Updated April 7, 2023
Definition of Spring Boot OAuth2
In Spring boot, we have one mechanism which helps us to do Authorization; this is called as oauth2.0; by the use of this, we can easily authorize the interaction between two services. The main purpose of oauth2 is to authorize two services on behalf of the user who has access to the resource. oauth2 is not meant for authentication rather;, it is used for authorization. We have a resource; resource own we, authorization server, resource server, and client when it comes to the important terminology to the oauth2. All this entity plays an important role in oauth2; they are supposed to play a specific part of the oauth2 flow. Mainly we have three types of flow for oauth2, but in this tutorial, we will cover the only one which is most widely used and secure. In the coming section of the tutorial, we will see how we can implement oauth2 in our application to provide an authorization mechanism, also a closer look what are the basic steps needed to achieve this in the spring boot application.
Syntax:
As we know that oauth2 is a mechanism that requires configuration in place in order to make it work. In this section, we will see basic configuration, which is very much required to start with oauth2 in spring boot see below;
@EnableWebSecurity
public class class_name extends WebSecurityConfigurerAdapter {
// logic goes here
}As you can see in the above line of code, we are trying to create the security class and trying to enable web security in order to implement this. Let’s take a closer look at the practice syntax for better understanding see below;
e.g. :
@EnableWebSecurity
public class DemoConfig extends WebSecurityConfigurerAdapter {
// logic goes here
}In the coming section, we will see in detail what are the steps needed to implement this properly in spring boot applications for better understanding for beginners.
How does Spring boot oauth2 work?
As we have already known that in spring boot, we can implement oauth2 to authorize the user, it basically meant for authorization, not for authentication. Also, the primary function of oauth2 is to authorize the user. Its basic purpose is to authorize the two different services required to access some resource from then on behalf of the user with has the access. In this section of the tutorial, we will see one problem statement and try to understand it better. As we have already known that oauth2 has various terminology which will give us a basic understanding of the flow and how it works internally; let’s get started;
1) Resource: This is the resource that we want to access, and for this, we want the authorization. It is called a protected resource as well.
2) Resource owner: This is the entity that has access to the protected resource, which means who can allow us to grant access to the resource we want to access or any other service want to access.
3) Resource server: This is the server that has the protected resource with it, and the other service wants to access it, but they have the valid authorization or access in order to use the resource.
4) Client: This is often term as a client means the one who wants to access the protected resource on behalf of the user. If the user gives the permission, then it can access otherwise, no.
5) Authorization server: This is the one that is very important, and it can be coupled with the resource server, or it can be the single server, which is running alone to authorize the other service and provide them the resource. But this server has to provide all kinds of security and should allow someone who is to authorize on behalf of a user.
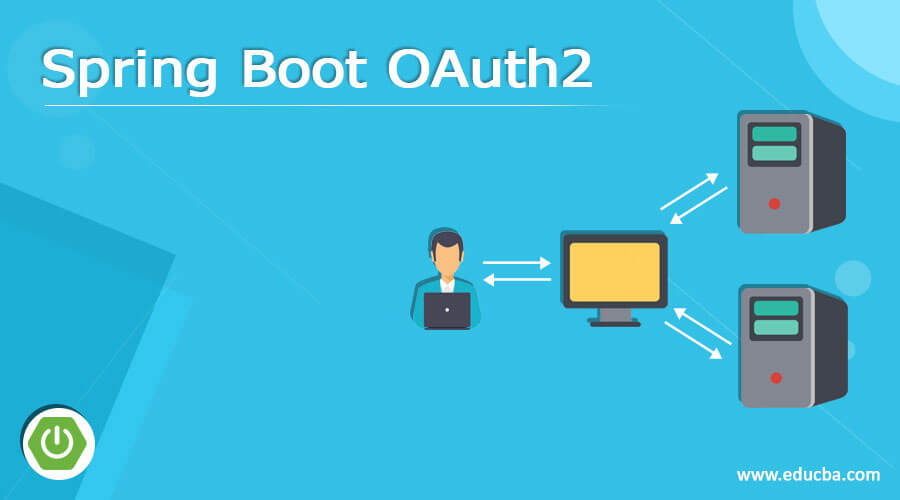
Let’s understand one problem statement to get this type of situation; in the below diagram, we have to state where we have user and two different services; they want to communicate with one other let’s get started to see below;
1) User has some data which resided on service two. But the user directly intercepts with service one, not with service at the moment. So user told service 1 to get the data from service 2.
2) In this case, service 1 and service 2 both do not know each other who they are.
3) Service 1 told service two that I want data of this user from you can you provide me? But service 2 does not know, and it will say I cannot provide without the user consent.
4) So now it will ask the user that service 1 wants to access your personal data, which resides on my server should I allow him access? or is this a valid URL?
5) Now, users will say yes, allow access to it is to the true one, allow them to access my data.
6) In this way, oauth2 works, in general, to allow the access of resources on behalf of the user.
To solve this problem, we have oauth2, which protects and secures our data from the server and only authorizes it when it comes from the right location with the consent of the user if the user allows it. So it is very secure, readable, and easy to understand as well.
Let’s take and look at the flow chart details how it exactly works in the scenarios to exchange the token, in order to get the details or data from the other service see below;
1) In the first step user will tell service 1 to get the data from service 2.
2) Now, in this step, it will go to the authorization server to request access in order to access the resource.
3) But the authentication server does not know because he only trusts his user, so it will again go back to the user and ask him if he wants to give access to this service.
4) Now, it depends on the user whether he wants to allow the access or not. In this case, it will allow and send this to an authorization server.
5) Now, the authorization server has cross-checked it with the user and got his permission to allow access to the service. Now the authorization server will give it an auth token in der to access the resource on the server.
6) With this auth token, now service 1 has to make one request to get the access token. S service 1 will pass this auth token to the authorization service and get the access token to access the actual resource on the server.
7) Now, the authorization server will give it back an access token in return
8) Now, this is the final step where service 1 will call the API endpoint to get the data of the user with the help of this access token.
This is how the flow of oauth2 works in the spring boot application. And we have already seen it is very much secure a well. in order to get the resource with the consent of the user, if he allows it, we cannot go and access it.
Conclusion
As we have already seen, it is easy to use, and how it works internally to authorize the external service on behalf of the user. Just make the small configuration and make this work properly. But before that, its working was important how it works in spring boot.
Recommended Articles
This is a guide to Spring Boot OAuth2. Here we discuss the Definition, syntax, How Spring boot oauth2 works? example with code implementation. You may also have a look at the following articles to learn more –
