Updated March 17, 2023
Introduction to Symmetric Algorithms
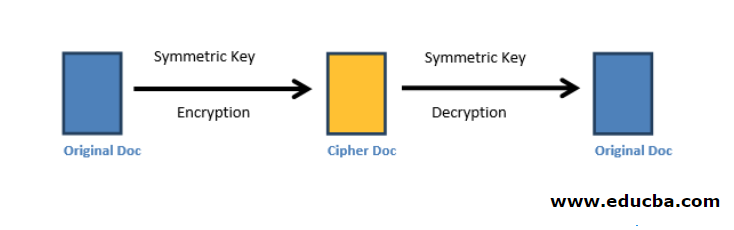
Symmetric encryption, which can also be called a secret key algorithm, uses only one key: a secret key for encryption and decryption of messages. The main disadvantage of symmetric key encryption is that all parties involved in communication have to exchange the key used to encrypt the message before they can decrypt it.
Fig1.a depicts the basic symmetric key encryption:
Figure1.a Symmetric-key Encryption
Types of Symmetric Algorithms
Broadly symmetric algorithms are classified into two.
- Block
- Stream
Block Algorithms
Block algorithms encrypt the data block by block (many bytes). Block refers to the specified set of bits, and these bits are altered/encrypted using a secret key. There is a drawback with the block algorithms, which is, let us assume that we are going to encrypt network stream data; this data is retained by the encryption system in its memory components. This retention of data is done when the system actually waits for complete blocks of data. This wait time may lead to a security gap that can compromise the data’s security and integrity. To avoid this threat, we can reduce the block and merge the data with previously encrypted data block until further blocks are received; in simple terms, this technique is called feedback. This algorithm will encrypt only if the complete block is received.
Stream Algorithms
In-Stream algorithms, the data is encrypted byte by byte and sometimes even bit by bit. In the case of a streaming algorithm, the data is not retained in the system’s memory; hence, one can say that this is much safer compared to the block algorithm as data is not retained in the system without encryption.
Furthermore, they are several types of encryption algorithms out of those few are listed below.
- DES & Triple DES
- RC2
- Blowfish
DES & Triple DES
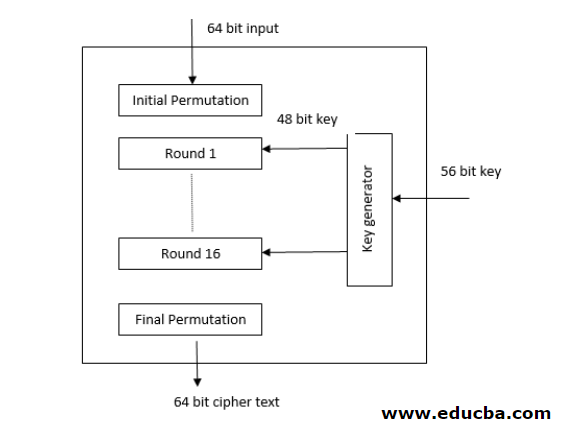
DES stands for a Data encryption standard that takes a 64-bit plain text and encrypts into a 64-bit ciphertext and decrypts back with the help of a 56-bit key. In DES, the encryption process starts off with an initial permutation stage where it will take the input as 64-bit data and permute them in a predefined manner. Followed by initial permutation is that 16 Feistel cipher rounds (An Feistel cipher takes the input and divides it into two parts and does the encryption on only one part) where each round will use a different 48bit cipher key. For encryption & decryption purpose, it uses a cipher and reverses a cipher algorithm. Finally, the data goes through the final permutation stage to get back the ciphertext. Similar to DES, Triple DES is nothing but DES cipher repeated 3 times. Fig2.a shows the generic architecture of the DES algorithm.
Generic Architecture of DES algorithm
RC2
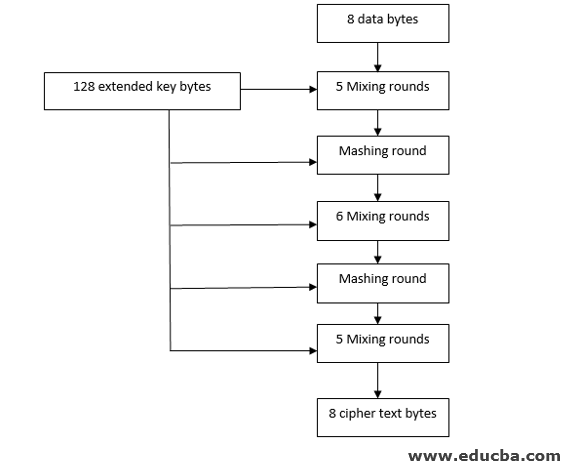
This is a block cipher algorithm where at first, the data is divided into a block size of 8 bytes, and these blocks are processed separately. This algorithm was widely used in the ’90s. Rc2 cipher uses a secret user key whose size can vary from one byte to 128 bytes. It takes this secret user key and uses a key expansion algorithm, and encrypts the data. This algorithm is designed in such a way so that it can be easily implemented in 16-bit microprocessors. Here there are no Feistel rounds; instead, the data undergoes 18 rounds of mixing and mashing. Fig2.b shows the generic architecture of the RC2 algorithm.
Generic Architecture of RC2 algorithm
Blowfish
This is an asymmetric algorithm that replaces DES. Here the block size used is 64 bits and key sizes ranging from 32 to 448 bits. Encryption using blowfish primarily consist of two stages
- Round function
- Output operation
The round function performs the following steps.
- Key whitening, where the left portion of the input data is taken, and exclusive OR operation are performed.
- In the second step, it uses S-boxes, these S-boxes maps 8-bit data to 32 bit, and the output is taken to combine with a combination of addition and XOR operations.
- The above two steps combined together referred to as the F function. With the F function’s output and the right side of the input data, XOR operation is performed.
- The final step involves the swapping of the output.
The output function reveres the final swap and performs output whitening. The output of this function is a blowfish ciphertext. Decryption with blowfish involves the usage of the same structure as encryption as it uses a Feistel cipher, but the round keys must be used in reverse order. The major advantage of this algorithm is that it is available in the public domain to be easily accessible. The drawbacks are; basically, it’s a bit time-consuming in generating the keys, and if the block size is small, it is vulnerable to attacks.
Applications of Symmetric Algorithms
Some of the places where the symmetric encryption algorithm is used are
- Card transactions are used to prevent identity thefts and fraudulent transactions.
- To confirm the identity of the messenger.
- Hashing and random number generation
- Database encryption
Conclusion- Symmetric Algorithms
Symmetric algorithms are much faster and efficient when compared to asymmetric algorithms. This is all the more reason they are used in bulk encryption. But its drawback is that the key management is very exhaustive; hence maintenance at a large scale is a tedious task, where we need to have high-grade security, to achieve this, we must have maintained the lifecycle of the key generated using a separate system. Hence we must always use proper encryption to avoid any attacks on our data.
Recommended Articles
This is a guide to Symmetric Algorithms. Here we discuss the Introduction and Types of Symmetric Algorithms along with DES & Triple DES. You can also go through our other suggested articles to learn more–