Updated July 11, 2023
Introduction to Security Policies
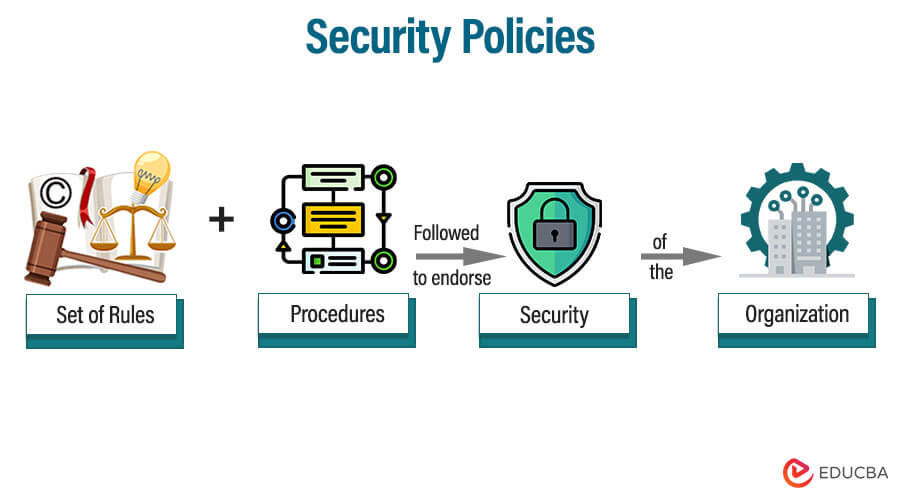
The following article provides an outline for Security Policies. Security policy can be defined as the set of rules and procedures which has been followed to endorse the security of the system or organization. It can be considered as the guidelines that have to be practiced throughout the organization to comply with the information security standards.
The policy varies from entity to entity, and for all of them, there are unique policies. The system not adhering to its policies is considered noncompliant and remains vulnerable to severe breaches. In contrast to that, all the organization practicing these policies has strong fundamentals to protect themselves from being attacked or data breaches in the future.
Top 6 Security Policies
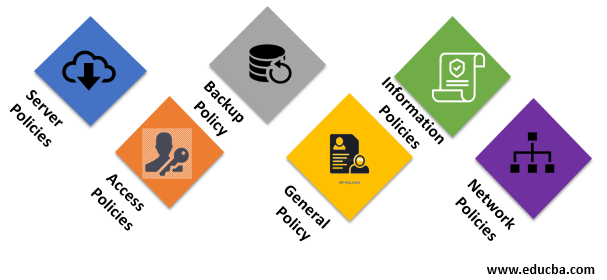
Given below are the top 6 Security Policies:
1. Server Policies
This policy is considered with the servers that are used in the organization for several purposes like storing data, hosting applications, DNS server, and so on. As per the policy, the server should be free from all the vulnerabilities, and the users should only have limited access as per their role and responsibility. The policy states that the server should be managed so that it does create a door for the attacker to breach the system. The OS running on the server should be updated and have all the recently released patches installed in it. The accessibility of the server is the other thing covered in this policy. It emphasizes the rights of users on the server.
2. Access Policies
As the name states, this policy is concerned with user access to any of the resources. The user not having access to any particular should not bypass the check at the entry point. In terms of server, there are some rights or roles assigned to the user, and this policy says that the user should not be able to perform any operation that is not covered under their permission. This policy also applies to the host as there is a user check before letting them connect to the local network. For the localhost, this policy states that the user with less access should not be login as admin or as any account with similar privilege.
3. Backup Policy
As per the backup policy, the backup of data should be created after a specific interval. The purpose of this policy is to ensure the availability of the data and also to support BCP (Business continuity plan). BCP refers to the plan that has to be followed to keep the business moving smoothly in situations like natural disasters, fire, etc. Even if the data in the existing location is destroyed for any reason, the backup will help regain it, ensuring the availability of data endorsing the A component from CIA components of ISMS(Information Security Management Systems).
4. General Policy
The general policies are comprised of the rules that are common for all the employees of any organization. For instance, having access to the common area, being able to mail on particular domains, and so on like. These rules apply to everyone who is part of the organization. This policy also covers the rules for the third-party vendor having access to the organization’s infrastructure. It brings all the stakeholders on one page in terms of adherence to the policy.
5. Information Security Policies
This policy may be defined as the set of procedures that ensure the security of the organizational data. It further contains various policies to ensure the security of the information.
- Clear Screen Policy: As per this policy, the desktop has to be kept clean, and no critical file should be kept there. The desktop should contain only the normal file that does not contain any sort of critical information.
- Clean Desk Policy: Everyone has to ensure that they are not leaving any critical file or data while leaving their desks. The usage of the pen, paper, mobile phones should be restricted on the desk so that there should be no way to get the data out of the system either by noting it or by clicking their pictures.
- Email Policy: The official ID should not be used for any personal use. One has to be very cautious before sending any mail to outside organizations. The emails one receives from external sources should be treated very sensitively, and any link given to that email should never be clicked on until the internal user trusts the sender.
- Password Policy: All the resources that require authentication check before letting the user in should comply with the string password policy. The user should not be allowed to create a weak password which later becomes a threat to the organization as poor passwords could be guessed easily.
- Information Sharing Policy: Any information should be shared among the folks who are supposed to access that data. For instance, any file related to a particular project should only be shared among the folk concerned with that project and not with any other party. Things like passwords should never be shared with anyone regardless of who is asking for them.
6. Network Policy
Network policy ensures the security of the network and helps the network to operate in an optimal state. The policy defines the accessibility of the network for different users and also defines the data protection rules that have to be deployed at the network level. Network is comprised of several nodes, and the policy covers the standards for all the nodes. The bandwidth of the Internet, the portion of the network like DMG or local network devices, should adhere to them’ policies. In a nutshell, it covers all the policies which are intended to cover the peers and resources in the network.
Conclusion
It is practiced worldwide to keep the system strong against attacks that could breach data, defame organizations, etc. Also, adherence to these policies makes the organization complain to the information security standards, which are considered mandatory to operate the business at a good or worldwide level.
Recommended Articles
This is a guide to Security Policies. Here we discuss the top 6 security policies like server policies, access policies, backup policies, general policies, etc. You can also go through our other suggested articles to learn more –