Introduction to Security Architecture
Security architecture is defined as the architectural design that includes all the threats and potential risks that can be present in the environment or that particular scenario. This also includes the security controls and the use of security controls. For the security architecture, the proper documentation is done that includes all the security specifications and all detailed information about the architecture. The organization uses for its system, and it is mainly used because the architecture is affordable and cost-effective and can be used easily by the organization.
Security Architecture with Diagram
This is defined as the part of enterprise architecture that is particularly designed for addressing the information system and fulfilling the security requirements of the organization. The system architecture system has a role that meets the security requirements and also helps to protect the company’s operating environment. It is beneficial for the company as it includes other activities like risk management activities that require continuous improvement, and security architecture helps to meet the organization requirements. It defines proper policies, rules, and regulations that need to be reinforced in the organization and provides proper information about them. The architecture is also used for allocating the controls for technical security so that the information system of the organization can be maintained properly. Some companies offer managed IT security services in Houston by a team of seasoned professionals for this very reason. As the same can be followed in a whole organization, it helps to define common regulations and standards for every employee so that everyone can follow the rules and maintain data integrity and security in the organization.
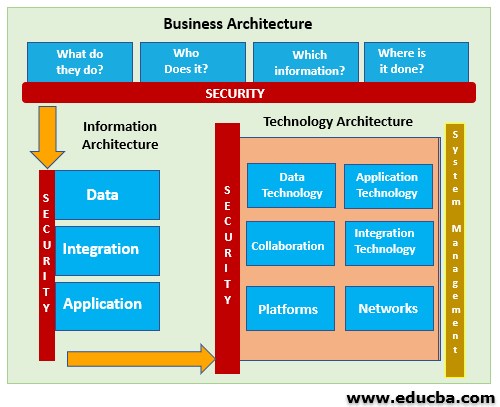
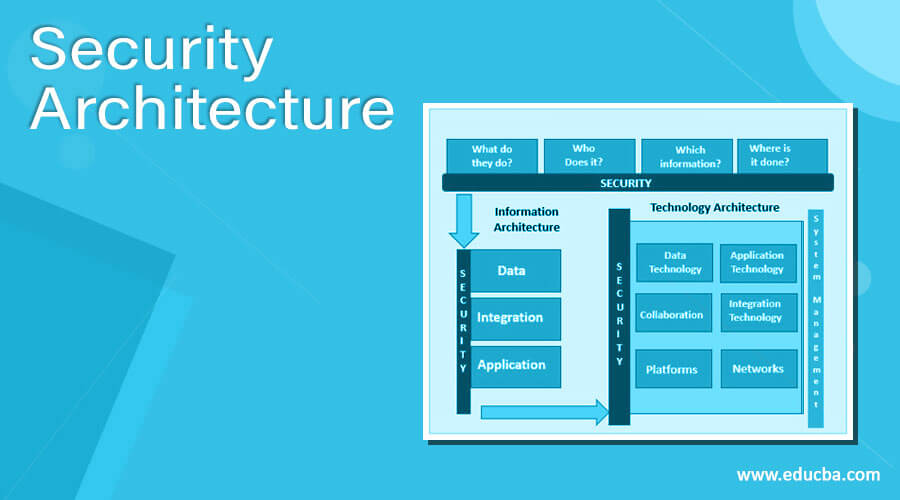
In the above diagram, the high-level design of the system architecture is shown. The abstraction is given here.
Components of Security Architecture
For making the security architecture important, there are certain components that are involved in the design. The components are people, process and the tools. All these components combined help to protect the organization’s assets. After defining the components, the next step is to make the policy and the reinforcement technique for the policies. After the other important steps are the method procedural for the implementation of security architecture and how the architecture will get enforced. By this, the overall design and architecture are designed for the organization that will protect them throughout their business operations. For a proper security architecture, some of the components are briefly discussed:
1. Guidance
The policies and procedures that act as the guidance should be design and implement properly. The policies should include the documentation that includes the objectives and goals for designing the architecture, standards, policies, rules and regulations for the organization, identification of scope and function, identification of other security policies.
2. Identity Management
It is the type of system that include the organization processes, technologies and policies that directly help users to gain access to the online applications and other network resources. For the organization, the proper responsibilities and roles need to be clearly stated, and individual tasks need to be designed for the employees.
3. Inclusion & Exclusion
The other components are the inclusion and exclusion that include the security of elements of the organization in which company resources are protected. The company resources include web resources, e-mail servers, private HR data and other reporting system information. The access should be grant to authorized users only so that the privacy and integrity can be maintained in the organization.
4. Access and Border Control
The organization should develop an architecture that is able to control the access to the business resources and can use the layer system for providing access to the company employees. Only authorized users should gain complete access to the system, and the rest should be provided with limited access of the system.
5. Validation of Architecture
As the technology advances, the company need to renew the policies and laws as per the changes, and continuous effort is needed by the organization in this change. For that, the continuous monitoring is required, and according to that, proper changes can be made in the architecture.
6. Training
As for the organization, to maintain the privacy and integrity, the security architecture system is very important. AS there is a continuous change in the system, it becomes important that the employee should know about the changes and proper training is given to them so that they can use the system and protect the company assets and elements.
7. Technology
To reinforce the security architecture, the software and hardware used for making the architecture become very crucial for the organization. Because of continuous change in technology, there is a requirement of continuous change in the system so that the system can be up to date and help to make the system secure and private.
Benefits of Using the Security Architecture
Some of the benefits are mentioned below.
- Help to protect the important company assets from the outside and provide security to the important resources to the organization. The architecture provides the limited access to the user so that the confidential data can be kept secure and safe.
- The architecture defines the common policies and standards that can be used by the every employee of the company and also define common rules so that no one face any difficulty to use the system. It helps the organization to reach their goal and easily conduct their business operations smoothly.
- The other benefit is risk management activities covered by the architecture as the risk management activity requires continuous assistance and also need continuous improvement, the security architecture act as a better solution for them.
Conclusion
Security architecture is a type of enterprise architecture and is very important for the organization to protect the company resources from the outside world. A strong security architecture is used by the organization to main security and data integrity in the system, and the policies and rules defined by the system are followed by the employee of an organization.
Recommended Articles
This is a guide to Security Architecture. Here we also discuss the Introduction and components of security architecture along with benefits. You may also have a look at the following articles to learn more –


