Definition
Social Engineering Toolkit in Kali Linux is an open-source penetration testing toolkit that enables hackers or attackers to exploit human social interaction and authentication processes. The tool allows you to fingerprint a victim’s social information(name and occupation), phone number, email address, and location. This information is then used to craft a convincing message that makes it appear as if they are from a legal source. The toolkit contains a wide variety of social-engineering tools that can be used to obtain sensitive or confidential information from the target machine by exploiting human psychology and behavioral patterns. This article takes you through all aspects of the social-engineering toolkit, including installation, features of SET, phases of SET, and uses of SET.
Explanation
The social engineering toolkit includes a wide range of attack vectors, including credential harvesting, payload delivery, and phishing attack. SET is used to create customized phishing emails executed on occupation and other personal information. SET includes a “USB HID attack” tool used to create a malicious USB device that emulates the keyboard and executes the pre-configured command onto the target system.
SET allows users to create custom payloads that can be used to execute specific actions in the target system or exploit specific vulnerabilities. Using techniques like keylogging and credential phishing, SET comprises tools for gathering credentials such as usernames and passwords from targets. The built-in reporting tool of SET allows users to track the success of the attacks and generate reports for analysis.
Key Takeaways
- The SET is an open-source tool for automating social engineering attacks. This tool includes the number of attacks.
- SET includes multiple built-in payloads, making creating custom attacks for specific needs easy. We can use SET for the use of malicious activity.
Steps to Install Social Engineering Toolkit
The social engineering toolkit allows us to perform phishing attacks. Using SET, we can create phishing pages for multiple websites. SET generates a phishing link which makes the legitimate website. The below steps show how we can install the social engineering toolkit on kali Linux as follows.
1. First, we need to open the terminal of kali Linux as follows.
2. After opening the terminal, go to the desktop folder.
Command:
# cd Desktop3. After going into the desktop folder, now in this step, create a new directory name as SET as follows.
Command:
# mkdir SET4. After creating the directory, now in this step, move into the SET directory using the following command as follows.
Command:
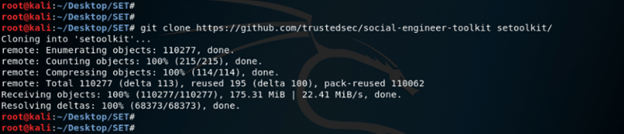
# cd SET5. After moving into the SET directory, now in this step, clone the SE Toolkit from GitHub as follows.
Command:
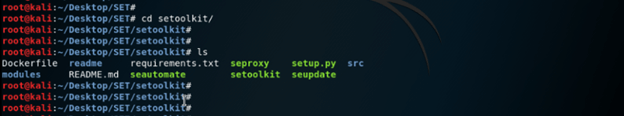
# git clone https://githum.com/trustedsec/social-engineer-toolkit setoolkit/6. After cloning the toolkit from GitHub, now in this step, we go into the setoolkit and check the file as follows.
Command:
# cd setoolkit
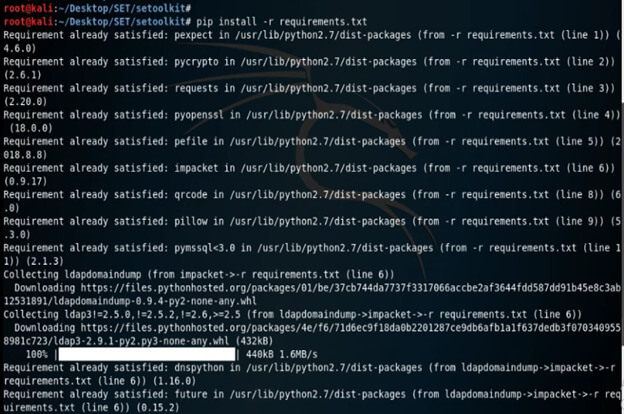
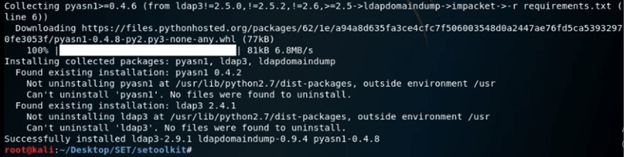
# ls7. After downloading the installation of SET, now in this step, we have installed requirement.txt using the pip command as follows.
Command:
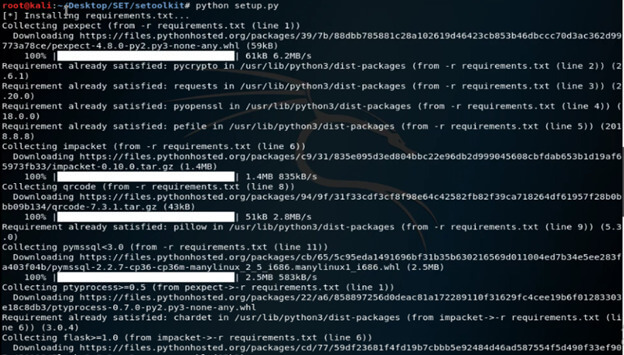
# pip install –r requirements.txt8. After installing the requirements.txt, now in this step, we have installed setup.py using the python command as follows.
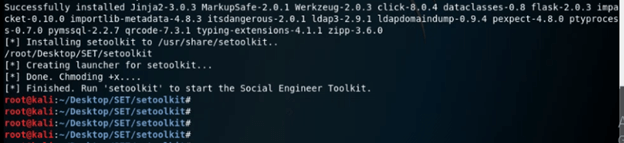
Command:
# python setup.py9. After installing all the requirements of setoolkit, now in this step, we are using setoolkit as follows.
Command:
# setoolkit10. After running the setoolkit, now in this step, we run the setoolkit by giving the option y as follows.
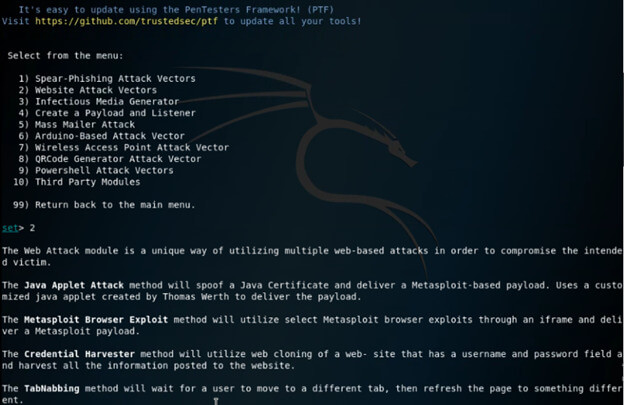
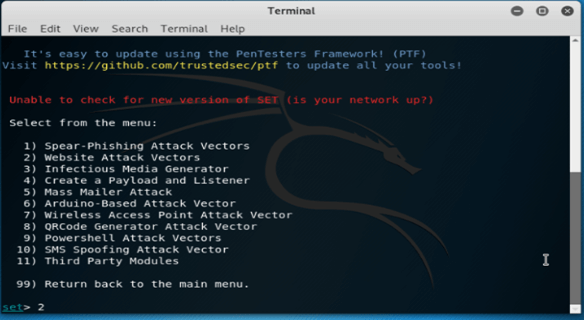
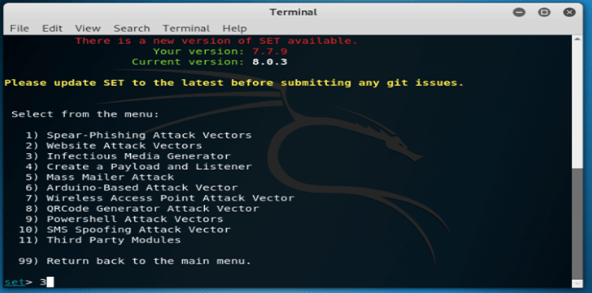
[y/n]: y11. After selecting the y option now in this step, we select the option as website attack vectors as follows.
set> 2
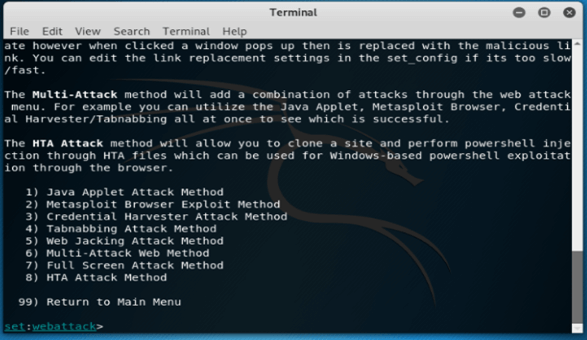
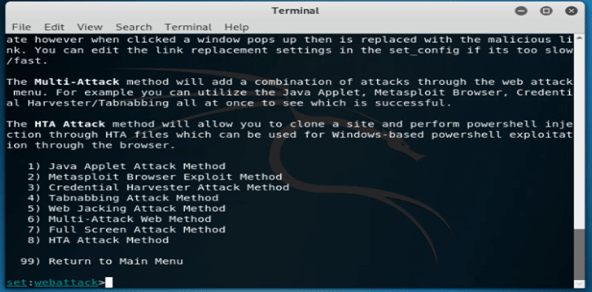
12. After selecting the option of website attack vectors, now in this step, we are selecting the credential harvester attack method as follows.
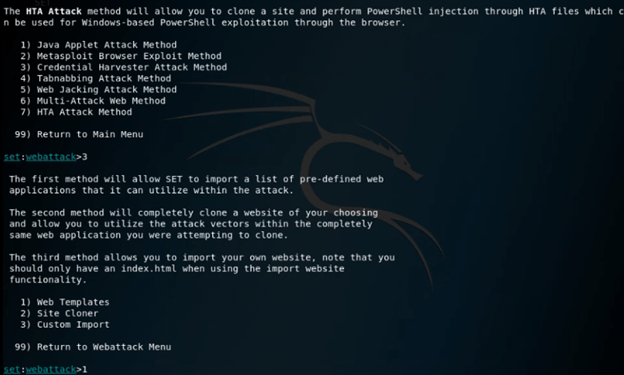
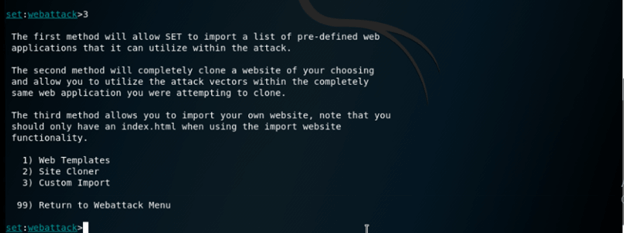
set:webattack> 3
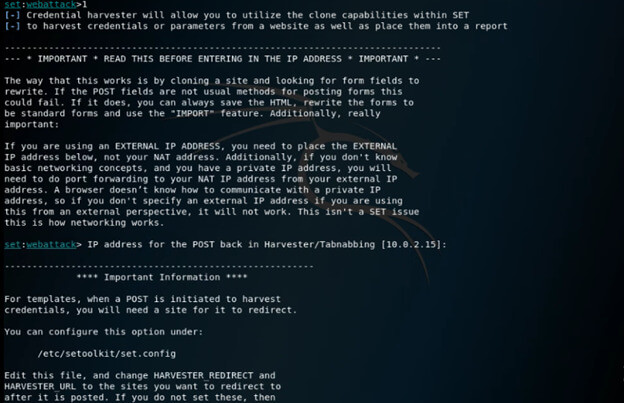
13. Now, in this step, we are creating a phishing page, so here we are selecting option 1 as follows.
set:webattack> 1
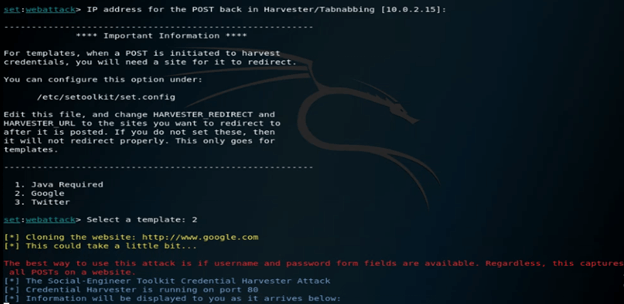
14. In the below example, we are creating the phishing page, so we need to choose option 2 as follows.
set:webattack> select a template: 2
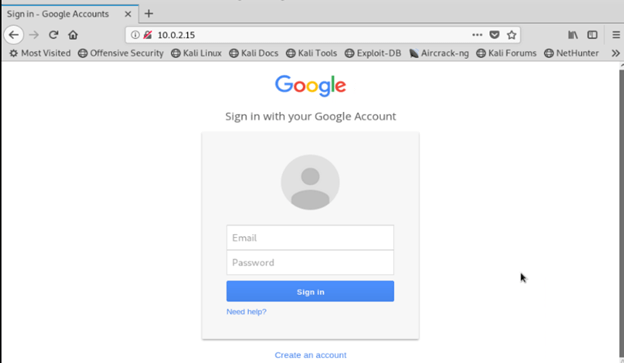
15. Now in this step, we have created the google phishing page as follows.
How to Use the Social Engineering toolkit?
SET contains multiple custom attack vector that allows us to make a believable attack. The below steps show how to use the social engineering toolkit as follows.
1. To use the SET we need to open the kali Linux in GUI mode as follows.
2. To open the SET, go to the applications -> social engineering toolkit -> SET.
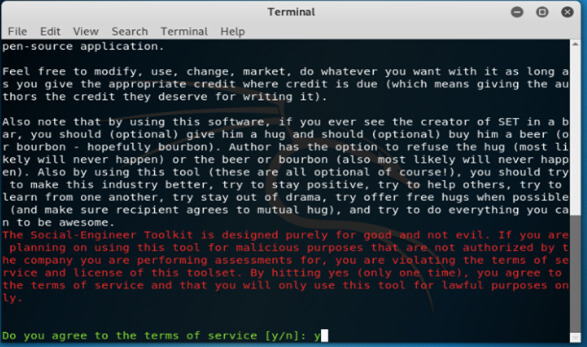
3. After opening the SET now in this step, we accept the terms of the SET as follows.
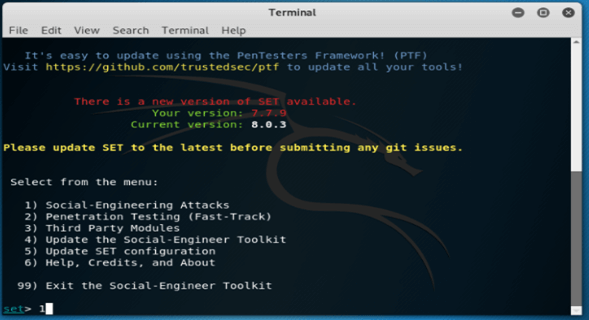
[y/n]: y4. After selecting the terms, we are now selecting the first option as social engineering attack as follows.
set>1
5. In this step, press 1 and enter, if we enter without entering any value, it will show all the details of each option as follows.
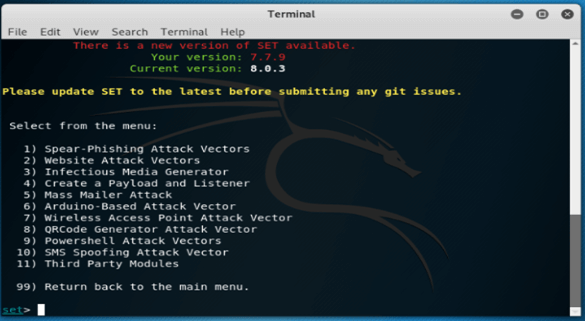
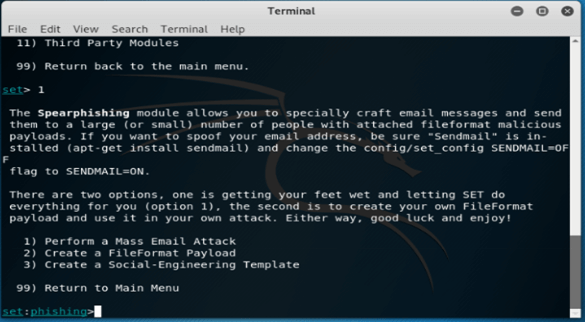
6. After checking all the details in this step, select the first option of spear-phishing attack vectors.
Set>1
7. After selecting type 1, now in this step, we are selecting sub-type 2.
set> 2
8. After selecting type 2, the next step is to select subtype 3.
set> 3
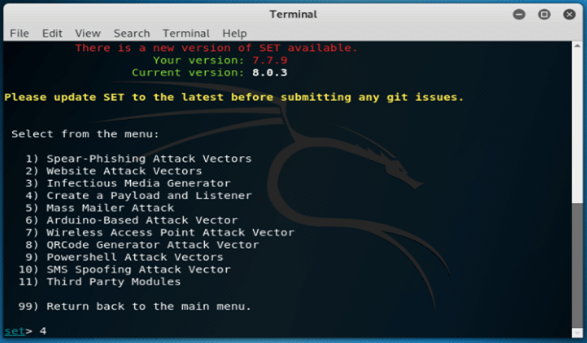
9. After selecting the 3 options, now by typing 99 go to the main menu and enter the 3 options again to select the infectious media generator as follows.
set> 3
10. After selecting the 3 options now we are selecting the option to create payload and listener. Now by typing 99 go to the main menu
set> 4
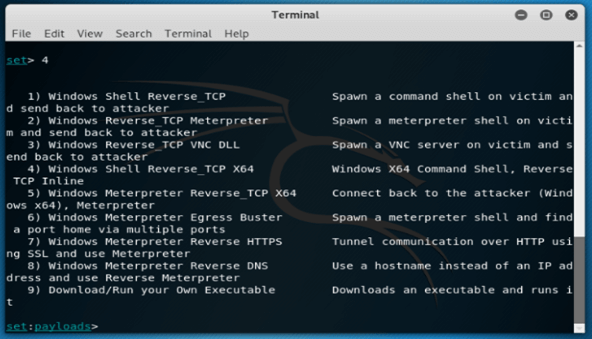
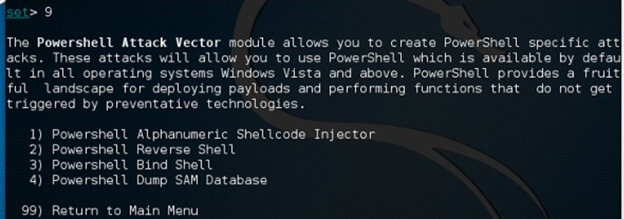
11. In the below example, we are selecting sub-option 9 to go into the power shell attack vector as follows.
set > 9
Phases of Social Engineering Toolkit
The SET includes four phases.
1. Investigation Phase
The Investigation Phase in SET involves identifying the target or group of targets and gathering as much information as possible. This includes email addresses, phone numbers, social media profiles, and other publicly available information. Finally, the attacker will use the information gathered to create a targeted social engineering attack that is more likely to succeed.
2. Hook Phase
It is the point where the attacker creates a scenario to trap the target. The purpose is to create a sense of urgency or excitement in the target that will cause them to take the desired actions, such as clicking on a link or downloading a file from fake emails that claim to offer a limited-time discount on a product or service.
3. Play Phase
This is the phase where the attacker executes the social engineering attack. The attacker impersonates a trusted individual, such as a friend or a colleague, to gain the target’s trust and convince them to take desired actions. The attacker offers something of value, such as login credentials free gift card, in exchange for the target’s personal information.
4. Exit Phase
The exit phase is the final step. In this, the attacker ensures that they have achieved their objective and tries to terminate the attack, maintaining a low profile to avoid detection. This phase involves cleaning up any traces of attack, such as removing any tools that were used and deleting log files. The attacker can avoid leaving any evidence behind that could b used to identify them.
Social Engineering Toolkit Features
The social engineering toolkit contains multiple features. Below are the features of SET as follows.
- It is open-source and free.
- SET will provide multiple attack vectors such as websites, spear-phishing, and infection media generators.
- It is already installed in kali Linux, so we do not need to install it again.
- It is portable, so we can easily change the attack vector.
- It will provide support to integrate with the other tools.
- It is platform independent tool that can run on Linux, windows, and UNIX operating systems.
- SET access to the testing platform of fast-track penetration.
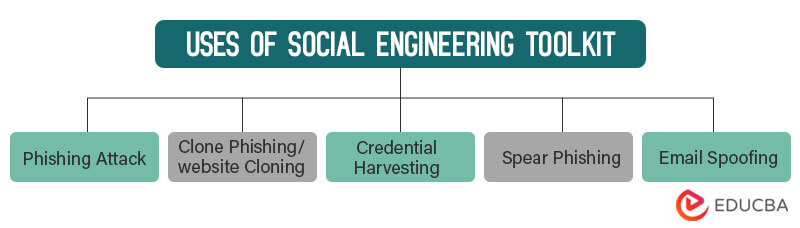
Uses of Social Engineering Toolkit
1. Phishing Attack
It can be used to create realistic phishing emails and social media messages that trick users into disclosing sensitive information such as credit card numbers, passwords, or other confidential data.
2. Clone Phishing/website Cloning
SET can be used to clone legitimate websites and create fake versions that are used for phishing or credential harvesting. When the victim enters their login credentials, the attacker captures the information and uses it to gain access to the real website.
3. Credential Harvesting
This involves creating a fake login page that looks like a legitimate website. When the victim enters their login credentials, the information is captured and saved later for use.
4. Spear Phishing
Used to create targeted phishing attacks that are tailored to specific individuals or groups. This can be particularly useful for penetration testing in organizations that have strict security measures.
5. Email Spoofing
SET can be used to spoof an email address, making it appear as if an email is coming from a trusted/reliable source when it is actually a phishing attack.
Conclusion
The SET is a powerful tool used to test the system’s security by simulating social engineering attacks. Social Engineering Toolkit in Kali Linux is effective, and it will also bypass the security measures like firewalls, antivirus, and other types of security measures. The SET will include multiple tools, such as email spoofing tools, phishing kits, and many more.
FAQs
Q1. What is the social engineering toolkit?
The SET is a collection of techniques and tools used to simulate social engineering attacks for testing security.
Q2. Which kind of attack is simulated with SET?
The SET simulates multiple types of attacks, such as pretexting, phishing, and many more.
Q3. Is it legal to use SET?
To use SET for testing purposes is legal. Also, it will be done with approvals and permissions. We can also use these tools to hack another system without permission.
Recommended Article
We hope that this EDUCBA information on “Social Engineering Toolkit in Kali Linux” was beneficial to you. You can view EDUCBA’s recommended articles for more information.