What is Security vs Compliance?
In the constantly changing world of information technology and data management, it is crucial to distinguish between security and compliance. Security pertains to safeguarding systems, data, and assets from potential threats, while compliance involves adhering to specific regulations, standards, and industry-specific requirements. While they share common goals of protecting data and mitigating risks, security focuses on proactive measures, while compliance involves meeting prescribed guidelines. Understanding these differences and their interplay is essential for organizations striving to maintain data integrity and legal adherence in an increasingly interconnected world.
Table of Contents
What is Security?
Security refers to the measures and practices to safeguard an organization’s data, assets, and systems from unauthorized access, breaches, damage, or theft. It includes various tactics and technological solutions to safeguard the availability, confidentiality, and integrity of data and resources, guaranteeing the smoothness and reliability of an organization’s activities. Security can involve physical security, network security, information security, and more, and it is a critical aspect of risk management in the digital age.
Key Objectives of Security
The key objectives of security are to protect an organization’s data, systems, and assets from unauthorized access, breaches, and threats. These objectives can be summarized as follows:
- Confidentiality: It is essential to ensure that confidential information is only accessed by authorized individuals or entities. This can help maintain the information’s security and privacy and prevent unauthorized access or disclosure.
- Integrity: Maintaining the accuracy and reliability of data and systems, preventing unauthorized alterations.
- Availability: Ensuring systems and data are consistently accessible and operational when needed.
- Authentication: Verifying the identity of users and entities accessing the organization’s resources.
- Authorization: Granting the right permissions and privileges to authorized users is crucial to ensure that only authorized personnel can access sensitive information. This helps to limit access to unauthorized individuals and maintain data security.
- Non-Repudiation: Ensuring that the parties involved cannot deny actions or transactions, providing accountability.
- Resilience: Preparing for and recovering from security incidents, minimizing downtime and data loss.
- Vigilance: Continuously monitoring for security threats and vulnerabilities and proactively addressing them.
- Compliance: Aligning security practices with relevant laws, regulations, and industry standards. Organizations aiming to achieve a robust blend of security and compliance can greatly benefit from integrated solutions that streamline processes effectively. For businesses in the security sector, leveraging specialized platforms is vital. Consider utilizing Managely’s management software for a security business designed to increase operational efficiency, control, and growth opportunities while addressing protective and regulatory needs.
- Risk Management: Identifying, assessing, and mitigating security risks to protect the organization’s interests.
Components of Security
Security involves different elements to safeguard an organization’s data, systems, and assets. These components can be summarized as follows:
- Access Control: Regulating who has permission to access specific resources and data and enforcing these permissions through user authentication and authorization mechanisms.
- Encryption: Data encryption safeguards information from unauthorized access by transforming it into an unreadable format, requiring a decryption key for deciphering.
- Incident Response: Creating and implementing plans for quickly identifying, handling, and recovering from security events and breaches is crucial.
- Authentication: Ensuring only authorized individuals access resources by verifying user and entity identity. Equally important is making sure your website meets ADA compliance and accessibility standards, ensuring that all users, regardless of their abilities, can access your site. By prioritizing both security and accessibility, you create a more inclusive and secure online environment for everyone.
- Firewalls and Intrusion Detection Systems (IDS): Implementing protective barriers (firewalls) and monitoring tools (IDS) to detect and block unauthorized network access and suspicious activities.
- Vulnerability Management: Identifying and addressing security weaknesses and vulnerabilities in systems and software to prevent exploitation by attackers.
- Physical Security: Physical security measures are critical to protecting physical assets such as servers and data centers. Utilizing automated commercial slide gate systems can enhance access control, ensuring that only authorized personnel gain entry to restricted areas. These systems serve as a first line of defense in numerous setups, granting advanced monitoring and response capabilities.
- Security Policies and Procedures: Establishing guidelines, rules, and best practices for security to ensure consistent and secure operations.
- Security Awareness Training: Educating employees and users about security risks and best practices to reduce human-related security vulnerabilities.
- Security Monitoring and Logging: Continuously monitoring systems for unusual activities and maintaining detailed logs for auditing and incident analysis.
What is Compliance?
Compliance refers to the adherence to specific laws, regulations, standards, and internal policies within an organization. It ensures the company’s operations, practices, and processes align with these established guidelines. Compliance measures are essential for meeting legal requirements, industry standards, and ethical obligations. Failure to comply may lead to legal and financial repercussions, harm one’s reputation, and erosion of trust. Therefore, organizations typically implement compliance programs to systematically monitor, enforce, and report on their adherence to the applicable rules and standards to maintain legal and ethical integrity.
Key Objectives of Compliance
The key objectives of compliance within an organization are as follows:
- Legal Adherence: Ensure the organization complies with all applicable laws, regulations, and industry-specific standards to avoid legal consequences.
- Ethical Conduct: Uphold ethical principles and standards in all business operations, fostering trust and integrity.
- Risk Mitigation: Identify and manage potential risks, reducing the likelihood of compliance violations and associated repercussions.
- Data Privacy: Safeguard sensitive data and protect the privacy of individuals in accordance with relevant data protection regulations.
- Transparent Reporting: Maintain accurate records and reporting to demonstrate compliance to stakeholders, authorities, and the public.
- Operational Efficiency: Streamline processes and practices to meet compliance requirements while minimizing disruption to business operations.
- Brand Reputation: Build and maintain a positive reputation by showing commitment to compliance, which enhances trust with customers and partners.
- Financial Stability: Prevent financial penalties and losses associated with non-compliance, helping to secure the organization’s financial stability.
- Internal Controls: Implement effective internal controls to prevent fraud, errors, and organizational mismanagement.
- Continuous Improvement: Foster a culture of ongoing improvement in compliance practices, adapting to evolving regulations and industry standards.
Components of Compliance
The components of compliance include elements that aid organizations in conforming to laws, regulations, standards, and policies. These components typically include:
- Regulatory Requirements: Compliance with industry-specific laws and regulations is crucial for organizations.
- Policies and Procedures: Establishing and communicating internal policies and procedures that align with external compliance requirements.
- Data Privacy: Safeguarding personal and sensitive data, often through data protection and privacy policies and practices.
- Reporting and Documentation: Maintaining accurate records and documentation of compliance activities and outcomes, including audit trails and reports.
- Auditing and Monitoring: Regularly assessing and monitoring compliance through internal and external audits and ongoing surveillance.
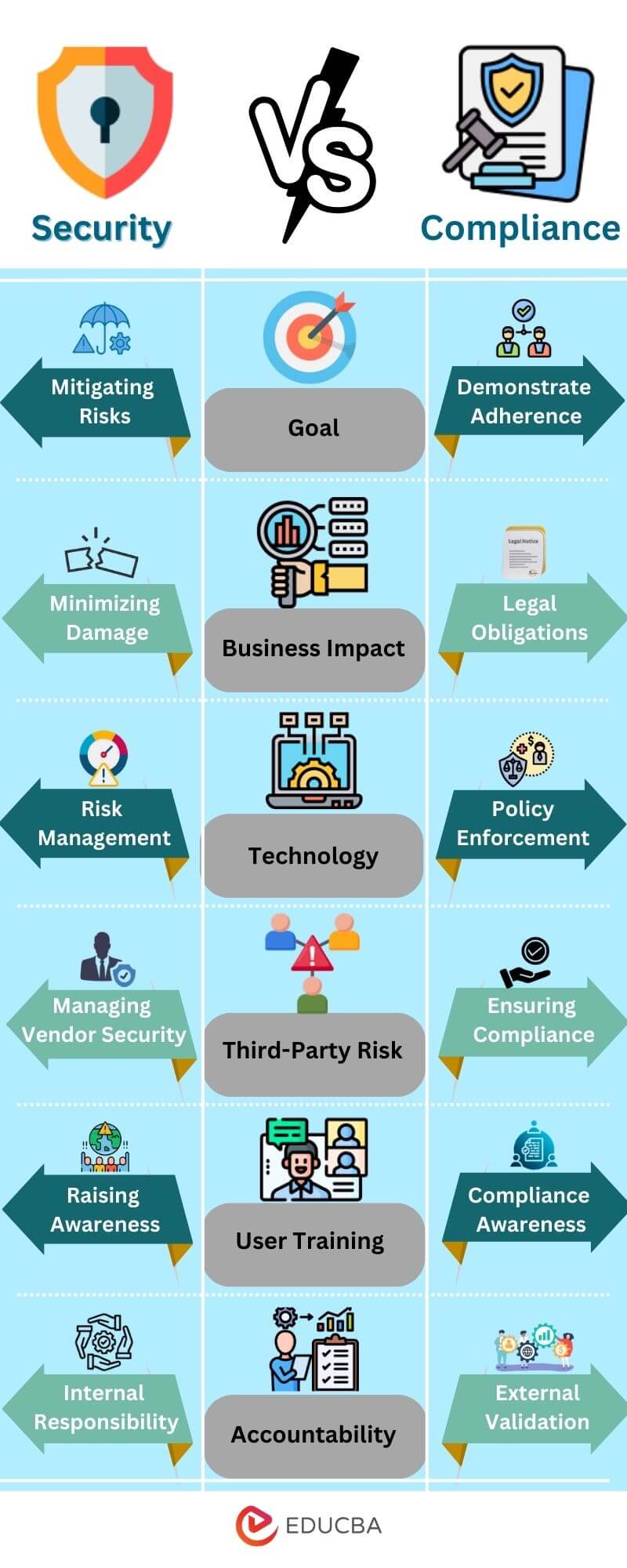
Security vs Compliance Infographics
Compliance Frameworks and Standards
Compliance frameworks and standards are established guidelines that organizations can adopt to ensure adherence to regulatory requirements, industry-specific rules, and best practices. They provide a structured approach to managing compliance.
- ISO 27001: A widely recognized international standard for information security management systems (ISMS) focusing on protecting sensitive information.
- HIPAA (Health Insurance Portability and Accountability Act): A U.S. healthcare compliance standard that governs the privacy and security of patient data.
- PCI DSS (Payment Card Industry Data Security Standard): A set of security standards for organizations handling credit card transactions and sensitive payment card data.
- GDPR (General Data Protection Regulation): A regulation by the European Union that mandates data protection and privacy for individuals, which applies to organizations that handle the personal data of EU residents.
- SOX (Sarbanes-Oxley Act): A U.S. federal law that establishes requirements for financial reporting and internal controls to protect investors from corporate fraud.
- NIST Cybersecurity Framework: Guidelines for managing and reducing cybersecurity risk are provided by the National Institute of Standards and Technology.
- COBIT (Control Objectives for Information and Related Technologies): This refers to a structured approach for overseeing and administering enterprise IT, which encompasses adherence to regulatory requirements.
- FERPA (Family Educational Rights and Privacy Act): FERPA compliance (Family Educational Rights and Privacy Act): FERPA, a federal statute, safeguards the privacy of student educational data.
- FISMA (Federal Information Security Management Act): A U.S. law that mandates information security standards for federal agencies and their contractors.
- AICPA Trust Services Criteria: A set of principles for evaluating and reporting on controls over information and systems.
Key Differences Between Security and Compliance
The table below compares the differences based on security, industry, scope, focus, outcome, and examples.
| Section | Security | Compliance |
| Definition | Protects data, systems, and assets from threats, unauthorized access, and vulnerabilities. | Ensures adherence to laws, regulations, and standards. |
| Focus | Robust security measures are implemented to shield against a wide spectrum of potential threats and vulnerabilities. | Adherence to specific legal, regulatory, or industry requirements. |
| Scope | Encompasses a broad set of practices and measures aimed at safeguarding the organization. | Concerned with meeting specific, often externally imposed, requirements. |
| Timing and Lifecycle | A continuous and ongoing process, with evolving threats and changing technologies. | Often involves periodic assessments and audits to verify compliance at specific times. |
| Voluntary vs. Mandatory | Voluntary and driven by the organization’s risk management strategy and security posture. | Mandatory and imposed by external authorities or industry regulations. |
| Measuring Success | Success is measured by the effectiveness of security measures in preventing breaches and incidents. | Success is measured by demonstrating adherence to relevant laws and regulations and passing compliance audits. |
| Examples | Implementing firewalls, encryption, incident response, and access control. | Adhering to GDPR, HIPAA, PCI DSS, SOX, FISMA, or industry-specific standards. |
| Outcome | A secure environment that protects against threats, data breaches, and unauthorized access. | Adherence to legal and regulatory requirements, reducing the risk of legal consequences and fines. |
Importance of Both
Both security vs compliance are essential for a well-rounded risk management strategy. Security protects an organization’s assets and data from threats that could lead to compliance violations, while compliance ensures that an organization operates ethically and legally.
By maintaining strong security measures, organizations can reduce the likelihood of breaches and security incidents, which, in turn, helps prevent potential compliance violations. At the same time, adhering to compliance requirements provides a structured framework for security practices and ensures that the organization operates within the bounds of the law.
How Security and Compliance Work Together?
Security and compliance are interrelated concepts that create a strong and resilient framework for safeguarding an organization’s information, assets, and reputation. Let’s explore how they collaborate to ensure a secure and compliant environment:
Security Supports Compliance
- Risk Mitigation: Security measures help mitigate risks and threats that could lead to compliance violations. For example, Access restrictions and encryption safeguard sensitive data, lowering the risk of breaches and guaranteeing compliance with data protection requirements.
- Data Protection: Security measures, such as data encryption and secure access controls, play a vital role in protecting confidential information. Compliance often requires organizations to safeguard sensitive data, and security measures help achieve this goal.
Compliance Informs Security
- Regulatory Guidance: Compliance requirements are often based on specific regulations and standards. By adhering to compliance mandates, organizations gain insights into what is expected regarding security. Compliance acts as a guide for security practices.
- Documentation and Audit Trails: Compliance often mandates the creation of detailed records and audit trails. These records can be valuable for security purposes, providing a history of system activities and helping to identify security incidents.
Shared Objectives
- Data Privacy: Both security and compliance aim to protect data privacy. Security measures like encryption, access controls, and data masking are essential for maintaining data privacy, a core component of many compliance regulations, such as GDPR and HIPAA.
- Ethical Practices: Compliance regulations often include ethical guidelines. Ethical behavior, such as not engaging in fraudulent activities or maintaining transparency, is essential for compliance and security.
Continuous Improvement
- Feedback Loop: Security and compliance should have a feedback loop. Security incidents and vulnerabilities discovered during security assessments can inform compliance efforts, prompting updates to policies and procedures.
- Updates and Adaptations: Organizations need to adapt as security threats evolve and compliance regulations change. Regular security assessments and compliance audits help organizations stay current and make necessary adjustments.
Resource Allocation
- Budget Allocation: Organizations should allocate resources to both security and compliance efforts. This ensures that the necessary technology, personnel, and training are available to maintain security and meet compliance requirements.
- Efficiency: Combining security and compliance efforts can lead to resource and cost efficiencies. For instance, security solutions that help with compliance can reduce duplication of effort.
Education and Awareness
- Training: Employees need to be aware of both security and compliance requirements. Training programs can educate them about best security practices and compliance with regulations.
- Culture of Compliance: Compliance culture promotes security culture. When employees understand the implications of non-compliance, they are more likely to follow security protocols.
Incident Response
- Plan Alignment: Security and compliance should align in incident response planning. When a security incident occurs, it’s crucial to address both the security breach and the potential compliance violations simultaneously.
- Mitigation and Reporting: A well-coordinated incident response plan ensures that security breaches are mitigated promptly and reported to regulatory authorities, as compliance regulations require.
Challenges in Balancing Security and Compliance
Balancing security and compliance can be challenging due to various factors that organizations must navigate.
- Conflicting Priorities: Balancing security measures and compliance requirements may pose a challenge as both goals may sometimes appear to conflict.
- Evolving Regulations: Frequent regulation changes require constant adjustments to compliance practices.
- Resource Allocation: Allocating resources for security and compliance can strain budgets and staffing.
- Complexity: Balancing multiple compliance frameworks in complex organizations can be intricate.
- Rapid Technological Changes: Security measures must adapt to new technologies, often outpacing compliance guidelines.
- Third-Party Vendors: Ensuring compliance in a vendor-dependent environment requires effective oversight.
- Audit Fatigue: Frequent audits for compliance can lead to audit fatigue and drain resources.
- User Experience: Stringent security measures may impede user experience and productivity.
- Sustainability: Maintaining the balance over time without neglecting security or compliance is a constant challenge.
- Non-Technical Risks: Balancing technical security and compliance needs with non-technical risks, such as legal or financial risks, is complex.
Conclusion
Achieving a harmonious balance between security vs compliance is a complex and ongoing endeavor for organizations. While security focuses on safeguarding against a broad range of threats, compliance demands strict adherence to specific, often evolving regulations and standards. Striking the proper equilibrium is essential for mitigating risks, protecting data, and maintaining legal and ethical integrity. It requires a proactive approach, resource allocation, and a culture of continuous improvement. Ultimately, organizations that successfully navigate these challenges are better positioned to thrive in an ever-changing landscape where security and compliance are indispensable.
Recommended Article
We hope that this EDUCBA information on “Security vs Compliance” was beneficial to you. You can view EDUCBA’s recommended articles for more information.