sure that our application is pointing to the correct URL in the file of configuration.
Redis TLS Configuration
To configure the redis TLS we need to request the TLS certificate from a certificate authority. In the above example, we have already requested the same certificate, now in this step we are configuring the same in our redis database server as follows.
Command:
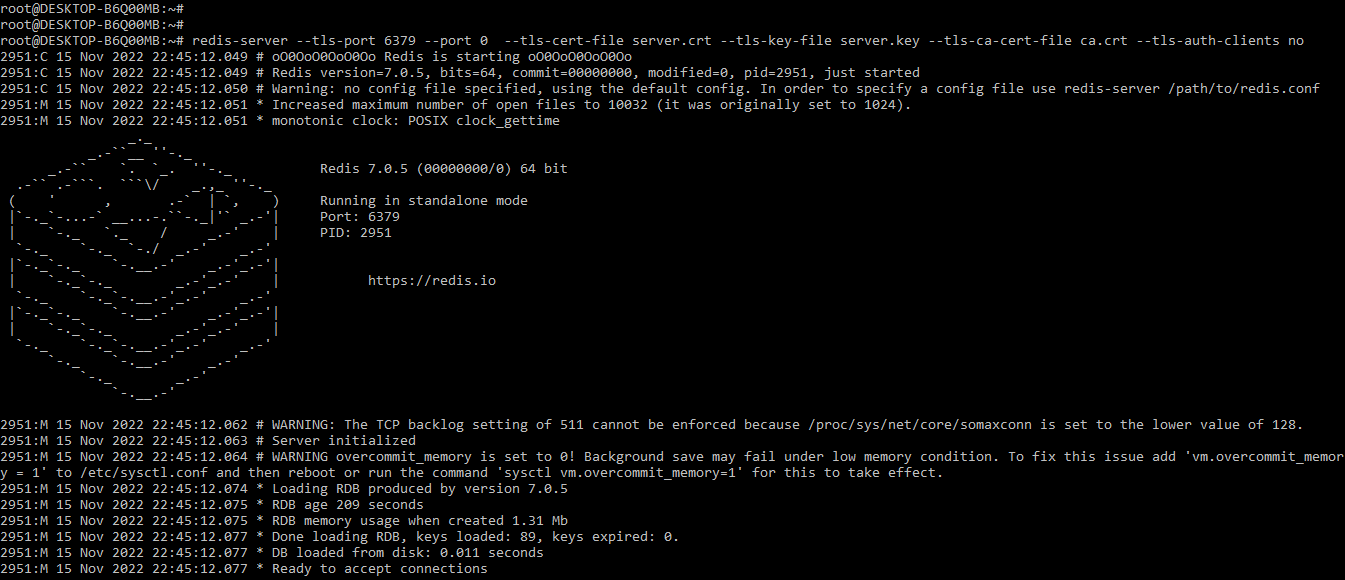
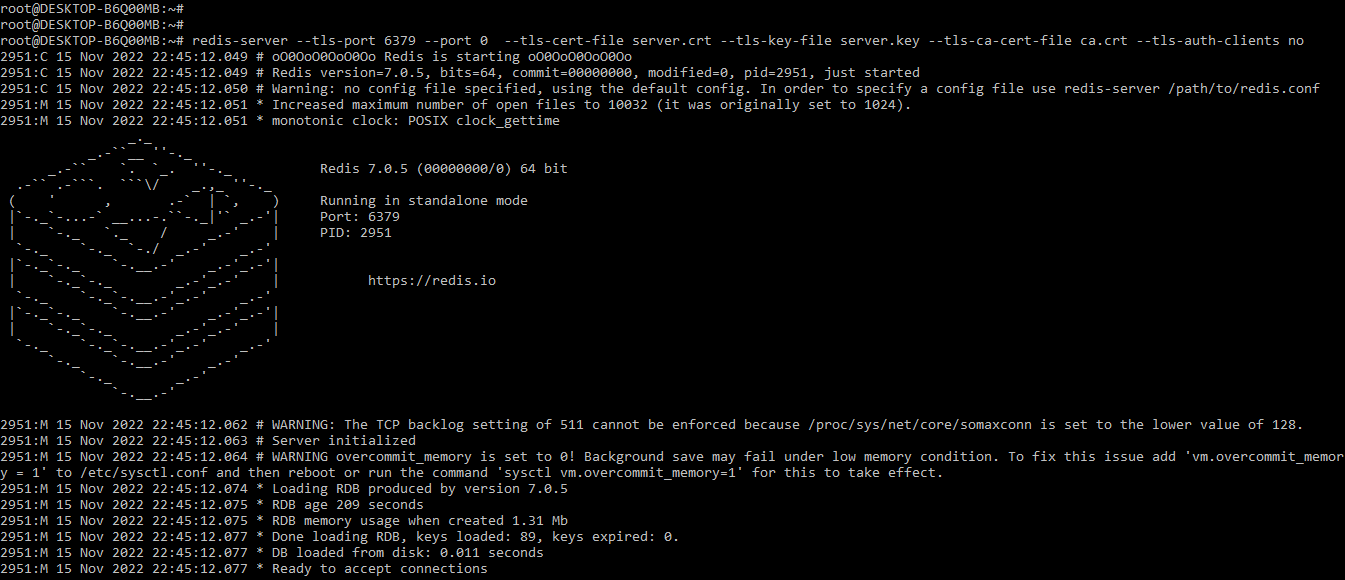
# redis-server --TLS-port 6379 --port 0 --TLS-cert-file server.crt --TLS-key-file server.key --TLS-ca-cert-file ca.crt --TLS-auth-clients noOutput:
In the above example, we have started the server by using 6379 which is the default port of the redis server. We are using port 0 for disabling the TCP socket of non-TLS. We are also using the TLS-auth-client parameter for disabling client authentication.
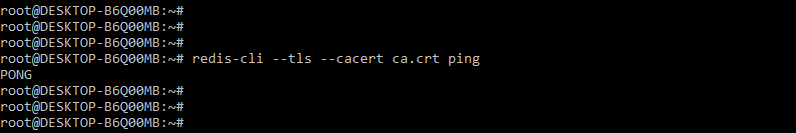
In the below example, we are testing the TLS configuration by using the redis-cli command. We are using ca.crt file for testing purposes as follows.
Command:
# redis-cli --TLS --cacert ca.crt pingOutput:
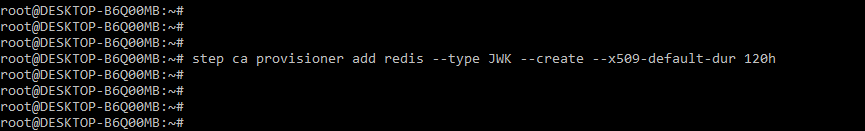
The provisioner is used by the CAS to authenticate certificate requests using one-time tokens and passwords. ACME is a non-standard authentication method that was used to validate certificate requests. We must use the ACME server in order to use the ACME. The provisioner is also used for the local agent network. We can use the appropriate provisioner, but it is dependent on the operational environment.
Command:
# step ca provisioner add redis --type JWK --create --x509-default-dur 120hOutput:
Configure the automation of TLS certificate of redis
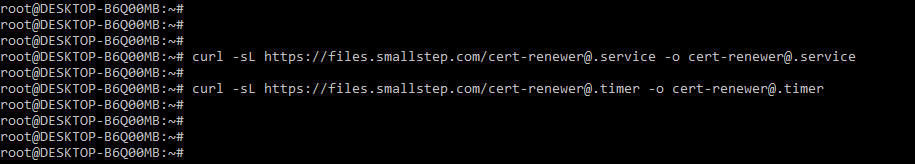
In the below example, we are creating the systemd based certificate for the renewal timer which was working with the step. For installing the file of the certificate renewal unit we need to run the following command as follows.
Command:
# curl -sL … -o cert-renewer@.service
# curl -sL … -o cert-renewer@.timerOutput:
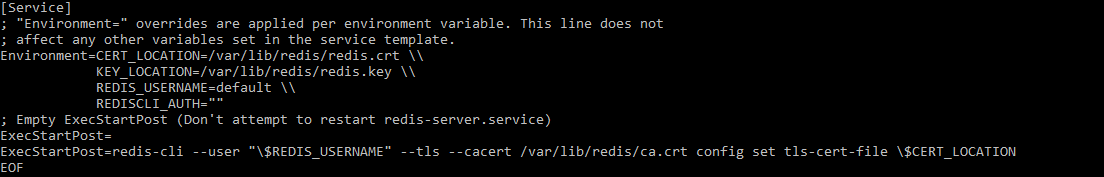
The renewal time is checking our certificate file in every five-minute intervals, we need to renew the same after two third of the elapsed time. For renewing the redis server certificate we need a systemd override.conf file as follows.
Command:
# vi override.confOutput:
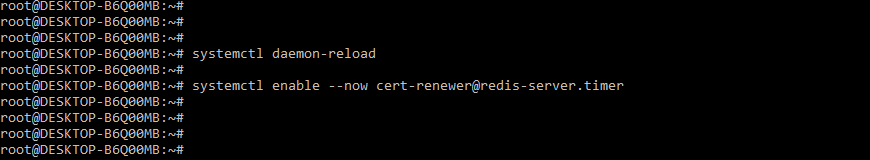
For starting the renewal timer, we need to run the systemctl daemon reload and enable the command as follows.
Command:
# systemctl daemon-reload
# systemctl enable --now cert-renewer@redis-server.timerOutput:
Distribute our root certificate to systems and users
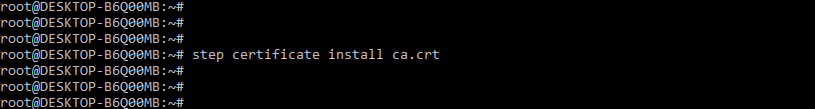
While configuring the TLS certificate we need to make sure that the certificate is signed by the CA. The trust CLI is including the below command to distribute the certificate.
Command:
# step certificate install ca.crtOutput:
We can also use automation rather than running the above command on all the machines. We are using multiple forms of automation.
Enable TLS
We are enabling the TLS in our system by running the following command as follows. We are enabling the TLS on the redis server at the time of starting the same. In the below example, we are using the port, certificate file, and key file for enabling the TLS as follows.
Command:
# redis-server --tls-port 6379 --port 0 --tls-cert-file server.crt --tls-key-file server.key --tls-ca-cert-file ca.crt --tls-auth-clients noOutput:
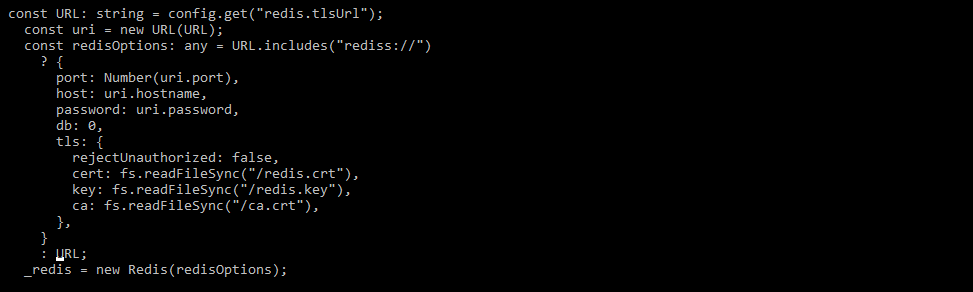
For enabling the tls, we also need to check the connection of the client. Below is the sample code of javascript for enabling the TLS as follows.
Conclusion
Redis command line interface and redis cli do not support connections over to the TLS. Cryptographic protocol is not allowing secure communications into the network. It is supported in redis from version 6, we need to enable the TLS in redis at the time of compilation. We are using TLS type of authentication in redis.
Recommended Articles
This is a guide to Redis TLS. Here we discuss the introduction, redis TLS certificate, configuration, and enable TLS respectively. You may also have a look at the following articles to learn more –