Introduction: Embracing the Cloud with Confidence
In today’s ever-accelerating digital world, businesses increasingly rely on cloud computing to streamline operations, enhance scalability, and drive innovation. However, as organizations transition their critical workloads to the cloud, they face a myriad of challenges, including security vulnerabilities, downtime risks, and data breaches. In the face of these challenges, resilience emerges as a crucial attribute for businesses seeking to thrive amidst uncertainty and disruption. But what exactly does resilience mean in the context of cloud computing, and how can organizations cultivate it effectively?
Table of Contents
- Embracing the Cloud with Confidence
- Understanding Resiliency in Cloud Computing
- Key Components of Cloud Resiliency
- Strategies for Building Resilient Cloud Systems
- Security Considerations for Resiliency in Cloud Computing
- Choosing a Cloud Provider with Strong Resiliency
- Benefits of Resiliency in Cloud Computing
- Best Practices for Ensuring Resiliency
- Case Studies – Resiliency in Cloud Computing
- Future Trends and Emerging Technologies
Key takeaways
- Resilient computing withstands and recovers from disruptions and ensures continuity in operations.
- Provide robust security to protect critical data and applications.
- Dynamically scale resources according to the changing demand and resource availability.
- Resilient cloud infrastructure strengthens security and ensures integrity, confidentiality, and availability of data and resources.
Understanding Resiliency in Cloud Computing
Resiliency in cloud computing refers to the system’s capacity to withstand and recover from disruptions, failures, or adverse events while maintaining essential functionality and performance. It encompasses various strategies and mechanisms implemented at different layers of the cloud infrastructure to ensure uninterrupted service delivery. This includes redundancy in hardware and software components, fault tolerance mechanisms to handle failures gracefully, automated monitoring and recovery processes to detect and mitigate real-time issues, and robust networking and security measures to safeguard against threats. Resiliency in the cloud is crucial for ensuring high availability, reliability, and continuity of operations, especially in dynamic and unpredictable environments where disruptions can occur due to factors like hardware failures, network issues, software bugs, or malicious attacks. By incorporating resiliency principles into cloud architecture and operations, organizations can minimize downtime, protect data integrity, and maintain service quality even under adverse conditions, thereby enhancing overall business continuity and user satisfaction.
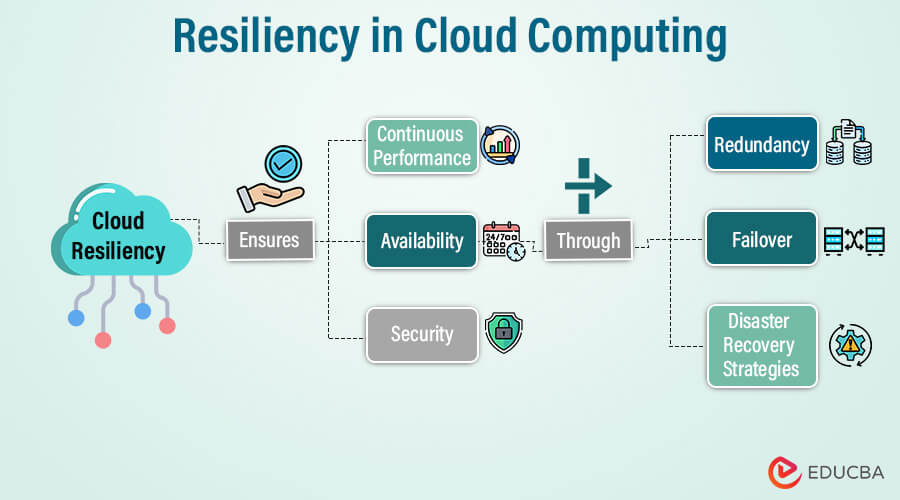
Key Components of Cloud Resiliency
Cloud resiliency works on several key components to ensure cloud services‘ availability, reliability, and recoverability. These components mitigate the impact of failure and disruption, ensuring business continuity.
- Redundancy:
In resilient computing, redundancy encompasses duplicating critical components such as storage, network connections, and storage. By distributing resources across multiple servers, redundancy minimizes the risk of a single point of failure and ensures continuity in operation if one fails.
- Fault Tolerance:
Disaster recovery encompasses the planning and preparing to respond to disruptions or disasters by employing recovery processes, replication, and robust backup to minimize data loss. IT teams should regularly test and update cloud-based disaster recovery plans to maintain effectiveness in a major disaster.
- Disaster Recovery:
Disaster recovery encompasses the planning and preparing to respond to disruptions or disasters by employing recovery processes, replication, and robust backup to minimize data loss. Regularly testing and updating disaster recovery plans for the cloud is essential to ensure their effectiveness during a significant disaster.
- Scalability:
Scalability defines the ability of a cloud system to smoothly handle the unexpected increase in traffic or workload demand without compromising performance. Resilient cloud computing relies upon scalable architecture to dynamically adjust resource allocation and deallocation on fluctuating demand. Cloud providers’ auto-scaling features automatically handle resource allocation based on performance metrics to maintain application responsiveness and availability under varying conditions.
- Security:
Resilient computing protects infrastructure, applications, and data from unauthorized access and attacks. Strict security protocols ensure the confidentiality, availability, and integrity of sensitive data in a cloud environment.
- Continuous Monitoring and Alerting:
Monitoring detects anomalies and vulnerabilities in real time by monitoring services, cloud resources, and performance metrics. Monitoring tools analyze collected data from different sources, such as events and metrics, to provide insight into the cloud environment.
The automated alerting prompts developers or administrators to critical issues or violence to allow them to respond on time and mitigate the risk. These alerts are triggered based on predefined criteria.
Strategies for Building Resilient Cloud Systems
Crafting a resilient cloud computing system involves considering three main strategies.
1) Testing and Monitoring:
This method incorporates an uninterrupted flow of testing and monitoring the cloud computing environment to ensure that it satisfies essential behavioral criteria. By executing independent testing processes, the system can identify flaws and errors early and adaptively reconfigure resources to sustain enhanced performance. This anticipatory strategy for system administration is vital for identifying, minimizing, and eliminating potential errors before they grow into big failures.
2) Checkpoints and restart:
In this approach, the condition of the entire cloud system is stored periodically at checkpoints. During system disruption, the system can be regained to the most recent checkpoint, ensuring Swift restoration and minimum data harm. This strategy assures that even during sudden system failure, the system can quickly return to normal functioning without significant disruption.
3) Replication:
Replication incorporates crafting redundant replicas of essential components within the cloud system. These copies are supplied to multiple hardware and software resources, ensuring they are present quickly in sudden system failures. However, the challenge with replication lies in synchronizing the state between replicas and the primary device to maintain consistency and coherence across the system. Despite this challenge, replication enhances resilience by providing redundancy and fault tolerance, reducing the risk of downtime and data loss.
By integrating these three strategies, the cloud system can optimize its resiliency and efficiently alleviate adverse effects of system failure, thereby confirming reliable and continuous service delivery to the users.
Security Considerations for Resilient Cloud Environments
- Strengthening Cybersecurity: Security with cloud technology involves utilizing cloud computing assets to optimize the safety measures of data and systems against cyber menace. When executed efficiently, cloud systems can provide multiple security advantages to users.
- Mitigating Threats: Firstly, cloud platforms can diminish the risk of Distributed Denial of Service (DDoS) intrusions by offering network resources and robust infrastructure that can endure massive intrusions targeted to disrupt services.
- Layered Protection: Cloud security measures often execute superfluous processes to protect data from unapproved, illegal, and unauthorized entry or leakage. This redundancy assures that even if one stage of security is compromised, there are multiple stages to safeguard confidential data.
- Assuring Compliance and Access Control: Cloud security solutions ensure users sustain adherence to compliance requirements and control access to advanced network features, optimizing the safety measures of personal information and financial assets.
- Responsive Support: Access to dependable customer service and IT support is vital for efficiently exploiting cloud security benefits. Punctual support from experts and professionals can assist users in swiftly considering security flaws and increase the advantages of cloud technology in protecting their assets, data, and systems.
Choosing a Cloud Provider with Strong Resiliency
Importance: Choosing a resilient cloud provider ensures uninterrupted administration and data safety. Find providers with redundant systems, geographically distributed data hubs, and a sturdy disaster management and recovery approach to minimize outage and data harm.
Essential parameters to Consider: Evaluate the provider’s past achievements in managing disruptions, compliance with security standards, and ensure performance. Analyze their risk-handling approach to diminish outage and cyber threats efficiently.
Customer Feedback: Measure the provider’s authenticity through industry standards, customer feedback, and case studies. Use trial scenarios and consultations optimally to assure compatibility with your organization’s requirements and future goals and objectives.
Benefits: Focusing resiliency in your cloud provider decision process protects your investment and assets, enhances operations, and imbues confidence in your digital system.
Benefits of Resiliency in Cloud Computing
| Sr. No | Parameter | Benefit |
| 1 | Decreased Downtime | Assures uninterrupted service access by minimizing user downtime and swiftly restoring flaws |
| 2 | Enhanced Adaptability | Since a resilient cloud computing environment can restore its flaws and scale up and down as required, it can be more adjustable to fluctuating workloads and requirements |
| 3 | Optimized Availability | Sustains system administration even at times of flaws, optimizing end-to-end system availability. |
| 4 | Enhanced reliability | Diminishes breakdowns and disturbances, resulting in increased user satisfaction and reliability. |
| 5 | Quick recovery | Restores rapidly from flaws and errors |
| 6 | Heightened security | Ensures and recovers from security vulnerabilities, reinforcing assets and data safety. |
| 7 | Cost saving | Alleviates costs regarding disruptions, incorporating lost revenue, repairs, and credibility impairment |
| 8 | Increased competitiveness | Increases customer attraction and enhances appeal to partners, nurturing a competitive edge in the business marketplace |
| 9 | Enhanced decision-making | It offers a firm foundation, which in turn increases the decision-making ability. |
Best Practices for Ensuring Resiliency
- Implement Redundant Systems and Fault Tolerance: Use robust systems and error tolerance approaches to sustain operational reliability during system failures.
- Implement Backup and Disaster Recovery Systems: The backup mechanism should be dynamic to preserve data and applications safely. Organizations should establish disaster recovery systems to ensure the safety and recoverability of data in the event of breakdowns or disasters.
- Apply continuous Monitoring and Alerting Tools: Deploy monitoring tools to identify performance and security flaws in real-time and install alerting approaches to inform teams of crucial issues for proactive outcomes.
- Implement Load Balancers: Use load balancers to evenly divide incoming traffic across different servers, preventing overburden and preserving system performance.
- Secure Cloud Environment: Reinforce security protocols with sturdy Authorization, encoding, and identity management. Timely audits and upgraded security measures are vital to detect vulnerabilities.
- Test Resiliency Regularly: Execute regular resilience assessment to authenticate backup, restore from disaster, and failover procedures. Test multiple failure scenarios, including application crashes and network outages, to assure readiness for disruptions and outages.
Case Studies: Resilient Cloud Implementations
Amazon Web Services (AWS)
Introduction:
A globally dispersed cloud computing system with sturdy infrastructure, AWS provides users with multiple services incorporating computing power, storage, and network capabilities.
Architecture:
AWS prioritizes resiliency characteristics by incorporating redundant data centers, multiple availability zones (AZs), and fault-tolerant designs. The dispersed geographical infrastructure ensures high availability, mitigating the adverse effects of failures.
AWS’s outage Resilience:
In February 2017, AWS experienced downtime in the US-East-1 sector, harming Trello, Quora, etc. However, due to AWS’s robust resiliency characteristics, many AWS clients functioned properly even during such an event. Organizations like Netflix and Airbnb, which depend on AWS, didn’t experience much of the effects of the outage, which shows that AWS has robust resiliency features.
Netflix:
Netflix depends heavily on AWS to provide its worldwide users with an uninterrupted streaming experience. With AWS’s design, Netflix goes undisturbed even during peak streaming hours due to AWS’s multi-AZ deployment and content caching. It didn’t experience much downtime during AWS’s 2017 outage issue.
Security and compliance:
AWS has gained many industry certifications by employing various security parameters. Its security measures incorporate an encryption process (IAM), identity and access management, and network failures to safeguard its assets and confidential information.
Conclusion:
AWS has set an example in the marketplace for efficiently incorporating resiliency in its architecture by adapting scalability, redundant design, and sturdy disaster-restoring capability. Events like the 2017 outage, where major customers like Netflix had minimal downtime effects, display AWS’s ability to sustain high availability. Businesses can leverage AWS’s resilience features to craft resilient applications, assuring continuity and dependability on the cloud.
Microsoft Azure
Introduction:
Microsoft Azure is an all-encompassing cloud computing system that provides multiple solutions like storage, networking, computing, etc. With a strong position in the global marketplace, Azure offers dependability, scalability, and safety for businesses of all segments and sizes.
Architecture:
Azure is crafted with resilience at its foundation, offering fault tolerance, disaster restoration, and robust redundancy. It has dispersed data centers, availability zones, and paired regions, assuring business continuity and availability.
Azure’s outage Resilience:
In September 2018, South Central US experienced Azure services go offline due to severe weather. The survey findings indicated that service disruptions occurred due to a cooling system failure, leading to system overheating. As a result of overheating, hardware damage also occurred in some areas. However, Azure has a powerful shutdown mechanism that can preserve data. After the incident, Azure software load balancers were installed to scale their storage capacity. Failed components of the data server were replaced with a better option. Azure also stated that “Impacted customers will receive a credit pursuant to the Microsoft Azure Service Level Agreement in their October billing statement.”
Conclusion
Azure has proved itself in the marketplace for efficiently incorporating resiliency in its architecture by adapting the best technologies, scalability, redundant design, and system failure restoring capability. Events like the 2018 system failure, where an immediate survey led to understanding and solving the problem efficiently, display Azure’s ability to sustain high recovery.
Future Trends and Emerging Technologies
1. AI-driven Resilience:
In resilient computing, integrating artificial intelligence and machine learning will allow the use of algorithms for decision-making and predictive analytics to manage cloud resources effectively.
- For example, One can use algorithms to analyze historical data to predict traffic patterns. Initially, collect a large amount of data, then employ machine learning algorithms to study the data and identify patterns. Train the algorithm using this data.
- Once the training is complete, the algorithm can predict future traffic patterns based on current and past information. Now, Cloud providers utilize these predictions to assign resources to meet the requirements automatically. If the algorithm predicts a sudden spike in traffic during rush hours, the cloud provider can dynamically assign extra server instances to sustain the load. Conversely, during periods of low rush hours, resources can be reduced.
2. Serverless Computing:
Implementing serverless architecture like AWS Lambda or Azure Functions will benefit cloud providers by helping them manage infrastructure, ensure high availability, and automatically scale resources on demand without any manual intervention.
- For instance, lambda dynamically provides resources if traffic density increases, assuring continuous service without manual disturbance. This smooth growth ensures high availability and enough resource assignment, optimizing user experience.
3. Hybrid and Multi-cloud Resilience:
Implementing hybrid and multi-cloud architecture reduces the burden on any single provider by distributing the workload across multiple providers and on-premises environments.
- For example, an application may use Microsoft Azure for computing, Amazon Web Service for storage, and an on-premises data center for specialized processing. This dispersed design mitigates dependency on a single provider, optimizing resiliency against potential failures or downtimes.
4. Immutable Infrastructure:
Immutable infrastructure treats cloud resources as disposable, meaning it views them as easily replaceable entities. Changes are made by deploying new and immutable instances instead of modifying existing ones. This minimizes the attack surface and configuration drift and ensures quick rollback if any failure occurs.
- For instance, instead of customizing the current instances, Unchangeable instances are deployed with the required settings. This strategy diminishes the chances of attacks and removes configuration drifts, assuring reliable performance and safety. A quick rollback to a known stable position is possible in case of a breakdown, diminishing potential outages, and downtimes.
Conclusion
Cloud computing resilience is vital in providing uninterrupted services and maintaining data integrity. With its robust strategies, it ensures continuity in businesses and mitigates potential risks from failure or disruptions. Resilient computing ensures optimal performance by implementing disaster recovery plans and proactive monitoring in a dynamic world.
Frequently Asked Questions (FAQs)
Q1) How does resiliency safeguard the cloud system from electromagnetic pulse (EMP) attacks?
Answer: Resiliency in cloud computing targets minimizes the dangers of EMP attacks by integrating physical and logical strategies.
Physical protection incorporates safeguarding critical frameworks and data centers from electromagnetic disturbances.
Logical protection: It incorporates an encryption process, data redundancy, and backup strategies for assuring data accuracy and availability.
Q2) How is serverless orchestration implemented in cloud resiliency?
Answer: Serverless orchestration automates the coordination and management of several microservices or functions in a cloud environment. It ensures that the workflow operates smoothly despite any failure or disruptions. It provides efficient resource utilization and quick recovery and improves fault tolerance by simplifying distributed systems management.
Q3) What are the implementation challenges of the distributed consensus algorithm for cloud resiliency?
Answer: The distributed consensus algorithm such as Paxos or Raft ensures agreement among multiple nodes. However, resilient or cloud computing challenges arise due to latency or partition, obstructing consensus and leading to a diverging state among nodes. Moreover, it also impacts performance and scalability as achieving consensus incurs overhead. Despite all the challenges, the distributed consensus algorithm plays a crucial role in maintaining resilience in cloud computing.
Recommended Articles
We hope that this EDUCBA information on “Resiliency in Cloud Computing” was beneficial to you. You can view EDUCBA’s recommended articles for more information.